When hacking Wi-Fi networks, having the right wireless adapter is essential. But hunting online for one can be a frustrating experience. To see how the handful of Kali-compatible adapters on the market measure up, I ran a series of tests to benchmark and compare their range, signal strength, and ability to enter monitor mode and perform packet injection. This should help you determine which adapter is right for your own hacking needs.
By now, you should already be familiar with Kali Linux and the Raspberry Pi 3 as a go-to setup for portable and efficient penetration testing.
However, if you need more information about choosing a wireless adapter for hacking or about your best options for a wireless adapter, then might I suggest following those links and giving my fellow Null Byte contributors' articles a quick study. Starting off can be a tad intimidating, but don't be discouraged, we're here to help!
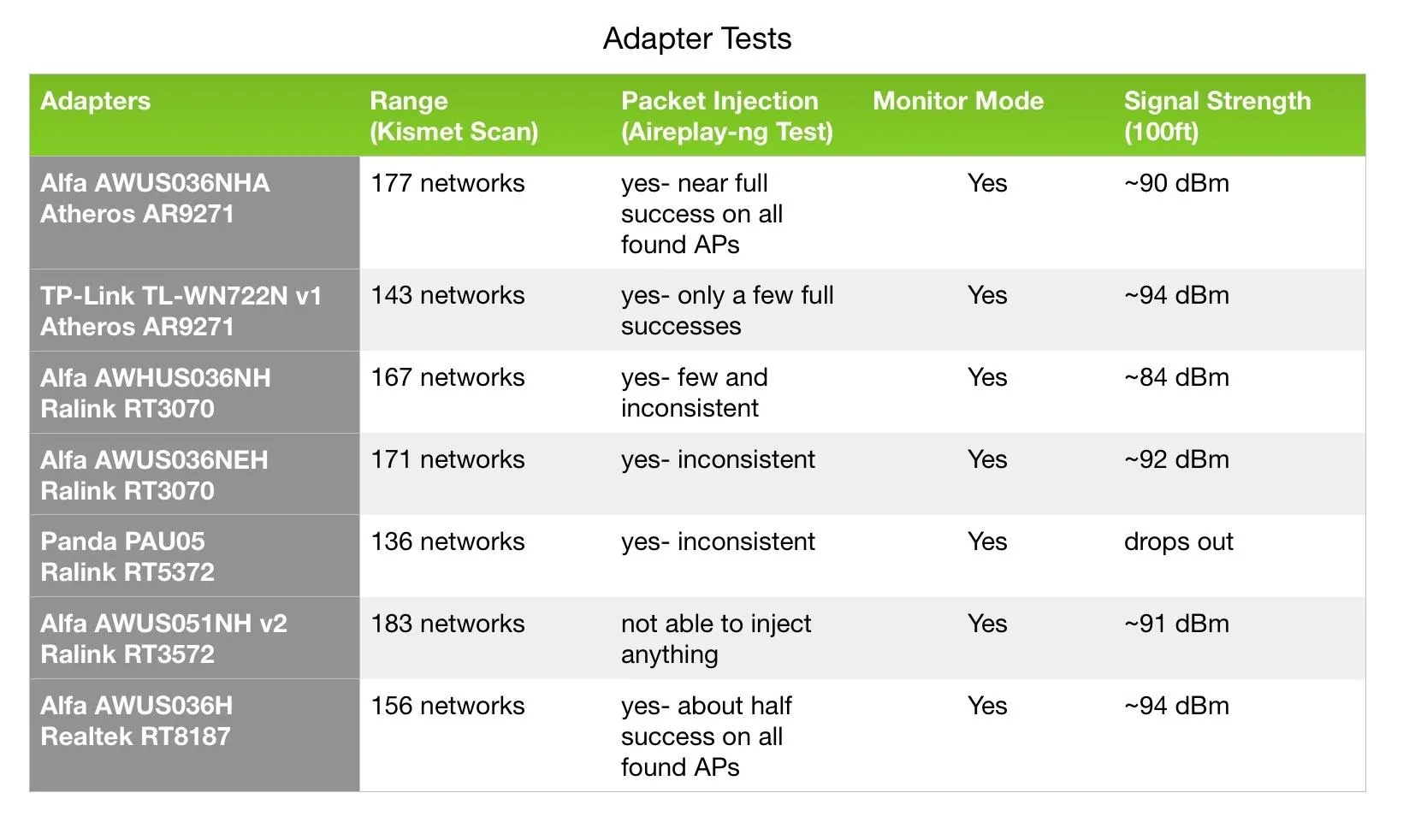
Compilation of adapter test results in a graph.
How Adapters Compare: Testing Parameters
Range and signal strength testing were performed in an apartment complex with a relatively busy wireless environment, running each adapter continuously for 10 minutes. To test for monitor mode and range, I simply ran a Kismet scan. For packet injection, I ran Aireplay-ng packet injection tests.
- Don't Miss: How to Automate Hacking Wi-Fi with Besside-ng
Then, I ran Airodump-ng scans to measure the signal strength between each adapter and a fixed test AP as I moved my adapter setup away from it. It should be noted that walls and other signal obstructing obstacles always play a factor in adapter performance. The results are organized by the chipset.
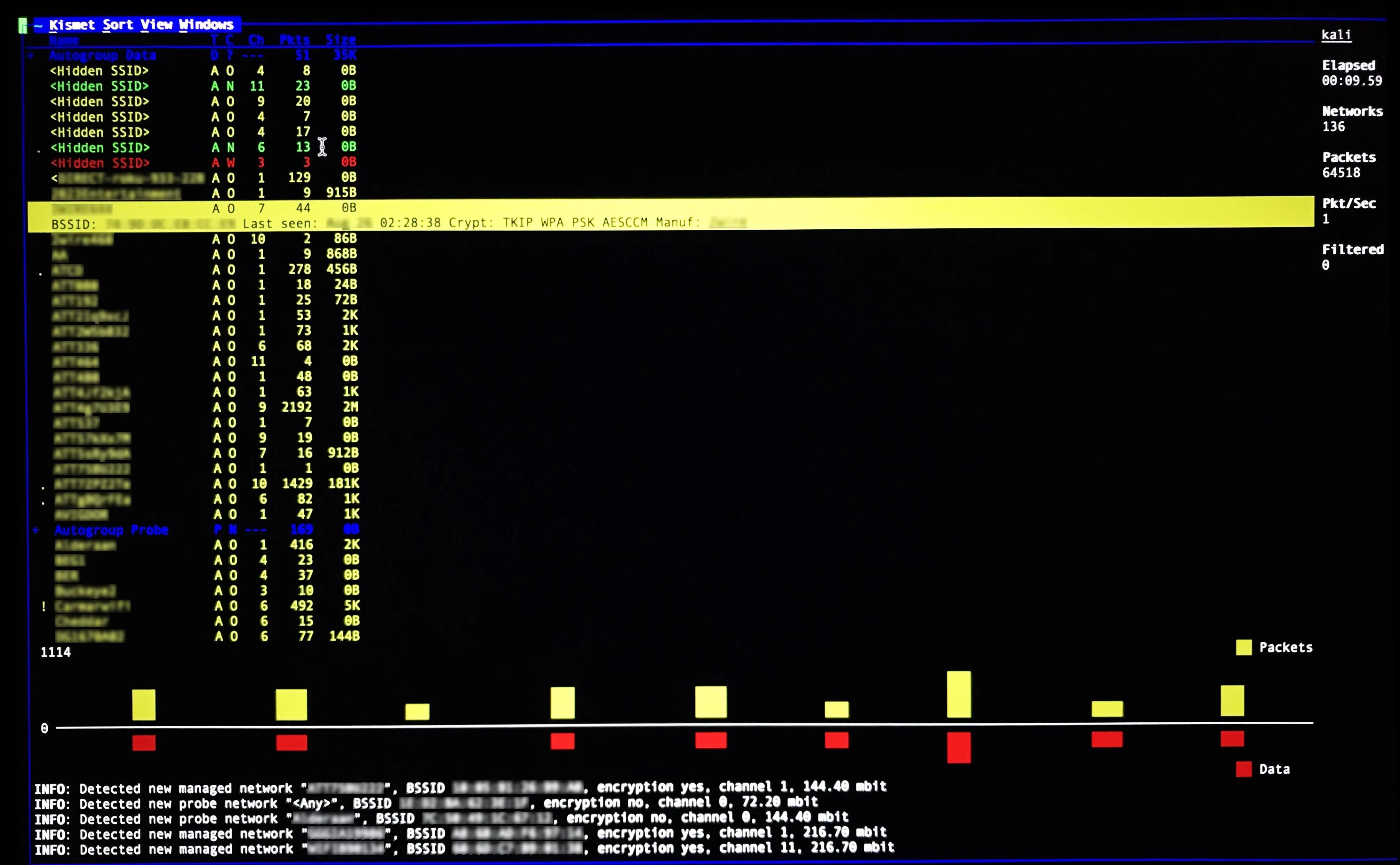
Here, we see a Kismet Scan showing results from an apartment complex.
Atheros AR9271 Chipset
Overall, the 36NHA performs exceptionally well under most circumstances. It supports monitor mode, and after 10 minutes, this adapter scanned 177 networks and had a nearly flawless packet injection percentage.
When moved away from the base testing AP, the signal lost significant power. At about 100 feet from the AP, the signal strength hovered in the 90 dBm range. At this point, reliable packet injection would be out of the question.
It's important to keep in mind what's between you and an AP you may be targeting. Having owned this Alfa myself, I can attest to its strength when placed somewhere with a clear line of sight.

The Alfa AWUS036NHA.
Like the 36NHA, the TP-Link supports monitor mode and performs adequate packet injection. Its range isn't as far —only about 143 APs were detected in my first test.
Signal strength was similar to the NHA all the way to about 100 feet from the base AP. Given its size and portability, it makes for a great compact adapter for a more alluring price.

The TP-Link TL-WN722N v1.
Ralink RT3070 Chipset
The 36NH does support monitor mode and has an impressive range, with 167 APs picked up during my first test. It also supports packet injection, however, its performance was rather inconsistent.
Its signal strength at around 100 feet from the AP dropped to the 80–90 dBm range, making it only slightly more useful if you're in need of a couple extra feet in strength. This small difference, however, could add up to a more significant advantage when paired with a directional antenna.

The Alfa AWHUS036NH.
The 36NEH performed very well for its compact size. Like the previous Alfas tested, it supports monitor mode and packet injection. Its range was especially impressive, picking up 171 networks in the 10 minute test period.
It's packet injection performance, however, was not stellar, as it was only able to achieve full injection success with a couple APs. Its signal strength was also comparable to the NHA and TP-Link. Similar to the TP-Link, it's a great option for a mobile setup.

The Alfa AWUS036NEH.
Ralink RT5372 Chipset
Like the TP-Link and NEH, the Panda wireless adapter is a favorite among most beginners because of its portability and price. It supports monitor mode and picked up 136 APs — the fewest overall.
Its signal strength was also the lowest performing, completely dropping signal at about 70–80 feet from the base AP. However, this adapter is by far the least conspicuous, since it doesn't possess any pesky higher gain antenna, and is therefore also best for on-the-go probing.
As for packet injection, the official word from the manufacturer is that it does NOT support packet injection. Its official chipset is also an RT5372, NOT 3070, per a Panda Wireless representative. This may be contrary to what you've read elsewhere online or even experienced yourself while using this adapter. That being said, my tests present a discrepancy in the claim that it does not perform any packet injection.
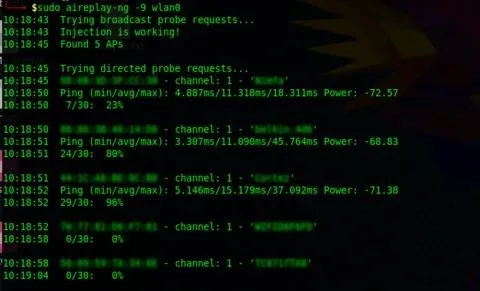
Running Aireplay-ng injection test on the Panda PAU05 wireless adapter.
In this case, its performance was comparable to that of the 36NH. I chose to run besside-ng to further gauge its packet injection ability. Besside-ng requires injection to achieve its goal of capturing WPA handshakes. A successful "pwn" of a network, means that the adapter is in fact capable of it.

Besside-ng test running with the PAU05 wireless adapter.
Currently, the jury is still out, as customer reviews on Amazon and personal use have suggested that the PAU05 can perform packet injection. However, some users have reported that it cannot. I hope to have a clearer explanation after further correspondence with Panda Wireless.

The Panda PAU05.
Ralink RT3572 Chipset
The 51NH v2 performed best in range out of all adapters tested by just a hair — 183 networks. It supports monitor mode but, unfortunately, it does not support packet injection, thus making it unusable for activities like executing a man-in-the-middle attack.
Unlike the other adapters, though, it does detect 5 GHz wireless signals, making it great for other activities such as wardriving; the searching, recording, and mapping of Wi-Fi networks in a moving vehicle. Once again, this adapters signal strength at extended range was also comparable to the NHA.

The Alfa AWUS051NH v2.
Realtek RT8187 Chipset
The 36H is the oldest of the bunch, but still performed fairly well considering its age. It supports monitor mode, picked up 156 networks, and performed moderately reliable packet injection.
Once again, this adapters signal strength was comparable to the NHA, if just a little weaker — hovering in the upper 90 dBm range. It should get the job done in most cases, but the more recent models are probably a safer bet.

The Alfa AWUS036H.
Making the Decision
Choosing a wireless adapter for your hacking needs comes down to several factors. No wireless adapter can do it all, nor are they all practical for every scenario. The TP-Link, NEH, and for some, the PAU05, make great options for portable hacking setups.
- Don't Miss: How to Create a Custom Wordlist with Crunch
Here, the TP-Link tested out as the most reliable in terms of packet injection, while the NEH was the best in range.
The 36H, 36NH, and NHA are more practical for stationary hacking setups. In this case, the NHA shines having the greatest packet injecting performance and a far range. Although all adapters mentioned are adequate for wardriving, the 51NH v2 makes the better choice in this field, as it has the best range and can pick up both 2.4 and 5 GHz wireless signals.
- Don't Miss: How to DoS a Wi-Fi Network Continuously
Because of these factors, purchasing the right adapter really hinges on how you intend to use your adapter. In case you're still unsure, the most important questions to keep in mind are:
- What are your goals with this adapter?
- Where will you be using this adapter?
- How much range are you trying to achieve?
- What kind of wireless bands are you looking out for? (802.11a/b/g/n/ac?)
- How portable are you looking to keep your setup? Will you be stationary or on the go?
If you have any comments, questions, or have run your own tests and have results to share, please leave them in the comments below!
- Follow Null Byte on Twitter, Flipboard, and YouTube
- Sign up for Null Byte's weekly newsletter
- Follow WonderHowTo on Facebook, Twitter, Pinterest, and Flipboard
Cover image and screenshots by Vantasky/Null Byte

























Comments
Be the first, drop a comment!