Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.
In order to function, Wi-Fi devices are always doing one of two things to try to discover available networks; They either send out beacon frames or probe frames.
How Beacon Frames Work
Wi-Fi access points (APs) emit packets called beacon frames which contain information about the access point they are advertising. This information allows nearby devices to be aware that the access point exists and to decide whether or not the network has been connected to before. If the network is recognized by a device, the device will attempt to connect to the network.
By opening a beacon frame in Wireshark, we can see that they contain information about the device that transmitted the packet, the Wi-Fi network the beacon frame is advertising, and information about what channel the AP is operating on and what speeds that the network supports. This is how your phone and laptop can offer you a list of networks nearby seemingly out of thin air, as your device will detect these packets and provide the user the ability to connect if they want to.
In Wireshark, a beacon frame looks like this:
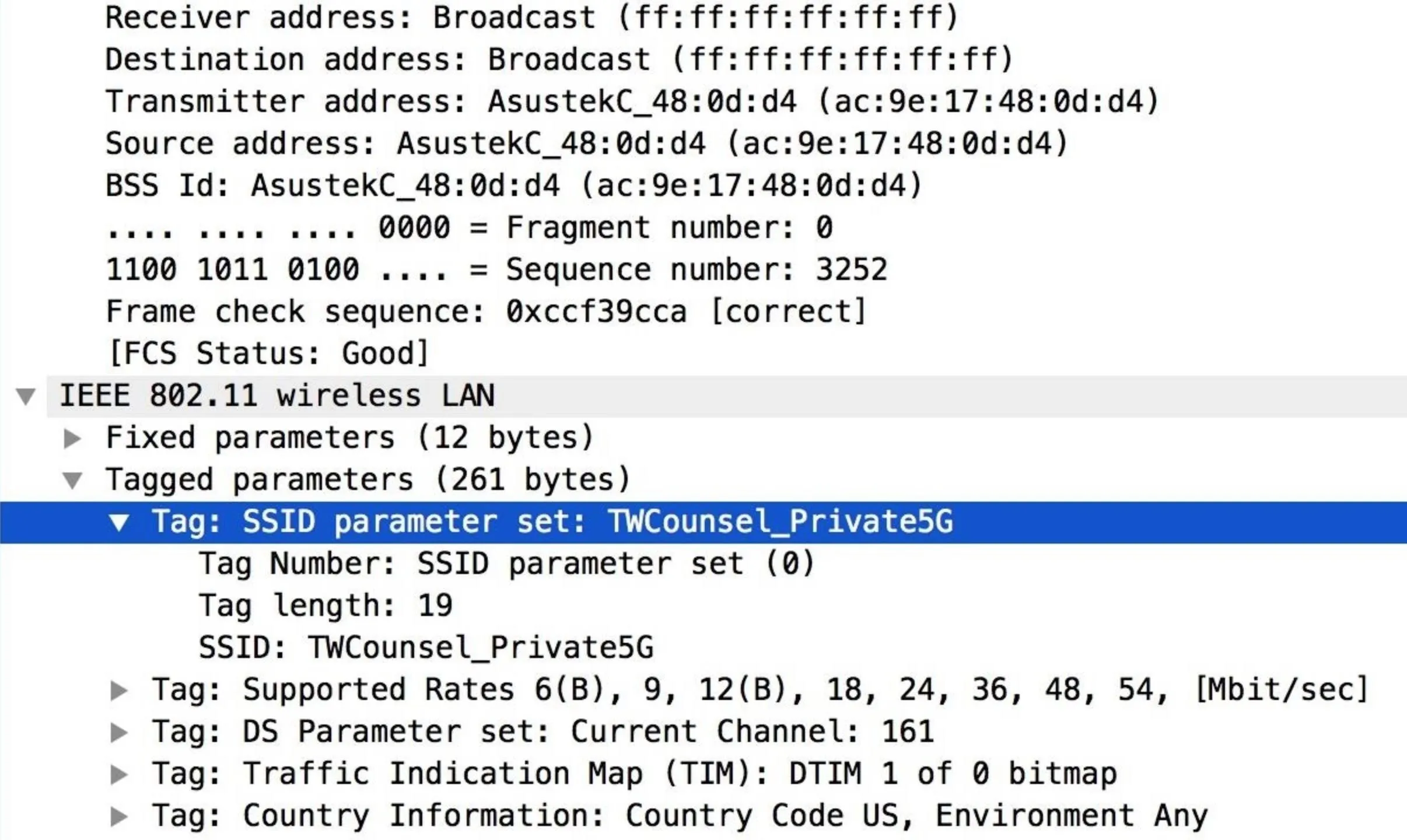
How Probe Frames Work
The second way a Wi-Fi connection happens is when your device attempts to find a nearby network to connect to by sending out a kind of packet called a probe frame.
Probe frames function in almost the opposite way of beacon frames. The client device will send out packets searching for Wi-Fi networks to which it has recently been connected. This allows you to quickly and seamlessly reconnect to networks like your home or work network if you are disconnected or momentarily wander out of the coverage of the network.
In Wireshark, we can look at a probe frame to discover information about the device sending the packet, as well as the name and channel number of the access point it is calling for. You can see the following probe frames transmitted on a subway train:
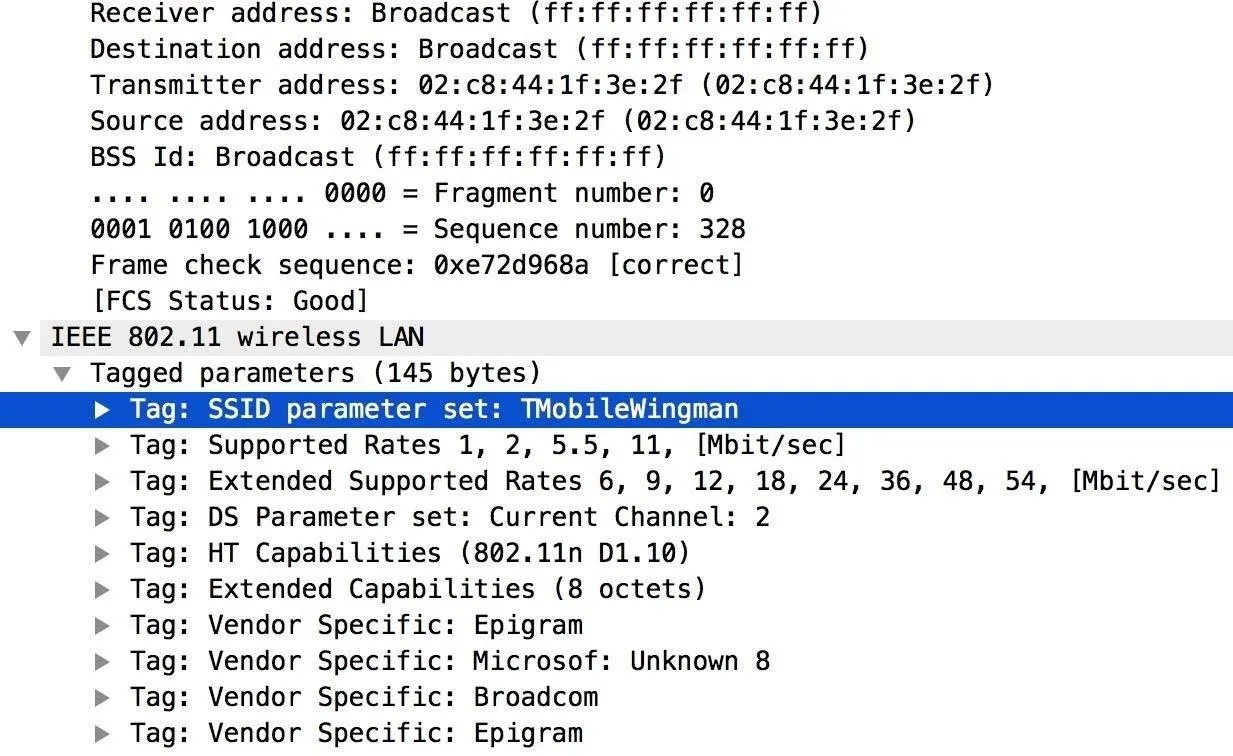
Devices like laptops and smartphones will send out probe frames on all channels even when the Wi-Fi is turned off. This is because Wi-Fi-assisted geolocation is turned on by default and is not affected by the Wi-Fi connection option being turned off. So, in general, turning off your smartphone's Wi-Fi alone will not prevent the device from sending probe frames.
What Probe Frames Can Show
This practice has attracted attention from security researchers like Mathy Vanhoef, who showed that probe frames can be used to track users with a high degree of precision and that even attempts to prevent this (like randomizing the MAC address used in probe frames sent by client devices) is not very useful in preventing tracking. Mathy's work has uncovered many ways of reading into the information contained in probe frames, including multiple ways of revealing a nearby device's real MAC address.
MAC address randomization is often done in ways that are not consistent or genuinely random enough to be effective, including sending the device's real MAC address in response to any beacon frame the device recognized, including ESSID's like "Google Starbucks." This means most people walking by a coffee shop with free Wi-Fi they've used before are momentarily de-cloaked while they are within range.
Aside from bad MAC address randomization, the information elements contained in probe frames include information that is often enough to create a fingerprint for tracking a device. This is because many devices do not follow the Wi-Fi standard exactly and arrange their elements slightly differently. The elements can be in different order or may contain some vendor-specific information.
Because the data in the information elements contained in the probe frame, as well as the incremental sequence number of the packets being sent, can be used to zero in on specific devices, probe frames provide arguably the cheapest way to automatically spy on targets both from a distance and up close. By using tools like Wigle Wi-Fi, we can also look for the physical address a target device has been to recently by inputting the ESSID we see in probe frames into the search to see if we can find a matching access point in our area.
Tracking Wi-Fi Devices via Probe Frames
Using probe frames and the ability to decloak or track users, we can learn a lot of information. Besides being able to detect intruders in areas they're not supposed to be, we're also able to monitor human activity and keep track of when people come and go. We can see what networks people have permission to connect to, and with multiple Wi-Fi sensors, we can track their movement in real time. Major retailers use this practice to monitor customer traffic flow through stores, using it to sell the retail space customers spend the most time to manufacturers at a premium.
Because probe frames are essentially a device sending an identifiable ping at regular intervals, you can track devices with a directional antenna with high precision. Because Wi-Fi has a line of sight range, a directional antenna can observe activity in a location a mile away to determine who is home and what devices are present without being anywhere near the area.
Combined with a system like a license plate or facial recognition scanner, probe frames could allow a hacker to tie your cell phone to your face or vehicle just by setting up a camera and a directional antenna.
The ability to track a target via their smartphone or laptop allows for hackers to design attacks that act intelligently, reacting to the presence of a target's devices by performing a malicious action like jamming one person's machine from being able to join nearby networks. Also, an attacker can use the information contained in probe frames to construct an attack to take over the data connection on a target's device.
Taking Over Data Connections Using Observed ESSID's
By listening in on probe frames, an attacker can attempt to take over the data connection of the target device by taking advantage of the information contained in probe frames. While many devices will no longer put the ESSID of the network they're looking for into their probe frames, there is a sizable percentage that either still does all the time or will under certain circumstances.
What You'll Need for This Guide
To get started using Probequest, you'll need to have a network adapter that can be put into monitor mode. This will allow you to hear transmissions from channels and networks other than the one your device is trying to connect to. If your laptop's card isn't compatible, you can check out our list of compatible network adapters.
Probequest installs with pip, so you'll need to have Python installed as well. If you're running Kali Linux, make sure to update and upgrade your system before starting by typing the following into a terminal window.
apt update
apt upgradeInstall Probequest
Installation of Probequest is very straightforward. In a new terminal window, type the following to install Probequest. If you get an error saying you don't have pip3, you can install it by typing apt install python3-pip into the terminal window, then try the command below again.
sudo pip3 install --upgrade probequest
Collecting probequest
Downloading https://files.pythonhosted.org/packages/93/6f/aaaf91f35eb7082c03e17a543df0646ae71620b6a579d40aef19b6d09aea/probequest-0.6.1.tar.gz
Collecting argparse>=1.4.0 (from probequest)
Downloading https://files.pythonhosted.org/packages/f2/94/3af39d34be01a24a6e65433d19e107099374224905f1e0cc6bbe1fd22a2f/argparse-1.4.0-py2.py3-none-any.whl
Collecting netaddr>=0.7.19 (from probequest)
Downloading https://files.pythonhosted.org/packages/ba/97/ce14451a9fd7bdb5a397abf99b24a1a6bb7a1a440b019bebd2e9a0dbec74/netaddr-0.7.19-py2.py3-none-any.whl (1.6MB)
100% |████████████████████████████████| 1.6MB 718kB/s
Collecting scapy>=2.4.0 (from probequest)
Downloading https://files.pythonhosted.org/packages/68/01/b9943984447e7ea6f8948e90c1729b78161c2bb3eef908430638ec3f7296/scapy-2.4.0.tar.gz (3.1MB)
100% |████████████████████████████████| 3.1MB 468kB/s
Requirement already up-to-date: urwid>=2.0.1 in /usr/lib/python3/dist-packages (from probequest)
Building wheels for collected packages: probequest, scapy
Running setup.py bdist_wheel for probequest ... done
Stored in directory: /root/.cache/pip/wheels/0e/8a/6e/39dc49dd1f36136060c4b65edd8e6b33350498ca742f113073
Running setup.py bdist_wheel for scapy ... done
Stored in directory: /root/.cache/pip/wheels/cf/03/88/296bf69fee1f9ec7a87e122da52253b65f3067f6ea8719b473
Successfully built probequest scapy
Installing collected packages: argparse, netaddr, scapy, probequest
Successfully installed argparse-1.4.0 netaddr-0.7.19 probequest-0.6.1 scapy-2.4.0You can also try installing the program from GitHub with the following commands.
git clone https://github.com/SkypLabs/probequest.git
cd probequest
sudo pip3 install --upgradePut Adapter into Monitor Mode
Next, we'll need to locate and put our wireless adapter into monitor mode. To do this, we'll open a terminal window and use ifconfig to give you the name of the network adapters that are connected. In Kali Linux, yours should be something like "wlan0."
ifconfigWith the adapter name known, we can then use Airmon-ng, making the final command to type airmon-ng start wlan0 to start the adapter in monitor mode. This will also change the name of the adapter, so run ifconfig again to check the new name. It should be something like "wlan0mon" in Kali.
airmon-ng start wlan0
Found 3 processes that could cause trouble.
If airodump-ng, aireplay-ng or airtun-ng stops working after
a short period of time, you may want to run 'airmon-ng check kill'
PID Name
508 NetworkManager
607 wpa_supplicant
8250 dhclient
PHY Interface Driver Chipset
phy0 wlan0 ath9k Qualcomm Atheros QCA9565 / AR9565 Wireless Network Adapter (rev 01)
(mac80211 monitor mode vif enabled for [phy0]wlan0 on [phy0]wlan0mon)
(mac80211 station mode vif disabled for [phy0]wlan0)Observe Nearby Devices
Once Probequest is installed and our card is in monitor mode, we can type probequest in a terminal window to see the primary commands.
probequest
usage: probequest [-h] [--debug] -i INTERFACE [--ignore-case]
[--mode {RAW,TUI}] [-o OUTPUT] [--version]
[-e ESSID [ESSID ...] | -r REGEX]
[--exclude EXCLUDE [EXCLUDE ...] | -s STATION [STATION ...]]The most basic command we can pass to Probequest to start seeing probe frames is as follows:
probequest -i wlan0monWith this simple command, Probequest will start listening in on the current channel. As you'll notice in the output, the information is also checked against a definition list to determine the manufacturer of the devices transmitting nearby.
[*] Start sniffing probe requests...
Mon, 23 Jul 2018 04:06:38 PDT - xxxxxxxxxxxxxxxxx (Onkyo Corporation) -> ATT5qEg4lg
Mon, 23 Jul 2018 04:06:38 PDT - xxxxxxxxxxxxxxxxx (Onkyo Corporation) -> ATT5qEg4lg
Mon, 23 Jul 2018 04:06:39 PDT - xxxxxxxxxxxxxxxxx (Apple, Inc.) -> CrossCamp.us StaffBased on the information we see, the identity of systems operating nearby should become clear. Expect to see brands that are printers, cell phones, IoT devices like Sonos and Nest Cams, and other nearby devices.
[*] Start sniffing probe requests...
Mon, 23 Jul 2018 04:06:38 PDT - xxxxxxxxxxxxxxxxx (Onkyo Corporation) -> ATT5qEg4lg
Mon, 23 Jul 2018 04:06:38 PDT - xxxxxxxxxxxxxxxxx (Onkyo Corporation) -> ATT5qEg4lg
Mon, 23 Jul 2018 04:06:39 PDT - xxxxxxxxxxxxxxxxx (Apple, Inc.) -> CrossCamp.us Staff
Mon, 23 Jul 2018 04:06:44 PDT - xxxxxxxxxxxxxxxxx (Hewlett Packard) -> TLLP_GUEST
Mon, 23 Jul 2018 04:06:44 PDT - xxxxxxxxxxxxxxxxx (Hewlett Packard) -> TLLP_GUEST
Mon, 23 Jul 2018 04:06:49 PDT - xxxxxxxxxxxxxxxxx (Nest Labs Inc.) -> CrossCamp.us Staff
Mon, 23 Jul 2018 04:06:49 PDT - xxxxxxxxxxxxxxxxx (Nest Labs Inc.) -> CrossCamp.us Staff
Mon, 23 Jul 2018 04:06:49 PDT - xxxxxxxxxxxxxxxxx (Nest Labs Inc.) -> CrossCamp.us Staff
Mon, 23 Jul 2018 04:06:49 PDT - xxxxxxxxxxxxxxxxx (Nest Labs Inc.) -> CrossCamp.us Staff
Mon, 23 Jul 2018 04:06:50 PDT - xxxxxxxxxxxxxxxxx (AzureWave Technology Inc.) -> WILDKATT
Mon, 23 Jul 2018 04:06:50 PDT - xxxxxxxxxxxxxxxxx (AzureWave Technology Inc.) -> WILDKATT
Mon, 23 Jul 2018 04:06:50 PDT - xxxxxxxxxxxxxxxxx (AzureWave Technology Inc.) -> WIFIBBA825
Mon, 23 Jul 2018 04:06:50 PDT - xxxxxxxxxxxxxxxxx (AzureWave Technology Inc.) -> WIFIBBA825
Mon, 23 Jul 2018 04:06:50 PDT - xxxxxxxxxxxxxxxxx (Hewlett Packard) -> TLLP_GUEST
Mon, 23 Jul 2018 04:06:50 PDT - xxxxxxxxxxxxxxxxx (Hewlett Packard) -> TLLP_GUEST
Mon, 23 Jul 2018 04:06:56 PDT - xxxxxxxxxxxxxxxxx (Hewlett Packard) -> TLLP_GUEST
Mon, 23 Jul 2018 04:06:56 PDT - xxxxxxxxxxxxxxxxx (Hewlett Packard) -> TLLP_GUEST
Mon, 23 Jul 2018 04:06:59 PDT - xxxxxxxxxxxxxxxxx (Onkyo Corporation) -> ATT5qEg4lg
Mon, 23 Jul 2018 04:06:59 PDT - xxxxxxxxxxxxxxxxx (Onkyo Corporation) -> ATT5qEg4lg
Mon, 23 Jul 2018 04:07:02 PDT - xxxxxxxxxxxxxxxxx (Hewlett Packard) -> TLLP_GUEST
Mon, 23 Jul 2018 04:07:02 PDT - xxxxxxxxxxxxxxxxx (Hewlett Packard) -> TLLP_GUEST
Mon, 23 Jul 2018 04:07:15 PDT - xxxxxxxxxxxxxxxxx (Hewlett Packard) -> TLLP_GUEST
Mon, 23 Jul 2018 04:07:15 PDT - xxxxxxxxxxxxxxxxx (Hewlett Packard) -> TLLP_GUEST
Mon, 23 Jul 2018 04:07:18 PDT - xxxxxxxxxxxxxxxxx (Apple, Inc.) -> CrossCamp.us Staff
Mon, 23 Jul 2018 04:07:19 PDT - xxxxxxxxxxxxxxxxx (Onkyo Corporation) -> ATT5qEg4lg
Mon, 23 Jul 2018 04:07:19 PDT - xxxxxxxxxxxxxxxxx (Onkyo Corporation) -> ATT5qEg4lgIf we want to be more specific, we can also use Probequest's -e and -s flags to exclude or only include devices calling for a particular network, respectively.
Cast a Wider Net
Sometimes, devices operating on another channel than the one we are scanning on will be missed by Probequest running by itself. This isn't desirable, so we can use another program to set our wireless card to hop around frequently and increase our chances of stumbling upon new devices nearby.
While running Probequest, open a new terminal window. To cause our network card to begin scanning, type the following Airodump-ng command.
airodump-ng wlan0monThis will open Airodump-ng and start switching the card between networks. You can minimize this window, then watch new devices appear in the Probequest window. As soon as I did this in our test setup, new IoT devices began appearing.
Mon, 23 Jul 2018 04:16:36 PDT - xxxxxxxxxxxxxxxxx (Sonos, Inc.) -> Sonos_dAQ4JQp4duS2hT8gqvKEQehK9c
Mon, 23 Jul 2018 04:16:38 PDT - xxxxxxxxxxxxxxxxx (Hewlett Packard) -> TLLP_GUEST
Mon, 23 Jul 2018 04:16:38 PDT - xxxxxxxxxxxxxxxxx (Hewlett Packard) -> TLLP_GUEST
Mon, 23 Jul 2018 04:16:43 PDT - xxxxxxxxxxxxxxxxx (Hewlett Packard) -> TLLP_GUEST
Mon, 23 Jul 2018 04:16:50 PDT - xxxxxxxxxxxxxxxxx (AzureWave Technology Inc.) -> WILDKATT
Mon, 23 Jul 2018 04:16:50 PDT - xxxxxxxxxxxxxxxxx (AzureWave Technology Inc.) -> WILDKATT
Mon, 23 Jul 2018 04:16:54 PDT - xxxxxxxxxxxxxxxxx (Hon Hai Precision Ind. Co.,Ltd.) -> unconfigured
Mon, 23 Jul 2018 04:17:02 PDT - xxxxxxxxxxxxxxxxx (Hewlett Packard) -> TLLP_GUEST
Mon, 23 Jul 2018 04:17:02 PDT - xxxxxxxxxxxxxxxxx (Hewlett Packard) -> TLLP_GUEST
Mon, 23 Jul 2018 04:17:02 PDT - xxxxxxxxxxxxxxxxx (Hewlett Packard) -> TLLP_GUEST
Mon, 23 Jul 2018 04:17:02 PDT - xxxxxxxxxxxxxxxxx (Hewlett Packard) -> TLLP_GUEST
Mon, 23 Jul 2018 04:17:08 PDT - xxxxxxxxxxxxxxxxx (Hewlett Packard) -> TLLP_GUEST
Mon, 23 Jul 2018 04:17:08 PDT - xxxxxxxxxxxxxxxxx (Hewlett Packard) -> TLLP_GUEST
Mon, 23 Jul 2018 04:17:08 PDT - xxxxxxxxxxxxxxxxx (Sonos, Inc.) -> Sonos_dAQ4JQp4duS2hT8gqvKEQehK9c
Mon, 23 Jul 2018 04:17:13 PDT - xxxxxxxxxxxxxxxxx (Apple, Inc.) -> CrossCamp.us Staff
Mon, 23 Jul 2018 04:17:13 PDT - xxxxxxxxxxxxxxxxx (Apple, Inc.) -> CrossCamp.us Staff
Mon, 23 Jul 2018 04:17:14 PDT - xxxxxxxxxxxxxxxxx (Onkyo Corporation) -> ATT5qEg4lg
Mon, 23 Jul 2018 04:17:14 PDT - xxxxxxxxxxxxxxxxx (Onkyo Corporation) -> ATT5qEg4lg
Mon, 23 Jul 2018 04:17:15 PDT - xxxxxxxxxxxxxxxxx (Sonos, Inc.) -> Sonos_dAQ4JQp4duS2hT8gqvKEQehK9c
Mon, 23 Jul 2018 04:17:16 PDT - xxxxxxxxxxxxxxxxx (Nest Labs Inc.) -> CrossCamp.us Staff
Mon, 23 Jul 2018 04:17:20 PDT - xxxxxxxxxxxxxxxxx (Hewlett Packard) -> TLLP_GUEST
Mon, 23 Jul 2018 04:17:20 PDT - xxxxxxxxxxxxxxxxx (Hewlett Packard) -> TLLP_GUESTWith this broader net established, a hacker can use this output to trigger an action when a specific device is present. To do this, you can do something like using the -o output flag to save only probe frames from one device to an output file, then have a program check the data every few seconds for new entries. When one is found, you can program something to happen, knowing that the target device is nearby.
Attempt a Takeover
After locating devices nearby, you may find devices that are broadcasting an ESSID that belongs to an open network. You will recognize these ESSID's because they belong to popular coffee shops, hotels, and other places where there is public Wi-Fi. If you identify an ESSID that you suspect is public, you can potentially use it to stage a MiTM attack. Because a device will not connect to a network with a password automatically unless the network has the same password, this will only work on open networks or on networks with a password you already know.
If deciding to do this, there are many tools available to create fake APs, including Airgeddon. While we won't revisit creating an evil AP in Airgeddon in this guide, you can check out our how-to below on creating a fake AP with Airgeddon.
The only significant change to our previous guide on Airgeddon is that instead of creating a fake network from one nearby, you can copy the ESSID from the probe frame and create an open Wi-Fi network with the same name the target device is calling for. If your target connects, then you can proceed to scan the device to learn more about it.
This can include the device network name, which is often the user's name in iOS devices. You can also do all the standard evil MiTM things like phishing pages and sniffing the packets coming out of the device to learn about software and apps they are running. While this attack only works against a percentage of devices, it can also be amplified by broadcasting the ESSIDs of common free networks.
Probe Frames Can Track You Even When Your Wi-Fi Is 'Off'
My research into probe frames has shown that they can be used to identify and track devices even with their Wi-Fi turned off over 800 feet away. What this means for users is that smartphones or laptops can give away your presence and even allow a hacker to write software that reacts specifically to your presence.
Because of the way Wi-Fi enabled devices to search for networks to join, it's possible for even greater security risks to emerge when these probe frames include information like the name of networks which have no password set that the device trusts. This allows an attacker to take over the data connection of the target device with no warning for the user.
If you want to protect yourself from this kind of snooping, you also need to disable a-GPS, or Wi-Fi assisted GPS, which also uses probe frames to get a better fix on your location. If a-GPS is off and your Wi-Fi is turned off too, then you should be safer against these threats.
You can also go into your list of saved networks and delete any networks that don't have a password because broadcasting the names of these networks will decloak your device and cause you to connect automatically. In general, it's not worth the risk for the convenience.
As a last note, having a "hidden" Wi-Fi network will cause your device to always be sending probe frames searching for it by name, so be warned if you're trying this ill-advised attempt at security that you're actually just making all of your Wi-Fi enabled devices incredibly easy to track and tie to you, in spite of your device's attempt to randomize your MAC address. MAC address randomization doesn't really help if everything you own is always screaming for the same hidden network.
I hope you enjoyed this guide to understanding and using probe frames to track Wi-Fi enabled devices! If you have any questions about this tutorial or probe frames, feel free to leave a comment or reach me on Twitter @KodyKinzie.
- Follow Null Byte on Twitter, Flipboard, and YouTube
- Follow WonderHowTo on Facebook, Twitter, Pinterest, and Flipboard
Cover photo and screenshots by Kody/Null Byte

























Comments
Be the first, drop a comment!