Last Friday's mission was to accomplish solving HackThisSite, realistic 2. This second mission in a series of realistic simulation missions was designed to be exactly like situations you may encounter in the real world, requesting we help a friend take down a racist hate-group website.
These missions are for everyone here, and you can join at any time. Your experience level doesn't matter. HackThisSite is a free, legal and safe practice ground for aspiring hackers wanting to test their knowledge on something real. We have full permission to exploit their servers, and we even get point rewards for it. In order to trump this mission, we need to find access to the administrator control panel.
Realistic 2
When we start this mission, we get a greeting from another person inquiring for our hacker-abilities.
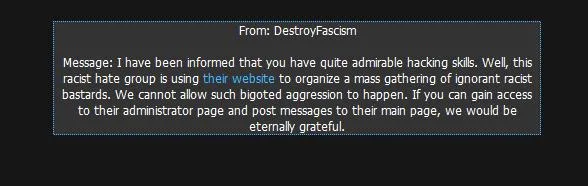
When we click the link in the message, we are brought to our target site. Upon initial inspection, the page may appear to be simple and errorless. However, if you view the page source and scroll down, you will notice something interesting.
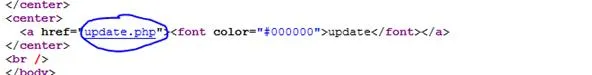
This means that somewhere on the page, there is a link with a font color of black. The link is called update, so let's check it out. If we highlight the whole page using ctrl + a, we will see the hidden link become visible. Click it.

You will be brought to a login page that asks for a password. If we look at the page source, all we get is a page link to update2.php, which only leads to the failed login page. How can we manipulate this? Let's try a SQL injection to bypass the password authorization by giving it a clause that is always true.
' or 1=1--
Enter that in the username, password field, or both. You will bypass the authorization and be brought to the mission's completion page.
Want more Null Byte?
Image via HackThisSite
























Comments
Be the first, drop a comment!