Last Friday's mission was to accomplish solving HackThisSite, realistic 3. The third mission in a series of realistic simulation missions was designed to be exactly like situations you may encounter in the real world, requesting we help a friend restore a defaced website about posting peaceful poetry.
These missions are for everyone here, and you can join at any time. Your experience level doesn't matter. HackThisSite is a free, legal and safe practice ground for aspiring hackers wanting to test their knowledge on something real. We have full permission to exploit their servers, and we even get point rewards for it. In order to trump this mission, we need to find a way to get access to the original source code and restore the website to its former state.
Realistic 3
The request for our hacking skills this time comes from a peace poetry enthusiast.
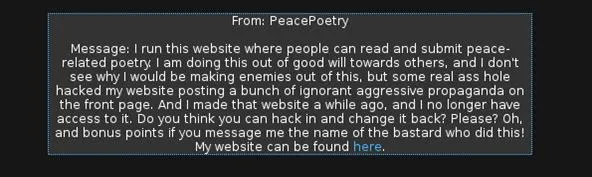
When we click the link in the message, we are brought to the defaced peace poetry site. If we explore the source code carefully, we can find a comment from the hackers.
![]()
So, if we trim the URL and add oldindex.html to it, we are brought to the old page. Logic tells us that the next step would be to find the exploit the hackers used and restore the page the same way, since the exploit existed in the old site.
After some exploration in the sites source code, you will find in the submit poetry section a vulnerable piece of code that can paste over files on the server. This is because instead of automatically renaming files with the same name, it pastes them directly over the old one. We can confirm this by visiting the URL in the form action. It automatically adds the poetry, even without submitting content. So by naming a file index.html and adding the oldindex.html page source to the comment, we can "deface" the site to its original state.

Want more Null Byte?
Photo by worthwhiletreasure
























Comments
Be the first, drop a comment!