This is it! That last basic mission. Last Friday's mission was to accomplish solving HackThisSite, basic mission 11. This final mission in the basic series was made to give us the skills and a place to apply our Apache server knowledge. This will teach us how to traverse through awkward and custom directory structures.
These missions are for everyone here, and you can join at any time. Your experience level doesn't matter. HackThisSite is a free, legal and safe practice ground for aspiring hackers wanting to test their knowledge on something real. We have full permission to exploit their servers, and we even get point rewards for it. To beat this final mission, we needed to traverse the Apache directories and search for an available password file. This requires us to know some Apache configuration
Basic Mission 11
When we start this mission, we get something a bit different from the usual.

To start, first we need to figure out what exactly is happening here. If you refresh the page multiple times, you will see that the song name changes.

After a while of this, a pattern forms. Google the song name and see who they are by. You will see they are all "Elton John" tunes. With a little clever thinking, try appending the letter 'e' for Elton onto the URL.
http://www.hackthissite.org/missions/basic/11/e/
This will bring us to a directory listing with another folder, "l". As you can guess, these directories are going to spell "elton". When you traverse along that path and reach the end, you will hit a roadblock. A blank page. No source code or anything. So what do we do?
In Apache, file view permissions in a directory can be manipulated with an .htaccess file. So if we append that to the URL...
http://www.hackthissite.org/missions/basic/11/e/l/t/o/n/.htaccess
We get...
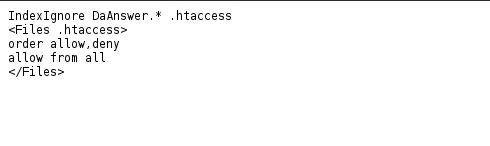
This tells us that the directory listing is blocking a file called "DaAnswer" from our view. Delete .htaccess and append "DaAnswer" to the URL. Oh my, we've reached another riddle.
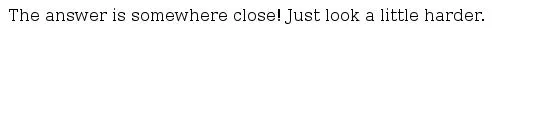
This part is simply a play on your logic. The password is simply whatever the script tells you it is. As you can see, my password is "somewhere close".
Want more Null Byte?
Image via fingerprint-security
























Comments
Be the first, drop a comment!