Last Friday's mission was to accomplish solving HackThisSite, basic mission 10. This mission teaches us how to use JavaScript to manipulate cookies on poorly coded cookie-based authorization.
These missions are for everyone here, and you can join at any time. Your experience level doesn't matter. HackThisSite is a free, legal and safe practice ground for aspiring hackers wanting to test their knowledge on something real. We have full permission to exploit their servers, and we even get point rewards for it. This week's mission on HackThisSite was to try to manipulate the login page in some way to log in as the administrator.
Basic Mission 10
We are greeted upon starting the mission.
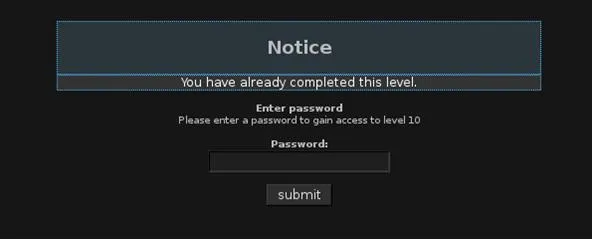
To exploit this, we can use the hint found on the mission introduction. JavaScript knowledge is recommended. So we can make an educated guess that JavaScript is involved in some way. After a bit of exploring, we discover that the page is using a cookie-based authorization by injecting this JavaScript into our URL bar:
javascript:alert(document.cookie)
We see that there is a cookie set, with the authorization set to "no". So that means we need to set it to yes.
javascript:alert(document.cookie="level10_authorized=yes");
Click the login button to be greeted with a successful login. This make the login form think that we have logged in previously with the correct user credentials, so it welcomes us right on in.
In order to protect against this, they should make sessions unique, use a cookie system that makes logins expire, or use cookies that are hashes rather than a boolean "You're in, you're out" approach.
Want more Null Byte?
Image via hashtagsocialmedia
























Comments
Be the first, drop a comment!