In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.
Bug Bounties & the Way Things Are Supposed to Work
Depending on the type of behavior, a bug can be quite valuable to discover, and software companies try to encourage bug reporting by offering to pay IT professionals and hackers a "bug bounty" of up to several thousand dollars to those who find them.
However, if these bugs are kept secret from the vendor, they become zero-day exploits for organizations like the CIA, or for oppressive governments around the world. Vault 7 on WikiLeaks reveals a culture wielding incredible power by hoarding these exploits at the expense of everyday citizens who rely on vulnerable infrastructure to run their lives. These "superpowers" give criminals and government agencies the option to "skip" legal, constitutional, and technical questions faced by their behavior.
Zero-day exploits are secret bugs, which can be processed into cyberweapon payloads that governments or criminals can use if no one discovers or fixes them. Companies offer bounties of up to a few thousands dollars for serious, newsworthy bugs, but with governments paying far more to keep exploits secret, hackers can either cash in a zero day for a huge payment or do the right thing for a fraction of the reward.
Today, hackers are offered far more to keep bugs a secret for truly valuable exploits, particularly ones that compromise privacy, enable espionage, and violate human rights. While some rewards miles from United Airlines might be alluring to an aspiring hacker, an exploit allowing tracking of international travel patterns might be worth real cash to a cyber-arms broker or government agency.
Bugs as Zero-Day Exploits & Why They're So Valuable—Obama Policy
There's a saying about artillery that applies to cyberweapons: "If the enemy is in range, so are you." It doesn't take a lot of common sense to realize an exploit won't remain secret if you try warn some people about it but not others, leaving Americans just as exposed as the intended targets.
The revelation of the advanced capabilities of the NSA badly damaged faith in American tech companies. In response, the Obama administration acknowledged that it was possibly not a great idea to have all these great weapons that rely on zero-day exploits in devices American infrastructure runs on. The administration, in the interest of national security, agreed to release critical bugs to vendors to enable the "hardening" of American devices and infrastructure.
The Vault 7 leaks show a culture that directly contradicts that position, leading some security researchers to take selling zero-day exploits as a foregone conclusion. Many companies have sprung up that couldn't care less about the bounties offered by software companies, such as French company Vupen, run by Chaouki Bekrar. When they attend hacking competitions, they keep the most valuable exploits for themselves.
"We wouldn't share this with Google for even $1 million," Bekrar told Forbes. "We don't want to give them any knowledge that can help them in fixing this exploit or other similar exploits. We want to keep this for our customers."
The leaks show the CIA went against the administration policy, choosing instead to hoard exploits in a growing cyberwarfare capabilities arms race between the US, China, and Russia. These weapons aim to cause casualties, damage, and destruction with a new type of warfare that has never been possible to wage before. Hoarding these zero days has real world consequences for users of these compromised devices, fueling a black market in cyberweapons that is impossible to control.
The Rise of Private Military Contractors Continues into Cyberwarfare Companies
In war, PMCs (private military contractors) have been providing cost-saving value for governments since the invasions of Iraq and Afghanistan. Companies like Blackwater offered to solve problems the US government needed solved, and this has caused and explosion in the private arms market.
The legal showdown prompted by the FBI's demand to Apple to produce iPhone malware drew national attention, but was suddenly resolved with a payment to an outside cybersecurity company. Just like that, a private contractor made over a million dollars to circumvent a legal process for the FBI. In fact, this is pretty common, with private cyberweapon marketplaces doing as much as $100,000,000 annually in sales.
This incident shed light on a growing trend of cyber mercenaries where companies specialize in weaponizing zero-day exploits for whoever pays them to. Like traditional arms brokers, the best paying customers are often those looking to do something illegal, criminal, or in violation of human rights. Groups like Hacking Team have been widely accused of enabling human rights abuses and selling cyberweapons to whoever will pay them, putting anyone with vulnerable devices at risk.
These weapons are known to proliferate and turn up domestically, trickling down to the civilian market as "spouse tracking" or "catch my spouse cheating" spyware to enable harassment, stalking, extortion, and other illegal activity. In particular, journalists and vulnerable people are routinely targeted by these less-elegant exploits of common vulnerabilities. But for hackers wanting to get paid, it's often more profitable to sell interesting bugs to spies than to worry about end users affected by the vulnerabilities.
The Growing Arsenal of Weapons Targeting an Increasingly Connected World
As our lives become increasingly influenced by connected devices, it has never been easier to cause damage through the weaponized use of exploits. Once limited to taking down websites or erasing data, cyberweapons in 2017 have the capability to kill people and destroy physical infrastructure.
A tense political situation has cause an explosion in the grown of cyberweapons, with the military pumping government funds into the private sector to create new and more lethal weapons. Unlike nuclear or conventional weapons, these weapons can be copied, transported, and used across the globe in a matter of seconds. The political value of these weapons, and the dazzling scope of power they provide, has lead organizations like the CIA to create new and more interesting ways to make people miserable through the devices around them.
Between the black and grey cyberweapons markets of zero-day exploits, and the government funded creation of more, these tools are growing increasingly sophisticated and powerful in scope. Thanks to the explosion in malware availability, users of modern technology globally are vulnerable to weapons that allow political control, extortion, and even national acts of sabotage or war.
In recent attacks in the Ukraine, Russia has deployed increasingly sophisticated cyberweapons in conjunction with disinformation attacks that deny citizens the right to an impartial understanding to the world around them.
The ability to present a person with false information from a supposedly trusted source and invade their private life represents a level of control and manipulation that can be abused and automated to a terrifying degree. From invasive data collection, to targeted disinformation campaigns, to automated exploits of zero-day vulnerabilities, most users are unprotected against this kind of interference in their everyday lives.
When Governments Stockpile Vulnerabilities, Private Citizens Lose Around the World
The cyberweapons of WikiLeaks' Vault 7 offer a snapshot into a world where the flaws in our devices are big-ticket items to spies, dictators, and jealous lovers who are willing to pay to cheat the system. An increasingly tense geopolitical situation is causing governments to stockpile cyberweapons capable of destroying critical infrastructure and causing loss of life, while quietly testing and refining these weapons in global conflicts. These weapons only work when governments pay to keep knowledge of these bugs secret and cyberweapons dealers accept payment to turn a blind eye to how their tools are used.
Everything from our traffic patterns to our understanding of what time it is relies on technology today. As we advance into a world of further automation and trust in the devices around us to run our lives and shape our understanding, we confront a the new reality of where technology fits into our lives today.
Rather than safeguarding the world's growing reliance on technology by disclosing and advancing development of zero-day vulnerabilities, the worlds governments are stockpiling methods of committing a new frontier of attacks against populations never targeted by such sophisticated weapons before.
Governments Buy, Swap & Lose Cyberweapons Used to Commit Human Rights Violations for Fun & Profit
Users and developers of cyberweapons insist that the capacity is needed to track down terrorists and criminals using encryption and other methods that make them hard to trace. Copying these weapons, however, takes only a moment, and NSA tools developed to invade computer systems were recently lost only to resurface on the black market.
Criminals can buy software to spy on government employees, shut down power stations, disable metro fare collectors, or encrypt millions of dollars worth of data thanks to the diligent efforts of the NSA and private contractors working to satisfy government contracts.
As shown by the CIA leaks, the casual way in which government agencies have began to share purchased or developed exploits increases the proliferation of highly sophisticated malware and worsens the risk of it falling into the wrong hands. Vault 7 documents show that the US and UK governments pay to join in on the fun of exploiting vulnerable devices under the promise to not warn vulnerable users in their own country or use the weapon on each other's citizens—even though they could.
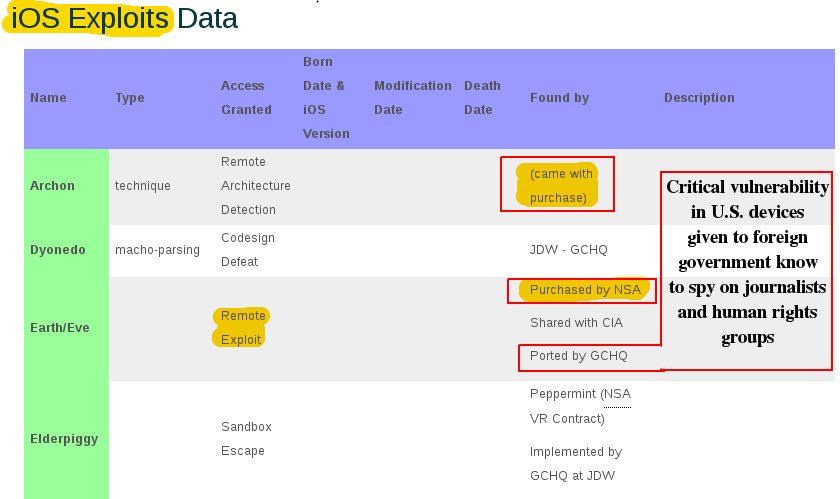
Critical vulnerability in devices used by US citizens shared with a foreign government.
The grey market purchase of a zero-day exploit in the Apple showdown prevented a potential constitutional confrontation that could have had far-reaching implications for digital privacy in America. Today, the cyber gray and black market provides governments a relief valve to attack the technology we rely on for privacy without outlawing encryption itself.
As these weapons grow in power and scale, we as hackers need to debate and decide whether contributing to today's stockpile of cyberweapons is worth putting the people around us, or around the world, at risk of having these tools used against them.
- Follow Null Byte on Twitter and Google+
- Follow WonderHowTo on Facebook, Twitter, Pinterest, and Google+
Cover image adapted from Igor Serazetdinov/123RF and SashaSV/Pixabay


























Comments
Be the first, drop a comment!