Welcome back, my greenhorn hackers!
Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.
As a result, we will start anew with Kali and I'll try to develop this series in a logical and sequential manner that a forensic investigator would follow. I will also include units in here on anti-forensics, or ways you can stymie the forensic investigator.
Although, I know you are all anxious for me to show you how to evade detection, you first need some background in the tools and techniques of the forensic investigator. Without that background information, you will be left at the whim of ever changing and improving forensic techniques. Only by understanding the tools and techniques of the forensic investigator can you stay ahead of the game and, more importantly, stay out of custody.
Kali Forensic Tools
Kali has a number of forensic tools built into its toolbox. Although many of these tools are outstanding in Kali, there are many more forensic tools available and I will not limit myself to those included in Kali, but we will start with these.
We can find those tools at Kali Linux -> Forensics.
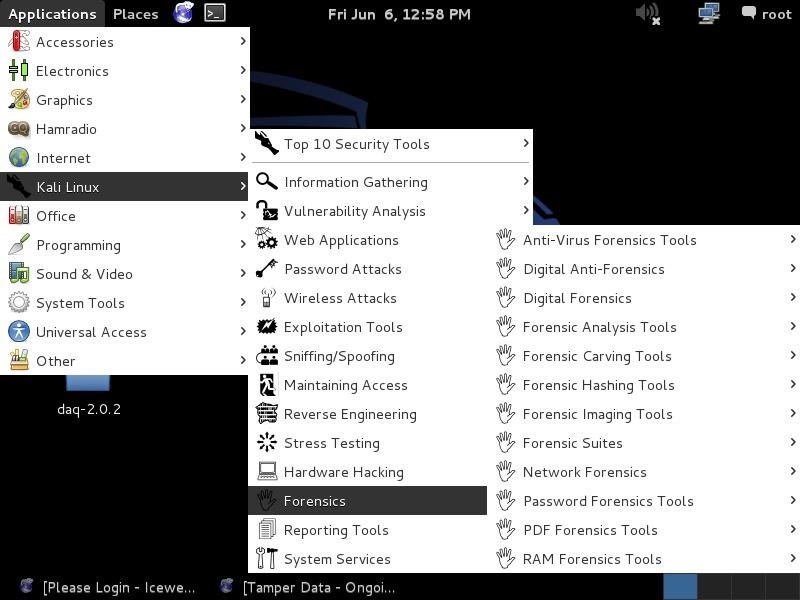
As you can see, Kali subdivides its forensic tools into multiple categories. These include the following.
- Anti-Virus Forensic Tools
- Digital Anti-Forensic Tools
- Digital Forensics
- Forensic Analysis Tools
- Forensic Craving Tools
- Forensic Hashing Tools
- Forensic Imaging Tools
- Forensic Suites
- Network Forensics
- Password Forensics Tools
- PDF Forensic Tools
- RAM Forensic Tools
Each one of these areas includes multiple tools for doing similar tasks. I will try to demonstrate the best tools and include the theory behind the techniques.
Commercial Forensic Tools
There are a large number of companies that produce commercial forensic tools, primarily for law enforcement use. The two dominant players are EnCase and the Forensic Tool Kit (FTK). These forensic suites tend to be all-encompassing, with tools for all types of cases and investigations. In addition, they have case management and reporting capabilities that go far beyond those of the open-source tools.
This doesn't mean they are better tools, but it does mean they easier to use (after all, they are designed for law enforcement officers) and they format and manage the information better than some of our open source tools. We will examine these tools a bit in this series, but digital forensics is better learned using open source tools as you really need to know what and how you are doing with these tools, rather than simply point, click, and print.
Areas That We Will Address Here
In the real world (anyone ever been there?), Linux systems are attackers and Windows systems are victims. As a result, we will focus our attention on understanding what artifacts the attacker (us?) might leave behind on a Windows system.
To be able to benefit from this discussion and tutorials, I have to assume that you have functional Linux knowledge and skills, a good understanding of TCP/IP and networking, and have reasonable Windows skills. In addition, to grasp the work of the forensic investigator, you will need to understand the close-grained anatomy of a Windows filesystem (usually NTFS) and the Windows registry.
Few hackers, and for that matter, few system admins, have that deep understanding of the NTFS and the registry, so I will have separate tutorials on those two subject matters.
I really hope you enjoy this series and find it useful, whether you want to make a career of catching hackers or simply want to remain free to hack another day.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























9 Comments
of course we do enjoy this series..! more pls :)
nice topic, i'll be very interested
I know this is kind of off topic but i just found null byte a few days ago and want to install linux on my flash drive as a dual boot would you prefer i get back track 5 or kali? I have been reading your beginner tuts and you say back track, however when i come to more recent posts you are using kali.
Welcome to Null Byte!
Since Offensive Security discontinued downloads of BackTrack, we were forced to "upgrade" to Kali. As a result, I recommend that you install Kali.
Hope to see you around here.
Thanks for the info i look forward to learning a lot from your tuts on here!
Yo!yo! The honorable OTW..I am very glad to finally be your site member and be able to ask questions...buddy i am very new to Linux,I recently downloaded and installed Kali Linux on my laptop and it's running pretty cool no hustles....and I have been following all your posts since the beginning of time....But there is never a day you mentioned of Kali Linux being able to hack a Blackberry smartphone like we can with android devices......IS HACKING A BB SMARTPHONE POSSIBLE?
Many Thanks in Advance
Dracula
Absolutely! Nothing is unhackable!
Glad you finally joined our world. Looking forward to hearing more from you.
OTW
Lol!!Magnificent...I like that one "nothing is unhackable" won't you please help on Hacking a BB smartphone?
Excellent series, massively helped me getting started with Kali. Just waiting 3 hrs for dcfldd to work it's magic and then the Autopsy can begin :) - Thanks
Share Your Thoughts