Welcome back, my tenderfoot hackers!
As you know, Metasploit is an exploitation framework that every hacker should be knowledgeable of and skilled at. It is one of my favorite hacking tools available.
Metasploit enables us to use pre-written exploits against known vulnerabilities in operating systems, browsers and other applications and place a rootkit/listener/payload on the target system. These payloads are what enable us to connect to the victim system and use it as our own after we have exploited a vulnerability in its system. In this tutorial, we will look exclusively at the payloads built into Metasploit.
Metasploit has many types of payloads we can leave on the target system. We are most familiar with the generic/shell/reverse_tcp and the windows/meterpreter/reverse_tcp payloads, having used those in multiple hacks already. In this guide, we will look at such things as how the payloads work, how Metasploit categorizes the payloads, and what the types of payloads are. I hope this understanding will help you to better choose the appropriate payload for your hack.
Let's take a closer look at these payloads in Metasploit.
Step 1: Fire Up Kali Linux & Open Metasploit
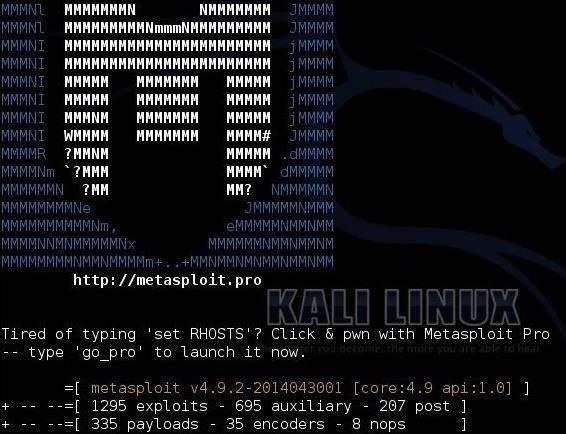
When we open the Metasploit console in Kali Linux, we immediately see that Metasploit lists the number of exploits, auxiliary modules, post exploitation modules, payload modules, encoders, and nops.
In the screenshot below, notice that there are 335 payloads in the current version of Metasploit (yours may be slightly different based upon your version of Metasploit). This is a huge number of payloads that can be used for multiple situations.
When we type:
msf > show payloads
Metasploit lists all 335 payloads as below.
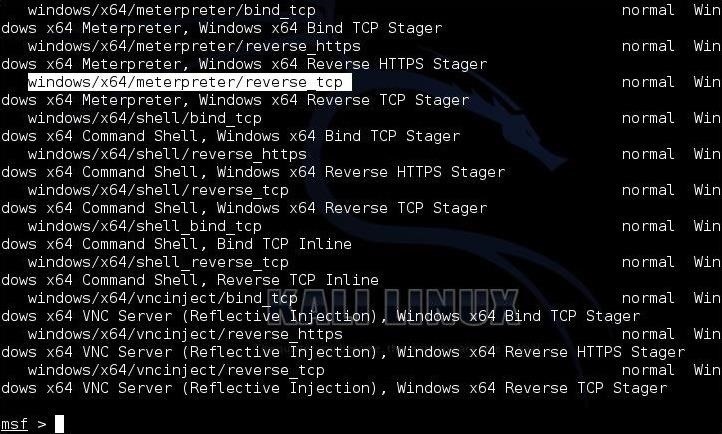
Step 2: Types of Payloads
Among these 335 payloads in Metasploit, there are 8 types of payloads.
Inline
These payloads are a single package of exploit and payload. They are inherently more stable, but because of their size, they can't always be used in small vulnerable memory areas.
Staged
These payloads essentially are able to fit into very small spaces and create a foothold on the system and then pull rest of the payload.
Meterpreter
Is the all powerful payload that we most often want on a victim system. It works by .dll injection and resides entirely in memory, leaving no trace of its existence on the hard drive or file system. It has a number of specific commands and scripts developed for it, enabling us to largely work our will on the victim system.
PassiveX
This payload is for use when firewall rules restrict outbound traffic. In essence, it uses ActiveX through Internet Explorer to hide its outbound traffic and evade the firewall by using HTTP requests and responds just as any browser would.
NoNX
In some CPUs, there is a built-in security feature called DEP (Data Execution Prevention). In Windows, it is referred to as No eXecute, or NX. The idea behind this security feature is to keep from data making its way to the CPU and being executed. The NoNX payloads are designed to evade this safety feature of modern CPU's.
Ord
These type of payloads work on nearly all Windows operating systems. These are extremely small, but somewhat unstable. They are dependent upon loading a .dll (dynamic link library) into the exploited process.
IPv6
These payloads, as their implies, are designed to work on IPv6 networks.
Reflective DLL Injection
These payload modules are injected directly into the target process while it is running in memory, thereby never writing anything to the hard drive and leaving little or no evidence behind.
Step 3: Payload Modules
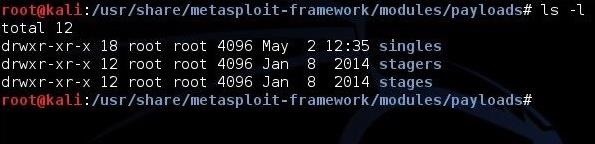
If we look in the Metasploit directory the Linux terminal in Kali, we can see that Metasploit categorizes its payloads into three different types. Obviously, the eight types above are consolidated into these three directories in Metasploit.
kali > cd /usr/share/metasploit-framework/modules/payloads
kali > ls -l
Staged
Staged payloads use tiny stagers (see below) to fit into small exploitation spaces. In other words, if the victim's system exploitation buffer or other memory area is very small and only allows a small amount of code to be executed, first a small stager is placed in the memory area. The stager then "pulls" the rest of the payload after this foothold is made on the victim system.
These larger staged payloads include such complex payloads as the Meterpreter and VNC Injection, both of which include large and complex code. Generally, a staged payload will split the name of the payload between a "/", such as in the payload windows/shell/tcp_bind. The "tcp_bind" is the stager (see below) and "shell" is the staged.
Unfortunately, this convention is not used consistently in Metasploit, so one often has to go to the "info" section of the payload or find the directory it is in to determine if it is a staged payload.
Stagers
Stagers are the small payloads whose only job is to fit into small memory area and then "pull" the larger staged payload along. They kind of "plant the flag" on the victim and then enable the larger payload to be loaded.
Singles
Often referred to as "inline payloads," singles are self-contained units that do not require a stager. They are generally more stable and preferred, but many times the code is too large to for the vulnerable memory area on the victim system.
Let's now take a look inside that singles directory.
kali > cd singles
kali > ls -l
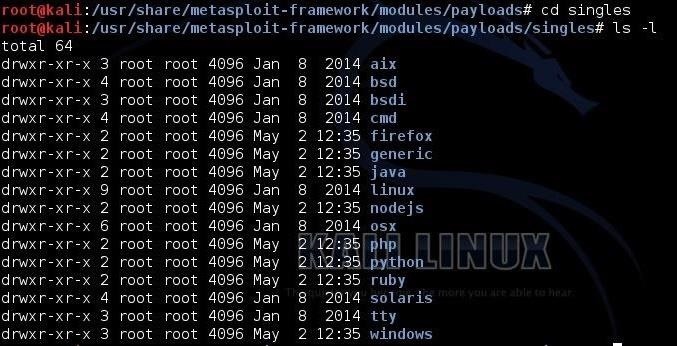
As we can see, the singles are broken down by vulnerable platform. If we want to see the singles available for the Windows platform, we simply type:
kali > cd windows
kali > ls -l
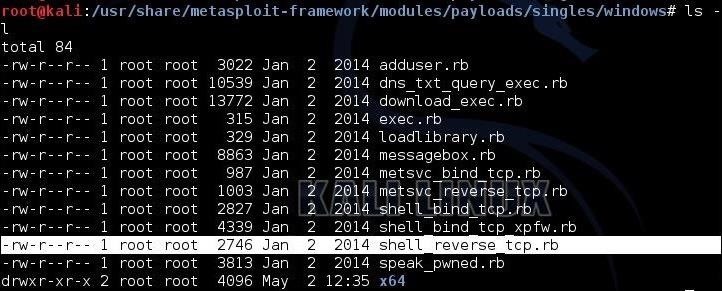
Inside this directory we can see all the singles payloads available for Windows. I have highlighted one of these payloads, shell_reverse_tcp, that we have used in many of our hacks.
Payloads are key part of the Metasploit infrastructure and provide us with access once the exploit has been completed. The better we understand them, the better we will be as a hackers.
That's it for now. Make sure to check back in on my Metasploit Basics series for more tutorials on Metasploit. So, keep coming back, my tenderfoot hackers!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















16 Comments
i learned a lot.
i have a couple questions though.
how do you pronounce staged and stager.
also all of your posts are about kali and backtrack.
would you say bugtraq is ok to use?
because this is the one i prefer.
thanks
Chris:
I have to use just one hacking distribution and Kali is the most popular. You certainly can use bugtraq but the location and the ways the tools work will be slightly different.
OTW
At the end of the day, you can only exploit and allow payloads to work if a certain port is open, and/or if a system is using very specialized software with bugs (for instance, it is difficult to exploit Win7 directly, but you can exploit Joomla Spider Contacts--which isn't exactly common software).
My question is, what does a hacker use
-after they are adept with Metasploit and are skilled enough to use other, more advanced tools
-when exploiting ports isn't an option (ex. only 445 is open, but they have an up-to-date MS-DS system)
Thanks, and by the way, I absolutely love your How-to's!
Prince:
Port 445 is NOT the only option. There are many other vulnerabilities in Windows and the applications that run on Windows.
OTW
Um, I'm not sure how to delete comments, so I'm replacing it with this.
where can we get a documentation of what each of the 300 or so exploits do in particular and how and when they can be chosen?
i have some question.
Dark Knight:
You are a hacker. Everything we use is malicious.
Metasploit is owned and managed by Rapid7, a Boston based security firm. Anyone can write an exploit, but Rapid7 decides which get included.
what i meant was if i used a exploit, will it try to destroy the target(like deleting every files)?
So the Rapid7 will check every exploits before it adds, right?
Unless the exploits say that is their goal, then no, they will not
Good Day,
I am new here and am trying for port forwarding on my router.
I hve tried almost everything but it is still not working.
YOU ALL ARE MASTERS HERE.
Can Someone please help me to achieve Port Forwarding on WR150 Binatone Router Or Any alternative for it.
My service provider says port forwarding is not possible in my case as it needs a lot of stuffs.
Please Help....
:'(
Try navigating to all of these sites:
192.168.0.0
192.168.0.1
192.168.1.0
192.168.1.1
Only one of them will work, once you are on that site, try all of these credential combinations:
admin:admin
admin:password
admin:12345
One of these should work, if not a quick search on Google of "Default router configuration passwords" should present you with a list of passwords you can try.
Once you are on the router configuration page, click around on the site until you see a page called "Port Forwarding". Than, add your IP, which you can find by on Windows/Linux, navigating to command prompt and entering ifconfig. On macOS/OS X go to System Preferences and click network, than your IP should be under turn Wi-Fi off. After you do this choose the port you want, as well as the IP, and enter them in the Port Forwarding fields, select apply, and...
Your done
I am using virtual box.Permission denied to open payload dir?
Great tutorial @OccupyTheWeb
How can i open ports of kali linux if i am using mobile hotspot
You can use serveo.net but I believe their website is down for a while. You can use NGrok instead.
Share Your Thoughts