In the first part of this series, we learned about darknets, as well as how they came about. But these patches of forgotten Internet are not the oasis of free information you might think. Despite being hidden—or just harder to come across—these networks are no more safe then anywhere else on the 'clear' Internet. The nature of networking and routing means your location is always known in server logs. It only takes one phone call to your ISP with your IP address to obtain both your physical address and a search warrant along with it. Therefore, a method must be used to cloak your action from those ever-growing prying eyes.

Enter Tor and Onion Routing
Simple traffic analysis and deep packet inspection can give up what you are sending, where you are sending it, where it is coming from and who it is going to. This is performed by your ISP to enforce data limits or anti-spam and piracy measures, and it can be performed by anyone with access to your network. This could be the FBI outside in a parked van or even your neighbor after he cracked your wireless password.
Tor works on the idea of onion routing. Let's take a more in-depth look at the idea behind this, as it's critical to how the Tor (and i2p) network operates. Each machine that's running the Tor service is running a Tor router on their network. Each of those routers (which we'll refer to as "nodes" from now on) work by forwarding traffic from other random nodes.

When you wish to send some data on the network, your node calculates a path though all the running nodes, and wraps your data in that many layers of encryption. When each of these random nodes receives your packet, they can only decrypt the layer assigned to them (only they have the key). As such, each node can only see the previous node a packet came from and the next node the packet should be sent to. At no point can the nodes dig deeper into the packet. They can only peel away the layer assigned to them. In this way, each layer is peeled away, one at a time, giving us the term onion routing.
The figure below illustrates how each layer of the "test" packet is peeled away one at a time on its way to the web server.
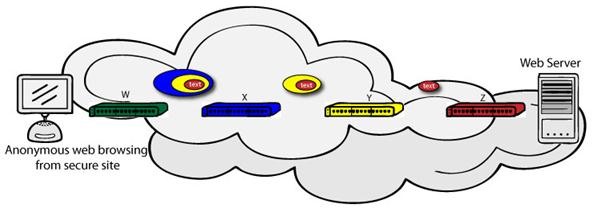
Exit Nodes and Escaping Content Filtering Firewalls
Inside the Tor network, there is a wide range of hidden content, a lot of which is not for the weak of heart. This is because Tor allows you to create your own internal website, known as a Tor Hidden Service. We'll dive deeper into those services in the next part of this series. For now, let's go over how Tor allows you to browse the web anonymously.
Normally you send your request to a web server using the normal HTTP port of 80. The server then reads what you need, and sends it over to you. By the very nature of this system, the server needs to know your router's IP address to communicate back to you, and this is contained in the header of the each packet sent. Essentially, it's connecting what you are doing on the Internet to where you live.
The problem occurs when a company or ISP peeks into those packets and blocks access based on their contents. You have seen examples of this at your high school computer lab and maybe even in your office at work. Websites and content that are not wanted can be filtered out before it even reaches you. Sometimes this is undertaken on a national level, like in China and Iran, by filtering directly at the ISP.
To reach regular websites on the 'clear' Internet, some Tor nodes are configured as exit nodes, which route traffic in and out of the Tor network. This hides who you are from the police, the web server, your ISP and anyone else listening in. As far as any of them know, you are the exit node! Also, as Tor uses its own port and encrypts the traffic, your content restrictions can be bypassed with ease.
Even as these exit nodes are often in other countries, there are still methods of tracking you down. None the less, putting a few layers between yourself and the world can never hurt. At the end of this article, I will explain the most efficient way to obtain the software you need and provide you a few links to start your adventure with.
Why Aren't We All Using Tor Then!?
Tor has a few serious issues with it that do need to be addressed. The most critical is a lack of end-to-end encryption. This means anyone who can sniff the traffic from an exit node can see EVERYTHING. They still have to trace packets back and forth to determine a location, but all the encryption is gone. Any personal info you transmitted will be wide open for the stealing. You can negate this by wrapping your data in a presentation-layer protocol like SSH, but that's not always an option.
Tor also does not provide protection against end-to-end timing attacks. If your attacker can watch the traffic coming out of your computer, and also the traffic arriving at your chosen destination, he can use statistical analysis to discover that they are part of the same circuit and locate you. This problem is tied into the one above in a way, as well.
Why Should I Use It?
Tor is still very effective at outsmarting firewalls and port scanning, and though more advanced, tunneling SQL injections. Tor is secure enough to communicate with and even better if you wrap that data in application-layer encryption beforehand. It is not 100 percent, but it's better than just rolling dice and hoping no one is watching.
Over the years, the model has been improved upon and added to. If you are looking for the next step up from Tor, you need to enter the world of i2p. In my next article, I will explain how they're similar and how they differ, sometimes drastically.
tl;dr
Tor is great at browsing the web anonymously and accessing the network's hidden services. The best way is to download the browser bundle directly from the website. There is no installation required, and you can even put it on a USB drive for mobile use as en emergency proxy!
Simply download and extract the archive, navigate to its directory and:
$ ./start-tor-browser
That's it! The Tor/Vidalia bundle includes the script that starts and connects to the Tor proxy and a modified version of Firefox that is set up to be secure and work with Tor out of the box. This includes disabling Javascript, Flash and any other add-ons that can be tricked into giving up your real IP.
Below is a list of links for a few Tor hidden services to start you off.
- dppmfxaacucguzpc.onion - The TorDIR, a listing of various hidden services, some on and offline.
- kpvz7k12v5agwt35.onion - The Hidden Wiki, a listing of more links and services. Be careful here.
- eqt5g4fuenphqinx.onion - Core.Onion, a great intro for new users.
Questions? Concerns? Leave me a comment or drop by our IRC channel and say hello.
UPDATE: Continue to Part 3 to learn about how to set up your own Hidden Services...
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























15 Comments
Is there an increased risk of having your machine compromised by using Ip2 or Tor? i.e. Does their use open up vulnerabilities that otherwise wouldn't exist? Nice article, by the way.
People can see you are transmitting a ton of encrypted data if they are listening, and what conclusions they come up with from that will vary. From a technical standpoint both services bind to localhost and as such, are not 'forward' facing to the open Internet.
Lol... waiting to see part 3. I was starting to wonder why I should even continue using Tor with the flaws above, until you mentioned I2P. Hats off man.. I am learning. Thank you.
Tor is useful, I think people might be taking me comments about its network the wrong way. I only mean to point out other options and reasons some might want to use them.
l2p is better? I'd like to know how.
I watched a presentation given by the two Tor (head) creators, they know their #$%@ and listening to them gave me only further confidence in Tor. Being able to sniff the exit node is an unavoidable reality of using any system like Tor. Route your tor traffic through a free VPN if you are really worried about this, but that doesn't stop the VPN from sniffing your traffic and stealing any information you enter.
Tor and I2P are very different tools, both provide anonymity but i2p is focused on the internal network where tor is focused on accessing the public web. After many comments and messages, I don't think I was overly clear about that, so my apologies. I could have perhaps explained that part better.
I advise people to never use a free VPN. Ever. They are making their money by selling your data and you should not expect them to be secure for the reasons you mentioned. I recommend I2P over Tor for communication because I2p is end to end encrypted between nodes (Tor is not) among a few other things. I2P runs into problems with a smaller network and limited routers moving traffic, but this is changing quickly.
Allen, the hidden services you write about are end-to-end encrypted in the same way I2P is. Tor cannot provide this when exiting to servers that does not support SSL, and neither can I2P.
You are 100% correct, the hidden services are good to go as the communication inside the network is encrypted.
Allen, just discovered your anonymity-darknets series, good writing! Re: part 2, It could be clearer that Tor and I2P have different goals/weaknesses. I'm looking forward to part 3!
Thanks Patrick. This was my first series here and thanks to these comments I can see a few things I could have explained better, or in greater detail. Moving forward though!
does tor completely block an Ip address or produces false ones?
Lets say you are going to visit a website. You send a request to view the page and the web server sends it to you. In this typical setting the web server has your IP address. What Tor does is adds a bunch of other routers between you and that web server. Each of those other routers can only see the IP of the router that sent it the request and the IP of where it needs to go. Once this traffic passes the exit node, and carries on to the the web server, that server only knows the IP of the exit node, not you. So, in that sense it does not block or produce false addresses, so much as it obscures your traffic to the point it can not be tracked.
For clarity sake I'l like to add a little about normal Internet routing and how it differs from Tor. All normal Internet traffic goes through a series of routers to get to it's destination. All data is transported in packets, each packet having a header that includes both the destination and source addresses (like the outside of an envelope has a destination and return address). Each router along the way receives data packets, looks at the destination addresses and passes the packets onward to the next router *not changing the source address*. Tor routers work differently. When a Tor router passes along a packet the packet has that router's address not the original source's address. The Tor network has it's own mechanisms to properly route packs between you and the Tor exit router, and as already mentioned, each Tor router only knows the addresses of the routers a packet immediately came from and the next router to which the packet will be sent, nothing more about the route.
This article s right you can never have too much encryption.
And also the Time delay factor is a minor but a considerable downside.
Anyways nice pen work..
Share Your Thoughts