Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.
If you've ever used your Gmail account to book a flight, you probably got a notification a few hours before your flight reminding you about it. Why? Because Google automatically added the flight to your calendar.
While many people would have just thought it was a nifty new feature and gone about their day, forgetting about it within minutes, this sparked an idea in the mines of the Black Hills information security team who wondered what Google was doing behind the scenes to make those events happen.
Their research led them to discover that it was not required to send an email to a target to create an event on their calendar. In fact, anyone can add an event straight from their calendar to the target's calendar, all without "inviting" or getting the approval of the target.
Today, we're going to look at how to do some basic research and execute this attack on any company that uses Gsuite. If you're not familiar with Gsuite, then think of Gmail but with the company's domain name instead of @gmail.com. First, let's analyze the emails that add these events.
How Gmail Adds Calendar Events
Naturally, the answer to this question is easy enough to find. The airline's developers have to be able to learn how to use this feature after all. Google has an entire developer page dedicated to the topic. In their own words:
Google Calendar is designed to be a helpful assistant, so that users can spend less time managing their day and more time enjoying it. You can use Schema.org markup in your emails to help Google Calendar automatically extract event details from confirmation emails for Flight, Concerts, Restaurant reservations or any other ticketed events; Calendar can then add these events to the user's calendar automatically. The events even stay updated in real time if the user's flight is delayed or when they receive an email update.
Basically, emails are just a bunch of HTML code, and with Gmail, in particular, they add the event data as Schema markup which supports both JSON-LD and Microdata. Which, of course, provides hackers with HTML knowledge interesting exploit opportunities.
Event Injection & Social Engineering
For example, an attacker could spoof a particular email when injecting events such that an employee would have an event added to their calendar by their boss with a malicious link or attachment for them. The vast majority of people are not in situations in which they can simply ignore meetings or demands of their superiors in their company, which should highly increase the likelihood such an attack would be successful.
That's one very particular example, but as the Black Hills team put it:
Injecting Google events could provide a very interesting situation for phishing users of a G Suite environment. As most users have been trained to spot phishing links in emails, and Google itself has a few protections against phishing Gmail users, we thought focusing on social engineering users through Calendar event may be more successful.
There are several unique and interesting aspects that calendar event phishing presents. First and foremost, you're able to achieve a sense of urgency which is difficult to attain in a phishing email. It doesn't take much imagination to see how this could potentially be used.
For example, the target could be led to believe there are only 10 or 15 minutes before a very important meeting. And don't forget if the target has signed into their Gsuite account on their mobile device — they'll get a handy notification on their phone as well. This urgency and panic could lead the target to click/tap on links or open documents which normally they wouldn't.
Also, as the Black Hills team alluded to since so much security training focuses on phishing emails, they may not even be suspicious of a calendar event in the first place.
Additionally, there's a social factor if a group or an entire company is targeted. All the targets will receive the same notification at the same time adding to the legitimacy of the event. This also adds the potential to position a target or targets by creating an event at a certain place and time. A hacker could potentially know where the target is going to be and use that knowledge for whatever purpose they wish or, on the flip side, they could ensure that the target is not where they normally should be.
So what steps would an attacker need to take to carry out such an attack? Let's take a look.
Find the Targets
As in any engagement, the first and most vital step is researching the target. Here the goal is to identify an individual to be the "creator" of an event and targets who are going to have that event added to their calendar. And of course, the linchpin, whether or not they're actually using the Gsuite of products.
What I'm about to show is the most basic level of an open-source intelligence (OSINT) investigation. There any number of tools readily available on GitHub to automatically gather this information and much much more.
Today, let's keep it simple and go to the least popular page on any website — but most valuable for us — the about page. While sometimes a bit tricky to find, the about page of any given organization has virtually all the information we need for this attack.
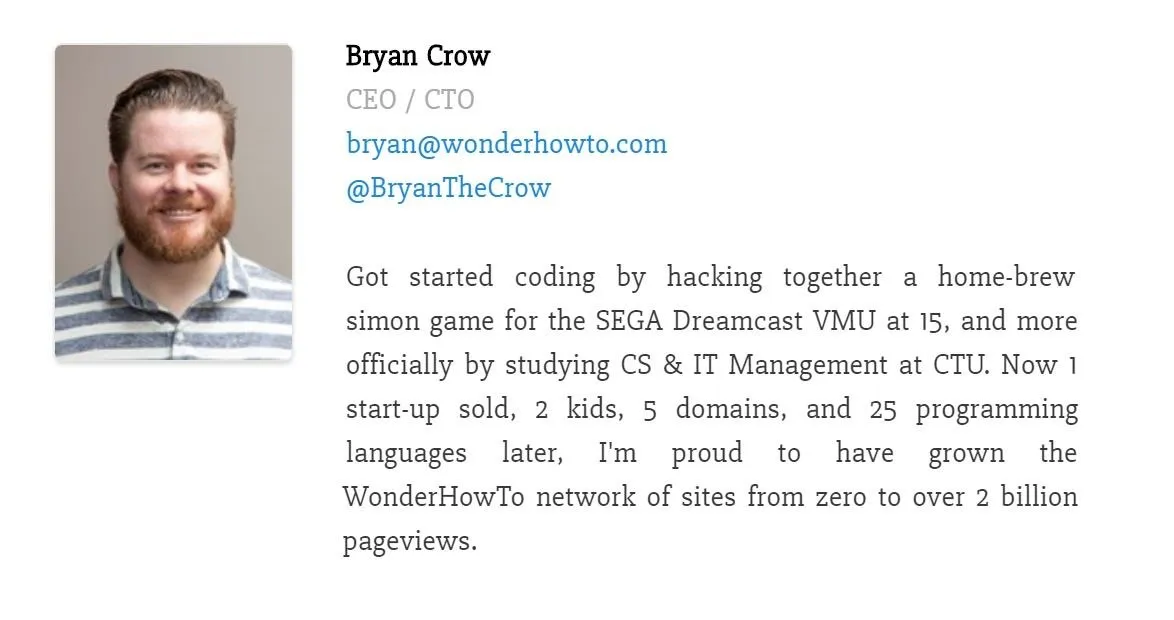
Primarily, we just need someone in a high-level position and an email. Just looking at the Null Byte about page, you can easily find who's most likely to be in charge, such as our CEO or Editors, with thier emails as well as usernames that they go by on sites such as Twitter.
It can also be a good choice to check a company's LinkedIn page, particularly if their about us is hard to find or non-existent. Furthermore, it can provide a more comprehensive list of lower-level employees who are most likely the targets of this attack. It is worth mentioning that the CEO could just as easily be targeted if it's discovered that they are very busy and use Google Calendar to remember when and where to be.
When you visit the LinkedIn page, simply click on "See jobs" near the top of the page just under the profile picture. You will have to be signed into a LinkedIn account to do this, but you can always create a quick fake account to do so.
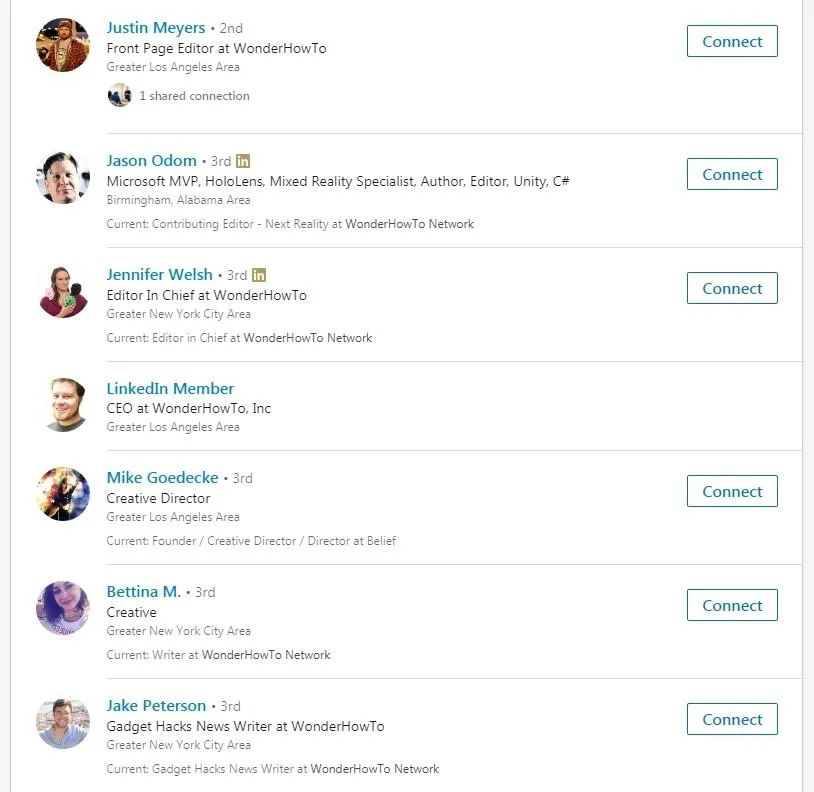
Once you're logged in, you'll be presented with a list that has a wealth of information on it. You can also get a sense for the size of a company. Obviously, this sort of attack is not going to work well in a large company such as Facebook if every single person is added to the event, nor in a smaller startup with only a handful of employees that are in constant contact with each other. This is why LinkedIn is useful in doing specific targeting.
For example, I can easily see that if I wanted to target all the Editors, I can create a list just by scrolling through and writing down the names of all the editors, and then have the Editor in Chief or CEO be the creator of an event. The more realistic the scope of the event, the more likely the target is to fall for it.
Discover if They Use Gsuite
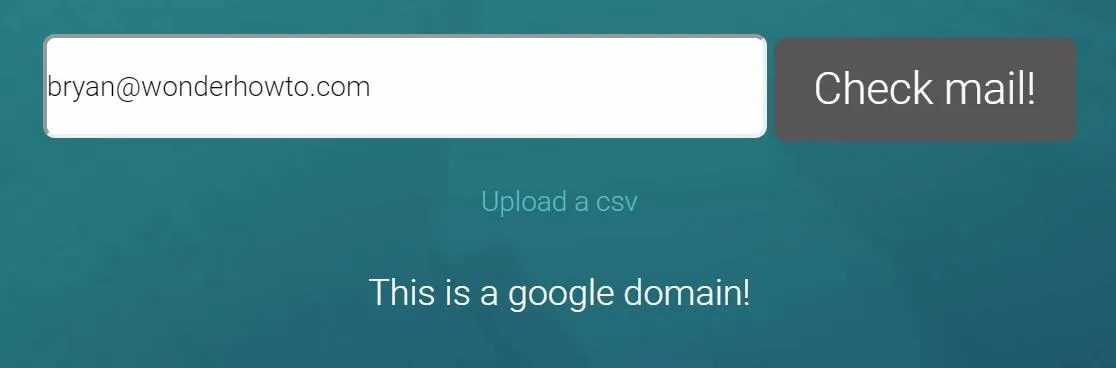
Now that we have some emails in hand, it's time to check and see if they're using Gsuite. Fortunately for us, there is a handy website to do just that — no downloading GitHub tools or anything. Go to Google Domain Tester and type in one of the emails, then click "Check mail!" If it says "This is a Google domain!" then we're ready to inject some events.
Create a Gmail Account
Now that we've done some research and know who we want the event to come from, it's time to make a fake Google account that looks like them. In this example, I'm using our CEO, Bryan. In an ideal world, we'd be spoofing the actual email address, however, for simplicity's sake, here we're making it look as if the individual creating the event, Bryan, accidentally did it from his personal Gmail account.
Go to the Google account setup page. Make sure you're signed out of your own Google account! Now, type in the name of the person you want to be hosting the event. You'll likely have to get a little creative with the username as the actual person is probably using their own name and some variations of it might also already be taken, but ideally you want to stay as close to the person's actual name (or usernames they are known to use) as possible so that the targets will recognize it.
Because we're all tech geeks around here, I tried using some leet-speak for the username but it was already taken.
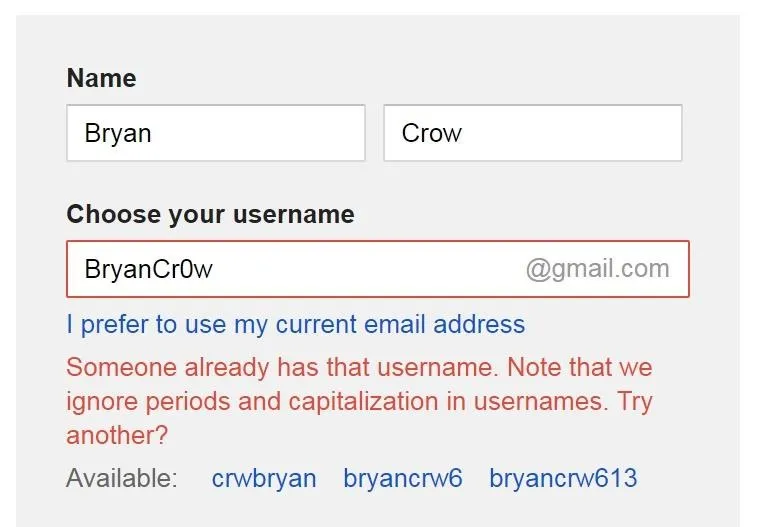
I ended up going with making Crow into Croow, but from my research, I could have also gone with BrianTheCrow, his Twitter name.
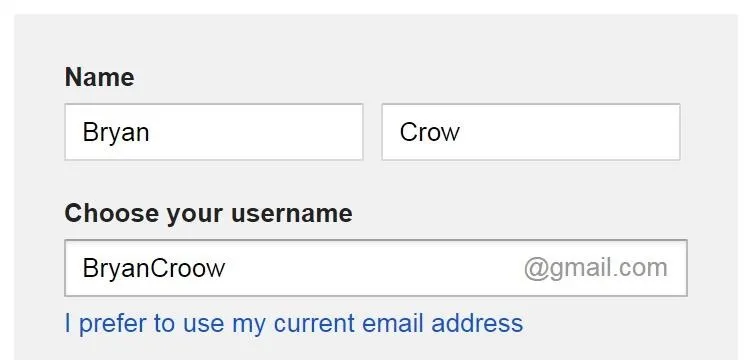
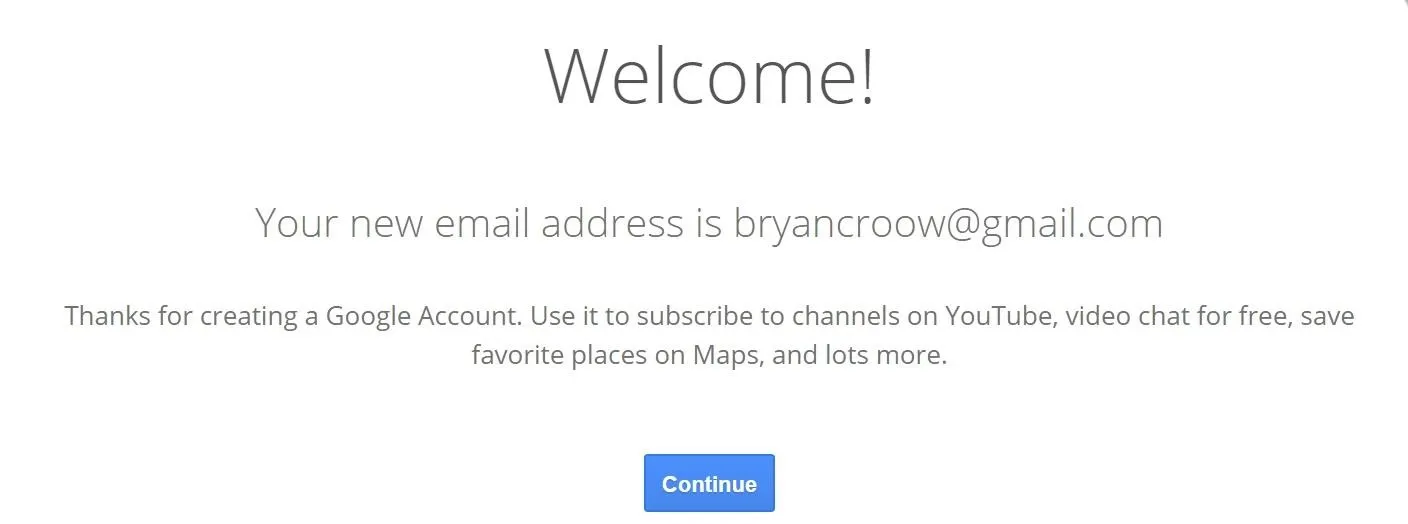
From there, create a password and fill out the remaining information as you wish — most of it can actually be left blank. Once you're all done setting up the Google account, we're ready to go to the next step.
Prepare the Payload
Now we need a payload or goal for the event we're about to create. The classics from email phishing would also work here, e.g., malicious links and documents. However, since we are using a calendar event, there are two possible goals we could have: physical goals and digital goals. Let me give you some examples.
Physical goals and payloads would be using the event text and time notifications to affect people in relation to the physical world around them. For example, getting the target to leave a place or be in a place at a particular time. A pentester who has gained access to the building but is unable to get into the target's office could use an important meeting or other critical event to lure the target to leave their office, giving the pentester physical access to the target's office for a few minutes. It sure beats pullling a fire alarm.
Additionally, the payload could be a meeting or inspection event. This would add an air of legitimacy to a social engineering attack such as gaining access to a building through a secretary ("Why, yes, I have a meeting with Bryan, just check the calendar. I'm sure it's there.") or, alternatively, if a pentester were using the classic IT man scam in a building, he could add events to the particular target's Google Calendar notifying them that someone would be coming around to work on their computer and install new software.
For the digital side of things, prepare your favorite remote administration tool (RAT) or any other exploit you wish to use. For example, we might use EvilOSX to dump the target's Chrome passwords as it's likely that anyone using Gsuite is also using Chrome.
Inject an Event
Open Google Calendar while signed in with the Google account created. Then, click on the calendar wherever you wish to create an event. In the pop-up window, click "More options."
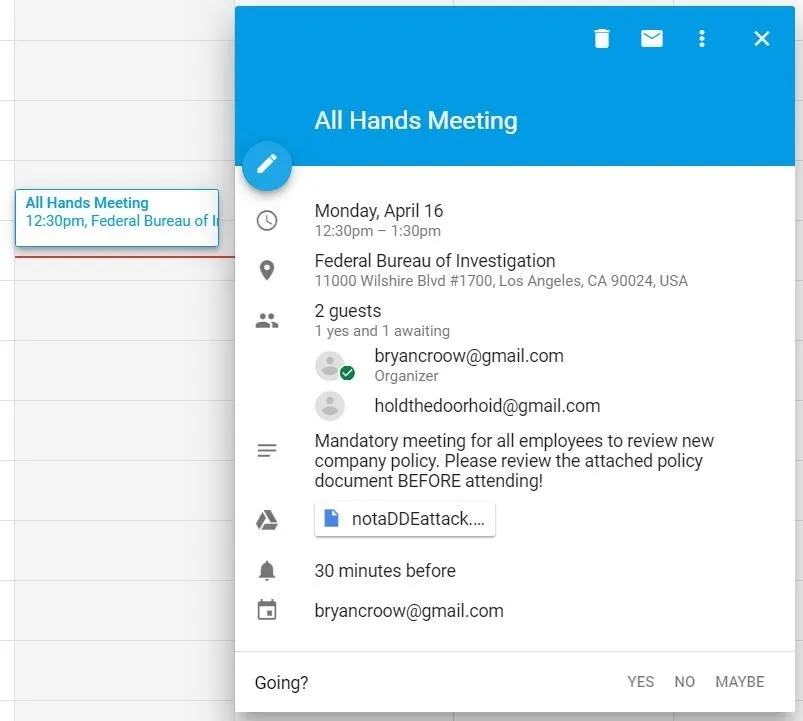
From there, tailor the event to align with your payload and goals. For this example, I've created an all-hands-on-deck meeting to review new company policies and attached a Word document with a DDE-based attack.
To the right side of the screen, under Guests, type in the target's email, then press enter to add them to the list.
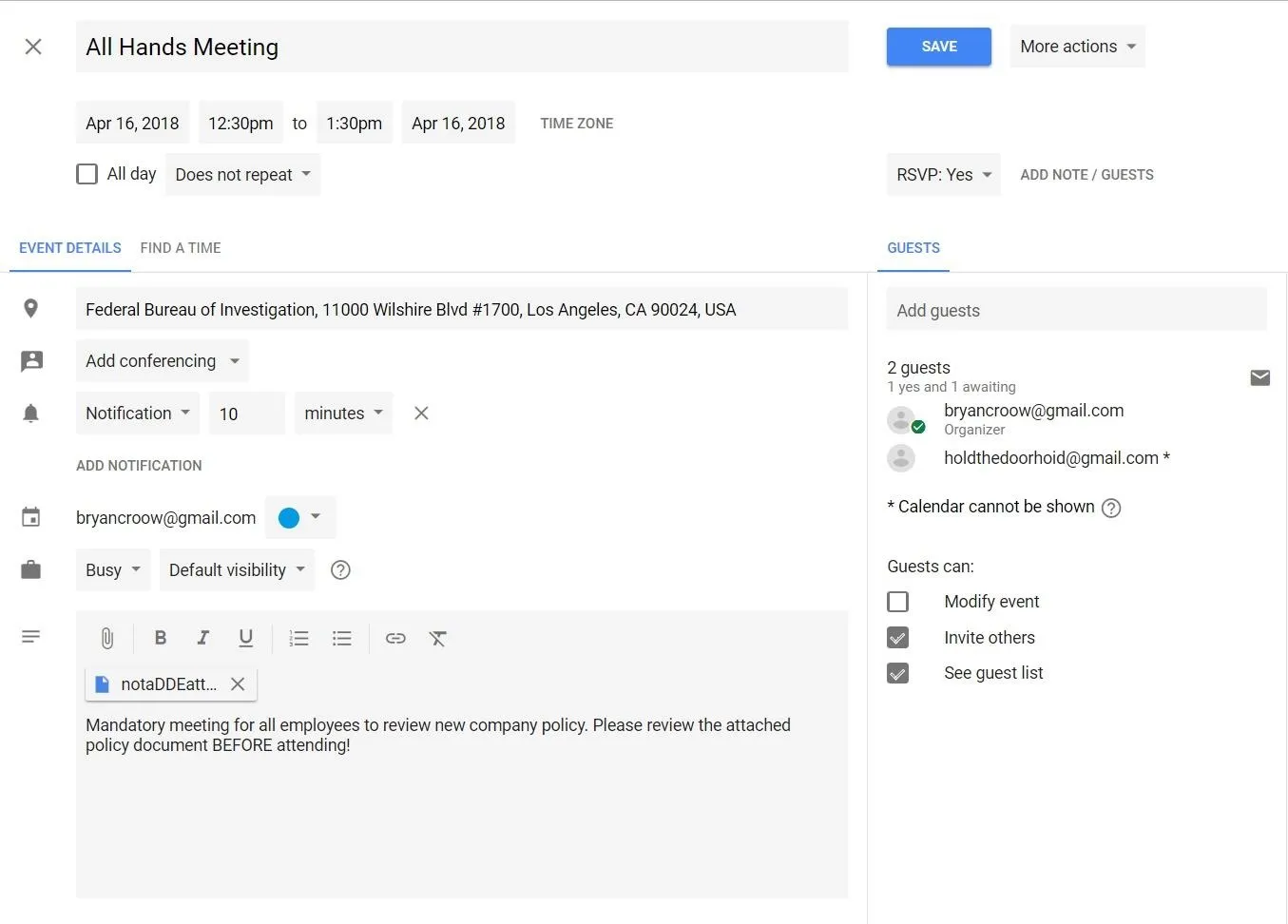
As you add guests, you may get a notification saying Google "could not resolve" the indicated guest. In my testing, the event was still added to the target's calendar, so you can disregard this message if you get it.
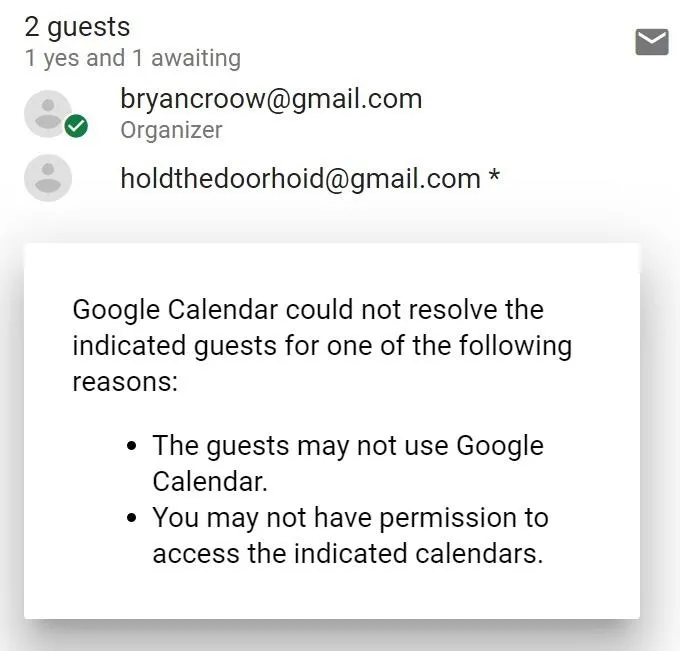
Once the guests are added and the event filled out, click "Save," and then when Google asks about sending invitations, click "Don't Send" - it will still add the event to the target's calendar, but this way a notification email doesn't show up in their inbox.
That's it! An event has been added to the target's calendar. Now just sit back and wait until the event time for results!
Protecting Yourself from Google Calendar Injections
This is one of those decision points which happens all too often in the security field of having to decide between convenience and security. Fortunately, there are a few settings you can adjust to help protect yourself without losing too much convenience. Just remember, the only foolproof method is to not use Google Calendar at all.
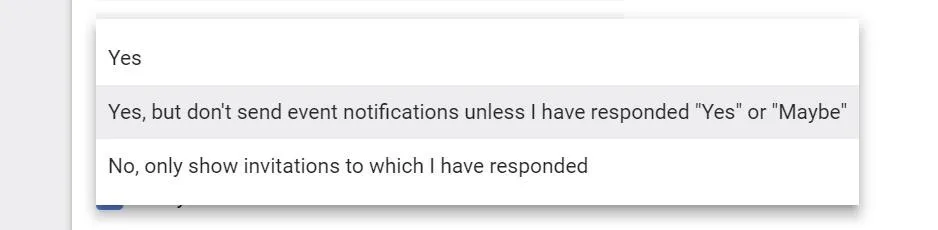
First, go to your Google Calendar Settings and find the "Event settings" section, then look for "Automatically add invitations." Click on it, then in the drop-down menu, select "No, only show invitations to which I have responded." This will protect you from attackers injecting events through Google Calendar such as we did above. But don't allow this to lull you into complacency — there is a way around this setting if the attacker goes through the Google Calendar API, which we will look at in a future article.
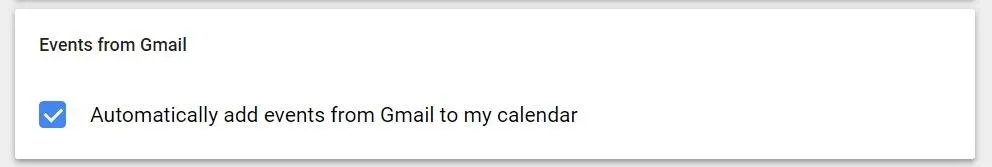
From there, scroll all the way to the bottom and look for "Events from Gmail." Uncheck "Automatically add events from Gmail to my calendar," then click "OK" on the popup warning. This will prevent emails such as the automatic flight booking we discussed earlier from being added to your calendar.
Event Injection Going Forward
Phishing emails in particular, and social engineering, in general, have always been surprisingly effective, and the addition of Google Calendar event ejection is just a natural evolution of that. Event injection gains a particular potency because of the lack of security training people have received on the subject, the sense of urgency that it invokes, and their inherent trust in Google and their calendar.
In future articles, we will look at using MailSniper to streamline the event creation process as well as how to use the Google API to circumvent the security settings we mentioned.
If you have any questions, you can ask here or on Twitter @The_Hoid.
- Follow Null Byte on Twitter and Google+
- Follow WonderHowTo on Facebook, Twitter, Pinterest, and Google+
Cover photo by Justin Meyers/Null Byte; Screenshots by Hoid/Null Byte

























Comments
Be the first, drop a comment!