Welcome, my neophyte hackers!
The aspiring hacker needs to know a bit of Linux to be successful, and probably most importantly, Linux networking. To fill that knowledge gap, I'm offering this guide on Linux networking basics.

I assume that you understand a small amount of networking concepts, things like IP addresses, MAC addresses, DNS, DHCP, etc. If not, please take some time to pick up a few networking basics. Our past admin here on Null Byte, Allen Freeman, has some really good guides you should check out:
- How IP addresses and MAC addresses work together
- A brief history on how the Net came to be
- How network packets are routed
- How everything connects today
Analyzing Networks
The most basic linux command for analyzing networks is ifconfig. It's very similar to the Windows command ipconfig. Let's take a look at it.
- ifconfig
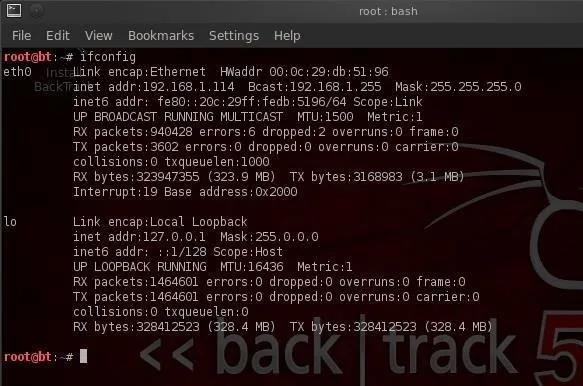
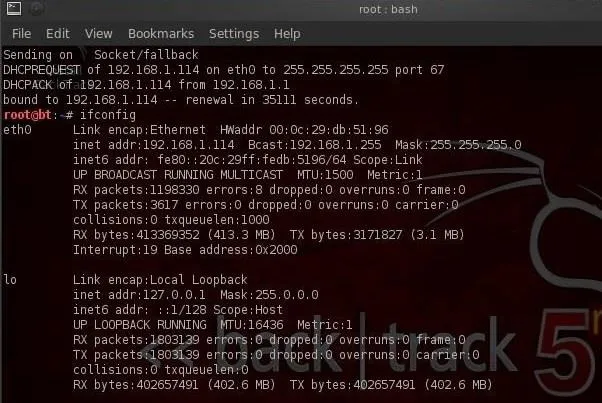
As you can see in this screenshot, ifconfig conveys a significant amount of information to the user. In the very first line, we see to the far left eth0. This is the first wired network connection, ethernet 0 (Linux usually starts counting at 0).
Following this, we see the type of network being used (Ethernet) and the hardware address (this is the globally unique address stamped on every piece of network hardware, in this case the NIC).
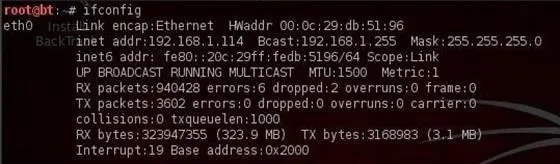
The second line then contains information of the IP address, in this case, 192.168.1.114, the broadcast address (the address to send out information to all IPs on the subnet), and finally the network mask (this is the info on what part of the IP address is network and which part is hosts). There is a lot more technical info there, but it's beyond the scope of a Linux basics tutorial.
If we look down below to what appears to be a second paragraph, we see the start of another paragraph with lo to the far left.
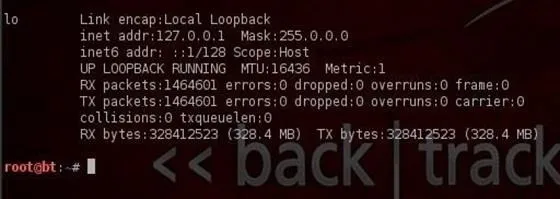
This is the loopback address or localhost. This is the address of the machine you're working on if you simply wanted to test something like a website. It generally is represented with the IP address 127.0.0.1.
Changing IP Addresses
Changing IP addresses can be fairly simple in Linux. Remember that in most cases, you're going to have a dynamically assigned address from a DHCP server. In some cases, you may need to reassign the address, especially if you're hacking. This can be useful in spoofing your IP address, making network forensics more challenging, but certainly not impossible.
We can do this by using the ifconfig command with the interface we want to assign the IP to and the IP address we want. Such as:
- ifconfig eth0 192.168.1.115
Now, when we type ifconfig, we can see that our IP address has changed to the new IP address.
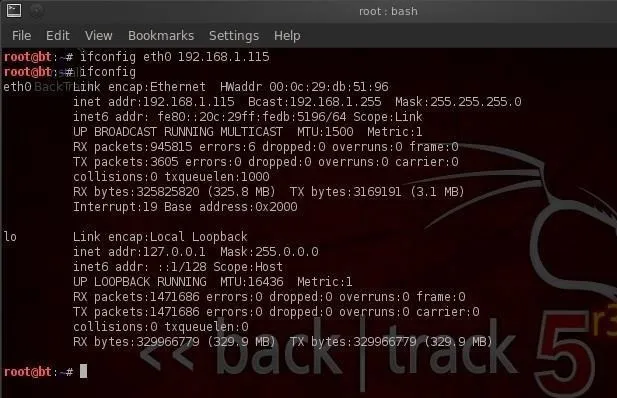
We can also change the netmask and broadcast address, if necessary, such as:
- ifconfig eth0 192.168.1.115 netmask 255.255.255.0 broadcast 192.168.1.255
DHCP (Dynamic Host Configuration Server)
Linux has a DHCP server that runs a daeman called dhcpd. It's this DHCP server that assigns IP addresses to all the systems on the subnet. It also keeps logs files of which machines had which IP addresses at which time. It's this log that is often used to trace hackers in a forensic analysis after an attack.
When I want to be assigned a new address from the DHCP server, I can simply call the server with the command dhclient (different Linux distros use different DHCP clients, but BackTrack is built on Ubuntu which uses dhclient), like this:
- dhclient
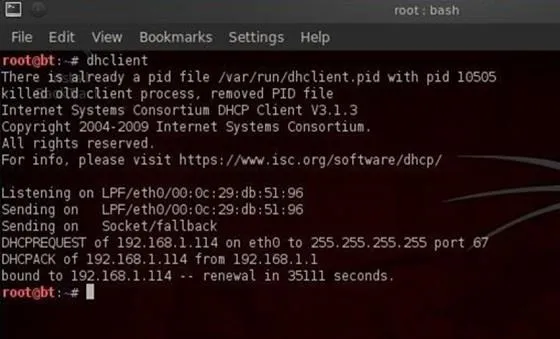
As you can see, the dhclient command sends out DHCPDISCOVER request from the default NIC. It then gets an offer (DHCPOFFER) of 192.168.1.114 from the DHCP server, then confirms the IP assignment to the DHCP server. Now, if we type ifconfig, we can see that the DHCP server has assigned a new IP address.
DNS (Domain Name Service)
DNS, or Domain Name Services, is the service that enables us to type in a domain name like www.wonderhowto.com, which it then translates to the appropriate IP address. Without it, we would all have to remember thousands of IP addresses of our favorite websites (no small task even for a savant).
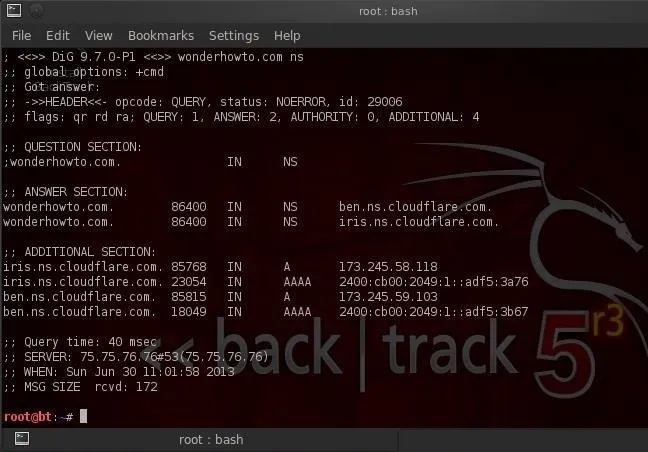
One of the most useful commands for the aspiring hacker is dig, which is the equivalent of nslookup in Windows, but offers us much more information on the domain. For instance, we digwonderhowto.com and by adding the ns option, it will display the name server for wonderhowto.com.
- dig wonderhowto.com ns
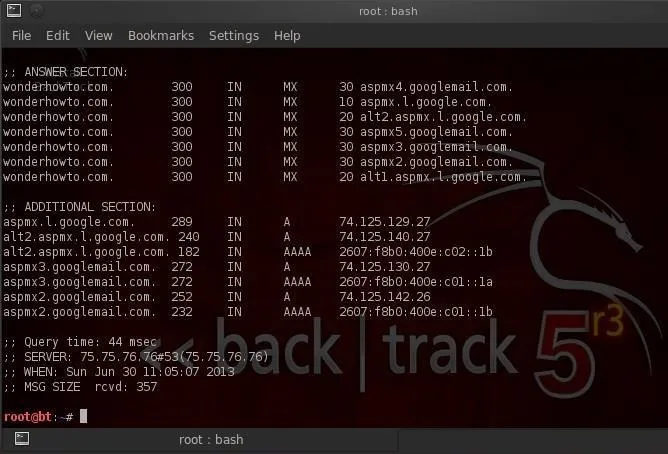
By using the dig command with the mx option, we can get info on WonderHowTo's email servers.
- dig wonderhowto.com mx
The most common Linux DNS server is the Berkeley Internet Name Domain, or BIND. In some cases, Linux users will often refer to DNS as BIND, so don't be confused. DNS or BIND simply maps individual domain names to IP addresses.
On our BackTrack system, we can point out DNS services to a local DNS server or a public DNS server. This pointing takes place in the a plain text tile named /etc/resolv.conf file. Let's open it with kwrite:
- kwrite /etc/resolv.conf
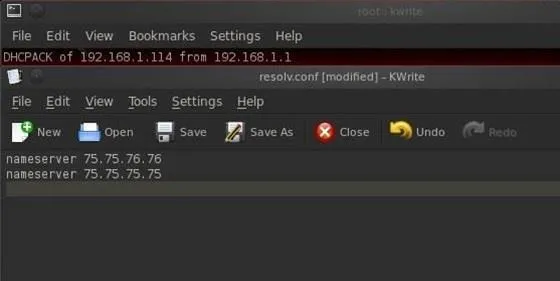
As you can see, we are pointing to two public DNS servers to provide us with DNS services. If we want to change our DNS servers or add another server, we can simply add another line to this text file and save it. The next time DNS services are required, the Linux operating system will look to the new DNS server designated in this file.
Simple, right?
In my next Linux tutorial, we will look at security and permissions, so keep coming back. If you haven't already, make sure to check out the first five parts of this series, and if you have any questions, ask away in the comments below or hit up the Null Byte forum for more help.

























Comments
Be the first, drop a comment!