Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.
A proxy hides your IP address but leaves behind some breadcrumbs, because most proxies have a cache system that will log browser history, passwords, and other data. There are some encryption options with proxies, but they aren't very helpful since there is still a log service. But these breadcrumbs are what makes proxies fast.
Since proxy servers cache webpages, they can increase the speed of downloading documents and websites because the proxy server does a local cache of previously downloaded requests from other clients first. In comparison, a VPN is a direct tunnel to the endpoint with encryption, which really slows things down.
Private Internet Access (PIA) is a popular and well-trusted VPN service starting at $2.91/month, one which we've covered before in the past for securing IoT and media devices. A VPN subscription to them also includes a PIA proxy service. Using their proxy for file-sharing allows you to download media like disk images securely without needing to route all of your traffic through a VPN, so you can still watch Netflix or browse the internet while you torrent.
In this tutorial, we will create an application-specific tunnel for downloading your content, allowing you to continue using the internet for other tasks or games uninterrupted and without extended ping times. Like mentioned before, proxy servers are faster because they do not come with encryption. PIA's proxy service does offer encryption if that's something you're interested in.
Download & Install µTorrent
µTorrent is a torrent client, which means it uses a peer-to-peer network to download files. While this is a great, fast way to download open-source software like Kali Linux disk images, it also isn't always wise to download hacking tools from your home IP address. For those wishing to download Tor or Kali Linux without ending up on a government list, a proxy can help protect your privacy.
This setup will work for many different torrent clients, but to keep this tutorial as cross-platform as possible, we will be using µTorrent. You can download the software from its website, and it should auto-select the client based on the operating system you are using. Go ahead and press the "Get µTorrent" button (the free one, obviously), and the download will start automatically.
After downloading, it's time to install. When we double-click the installer, a configuration wizard will pop up. We want to hit the "Next" button in the bottom-right corner. After that, the end-user license agreement will spring up, and so we want to "Accept" that.
It wants to install a Yahoo extension on your default web browser, and we don't want that. Go ahead and "Decline" that, and then the final installation steps will occur automatically.
Configure µTorrent
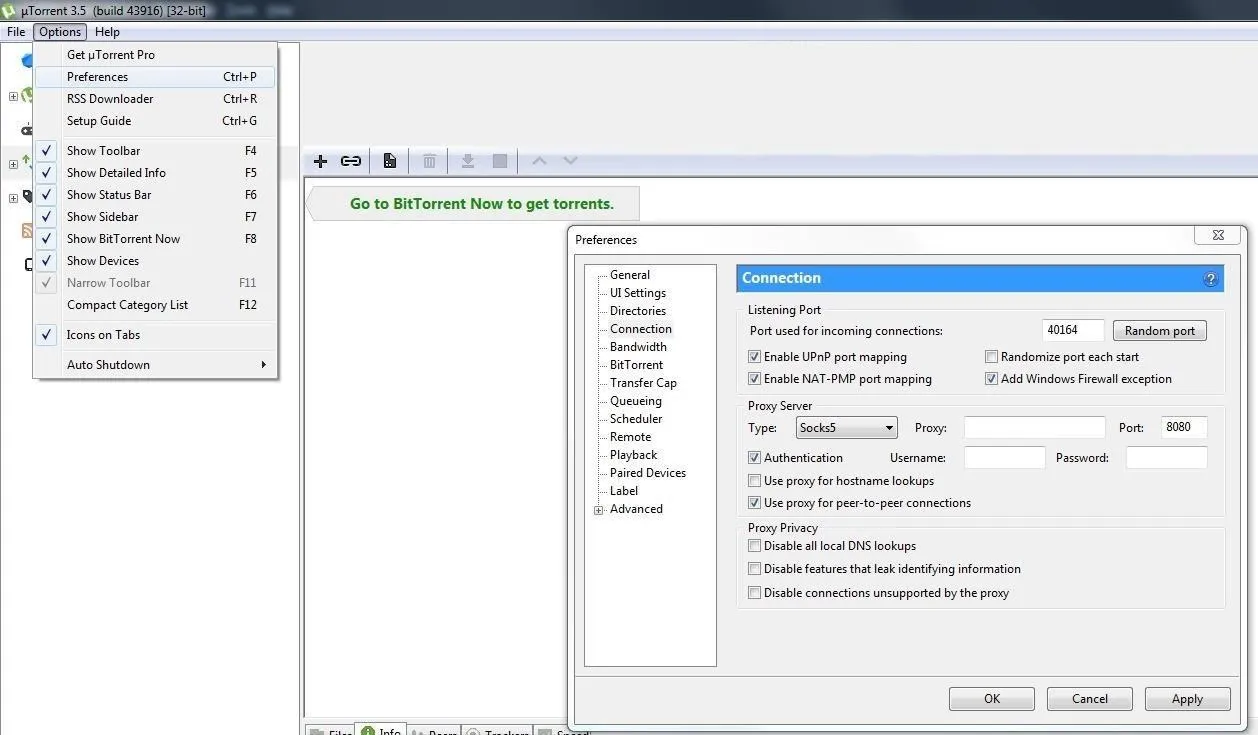
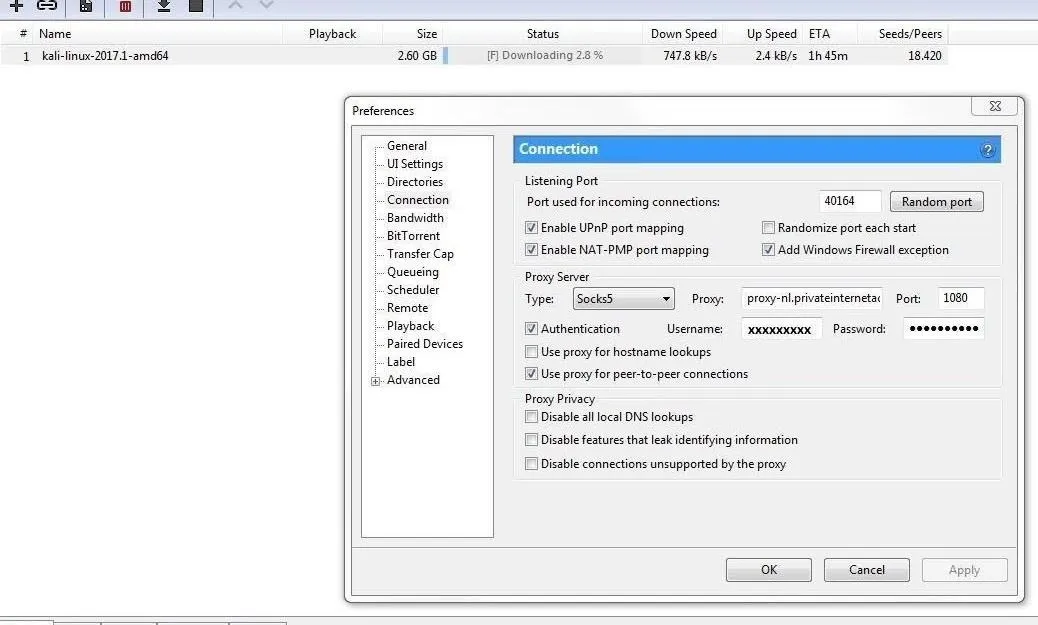
First, let's open up µTorrent. We want to click the "Options" tab and then select "Preferences" from the drop-down menu. The Preferences window will pop up, and next, we will want to click on the "Connection" tab. Once there, we will see the Proxy Server field, as seen below. It's asking for proxy credentials, so we'll need to create those first.
Generate Proxy Credentials
Let's open up a web browser and log into our PIA VPN client. After you log in, scroll down until you see the PPTP/L2TP/SOCKS Username and Password section. These username and password pairs are generated for use with PPTP, L2TP, and Proxy SOCKS connections. Write down or save the username and password for the next step.
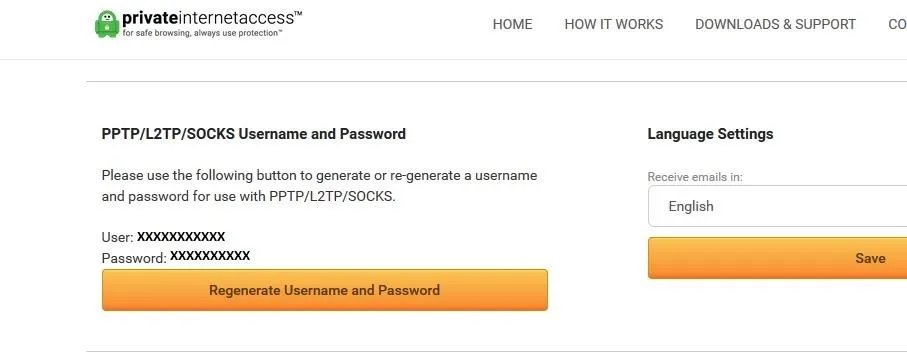
Configure the Proxy Server
Return to µTorrent's "Connection" settings, and change the Proxy Server type to "Socks5." Check the boxes next to "Authentication" and "Use proxy for peer-to-peer connections," then grab that username and password from PIA client page and stick them in the Username and Password fields under the Proxy Server section.
Next, for the Proxy field, we want to input the address "nl.privateinternetaccess.com," and for the Port number, we want to change it to port 1080. We are using this port because PIA servers assign this port to their proxy servers. Press "Apply," and then "OK."
Torrent a File via Proxy
Now, let's download our target torrent file. In this case, our target will be the free live image of our favorite pentesting OS, Kali Linux. Torrenting files is often quicker than downloading the same file from a web browser, as a peer-to-peer download isn't limited by how far the websites download server is.
You can navigate to the torrent file on the Kali downloads page. We are going to select the "Kali 64-bit" version using the "Torrent" download. A file with a name like "kali-linux-2017.2-amd64.torrent" should download.
Go ahead and either save or open the TORRENT file with the µTorrent client. Then, right-click on the "kali-linux-20xx-.x-xxxxx" and select "Force Start" to prioritize and initialize the torrent. If the torrent does not start, then the proxy settings were not correct or your subscription had expired. If it succeeds, you should see something like the screen below.
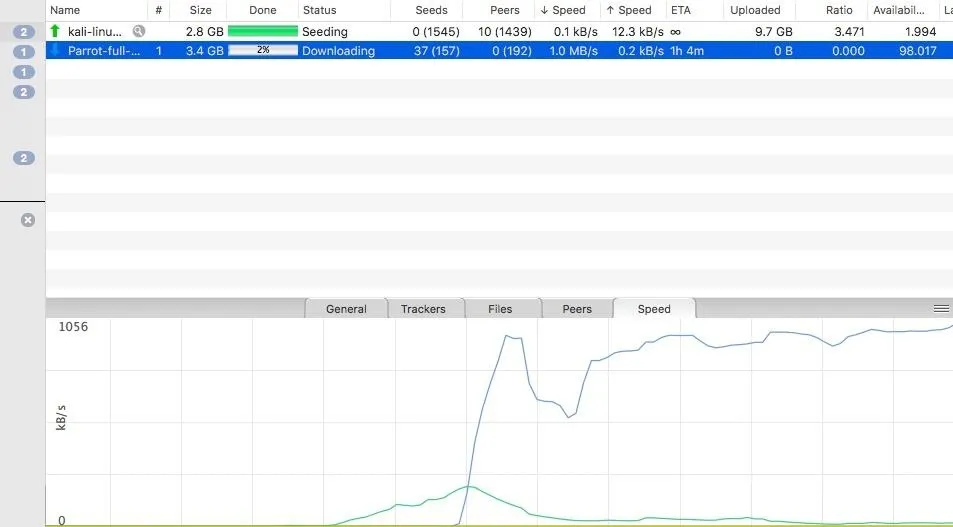
Here we see a successful connection as a file downloads.
Once the connection levels off, your download should work normally. As soon as it's finished, you'll have downloaded your first piece of data via proxy.
Proxies Have Even More Beneficial Uses
In the end, we connected our torrent client to redirect our internet traffic to Private Internet Access's proxy servers. This ensured that our private information is concealed while torrenting. Since we did this in an application-specific way, we are also able to use this configuration for web browsers and other application that allow proxy redirection settings.
Depending on where the proxy is, we can also get around geolocation filters to access regionally-restricted websites. This useful ability can fight censorship and be used to get around many types of network restrictions.
Some organizations, like school and governments, use proxies in their network for almost the exact opposite reason. They configure proxies to actually filter blacklisted websites, like porn or social media, so people in the organization do their work and without getting distracted.
In that example, a client sends a request to the proxy server to fetch a file or webpage. When the proxy server receives the data, it will interpret the request and decide if that data will be sent back, depending on the settings and rules applied to the proxy server, such as blocking pornography. The client will then receive the file or webpage they requested, provided it passed the proxy filter.
Again, since proxy servers also cache webpages, if an organization's network has hundreds or thousands of users searching for the same thing, it cuts down the search index times on the network and reduces upstream demand.
Have any questions? Comment below or hit me up on Twitter @Nitroux2.
- Follow Null Byte on Twitter and Google+
- Follow WonderHowTo on Facebook, Twitter, Pinterest, and Google+
Cover photo by Kody/Null Byte; Screenshots by Nitrous/Null Byte

























Comments
Be the first, drop a comment!