Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.
What Is a Canary Token?
A canary token is a unique link designed to detect when someone clicks on it, shares it, or interacts with it in some way. You can think of it like a tripwire left by defenders to let them know when someone is poking around somewhere they shouldn't be on your network. Disguised as information attackers would be interested in accessing, the idea is to leave tokens on your network so that intruders send a flurry of notifications when they begin doing things they shouldn't.
Honeypots, honeytokens, and other types of traps for attackers are not a new idea. Honeytokens use fake login credentials that are stored in an insecure file on the network, encouraging attackers to try to use them. A blue team watching for these fake credentials can then detect any time someone attempts to log in to a service on the network using them, alerting them that an attacker has gained access.
A honeypot is a more elaborate way of trapping attackers, creating fake systems to attack while trying to learn as much as possible about the attacker. Honeypots will try to get an attacker to use whatever malware or tactics they use to exploit a system within a fake environment that poses no risk. By getting a hacker to do their worst against a fake network, defenders can learn more about who is behind an attack and what tools criminal hackers use.
Canary tokens are designed to be so simple anyone can use them. Depending on how you deploy them, they can detect when someone clicks a link, opens an email, shares a file, or otherwise interacts with the tracking link.
Skype & Slack User Tracking with Canary Tokens
One unique property of Canary tokens is that your target doesn't need to click on the link in order to trigger the token. In an incident reported by Bellingcat, a penetration tester discovered that his phishing server had been discovered after noticing a Skype server connecting to it. He learned that any time a link is shared in certain private messengers, a link preview is generated to show a thumbnail of the webpage. This means that a Skype server actually connects to the Canary token URL, giving us a result like the one below.
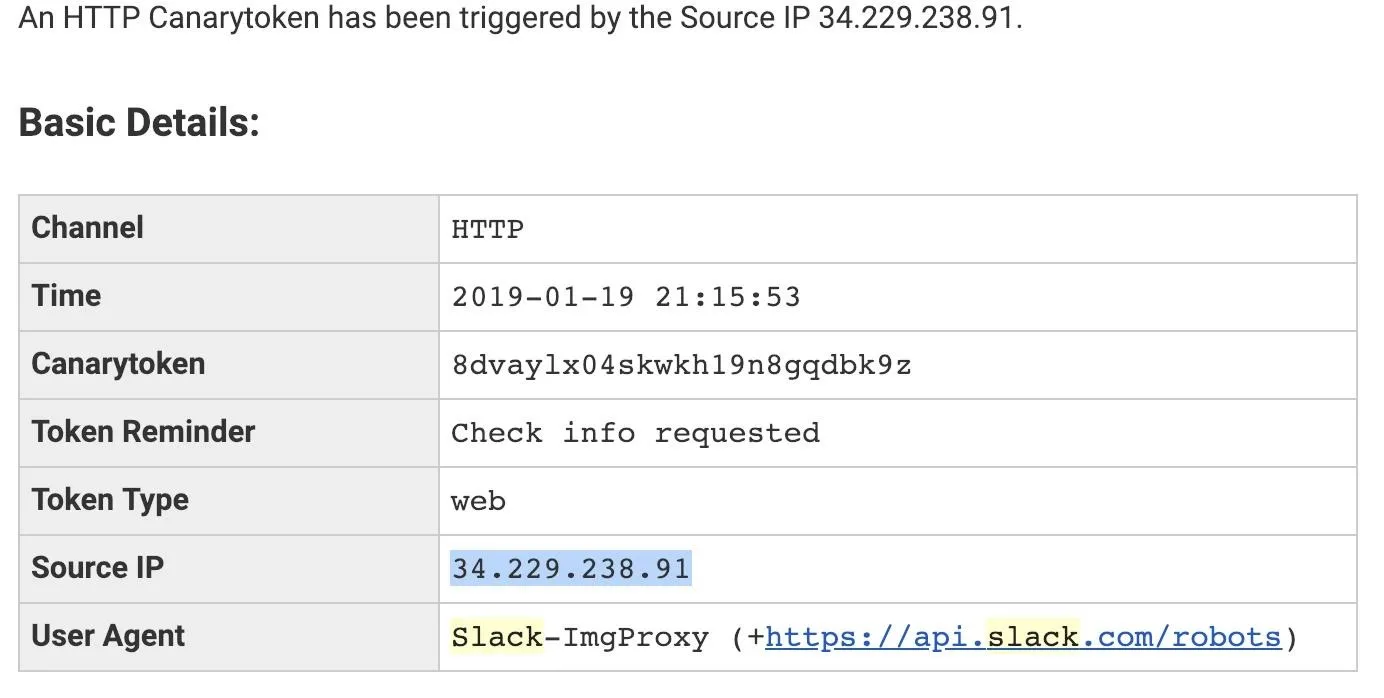
In testing, I found that Slack messenger actually triggers an alert any time a member of the chat connects to the channel the Canary token is shared in. This means by sharing a link in a group chat of many different messengers, you can monitor when anyone new joins the chat, even if no one clicks on the link. While this is pretty exciting, the link generated for Canary tokens still does look a little suspicious.
While Slack and Skype were some of the worst offenders, this trick works in several other types of instant messaging applications as well.
Shortened URLs
To get around the fact that Canary tokens very obviously link back to a website full of information about what they are, it's best to hide the link as much as possible. One way of hiding URLs that is popular among hackers is to use URL shorteners like Goo.gl (which is shutting down for good on March 30, 2019) or Bit.ly. These services create a tunnel from a shortened URL to a much longer one, allowing users to more easily share long URLs.
We can abuse these by using a URL shortener to create a less suspicious looking link to include in a Slack or Skype chat. If you own your own web domain, you can also have your web domain route to the Canary token URL, but for anyone who just wants to try this out, Bit.ly works fine. While testing, I was able to show that canary tokens hidden behind shortened URLs work almost exactly the same as posting the raw link.
What You'll Need
Canary tokens can be used from any platform with a web browser, including Windows, macOS, and Linux. You'll need a web browser capable of navigating to the Canary tokens website to generate a link, and then a device you want to track.
If you want to test the ability to monitor when your Canary token is shared in a messenger vulnerable to generating URL previews, you can connect to another device through Slack, Skype, WhatsApp, Facebook Messenger, Wire, or Apple iMessages.
Finally, you'll need an email address to receive Canary token alerts. If you don't want to do this, you can still use the web interface, but don't lose the link or you won't be able to access results.
Create a Canary Token
On the Canary token website, you can generate a Canary token by clicking on "Select your token" and choosing the type you want to create.
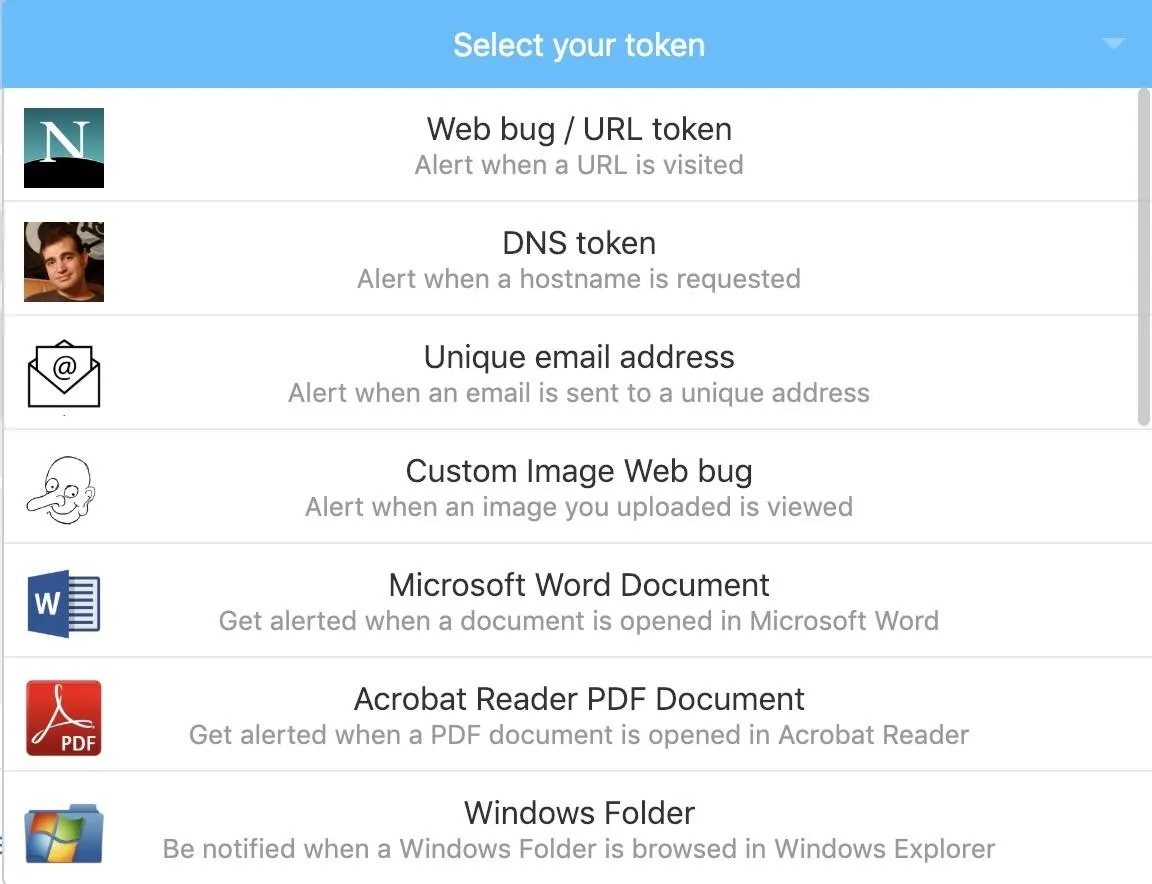
The easiest type of link to generate is a "Web bug / URL token" which will trigger an alert whenever someone clicks on the link or shares it. This is designed to act as a website link, but there are several other options to choose from as well.
A "DNS token" creates an alert whenever a URL is requested, regardless of whether or not the webpage is actually loaded. A "Custom Image Web bug" acts like an image that can be loaded as part of a webpage or email. By adding a web bug to a public website or email, you can tell when someone opens the email or webpage by watching for when the image is requested.
The other available Canary tokens are files which report back when opened or browsed, available as Word documents, PDF files, or a Windows Folder form factor. For our first demonstration, click on the "Web bug / URL token."
Next, supply the email address you want to receive the notifications from. You can also skip this and just configure it through the web interface, but if you lose the link, you'll have a very difficult time interacting with Canary tokens you create.
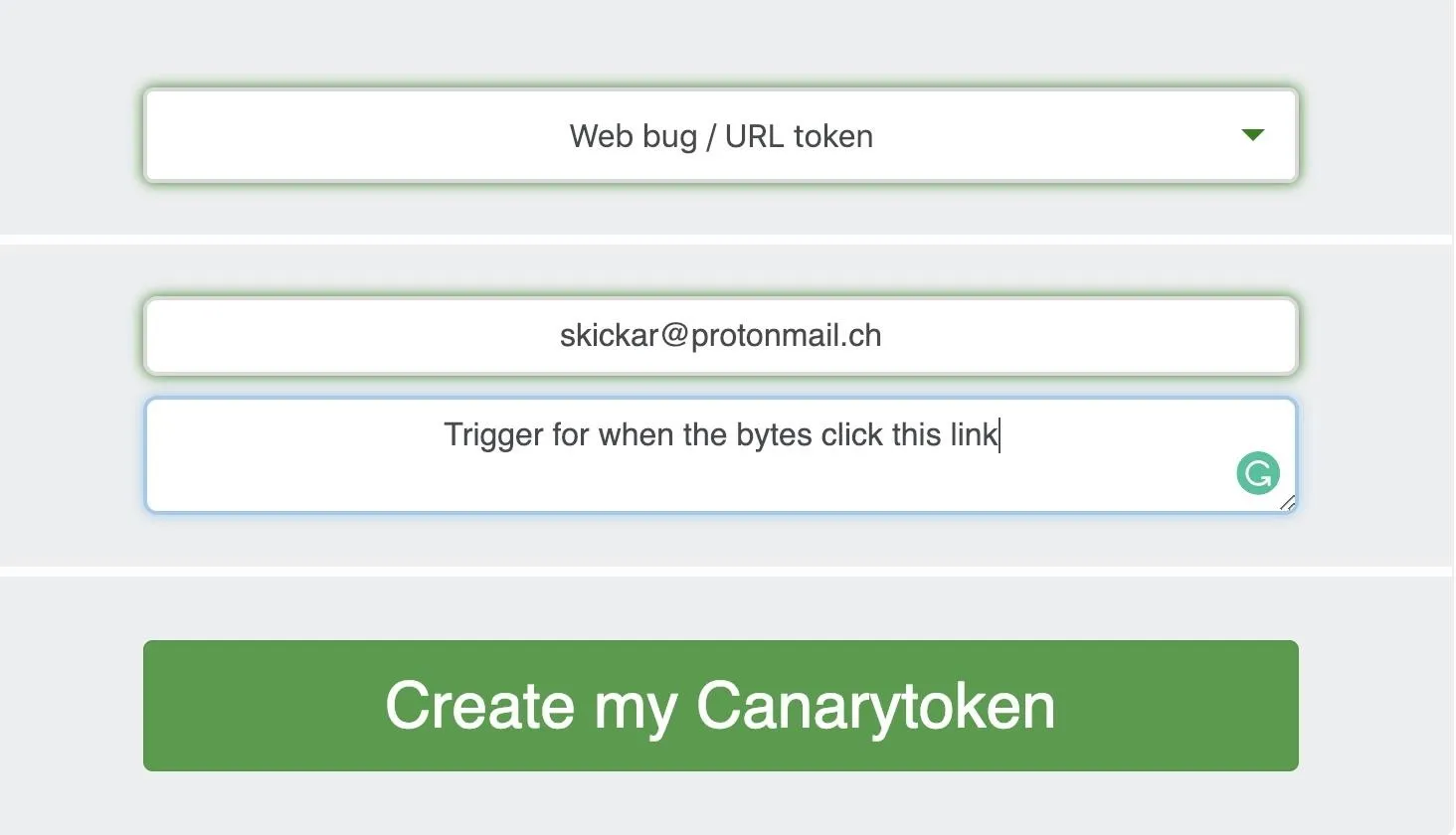
Finally, click "Create my Canarytoken" to generate a link.
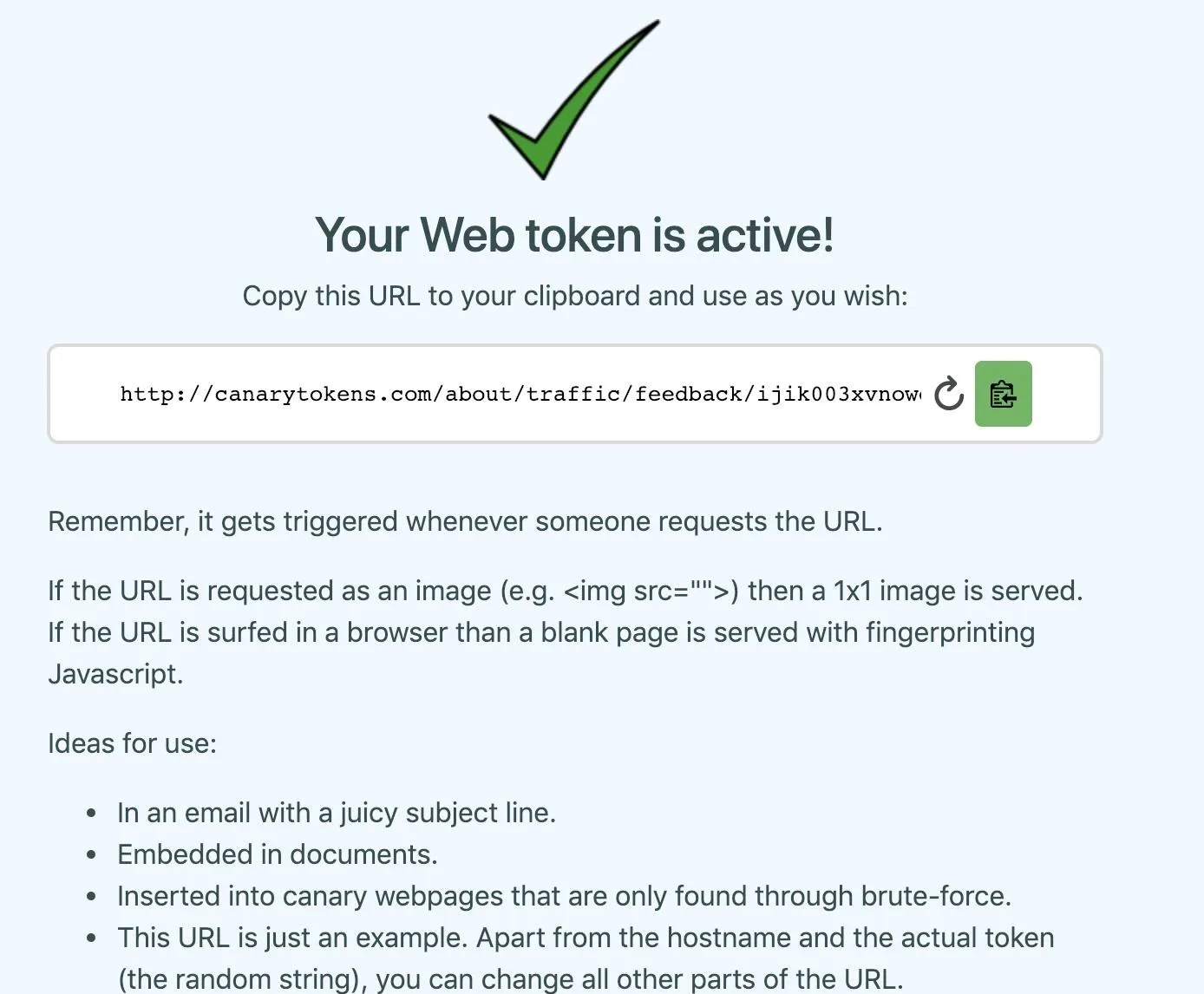
Click the Link
Now that we've created a Canary token, we can look at the management portal. Click on "Manage this token" in the top right corner, and you'll be directed to the page which lets you monitor and control the Canary token.
Here, you can adjust settings to change whether you receive email alerts, as well as enable or disable a scanner that tries to learn more about the browser a visitor to the link is using. To see what it looks like when someone connects, we can click the link we generated, which is here.
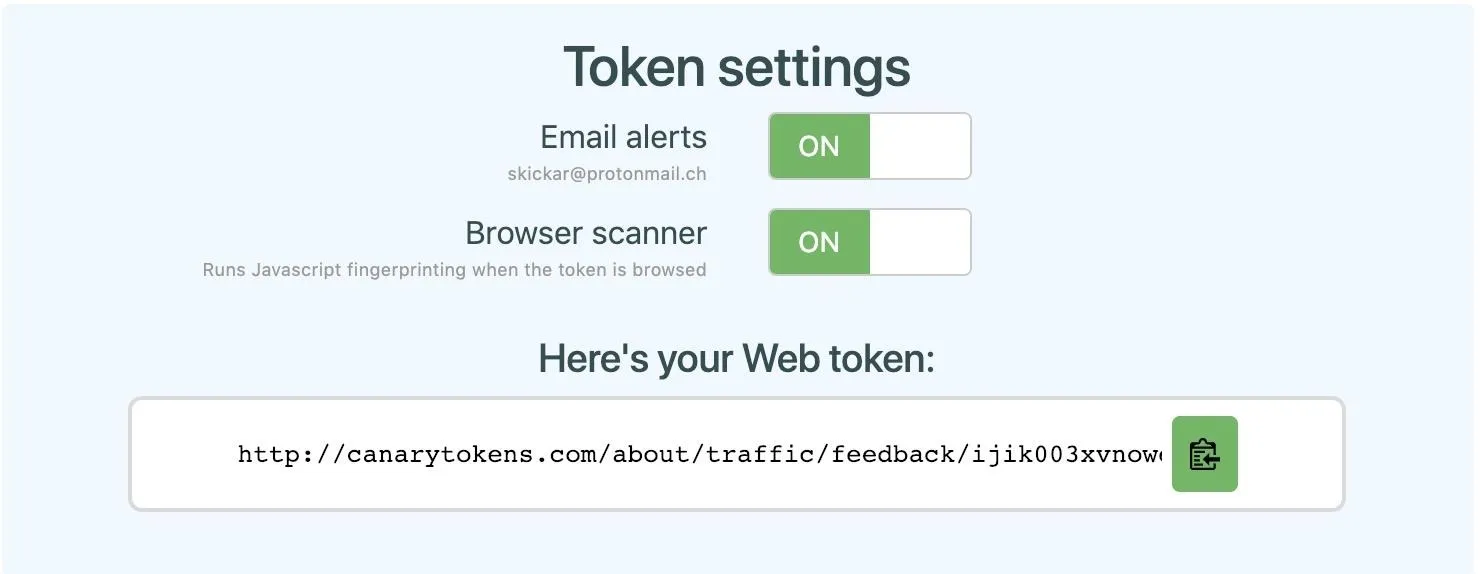
When we click the link, a blank looking web page appears. Even though it doesn't look like the page has loaded anything, we can right-click on the website and click "Inspect" to see scripts that have been loaded on the page. Here, we can see some JavaScript working to identify the device that is connecting to the page.
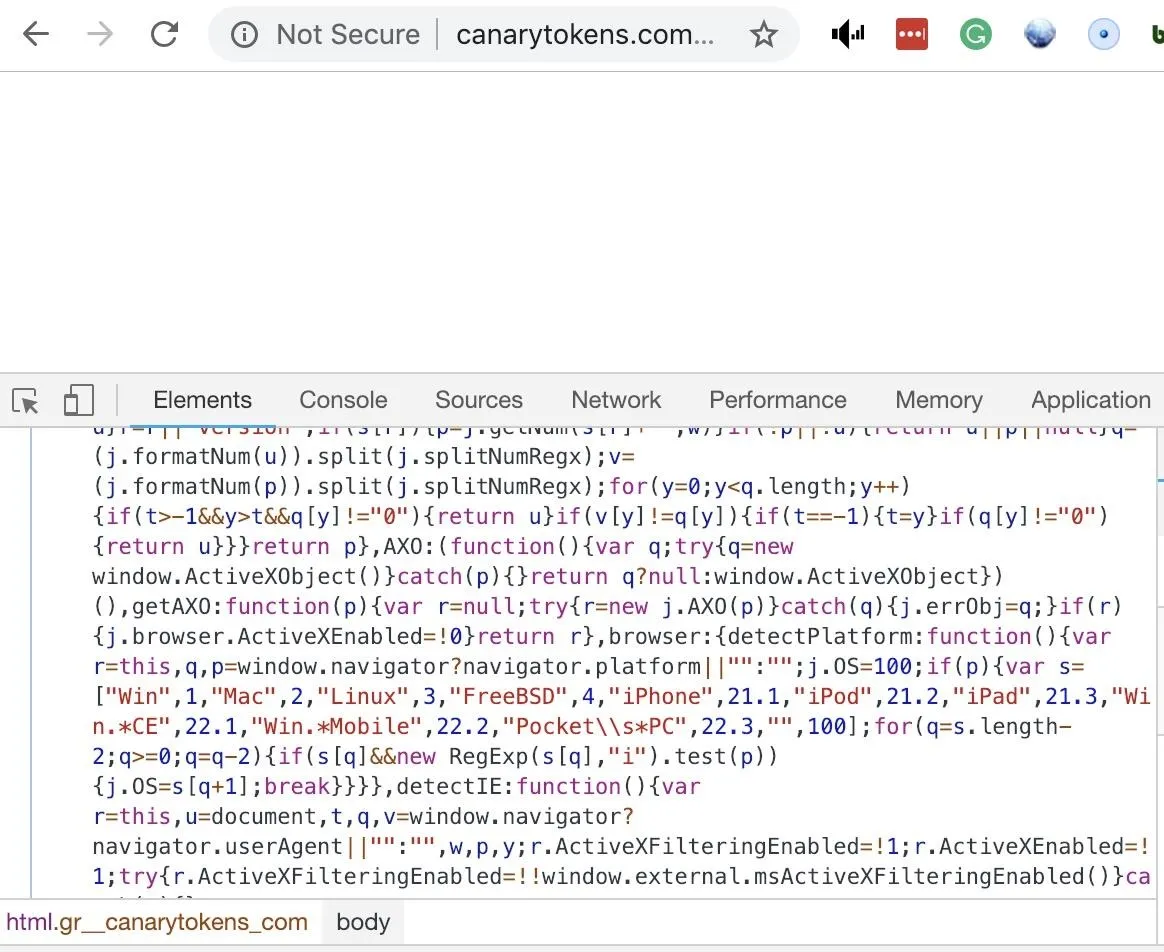
Returning to the token management dashboard, we can see detailed information about the device that just accessed the link. Here, we can see my general location, information about my browser and machine, and even my internal IP address on the network.
Hide from the Bird with Chrome Extensions
While this amount of information being displayed is alarming, there are some ways we can attempt to get around the way Canary tokens detect this information. For one, we can try changing our user agent with a Chrome extension, allowing us to pretend to be another kind of device. While this won't hide all of the details of our device, it can help make it harder to discover what kind of system we're using.
In this example, I set my user agent to that of an iPod.
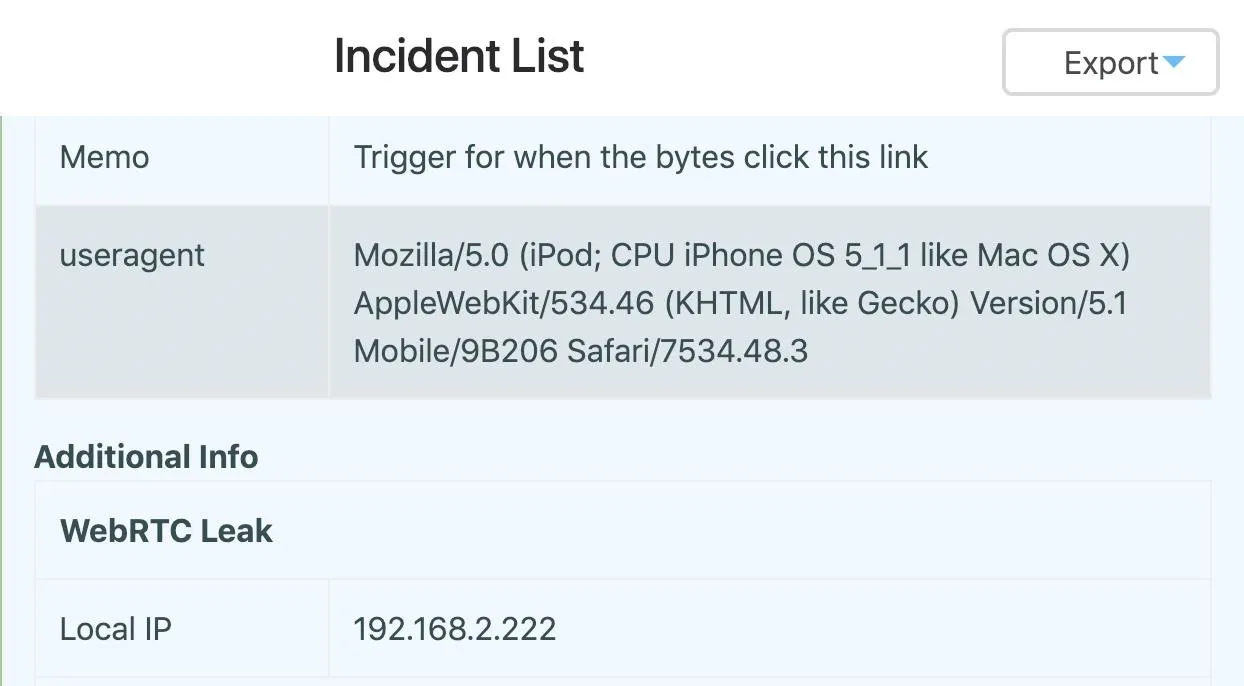
While this hid the type of browser I'm using, the Canary token can still see my IP address and roughly where I am. To take things to the next level, we can try to hide from the Canary token by using a VPN. In this example, I used a VPN and Chrome extension to hide the system I'm using and my location more effectively. The Canary token thinks I'm a Yahoo web spider from Hälsingborg, Sweden.
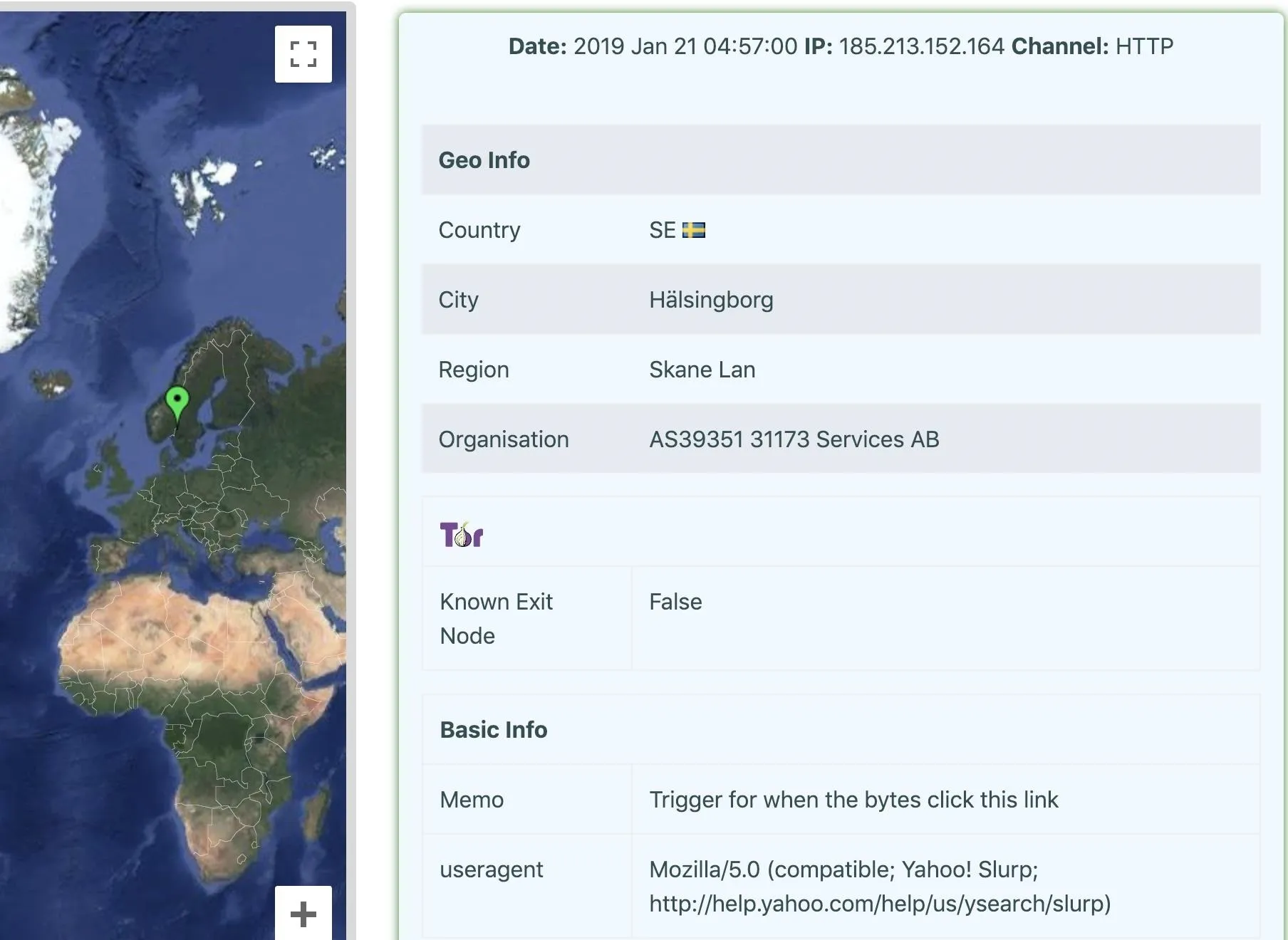
While other information can still be leaked, there are tools available to hide from being accurately identified by a Canary token.
Use URL Shorteners
Another way of using a Canary token is to shorten it with a URL shortener. You can use services like Bit.ly or Goo.gl to hide the real URL, which in most cases doesn't change the way the link behaves when shared in a chat online. To do this, you can go to the Google URL shortner or Bitly to shorten the link. As mentioned before, the Google URL shortener service is shutting down on March 30, 2019.
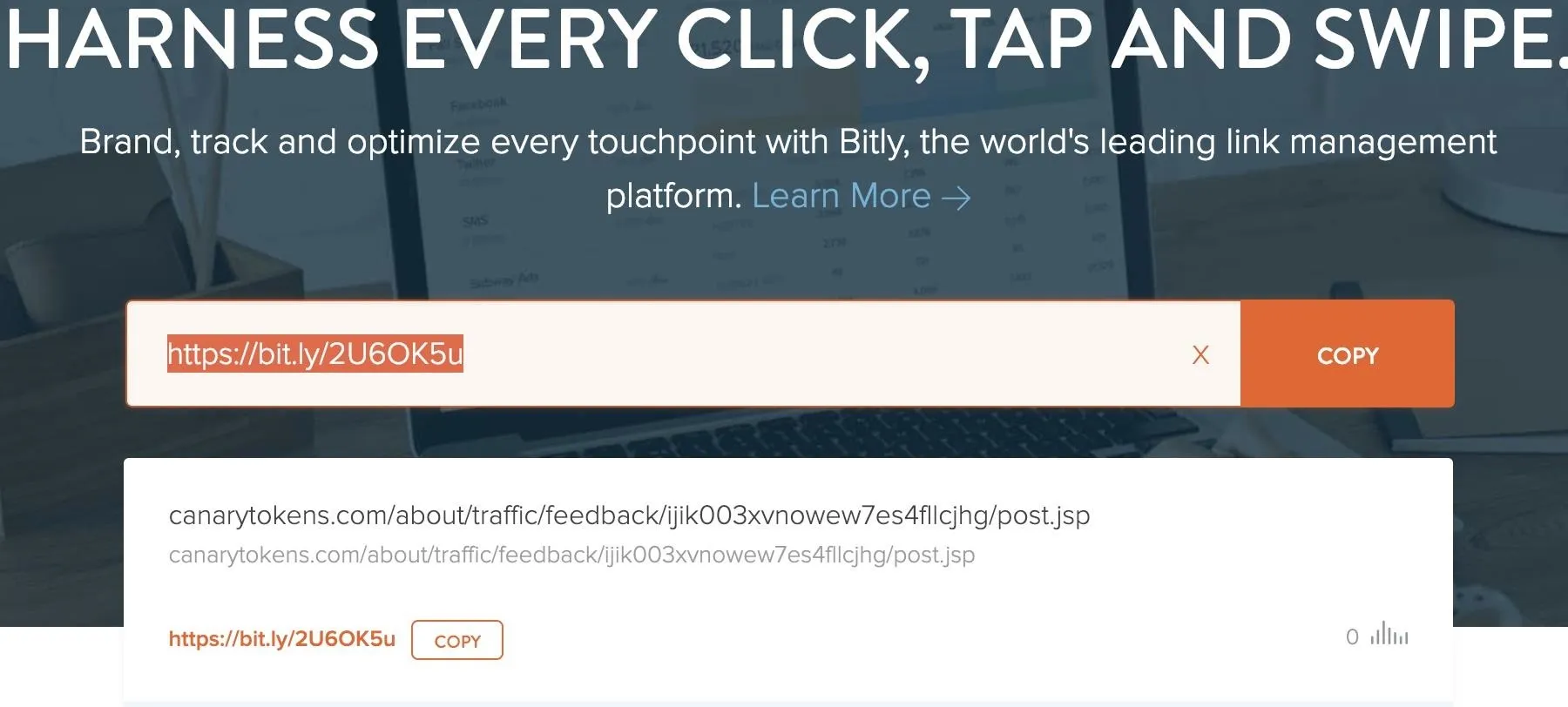
After adding your Canary token link to Bit.ly, you can use the shortened link the same way that you would use the original. Often, this shortened link will attract less suspicion than the super-long Canary token URL.
View the Behavior with Messengers
An interesting property of Canary tokens is that they can alert you to when someone checks a private chat. Each time someone logs in to a service like Slack, a URL preview is helpfully generated by Slack. This means that if you drop a Canary token in a Slack channel, you can get real-time updates whenever someone opens the chat, even if they don't click on the link.
- Don't Miss: How to Spy on Anyone's Smartphone Activity
This behavior also often works through URL shorteners, allowing you to drop links that automatically report on anyone viewing them without looking as suspicious.
In the management portal for the Canary token, you should see hits from Slack or Skype attempting to preview the URL if you posted it raw, or expanding the link if you posted a shortened version.
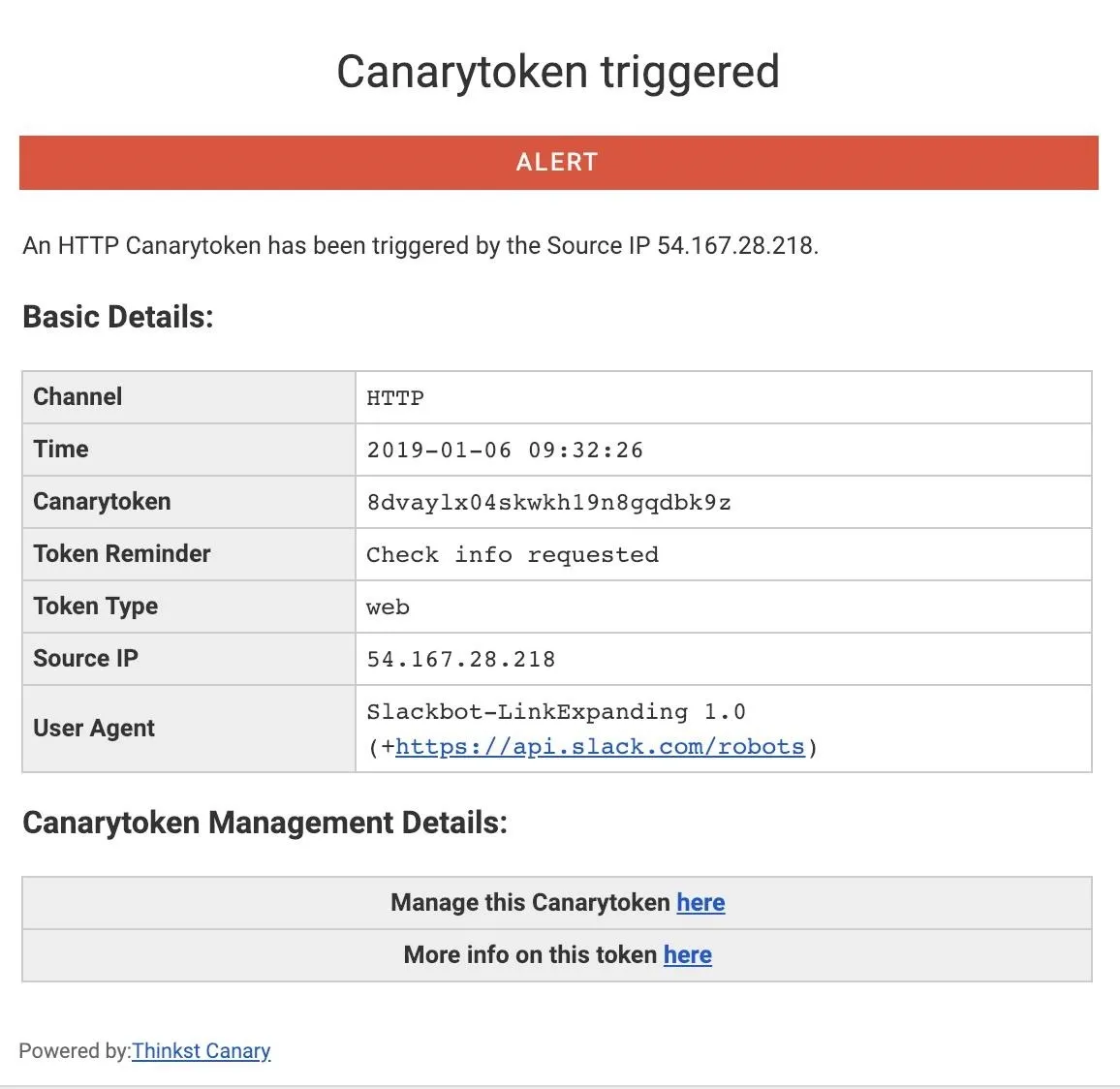
You can find this behavior will work across Slack, Skype, WhatsApp, Facebook Messenger, Wire, or iMessage. While you'll get far more information about a target if they click on the link, even placing a link in a sensitive chat can still give you insight as to when someone has seen or is discussing the link.
Use Other Types of Canary Tokens
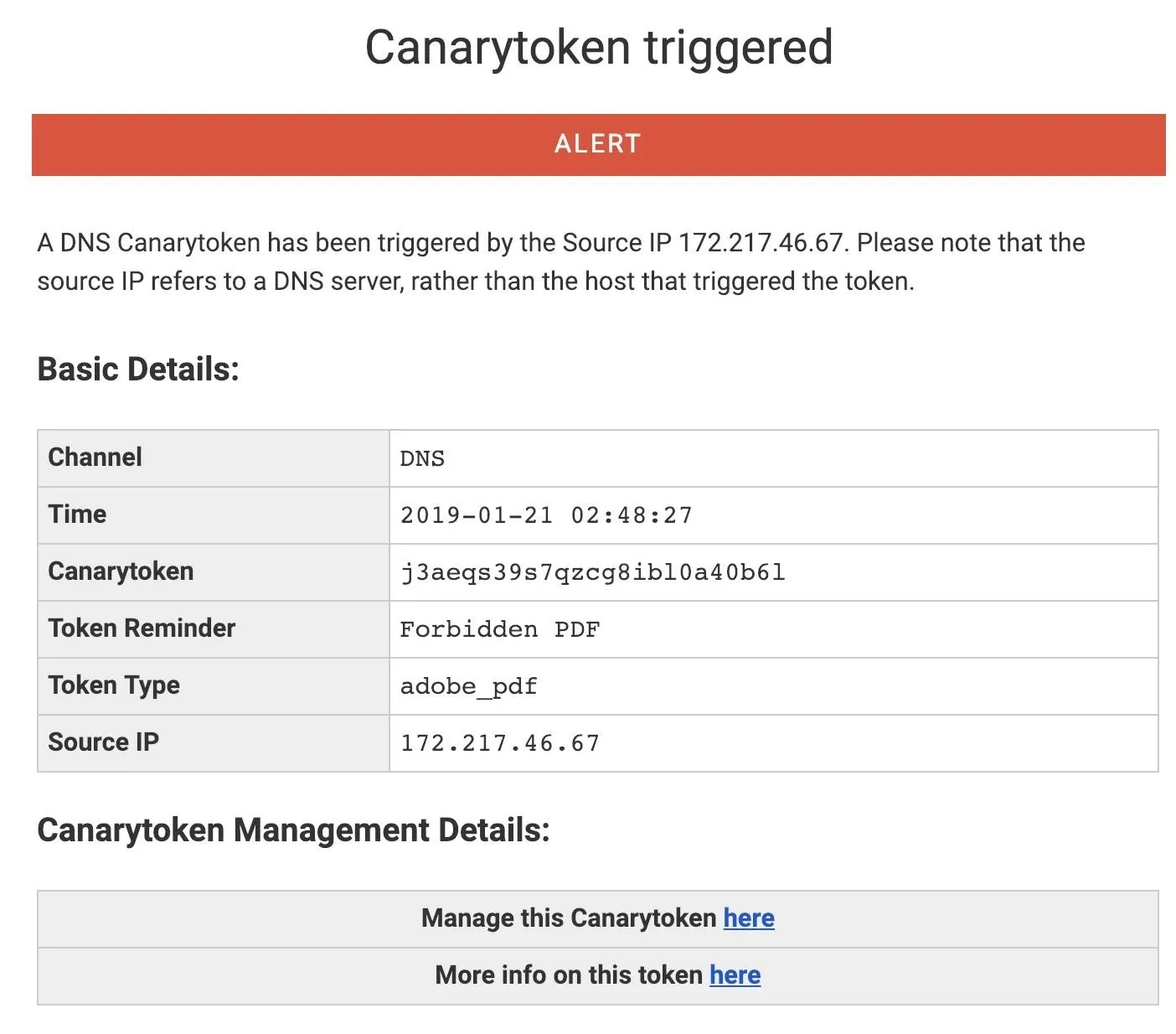
While we've explored the Web Bug Canary token, there are a number of other useful tokens we can try. To see how they work, let's try the PDF file token.
Navigate to the Canary tokens website, and generate an "Adobe Reader PDF Document." Fill in your email address and a note to remind you what the token is for, and download the PDF file.
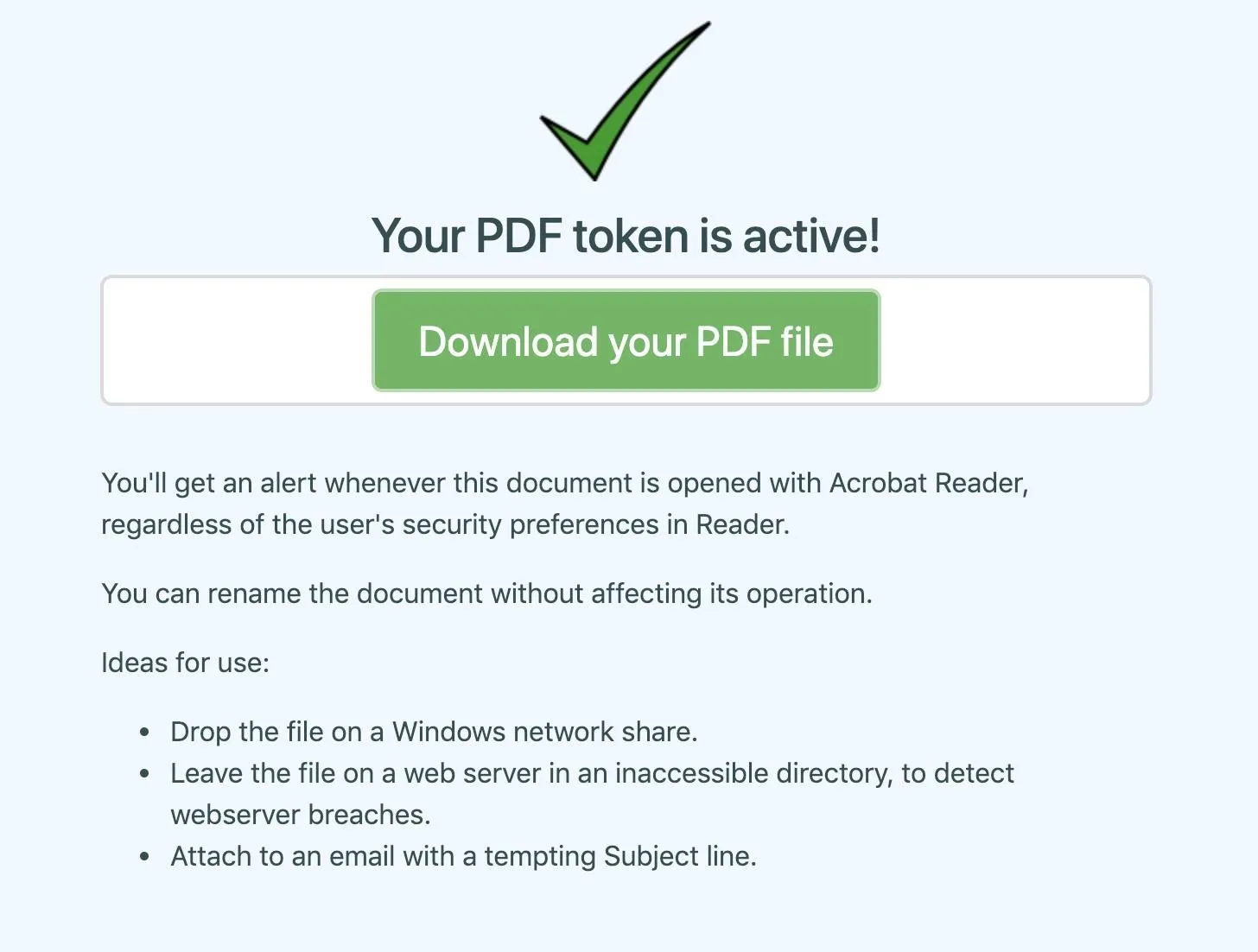
There are several great recommendations for how to use this token included on the site, but in this case, we'll take a look at how the Canary token can bypass a user's choices to phone home.
On a macOS system, opening the PDF file in Adobe yields the following warning. To play the part of the concerned target, I clicked "Block" to prevent the Canary token from detecting that I'd opened the PDF file.
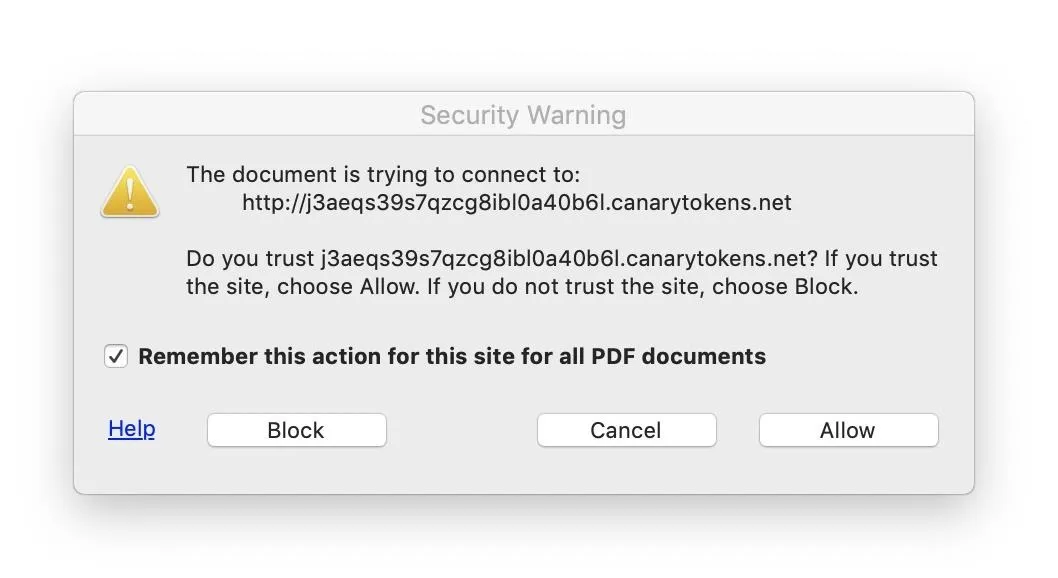
Unfortunately, it doesn't matter that I told Adobe to "block" the site, because it already connected! Adobe went ahead and pinged the Canary token server before it even sent us the alert, meaning it really didn't matter that we clicked "block." The attacker can still see that I've opened the document, in spite of my efforts to prevent it.
There are a number of creative ways to use these tokens to detect user actions, this is only the start!
Canary Tokens Make Tracking Easy
If you're looking to get creative using Canary tokens, there is no limit to the ways you can embed them to detect suspicious behavior. A popular suggestion is to cause a startup script to request the URL when a user logs in, notifying you each time a computer is accessed along with the IP address of the network it is connected to.
While it's possible to hide from these tracking techniques, doing so can be difficult. This makes Canary tokens flexible, easy to deploy solutions for tracking with links. If this kind of tracking freaks you out, you should know that advertisers and other online companies routinely use these and even more sophisticated tactics to track customers.
I hope you enjoyed this guide to creating and using tracking links! If you have any questions about this tutorial on Canary tokens or if you have a comment, feel free to ask it below or reach out to me on Twitter @KodyKinzie.
- Follow Null Byte on Twitter, Flipboard, and YouTube
- Sign up for Null Byte's weekly newsletter
- Follow WonderHowTo on Facebook, Twitter, Pinterest, and Flipboard
Cover photo and screenshots by Kody/Null Byte

























Comments
Be the first, drop a comment!