The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.
If you've ever tried hacking on an iPhone, you know it's not a straightforward process. A few problems arise when trying to do any sort of hacking from a smartphone. First, the operating systems are incredibly restrictive. The closest thing to "hacking" you'll ever get on an iPhone is a port scanner.
You could jailbreak your iPhone, or put Kali NetHunter on an Android device, but even then you are extremely restricted when it comes to wireless hacking by the hardware. Essentially, these strategies expect too much flexibility from devices that were designed for a specific purpose.
Enter The Sonic. It comes pre-built with all of the tools needed to control a Raspberry Pi right from your smartphone. This is where we start to loosen the proverbial chains of our smartphones, by adding a more versatile companion device. When we connect to The Sonic, we can offload any work our phone can't do and take advantage of a fully functional Kali Linux attack suite.

The Sonic, complete with wireless network adapter, being discreet.
This build is different from our previous Raspberry Pi-based Kali Linux, in which our Pi connects to our smartphone's hotspot to be controlled. If your phone doesn't have a hotspot, The Sonic will turn the Raspberry Pi's internal Wi-Fi card into a command-and-control communications Wi-Fi link, which you can connect to from any smartphone to access its features.
One major difference in these two build methods is that the The Sonic will not be able to tether an internet connection from your phone. To connect to the internet, you will need to first connect to The Sonic's wireless AP from your smartphone, and then connect The Sonic to a nearby Wi-Fi network to establish a link to the internet.
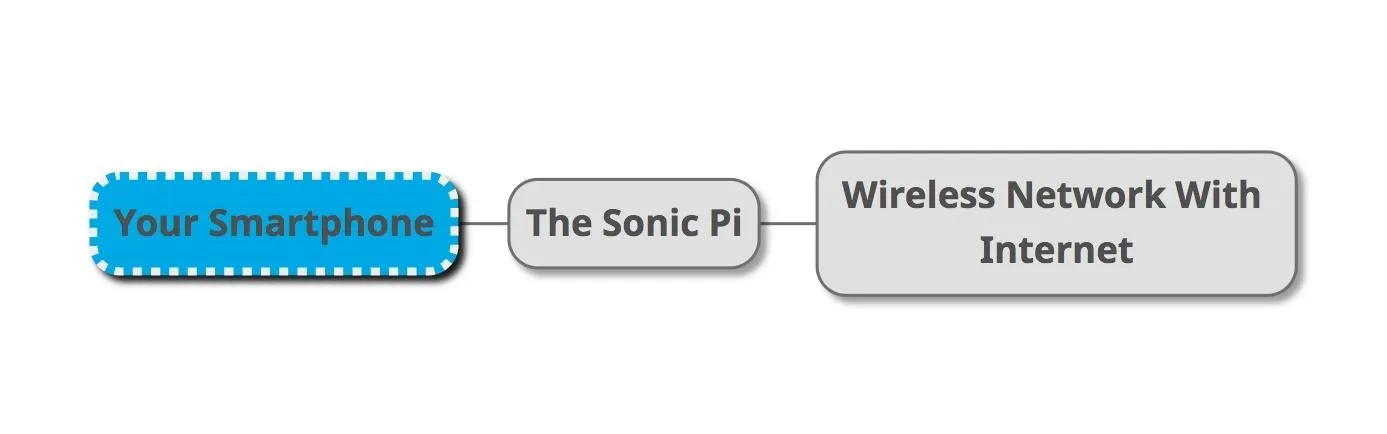
The Sonic Pi can access a network for you, hiding your real MAC address. To access the internet, you first connect to the Sonic Pi, and then connect the Sonic Pi to the Wi-Fi network providing internet.
This means The Sonic will need two interfaces, the command-and-control to host the connection to your smartphone and the "attack" antenna to connect the Pi to the network you want to access the internet from.
For more on our alternative Kali Linux build, check out the link below.
Gathering the Necessary Parts
Going on the Sonic's website, we see that there are some other parts we're going to need. In addition to a Raspberry Pi 3, the following parts are suggested:
- A TP-Link TL-WN722N wireless card. Any wireless card with an Atheros chip should also satisfy this recommendation. If you're not sure what chipset your wireless card uses, check out the link below for our breakdown.
- We will also need a microSD card to burn The Sonic image to.
- Although it isn't a specific requirement on The Sonic website, we're also going to want to pick up a good battery for our Raspberry Pi. If we want truly mobile hacking, we need a truly mobile solution. I tested this battery with a Raspberry Pi 3 B and it lasted more than 7 hours!

To make a Sonic, you'll need a Raspberry Pi 3 and a Kali-compatible wireless network adapter.
The main benefit to using the Pi over something like a laptop is portability and stealth. While a laptop with several antennas sticking out looks pretty suspect, someone using The Sonic appears to be doing nothing more than checking their phone.
Now that we've got the hardware, we need to get some matching software. For mobile devices, we need to make sure we have the Google Chrome web browser. Safari on iPhone doesn't support the JavaScript functions that The Sonic uses, so we need Google Chrome to access it properly.
Downloading & Burning the Sonic Image
You can download the IMG file for The Sonic from here. The image will be delivered in the form of a 2.1 GB ZIP archive, which you'll have to extract. After you unzip the image, the total size will be around 16 GB, so be aware you're working with some pretty big files.
Because the files are so massive, it's a good idea to verify their integrity. You can do this by checking the hash values for the downloaded file and comparing them to the ones shown on the download page of the website. FCIV is an easy to use command line tool for Windows to calculate the hash values. For Linux, you can use the command md5sum, and Mac users can use the command md5.
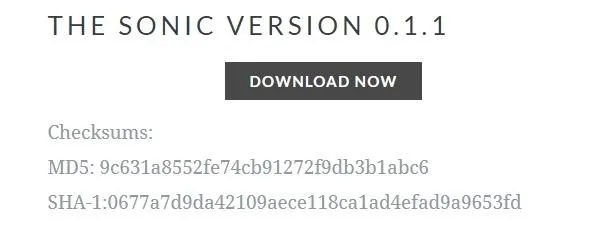
The hash checksums for the .zip file can be found on The Sonic website.
Once you have the image, the steps to flash it to the microSD card vary depending on your operating system. Find your operating system below and follow the necessary steps.
On Windows
In order to flash The Sonic image on Windows, we need some additional software. Win32 Disk Imager will let us pick the image file, select what device we want to write to, and finally take care of the rest for us.
On Mac & Linux
We can use dd in our terminal. First, we will need to figure out which connected disk device represents the SD card. This can be done by running lsblk in Linux, or diskutil list in macOS. Next, we need to unmount the device via umount (disklocation) in Linux, or diskutil unmount /dev/device in macOS. Finally, we write the image to the SD card with the following command.
dd if=theImageFile.img of=/dev/device bs=4m.
Once the card has been flashed, insert it into your Raspberry Pi.
Connecting to the Sonic
Now it's time to start up our Sonic!
A quick note before we continue: The Sonic is programmed to automatically configure the necessary Linux files to set up an access point. To do this, the Pi will restart itself once or twice. This is completely normal.
During this process, The Sonic is assigning your Raspberry Pi's internal Wi-Fi card a special interface name so that it can run an access point. After that, The Sonic will run a few startup scripts to configure the access point, enable SSH login, and run the web application.
Plug your wireless network adapter into the Raspberry Pi, and power on the Pi by connecting it to a power source via the Micro USB power cable.
Once the Pi is done setting itself up, it will start the built-in access point. By default, the SSID is The Sonic and the password is password. It's definitely a good idea to change these at some point. This can be done by going to the "AP Manager" tab on The Sonic web app, which we'll take a look at soon.
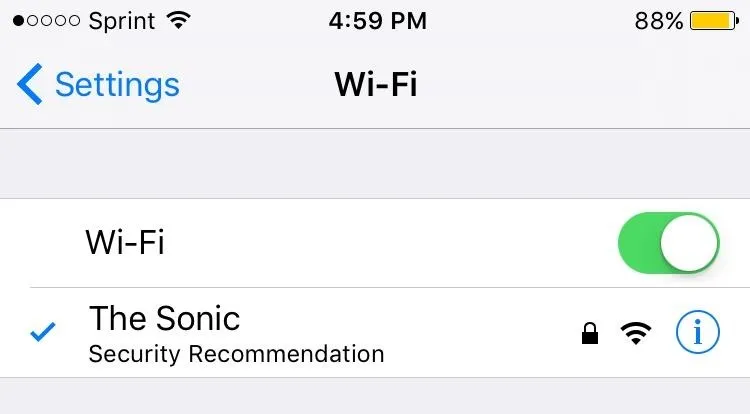
The default WPA password for The Sonic is the easiest "password" ever.
Troubleshooting Issues with the Sonic
If you don't see an access point named "The Sonic" after 15 minutes, there are a few things to check.
First, turn off your Sonic, plug it into a monitor, and power it back on. We want to check and see if the device is booting up normally, or if there's an issue such as an infinite reboot loop or error message.
If the device is stuck in an infinite loop of rebooting, or you get an error message reading "link wlan0 is not ready" for eternity, there may be a problem with the drivers related to your particular wireless network adapter. If you have another wireless adapter available, try switching to that card.
Otherwise, try unplugging the card and booting The Sonic up without the external interface. Once the Pi boots successfully, check to see if the driver for your wireless card is installed. You can find out what drivers are installed by typing the following.
lspci | grep -i wireless
If the driver for your wireless card is not installed, the steps for installation vary. Visit the manufacturer's website for steps on how to install the drivers necessary for Debian Linux.
If the Pi boots up successfully, but you can't see an access point called "The Sonic," try connecting a keyboard and running the following.
Check see if both Wi-Fi cards are detected, and if an interface named "wap0" is present. If you can't find an interface named "wap0," type the following.
/var/www/html/scripts/ifaceChecker.py
This will run the script that checks the current state of the Raspberry Pi's built-in Wi-Fi interface. If it can't find the interface, there may be a problem with the built-in Wi-Fi card on your Raspberry Pi.
In that case, try using a second Raspberry Pi if you're lucky enough to have another one around, or double-check the Wi-Fi card with a different Raspberry Pi image such as Raspbian and a monitor.
If none of the above seem to help, there may have been a mistake when you first imaged your SD card. Try re-imaging the card as well. You can also look at the documentation on the website here.
Using the Sonic
Once we're connected, the world is our oyster! Well, at least the parts of the world with serious security flaws. Before we do anything though, we're going to want to connect to Wi-Fi, since the current connection will not serve data to our phone or Pi. Thankfully, The Sonic has a built-in web application that makes those sort of otherwise tedious terminal tasks very trivial.
By default, the web application is located at 192.168.8.1. Just punch that address into the browser on your smartphone, and you'll be greeted by a prompt for a username, and then a password. By default, the username is sonic and the password is password.
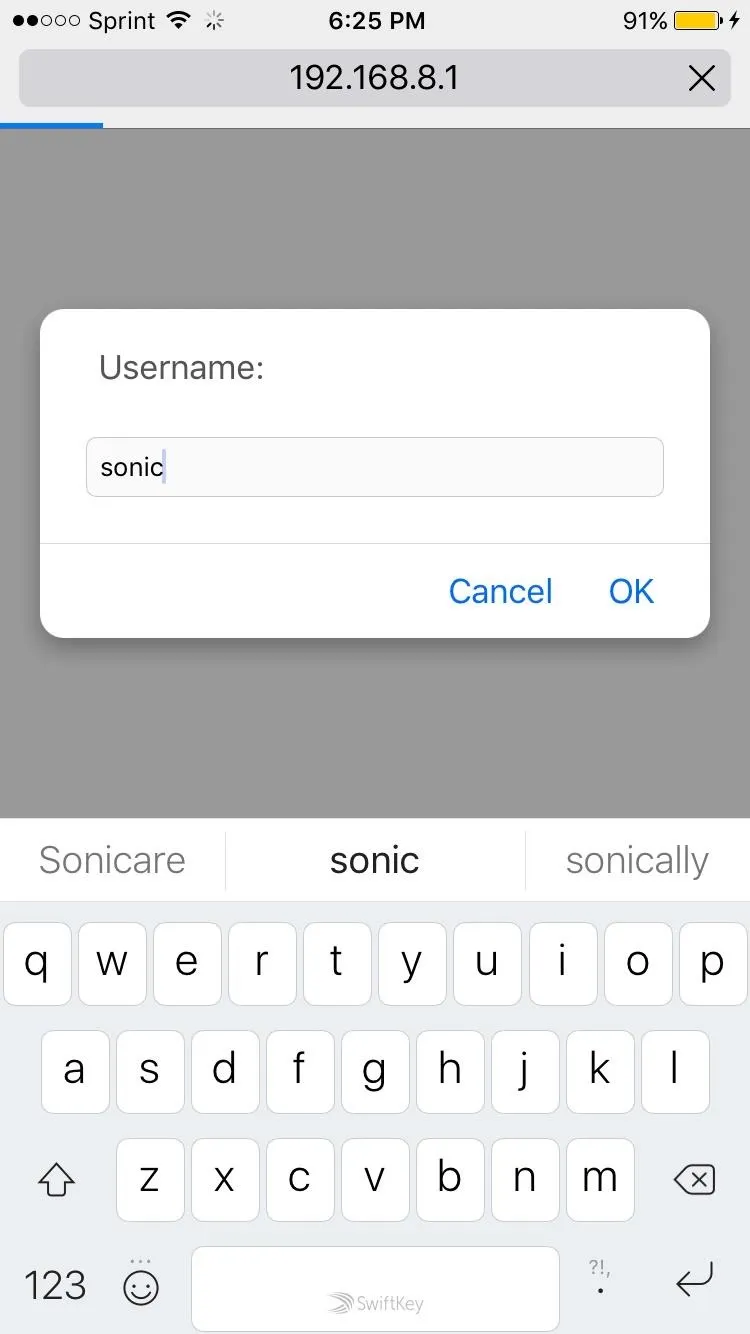
Here, we log in to the Sonic Pi web application.
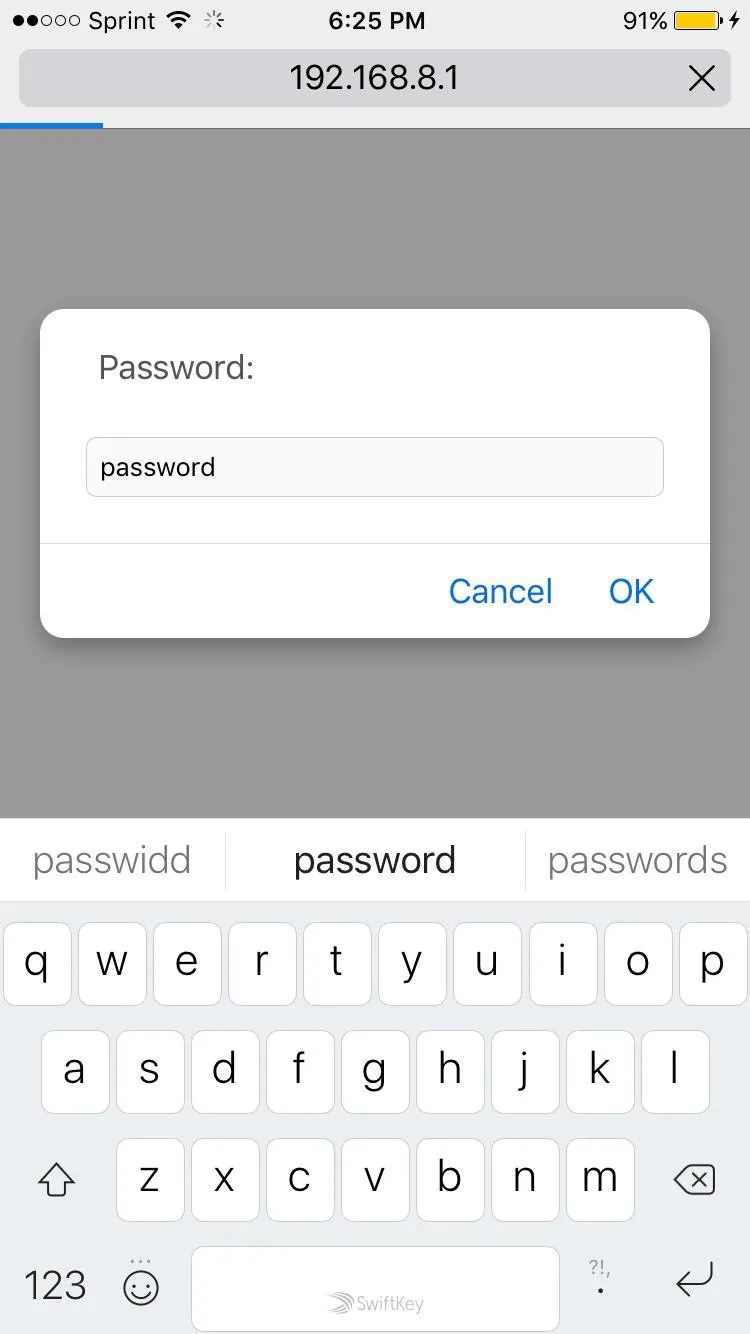

Here, we log in to the Sonic Pi web application.

Once you've done that, the main menu will come up as seen on the left-hand side below. The menu design is definitely basic, but it's to the point. By tapping "Wifi Manager," we can quickly list Wi-Fi points around us (seen on the right-hand side).

In The Sonic web app, the main menu (left) and the Wifi Manager (right). The AP names have been hidden for privacy.


In The Sonic web app, the main menu (left) and the Wifi Manager (right). The AP names have been hidden for privacy.

The access points we see are listed by signal strength. In this example, all of the access points with "(Open)" are a part of a Wi-Fi network that doesn't have a password, but requires authentication via a web portal to use.
Unfortunately we don't have credentials. However being the smart hackers we are we, we can still get access anyway.
Gaining Access to a Network
In order to bypass the web-based authentication for this network, we first need to understand how the authentication keeps track of its users. Just like certain websites use cookies to pre-authenticate users who have already logged in, these types of networks log the MAC addresses of clients to keep track of whether a device is authorized or not.
So what we need to do is find the MAC address of a client already connected. The Sonic makes this process incredibly easy for us. If we hop back into the web app, we can find some pretty nifty features.
In the Wifi Manager, let's tap on the button for the network we are trying to hack into. We'll be greeted with a screen similar to the one on the left below. Here we see a couple options: We can either connect to the network or do some wireless sniffing and see all of the clients connected to the network. Of course, we want to snoop, so we tap "List Connected Devices."
Upon tapping this button, the Sonic will open a new tab that will start scanning for connected devices. Basically, a background process running Airodump-ng from the Aircrack-ng suite will process the output and show us the results. This process takes about 33 seconds to load, so you'll have to be patient.
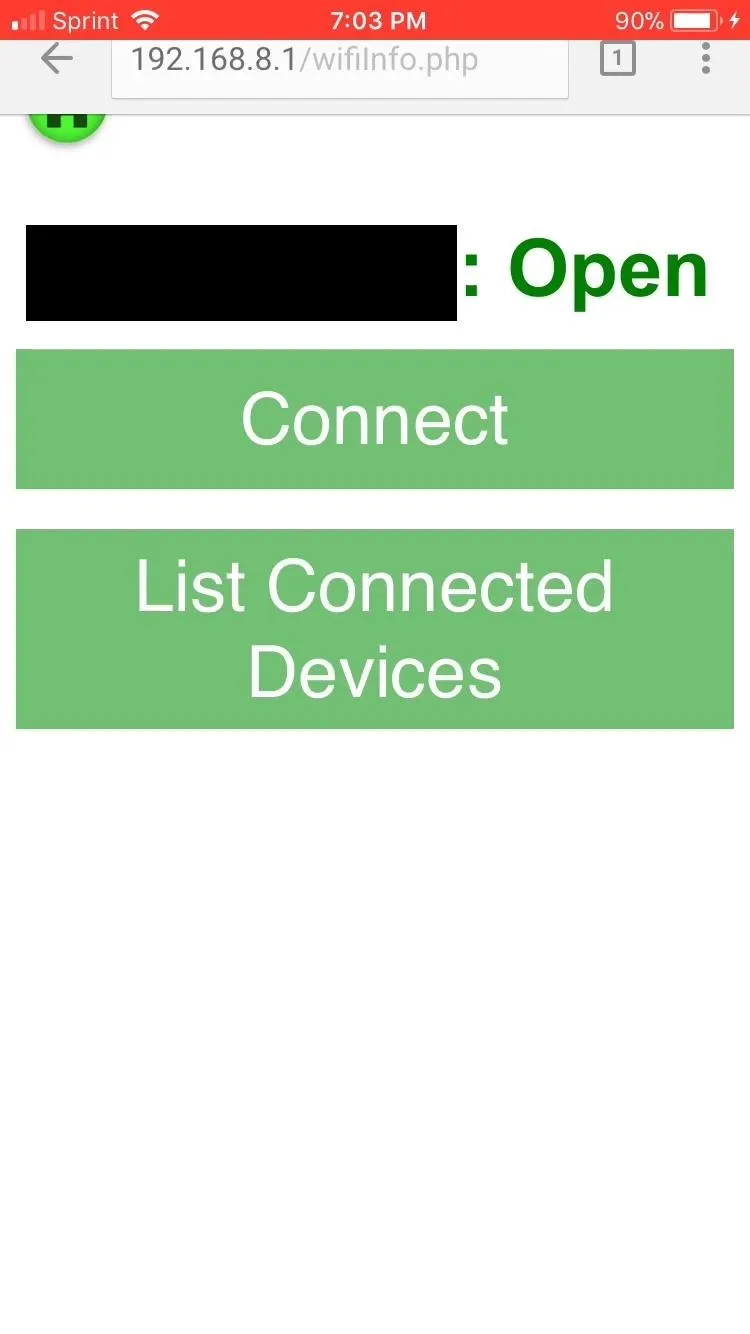



This feature is currently the only one that doesn't work in the Safari browser. Safari doesn't support the new tab JavaScript function the Sonic uses. Plans are in place to extend support to Safari once additional features have been implemented.
Changing Our MAC Address
Once the web app has finished loading, we'll be presented with a list of client MAC addresses. By simply tapping one, we'll be sent to the MAC Changer page where all of the necessary data will have been sent to assign our device this new MAC address. Now, all we have to do is go back to the Wifi Manager and connect to the point. We're in like Flynn!
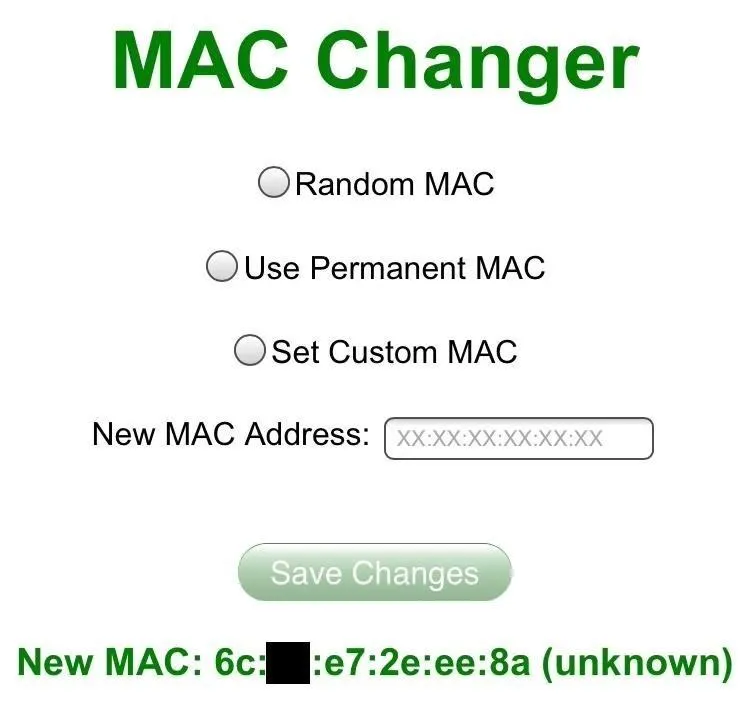
It is worth noting that by doing this, you will most likely disrupt the service of whoever the device you are masquerading as belongs to. With this in mind, the attack isn't exactly stealthy.
But putting that aside, now that we can connect to the network, there really isn't much we can't do. The Sonic is set up to route its built-in Wi-Fi access point through the access point it's just connected to in order to connect to the internet. This means you can still access the internet from your phone, once The Sonic is connected to a nearby access point.
From here, we have the ability to sniff local traffic, spoof a DNS server, run exploits on network devices, and just about anything else you could do from a Kali Linux laptop or desktop. The beauty of The Sonic is how portable and stealthy the device is.
Get Started & Unleash Your Inner Hacker
Again, while the project is still very new, the foundations of The Sonic make it a plug-and-play hacking tool like no other. The Sonic is being actively maintained right now, and new features are being added to the web app to make it much more intuitive and convenient to use.
If you want to be able to wield The Sonic to its full potential, you'll have to first master Kali Linux. Keep scrolling through Null Byte and drinking in all of the hacking goodness we have here!
Feel free to comment below with questions or contact me on Twitter @xAllegiance.
- Follow Null Byte on Twitter and Google+
- Follow WonderHowTo on Facebook, Twitter, Pinterest, and Google+
Cover photo by SADMIN/Null Byte
Screenshots by allegiance/Null Byte

























Comments
Be the first, drop a comment!