Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.
Our video covers everything you need to know, but you can also read through the article below for more details on each method. And, of course, it's always here if you like following written guides more than video tutorials.
Password Cracking
Password cracking is a tried-and-true method of breaking into a Wi-Fi network that generally relies on the user picking a bad password. While there are many ways this attack can unfold, in general, there are two ways that a user can be fall victim to this attack.
The first is by taking advantage of a target using an insecure type of encryption called WEP to lock their Wi-Fi rather than the more modern WPA that is standard for most networks. Using a WEP key allows even a sophisticated password to be broken in minutes, rendering it not very effective.
There are many tools available to hack WEP networks, but simple command-line programs like Besside-ng are able to locate and crack WEP networks using Kali-compatible wireless network adapters.
Aircrack-ng 1.2 rc4
[00:00:02] Tested 14115 keys (got 20198 IVs)
KB depth byte(vote)
0 0/ 1 61(30208) 68(26112) DC(26112) E3(24832) 5D(24576) 6E(24576) ED(24320) 08(24064) 43(24064)
1 1/ 16 4C(26368) BD(26112) 6F(25600) AE(25088) 00(25088) A5(24832) A6(24576) A4(24320) EF(24320)
2 0/ 36 46(25856) CE(25600) D1(25088) DE(24832) E1(24832) 89(24832) C7(24576) C8(24320) E3(24320)
3 1/ 4 79(26880) 10(25088) 25(25008) 51(24832) 6F(24832) D2(24832) 45(24576) 6C(24576) 70(24576)
4 1/ 8 4F(27648) 64(26368) E4(25600) 5D(25600) 97(25344) FD(25088) 05(25088) AC(24576) 59(24320)
KEY FOUND! [ 61:4C:46:32:4F ] (ASCII: aLF20 )
Decrypted correctly: 100%
root@skickar:~# _The second kind of password cracking attacks the more secure WPA method of encryption and involves brute-forcing the password. By kicking devices off the target network for a few seconds, a hacker can force devices to connect back to the network and exchange a sequence of packets called a four-way handshake.
This handshake is enough for a hacker to go home and try guessing a huge list of passwords against the captured handshake. Using their computer's processing power, a hacker can try millions of passwords very quickly, allowing them to break bad passwords in minutes or hours. The tools for WPA cracking are increasingly sophisticated and include Airgeddon, Besside-ng, and Aircrack-ng. These tools can be used to capture and crack network passwords from the intercepted handshake.
For the end user, this means that you must assume that anyone could grab a four-way handshake from your network. If your password is weak or you use it in other places, that could be serious cause for concern depending on how much time an attacker has to spend brute-forcing it.
Solution: Better Passwords
Hackers rely on a few common habits to be effective with password cracking. Using stolen passwords which have been harvested from real user accounts is a common tactic that preys on the tendency for users to reuse their favorite passwords, increasing the chance that the passwords will be lost by some service you've signed up for. Don't reuse passwords as a rule, because that forces you to trust every service you sign up for to never lose your password.
Using password managers like LastPass and KeePassX can make it easier to use unique passwords, but you should avoid passwords like phone numbers, addresses, or anything especially obvious. Instead, choose longer passwords that are unique and don't rely on any information or interests you've made public.
You can also use tools to detect whether someone has joined your network that doesn't have permission to. By downloading the free, cross-platform Fing application to your smartphone, you can scan and take an inventory of any network you are connected to. If a device is connected that shouldn't be, you have the proof that an unauthorized user is connected and can take steps to kick them out by changing the password or resetting the router.
Social-Engineering Attacks
Social-engineering attacks can look very different, and this is partially what makes them so hard to spot. Generally, a social-engineering attack will rely on tricking the user rather than using a technical exploit, so a victim may not realize anything has happened.
There are a lot of reasons why you shouldn't give someone your work or home Wi-Fi password, and very few reasons why you should if you don't trust them. It's important to remember a few facts about Wi-Fi:
- Wi-Fi allows direct communication with devices on your network, like webcams, desktop computers, and other devices that may be wired rather than wireless. Having the Wi-Fi password means you can attempt to log into or attack these devices.
- Having the Wi-Fi password can allow an attacker to change the information you or others on your network see when you visit webpages or use the internet.
- Once someone is into your network, they can access the router and build a persistent remote backdoor, preventing you from kicking them out even if you change the password.

Passwords are easy to give out, but once someone has access, it's hard to dislodge them.
Knowing this, a social engineer may attempt to approach someone who knows the Wi-Fi password to gain access. This may be as obvious as a stranger who has no reason for having the Wi-Fi other than simply asking for it or as elaborate as calling the target as the target internet service provider and asking an employee help them fix a problem with the internet.
Solution: Always Be Suspicious
When recognizing a social-engineering attack, you can generally spot a few things that could tip you off that someone wants access to something they're not supposed to have. If someone presents a story where the solution is to hand over your Wi-Fi credentials, try to present an alternative solution, like "I can look that up for you," and see if they pivot to stay focused on the password.
Many networks include the ability to create a guest network that does not allow for communication with other devices on the network, preventing users from logging into the router or trying to brute-force passwords. These systems should also be isolated from anything critical, and guest networks should restrict any users to their own subnets to minimize the risk of a password being shared. It's also recommended to change your Wi-Fi password periodically, at least once every six months or so, and keep track of who has access.
Finally, practice the principle of least privilege, meaning only give out your password on a need-to-know basis. If someone has a burning desire to get the Wi-Fi password, ask yourself why, and treat it as seriously as giving out a PIN for a bank account. If you don't have the time to secure your network above and beyond what the average person does, don't risk letting anyone in that you don't trust.
WPS PIN Attacks
WPS setup PIN attacks have been widely used since they were discovered, enabling brute-forcing attacks like Reaver to chew through possible setup PIN guesses and break into any affected router in around seven hours. This is due to poor choices in the way the password is validated, and the attack completely bypasses the password set by the user. Even with the most secure, secret password in the world, a router vulnerable to Reaver can be broken into and completely pwned by anyone in range.

The WPS setup PIN typically can't be changed, unlike a password.
While Reaver was scary enough, a new generation of vulnerabilities emerged with the development of WPS Pixie-Dust. This attack took advantage of flaws in the way many routers set random values and dramatically changed the way that hackers took advantage of WPS setup PINs. With WPS Pixie-Dust, an affected router could be compromised in minutes or seconds, not hours.
Once an attacker has your WPS setup PIN, they will always be able to dump your router's password, no matter how many times you change it. Since many routers do not let you change the PIN, this means the router is permanently compromised as long as the setting is left enabled. This will often also get them administrative access to the router and represents a huge hole in the security of a network that has otherwise strong security.
Solution: Disable WPS & Verify with Testing
While many routers offer the convenience of WPS setup PINs, most can be disabled to prevent Reaver or Pixie-Dust attacks from succeeding. To do so, you'll need to log into the settings of your router and look for the part of the page that references the "WPS Setup" or "WPS Access" settings. Once there, disable the WPS setup PIN. Once this is done, restart the router and check to see if the setting is still disabled.
While this may be enough for some routers, some older models may say they've disabled the WPS setup PIN when in reality they still respond to WPS and Pixie-Dust attacks. If you suspect this may be the case, it would be wise to run a tool like Wash, which will locate every network nearby which has the WPS PIN enabled. If your router appears on this list even after you changed the setting, it's probably time to buy a new router.
On Kali Linux, you can run the wash command if you have a compatible wireless network adapter. If you do, put it into monitor mode and type the following to display any nearby vulnerable networks.
wash -i {monitor-interface}You should see something like the output below. Here, we can see a network called TRENDnet on channel 9 using WPS version 1.0. This means the device either has the setting enabled or it might not be possible to disable the setting on that particular model of router.
root@kali:~/reaver-wps-fork-t6x/src# wash -i mon0
Wash v1.5.2 WiFi Protected Setup Scan Tool
Copyright (c) 2011, Tactical Network Solutions, Craig Heffner <cheffner@tacnetsol.com>
mod by t6_x <t6_x@hotmail.com> & DataHead & Soxrok2212 & Wiire & kib0rg
BSSID Channel RSSI WPS Verison WPS Locked ESSID
--------------------------------------------------------------------------------------
D8:EB:97:13:BF:D9 9 00 1.0 No TRENDnetRemote-Access Attacks
While remote access can be a handy feature, having this feature turned on by default is a terrible idea. The reason this is ill-advised stems from the way devices are discovered and indexed on services like Shodan. This search engine indexes any devices with ports which are directly exposed to the internet, such as IP cameras, routers, and IoT devices. While this should not be enabled by default, many devices come with this setting enabled for convenience and also come set with easy-to-guess default credentials.
The risk of remote access comes from two different sources, external and internal. Once a device has been discovered by Shodan, it's only a matter of time before someone, be it a hacker or a bot, tries to log in. When they do, an external attacker will usually be relying on a list of default passwords for that particular device. Once in, they can pivot to other devices in the network. This is especially bad if the router is exposed because an attacker compromising the router can take over the entire network.
The internal risk of this attack is that someone with temporary access via LAN or the Wi-Fi password can enable remote administration and then simply leave and bide their time. Any time they want to connect to the network remotely, they can simply log in with the credentials they set up to do so. Many times routers will have this feature and make easy to enable, allowing an attacker to take advantage of momentary access to plant a permanent back door.
Solution: Disable Remote Access & Port Forwarding
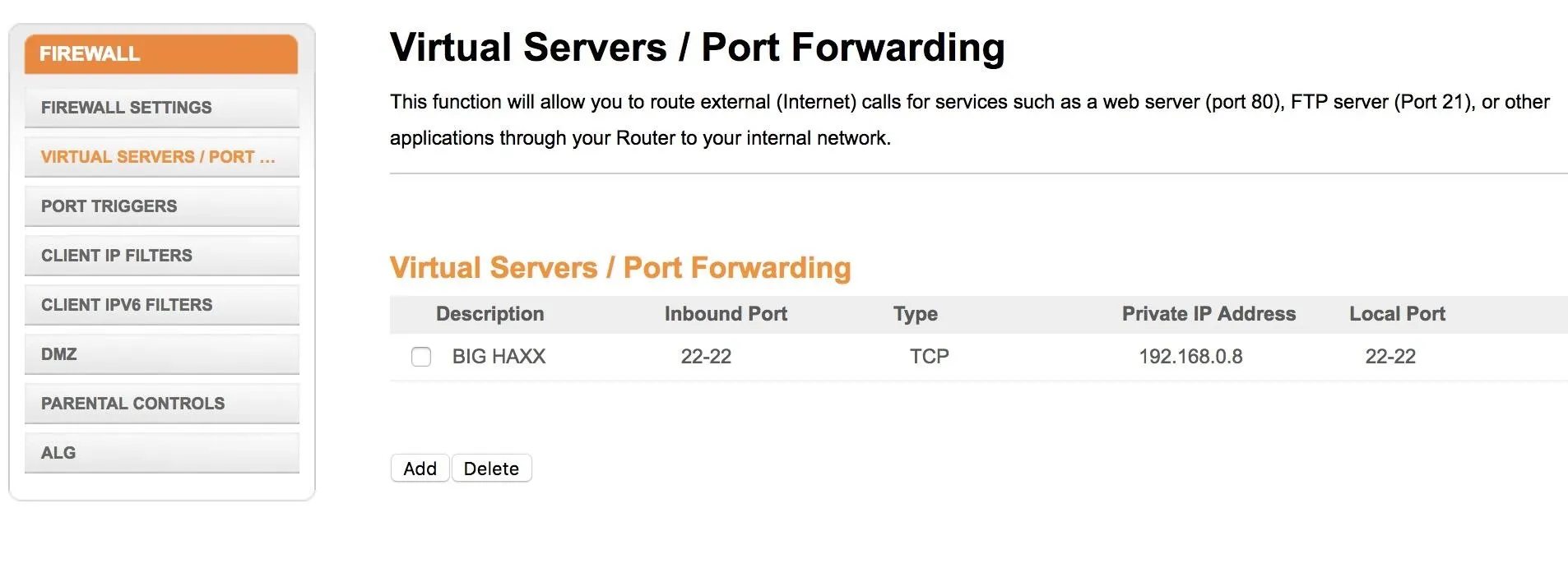
The first step you can take to ensure your devices aren't exposing ports directly to the internet is to log into the administrative portal and look for a tab that mentions "Port Forwarding" rules or settings. This is the section of the router where you can add port forwarding rules, and it may be located under the "Advanced" tab on some devices. When you find the page, you should expect to see no port forwarding rules there, as seen in the image below.
If, however, your router's port forwarding page already has rules entered, you will want to immediately determine if they were enabled for a legitimate or necessary reason. If not, you should disable these settings immediately. While these rules may allow things like access to webcams from an external network or an app, if you don't recognize them, it's generally not worth the risk.
Rogue Access Points
A rogue access point is a W-Fi network designed to trick users into connecting. After doing so, it's capable of stealing passwords, controlling your internet experience, and spying on connected devices. Hackers deploying rouge access points don't need an expensive setup, as there are tools like the Wi-Fi Pumpkin which run on simple, low-cost hardware like the Raspberry Pi.
A simple setup like this can force a user off their normal network with a series of deauthentication attacks. Once the frustrated user finds they can't use their normal network, a similarly named network with no password is provided to tempt the user.
After connecting, this fake network will often act like the router is installing an update or otherwise restarting, and request a password to reboot. While this might seem suspicious, the average user focusing on their work will simply be wanting to deal with the distraction quickly, often entering their Wi-Fi password without a second thought.
Tools like Airgeddon allow tremendous flexibility for a hacker in creating fake APs, and the "Evil Twin attack" module uses a customizable phishing page to allow hackers to automatically generate phishing pages in different languages. While these attacks are impressive, the reason they work is that they trick a user into connecting to a network other than one they trust.
The way your laptop and phone searches for Wi-Fi can also be enough to take over your connection if you use a lot of free Wi-Fi networks that don't require a password. When your phone or laptop sends probe frames asking if any recently connected to networks are available, attackers can create a fake Wi-Fi network with the same name as the one your device is searching for. If the network didn't have a password, your device will connect seamlessly without warning you.
Solution: Spot Signs of a Rogue AP
When you're using Wi-Fi, you should always be aware of what network your computer is connected to. It's easy to test this by turning on the personal hotspot on your phone and naming the network the name of a coffee shop you've used the Wi-Fi of lately and no password. If your computer connects automatically, it's likely that you wouldn't even know if an attacker were to take over your internet connection.
The ways that computers store the wireless networks they've joined isn't very smart, and most computers will automatically join any network with the same name of a network they've joined before. The exception to this rule is if the network has different security settings from the one that was visited prior, like suddenly requiring a password.
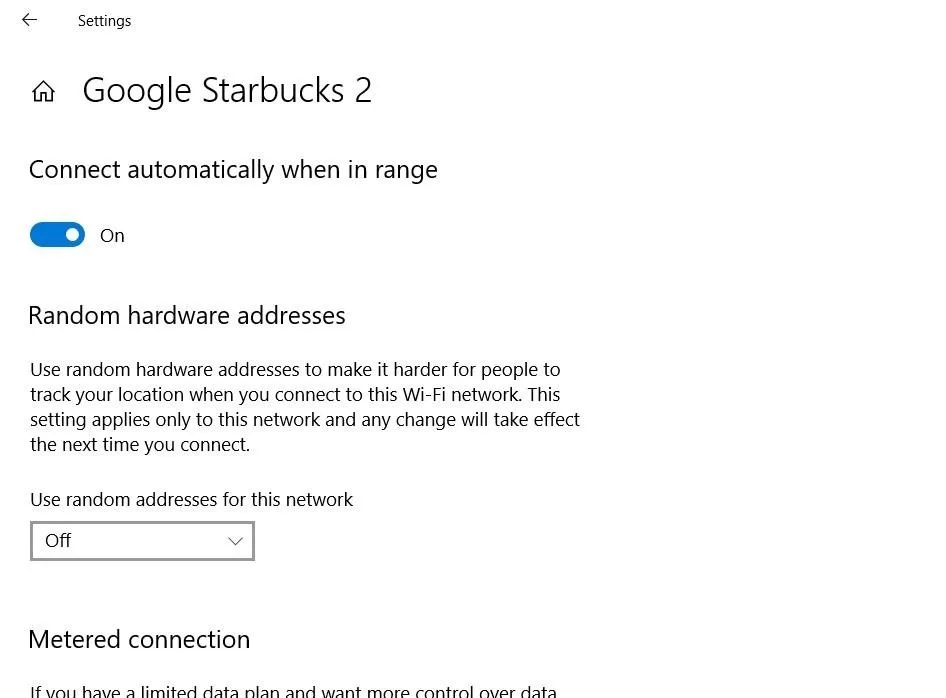
On Windows, you can disable the setting of automatically connecting when in range.
You should go into your computer's Wi-Fi settings and delete any networks you no longer wish to connect to. Above, you can see the wireless settings for a network on a Windows system. Below, a macOS system provides the options to prioritize or delete networks previously joined.
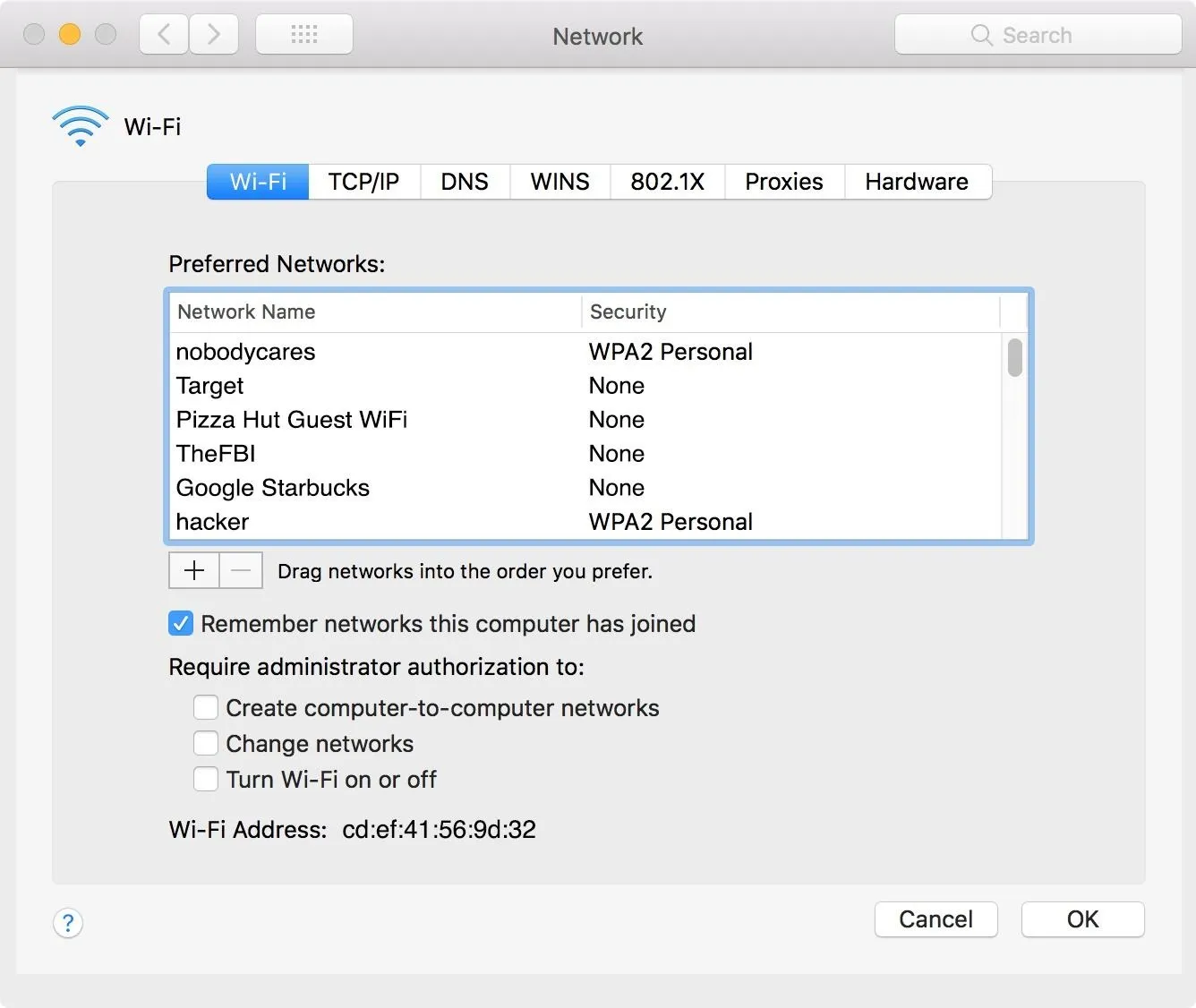
If you don't want your computer's connection to be taken over by a random network you forgot you connected to weeks ago, make sure to delete these and test to make sure your computer doesn't connect to networks with the same name.
Next, it's smart to avoid connecting to unknown networks whenever possible, and instead, use your phone's hotspot or a trusted network. Make sure to use a VPN whenever possible to ensure that even if your connection is intercepted, it won't be as easy as injecting content into webpages to steal your credentials. Even while using a VPN, be suspicious whether it's connecting to a conveniently available "Google Starbucks" Wi-Fi network miles from the nearest coffee shop or just resorting to using a new one when your trusted network doesn't work.
Stay Safe Out There!
Wi-Fi hacking can take many forms, but by hardening your defenses and ensuring there are no easy routes into your network, you can make it a lot harder for someone wanting to break into your network. There are two parts to staying safe when it comes to Wi-Fi, securing your personal Wi-Fi network, and ensuring you're being careful and skeptical when you're using any network you don't control.
In general, VPN services are helpful because they allow you to create an encrypted tunnel of traffic that prevents the owner of the traffic from seeing what you're doing, but this doesn't by any means protect you from the other risks of connecting to unknown networks. Stay safe, and if you need to use Wi-Fi and the only option is a network you don't trust, consider using your phone's hotspot instead.
I hope you enjoyed this guide to defending against Wi-Fi hacking! If you have any questions about this tutorial or Wi-Fi hacking guides, feel free to leave a comment or reach me on Twitter @KodyKinzie.
- Follow Null Byte on Twitter, Flipboard, and YouTube
- Follow WonderHowTo on Facebook, Twitter, Pinterest, and Flipboard
Cover photo and screenshots by Kody/Null Byte (unless otherwise noted)





























Comments
Be the first, drop a comment!