Very often we have processes in Linux that we want to always run in the background at startup. These would be processes that we need to start at bootup and always be available to us.
If we are running a Linux distribution with a GUI (graphical user interface) like Kali or Ubuntu, we need the X11 process to be always running. If we are using Linux as a web server, we probably always want Apache and maybe MySQL to start up at bootup and always be running.
In this tutorial, we will examine how Linux starts processes at bootup and configure Snort, the world's most widely used IDS (intrusion detection system), to start automatically when booting up so that it is available to protect our network without any user interaction.
The Linux Boot-Up Process
To start, we need to examine the Linux boot-up process. In Linux, the boot-up process begins with the BIOS (basic input/output system), then the MBR (master boot record) executes GRUB (GRand Unified Bootloader), then the kernel executes the init (initialization, or first process), and then, finally, the runlevel program is executed from /etc/rc.d.
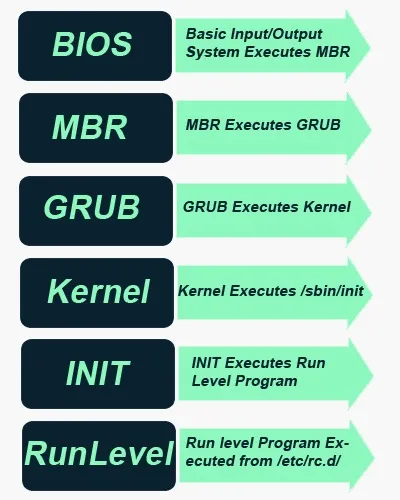
As you probably already know, Linux can be started in multiple runlevels, which are:
- 0 - halt the system
- 1 - single user mode (minimal services)
- 2 - multi-user modes
- 3 - multi-user mode
- 4 - multi-user mode
- 5 - multi-user mode
- 6 - reboot the system
Our Kali, being a Debian-based Linux distribution, usually boots into runlevel 2.
The Init.d Process
Init is the very first process. It is the ancestor of all Linux processes and always has the process ID of 1. As you can see in the screenshot below, init has the PID of 1.
kali > ps aux | grep init
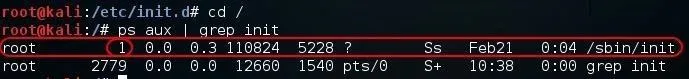
This init process then hands over the boot-up processes to rc.d daemon.
It's important to note here that different Linux distributions handle the daemon start-up process slightly differently. In general, they all use the init process as the first process, but how they hand off to the start-up scripts differs slightly. In this case, we will be looking specifically at our Kali Linux which uses the same procedure as other Debian-based Linux systems.
List the init.d Directory
Now that we have a basic understanding of the boot-up process in Linux, let's see if we can add Snort to the boot-up process in our Kali.
First, let's go to the directory /etc/init.d, the init process daemon directory (not to be confused with inetd). In this directory are all the scripts to start various processes at bootup.
kali > cd /etc/init.d
kali > ls -l
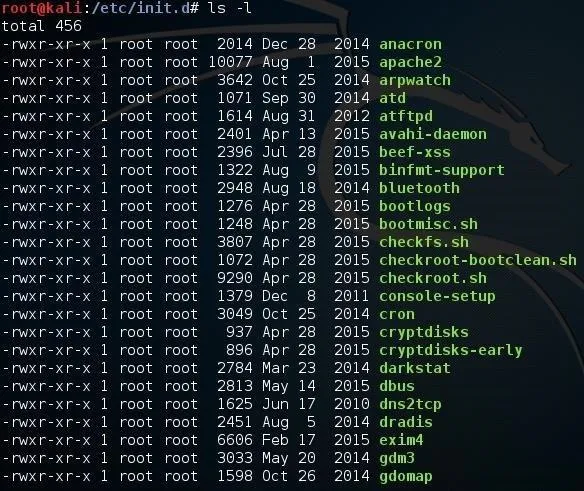
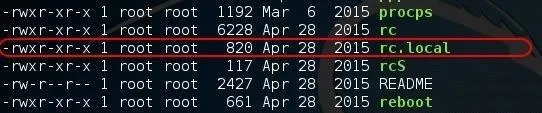
As you can see, these are files that can be executed by init upon bootup. Note, for example, apache2. If we go a bit further down the page, we should find rc.local.
Open rc.local with a Text Editor
Now let's open rc.local in any text editor, which contains a script to start necessary processes in the background when the system boots up. I will be using Leafpad here.
kali > leafpad /etc/init.d/rc.local
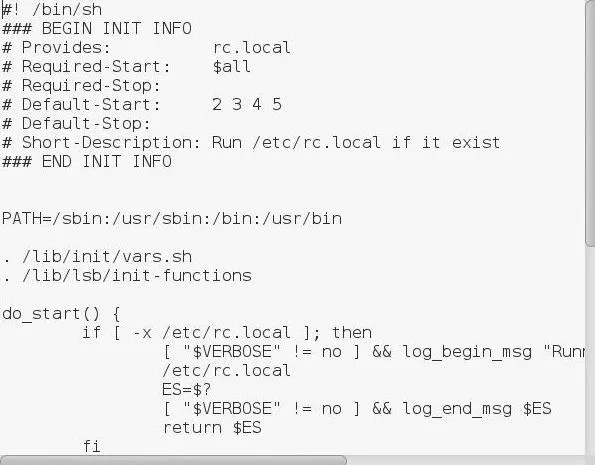
Install Snort
Now we will see if we can use what we learned to get the Snort IDS to always start at bootup. If don't already have Snort installed, do so now. To do so, you can type:
kali > apt-get install snort
The Snort package will downlaod and install. As part of the install, Snort will place a start-up script in the /etc/init.d directory. Let's look there and confirm.
kali > ls -l
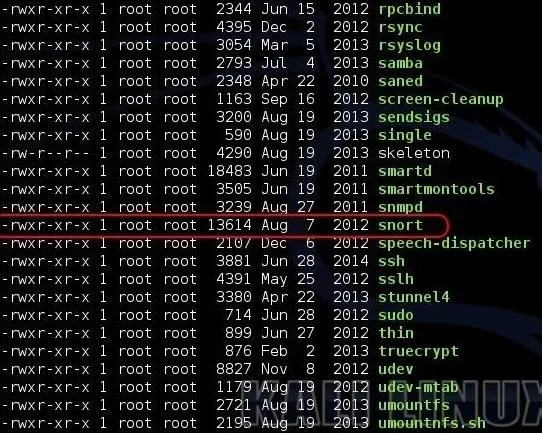
As you can see, Snort has placed a start-up script in the /etc/init.d directory. Now all we need to do is to execute that script each time the system starts.
If you compiled Snort from source code, you may not have this script. In that case, simply create a file named "snort" and save it to the /etc/init.d directory. In that file, place a command to start Snort such as:
/usr/sbin/snort -D -c /etc/snort/snort.conf -l /var/log/snort
Make certain that this script has execute privileges (755).
Strat Snort from rc.local
There are many ways to get a script to run at start up, but probably the simplest is to use the rc.local file. As we saw above, the rc.local file contains a script to start various services upon boot. Now all we need to do is append that file with commands to start Snort.
Let's open that file with Leafpad and add two lines at the end of the file to [1] make certain that the proper interface is up and in promiscuous mode (ifconfig eth0 up -arp) and [2] execute the script that the Snort package placed in the init.d directory (/etc/init.d/snort start).
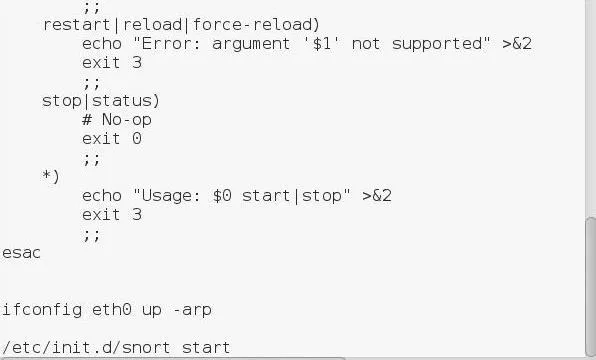
Now whenever your system starts, Snort will always start in the background. Let's test it. Reboot your Kali system and let's see whether Snort starts automatically.
Now that our system has rebooted, let's check to see if Snort is running by typing:
kali > ps aux | grep snort
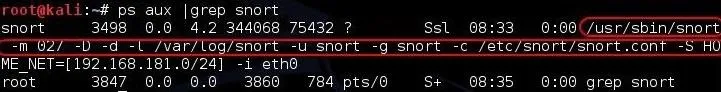
Success! Now our network is always protected by Snort whenever we start our system!
Keep coming back, my neophyte hackers, as we continue to explore the inner workings of Linux to give you the skills to become a professional hacker!
- Follow Null Byte on Twitter, Flipboard, and YouTube
- Follow WonderHowTo on Facebook, Twitter, Pinterest, and Flipboard
Cover image by Justin Meyers/Null Byte; Screenshots by OTW/Null Byte

























Comments
Be the first, drop a comment!