Five Phases of Hacking:-
The five phases of Hacking are as follow:
- Reconnaissance
- Scanning
- Gaining Access
- Maintaining Access
- Covering Tracks
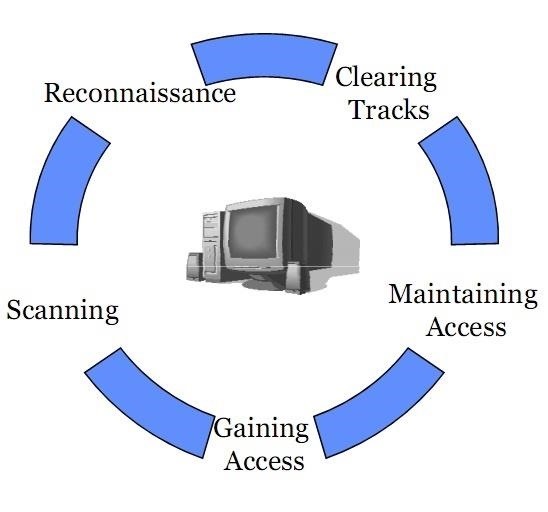
The Five Phases of Hacking
Reconnaissance:- This is the primary phase where the Hacker tries to collect as much information as possible about the target. It includes Identifying the Target, finding out the target's IP Address Range, Network, DNS records, etc.
Scanning:- It involves taking the information discovered during reconnaissance and using it to examine the network. Tools that a hacker may employ during the scanning phase can include dialers, port scanners, network mappers, sweepers, and vulnerability scanners. Hackers are seeking any information that can help them perpetrate attack such as computer names, IP addresses, and user accounts.
Gaining Access:- After scanning, the hacker designs the blueprint of the network of the target with the help of data collected during Phase 1 and Phase 2. This is the phase where the real hacking takes place. Vulnerabilities discovered during the reconnaissance and scanning phase are now exploited to gain access. The method of connection the hacker uses for an exploit can be a local area network (LAN, either wired or wireless), local access to a PC, the Internet, or offline. Examples include stack based buffer overflows, denial of service (DoS), and session hijacking. These topics will be discussed in later chapters. Gaining access is known in the hacker world as owning the system.
Maintaining Access:- Once a hacker has gained access, they want to keep that access for future exploitation and attacks. Sometimes, hackers harden the system from other hackers or security personnel by securing their exclusive access with backdoors, rootkits, and Trojans. Once the hacker owns the system, they can use it as a base to launch additional attacks. In this case, the owned system is sometimes referred to as a zombie system.
Covering Tracks:- Once hackers have been able to gain and maintain access, they cover their tracks to avoid detection by security personnel, to continue to use the owned system, to remove evidence of hacking, or to avoid legal action. Hackers try to remove all traces of the attack, such as log files or intrusion detection system (IDS) alarms. Examples of activities during this phase of the attack include steganography, the use of tunneling protocols, and altering log files.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























10 Comments
This is a good article for new people, there are several of these in this community and honestly I have noticed that people don't follow something like this often.
Like most people wanting to skip straight to phase 3 with little to no regard for phases 1 and 2.
ghost_
Yes exactly, infact every hackathon there is always someone trying to just try 'all the basics' even though that never works, they forget that nmap exists sometimes. I think this is just a fact of beginners, we all have to learn to be patient.
Recon saves you a ton of work in the long run. ^
You would think these people that come here asking for "hacks" should at least bother to learn a bit about hacking. Hopefully they read this post,
They won't.
ghost_
This is for newbie people out there asking how to hack instantly and they actually jumping to phase 3 without the data collected from phase 1 and phase 2.
Im a curious newbie!
What information would you say is absolutely needed from phases 1 and 2 to have a successful phase 3 if I just plan to get into a Home PC? I already have a Skype IP from Skype resolver and social media usernames.
I find it quite amusing because I am a newbie, wannabe, hacker gearing up for retirement (i don't have a rose garden or collect stamps) but I at least have a plan and a lot of patience. The more I read and research the more I need to read and research and articles like this help a lot.
I have recently started studying cpp and loving it, next on my list is networking followed by the nitty gritty building blocks of a couple of OS's.
I'm looking forward to learning a lot from sites like this.
Thank you.
Glad to hear it. It's a rewarding past time.
SO AFTER A YEAR ARE YOU A HACKER NOW?
Share Your Thoughts