Security-Oriented C


How To: Security-Oriented C Tutorial 0xF8 - PE File Infection
How is it goin', fellow 1337 haXX0rZ! dtm here with another article, this time, we'll be looking at infecting PE files, executables in particular for this write-up. Obviously some prerequisite knowledge will be needed since this isn't really newbie-friendly. If you are still a beginner, fear not, it might still be interesting to read! Hopefully!
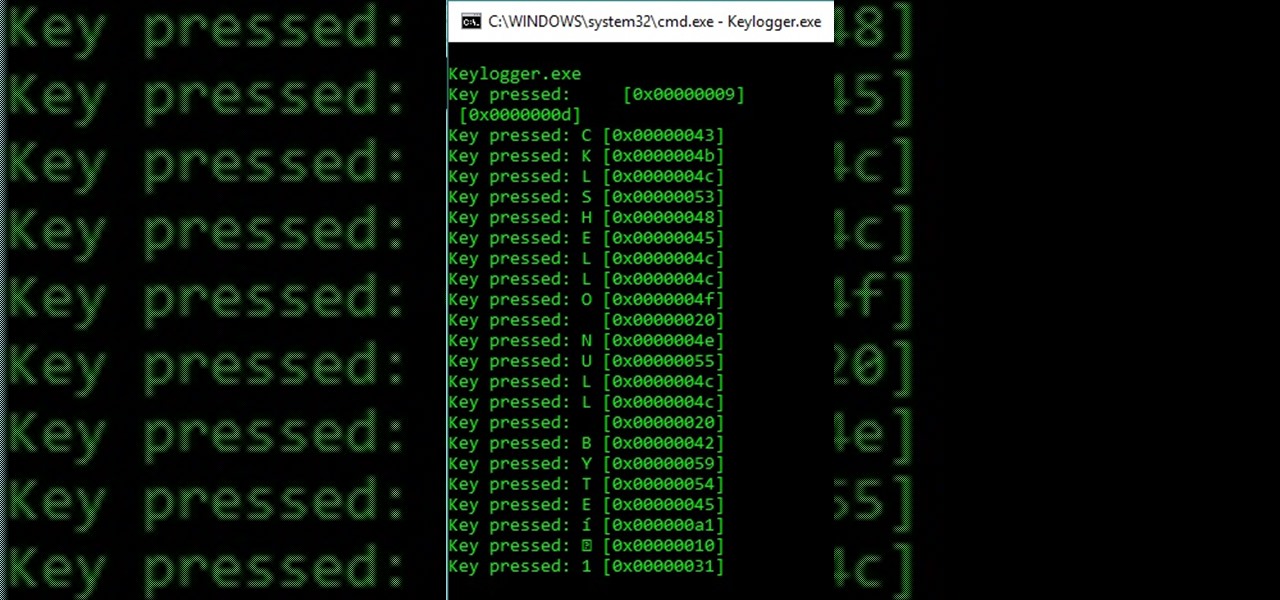
How To: Security-Oriented C Tutorial 0xF9 - I Spy with My Little... Program - Keylogging 101
Yo yo yo, what's goin' on my devilish fiends? Have you come here to learn how to make a keylogger for malicious intent? You sly fox! But in all seriousness, this article will cover quite a simple method for creating the most basic of Windows keyloggers. You're in for a surprise! Let's dive right in!

How To: Security-Oriented C Tutorial 0x22 - Introduction to the WinAPI
It's been a while since I wrote up an article for this series but I did say that I'd be covering some WinAPI. So if you're interested in programming for the Windows platform, hop aboard and follow along.

How To: An Extended Guide on Runtime Crypters
Hello again, folks! I'm back with another (final) guide on runtime crypters which is an extension on my previous runtime crypter guide. If you have not read it yet, I highly recommend that you do since the fundamental theory of the PE format. Again, this will be a Windows-specific guide, so I'll repeat this: If you're a hater and cringe at the slightest sound of Microsoft's grotesque baby, feel free to close this tab, delete your history, exit your browser, pour some oil onto your machine and...

How To: Security-Oriented C Tutorial 0x21 - Linked Lists
Welcome to the final tutorial of the series on standard C. This article will cover the linked list abstract data type (ADT). There will be a lot of abstraction to try to deliver the understanding in the most basic way for easiest interpretation of what they are and how they work, then we will get into the guts of it and learn the technical code underneath. For those who have yet to grasp the concept of pointers, it's advisable that you do that first before approaching this. Having learned thi...

How To: Security-Oriented C Tutorial 0xFA - Enhancing Our Crypter
Hello again, readers! In our previous crypter tutorial, we looked at how we could obfuscate our malware (or any program) by using a simple one-byte XOR key. In this quick tutorial, we will be looking at how a simple little tweak can create a better means of obfuscation. Let's get right into it!

How To: Security-Oriented C Tutorial 0x20 - Problems with popen and Shifty system
How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.

How To: Security-Oriented C Tutorial 0xFB - A Simple Crypter
Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the previous tutorial.

How To: Security-Oriented C Tutorial 0xFC - A Simple XOR Encryptor
Welcome to a tutorial on XOR encryption. We'll be looking at what XOR is and how we can use it to encrypt or decrypt data.

How To: Security-Oriented C Tutorial 0x19 - Functions Part V: Passing by Reference
Hello there! This will probably be the final tutorial on functions where we will be looking over a method called pass by reference. This technique allows us to modify large amounts of data without the overhead and return multiple values. Let's go!

How To: Security-Oriented C Tutorial 0xFD - Software on Steroids - Upgrading Our Malware
Welcome back to a tutorial on malware. We'll be discovering a method to beef up our little trooper. Without further ado, let's jump right in!

How To: Security-Oriented C Tutorial 0x18 - Malloc and the Heap
Hey guys, in this tutorial, we are going to learn about the heap segment and how to use it for storing data in our programs. We will also go into the details of its use in conjunction with the char pointer and struct data types.

How To: Security-Oriented C Tutorial 0x17 - Structs
What's up, peeps? In this quick tutorial, we will be looking at structs, a special kind of data type.

How To: Security-Oriented C Tutorial 0x16 - Functions Part IV: Recursion
Hello again, and welcome back to another tutorial on functions, this time, covering recursion. What Is Recursion?

How To: Security-Oriented C Tutorial 0xFF - An Introduction to Malware
Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.

How To: Security-Oriented C Tutorial 0x15 - File I/O
Hello readers, in this tutorial, we will be discussing how to perform file operations such as reading and writing.

How To: Security-Oriented C Tutorial 0x14 - Format String Vulnerability Part I: Buffer Overflow's Nasty Little Brother
What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may.

How To: Security-Oriented C Tutorial 0x13 - Pieces of a Puzzle
Before we begin learning about another vulnerability, we are going to explore printf in a bit more detail. This will be quick little tutorial.

How To: Security-Oriented C Tutorial 0x12 - Scope
What's up readers? We have ever so slightly touched upon this concept of scope with variables but still don't really know what it means. In this tutorial we will learn the behaviors of variables existing in our programs and within functions.

How To: Security-Oriented C Tutorial 0x11 - Command Line Arguments
In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

How To: Security-Oriented C Tutorial 0x10 - Pointers and Addresses
In previous tutorials we have encountered these things called pointers and addresses but we still don't know what they really are. Let's learn a bit more to clear things up.

How To: Security-Oriented C Tutorial 0x0F - Functions Part III: The Stack
Welcome back to another tutorial on functions. Last time, we looked inside memory to see what functions looked like in the flesh and all that Assembly was pretty nasty. At least you have some exposure to it. This time, we will be examining how functions work with the stack.

How To: Security-Oriented C Tutorial 0x0E - Functions Part II: Memory
In the last tutorial, we learned how to make functions and how they work on the high level. This time, we will take a peek under the hood again, stare deep into its soul and see its ugliness face to face to see how it works in the lower level.

How To: Security-Oriented C Tutorial 0x0D - Functions Part I: Introduction
Welcome to a tutorial explaining functions. This article will help clarify some things we have already been exposed to such as function prototypes, function calls, return values, etc.

How To: Security-Oriented C Tutorial 0x0C - Buffer Overflows Exposed!
Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show.

How To: Security-Oriented C Tutorial 0x0B - User Input
Hey readers! This tutorial will be the entry point for the introduction of buffer overflows. Something like requesting user input is a very common place for vulnerabilities to pop up and we will definitely have fun while trying to make programs crash. But for now, let's start with how we can get input from a user.

How To: Security-Oriented C Tutorial 0x0A - Man Pages
Okay guys and gals, this will be a quick tutorial on using the incredibly helpful man pages. What Are Man Pages?

How To: Security-Oriented C Tutorial 0x09 - More on Strings
What's up guys! It's time to discuss strings in more detail. Review

How To: Security-Oriented C Tutorial 0x08 - A Trip Down Memory Lane
Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear and focused when reading the following article because it may prove to be confusing. Also, if you do not understand something, please verify all of your doubts, otherwise you may not completely understand when we touch on...

How To: Security-Oriented C Tutorial 0x07 - Arrays and Strings
Welcome to another C tutorial. We will be looking at arrays, discussing what they are, when they are used and their special relationship with the char variable. Let's begin.

How To: Security-Oriented C Tutorial 0x06 - Operators
Hello again! In this tutorial, we are going to go over something called "operators" which will help us build upon conditions of control structures and also some variable manipulation. Without further ado, let's dive in!

How To: Security-Oriented C Tutorial 0x05 - Control Structures Part II: Loops
Welcome back to control structures, part two featuring the three types of loops. Here we go! What Is a Loop?

How To: Security-Oriented C Tutorial 0x04 - Control Structures Part I: If Statements
Welcome back to another C tutorial, this post covering the first part of control structures, if statements. Let's get right into it.

How To: Security-Oriented C Tutorial 0x03 - Bits, Bytes, Broken?
Hey there, reader! In this tutorial we are going to explain how values are stored in variables as either signed or unsigned. Try to not get lost!

How To: Security-Oriented C Tutorial 0x02 - Variables && Data Types
Hello again, reader! In this post, we are going to cover some data types and how to declare variables. It shouldn't be too hard so just sit back, relax, grab some popcorn and enjoy the ride (while you still can!).

How To: Security-Oriented C Tutorial 0x01 - Hello, World!
Welcome back, reader! In this tutorial, we will be covering our first program! So let's get to it. We all know the unspoken tradition of the first program when learning a language and of course, here we will respect and complete it. Fire up your favorite text editor (be it vim, emacs, gedit, it's all the same to me, no h8) and try to keep up.

How To: Security-Oriented C Tutorial 0x00 - Introduction
Hello there, reader! If you've clicked on this How-to then it means you are interested in learning some C programming or just generally curious about what this page has to offer. And so I welcome you warmly to the first of many C tutorials!







