Welcome back, my hacker novitiates!
Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.
DIRB, developed by The Dark Raver, is a tool designed to find these objects, hidden and unhidden. Since it is already included into Kali, there is no need to download and install anything. For those of you who need to download it, it is available here.
Step 1: Open a Terminal
The first step, as usual, is to fire up Kali and open a terminal.
Step 2: Start DIRB
Once we have a terminal open, go ahead and type dirb to get the help screen.
kali > dirb
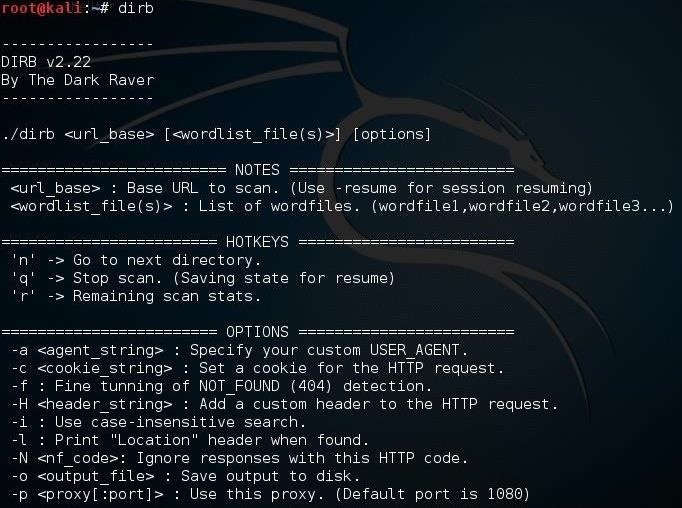
As you can see in this screenshot above, DIRB's syntax is very simple with multiple options. In its simplest form, we only need to type the command dirb followed by the URL of the website we are testing.
kali > dirb URL
Step 3: Using DIRB for a Simple Hidden Object Scan
It's simplest form, DIRB will scan the website looking for 4,612 object types. Let's try it on our favorite test site, webscantest.com.
kali > dirb http://webscantest.com
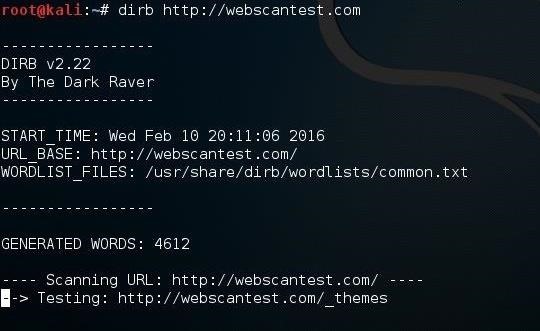
DIRB begins the scan looking for those keywords among the website objects.
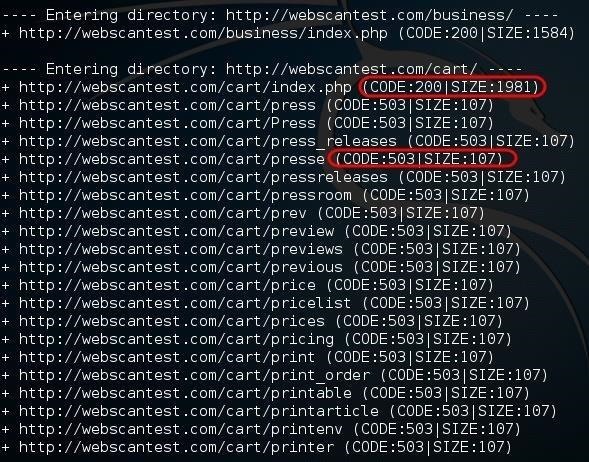
When DIRB finds a good directory (Code 200), it then begins to look inside that directory for additional hidden objects. Code 503 indicates "temporarily unavailable."
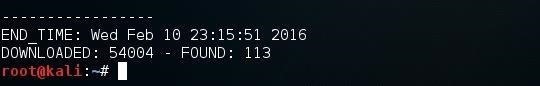
Finally, when DIRB is done, it reports back the number of found objects (113 in this case). Note that in the help screen above, we can use the -o switch to send the results to an output file to save the results to a text file.
Step 4: Testing for Special Vulnerable Lists
We can use DIRB to test for specific vulnerable objects within specific types of web technologies. Each web technology has different vulnerabilities. They are NOT all the same. DIRB can help us look for specific vulnerable objects specific to the particular technology.
In Kali, DIRB has specific wordlists to search for these vulnerable, often hidden objects. You can find them at:
kali > cd /usr/share/dirb/wordlists/vuln
Then list the contents of that directory:
kali > ls -l
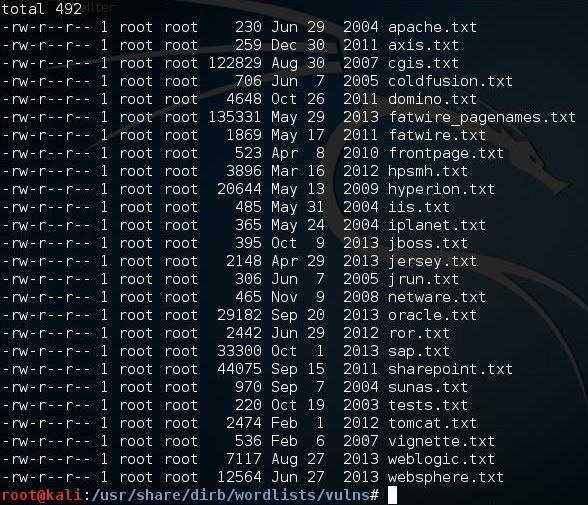
As you can see above, there are numerous wordlists that contain keywords of vulnerable objects in different web technologies such as Apache, ColdFusion, FatWire, ISS, JBoss, Oracle, SAP, Tomcat, WebLogic, and many more. Since I suspect my website is running Apache as a web server (I could do a banner grab or use httprint to make certain), it makes sense to try the apache.txt wordlist first.
We can now build our dirb command to use that Apache vulnerable object wordlist by typing:
kali > dirb http://webscantest.com /usr/share/dirb/wordlists/vulns/apache.txt
When we hit enter, DIRB will scan the site looking for vulnerable objects from the apache.txt wordlist.
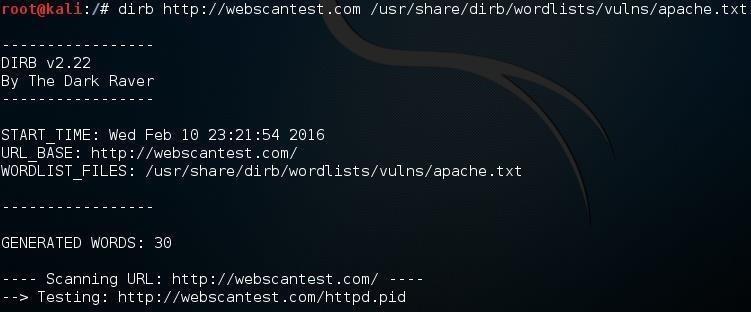
Now, DIRB will use that Apache list to look for known vulnerable objects. If it finds any, then you can take the next step and look for an exploit to take advantage of it in Exploit-DB, Metasploit, SecurityFocus, or any of the other many exploits sources on the web. Of course, you must use the vulns wordlist appropriate to the technology being used in the website. For instance, if it is a Windows IIS server, you should use the iis.txt wordlist.
Keep coming back, my hacker novitiates, as we continue to explore the technologies and techniques of the most valuable skill set of the 21st century—hacking!
Just updated your iPhone to iOS 18? You'll find a ton of hot new features for some of your most-used Apple apps. Dive in and see for yourself:






















3 Comments
I would recommend you dirs3arch: https://github.com/maurosoria/dirsearch for that purpose. It´s fast python based: Multithreaded
Keep alive connections
Support for multiple extensions (-e|--extensions asp,php)
Reporting (plain text, JSON)
Heuristically detects invalid web pages
Recursive brute forcing
HTTP proxy support
User agent randomization
Batch processing
SIMON SESSLER,why dont you make a tutorial on dirs3arch??
whether when we run the dirb command we are required to use our wlan0 macchanger
Share Your Thoughts