Welcome back, my budding hackers!
Recently, I showed you how you could exploit the widely disseminated OpenSSL vulnerability that has to become known as "Heartbleed". Although the world has known about this vulnerability for over a month now, it will likely take many more months—or even years—for everyone to close this vulnerability.
Last week, Errata Security scanned the Web on port 443 looking for servers still affected by Heartbleed, and found over 300,000+ servers possibly still vulnerable, as compared to the 600,000+ from a month ago. If history is any judge, some websites will likely never patch this vulnerability. If that is the case, we can keep using this exploit for some time to come.
In this tutorial, I will show you how to test a website/IP address to determine whether the Heartbleed vulnerability is available to you.
Step 1: Open Kali & Nmap
The first step is fire up Kali and get an nmap prompt. Fortunately, nmap is in our PATH variable and we can run it from any command prompt. The folks at insecure.org (Fyodor and friends) developed a script that scans a website to determine whether it is vulnerable to the OpenSSL vulnerability. That is what we will be using here.
Step 2: Download Heartbleed Scanner
With Kali open, we first need to download and install the Heartbleed scanner script for nmap. You can find it here. Download and save it to the directory /usr/share/nmap/scripts.
Of course, you can just copy and paste it into the Leafpad text editor in Kali (or any text editor) to the same location.
Step 3: Download & Install the Library File
The nmap Heartbleed scanner requires a special library file to be effective. That file is tls.lua. Download it here or copy it to usr/share/nmap/nselib.
Step 4: Run It Against Websites
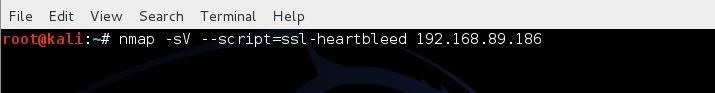
With the Heartbleed script and the tls.lua library in place, we now are ready to begin hunting for vulnerable websites. The syntax for running this script is:
nmap -sV --script=ssl-heartbleed 192.168.89.186
Remember, I'm running it against a web server in my lab on my LAN here. When running against web servers on the Internet, simply replace my private IP with the public IP of the web server.
If the website is vulnerable to the Heartbleed attack, it should get results similar that below.
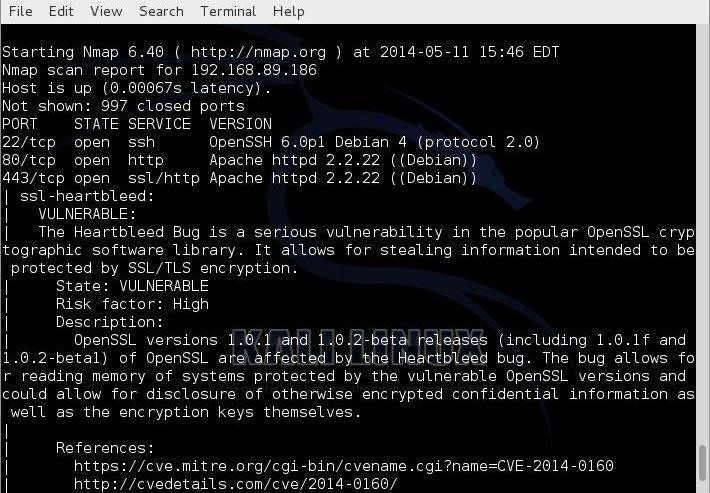
As most web administrators are slow to patch vulnerabilities, many web servers are still vulnerable to the Heartbleed attack. You can use this tool to find those servers and then use the Heartbleed exploit to extract critical information from the memory of the server, if it is vulnerable.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















27 Comments
OWT:
Could we also scan the Internet by picking a ip address range and adding like /500 to the nmap scan.
Jon:
nmap syntax will allow you to scan a range of IP addresses. Some possibilities include CIDR syntax such as 192.168.1.0/24 (256 IP addresses) or 192.168.1.0/16 (65535 IP addresses). In addition, you can simply list the IP's to be scanned separated by commas (you can also input a list with the -iL switch). Lastly, you can use something like 192.168.1-255 which will also scan 65536 IP addresses.
Hope this helps.
OTW
OWT:
nice thanks 65k ip address's should be more than enough.
One of your best articles btw :)
Thanks Jon. That means a lot coming from you.
OTW
Thank you soo much.
Evil Genious
am getting the error
Starting Nmap 6.40 ( http://nmap.org ) at 2014-05-13 15:44 CEST
NSE: failed to initialize the script engine:
/usr/bin/../share/nmap/nsemain.lua:779: 'ssl-heartbleed' did not match a category, filename, or directory
stack traceback:
C: in function 'error'
/usr/bin/../share/nmap/nsemain.lua:779: in function 'getchosenscripts'
/usr/bin/../share/nmap/nsemain.lua:1271: in main chunk
C: in ?
QUITTING!
Hey, good job with your posts again! Just saying that kali linux updated Nmap in it's latest update and Nmap 6.45(latest) already comes with ssl-heartbleed script :)
Hello,
when i attempt to do this scan it does not show the ssl-heartbleed section and only shows the results of open ports and OS. i have checked to make sure that the files are in the right place and have nmap 6.46 that has this script built in. How can i get this to work?
I found why it didnt seem to work, it shows no output when the server is not vulnerable so i added --script-args vulns.showall to show even when it was not vulnerable and it worked.
root@xxx:~# nmap -sV --script=ssl-heartbleed XXX.XXX.XXX.XXX
Starting Nmap 6.45 ( http://nmap.org ) at 2014-05-14 14:31 CEST
Nmap scan report for xxx.com (XXX.XXX.XXX.XXX)
Host is up (0.031s latency).
All 1000 scanned ports on xxx.com (XXX.XXX.XXX.XXX) are filtered
Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 33.02 seconds
------------------------------------------------------------------
What does this result mean?
Anonymous:
It appears that you can't reach the server because of a firewall. Try it at another IP address.
OTW
Thanks a lot for your fast response OTW. Is there any way to make nmap tell you if a firewall is there? Sounds like firewalls make reconnaissance impossible.
No, not impossible, but more challenging. There are many ways to get past firewalls, but that is another tutorial.
does doing nmap -sS ------------------- makes me evade the firewall? or scanning in sneaky mode(hours) make me dodge the firewalls??? thanks
I wish it were that simple. Neither will work.
lol...then i will humbly ask for a tutorial...as you can see...we all need it :D
OK
LionKing and Anonymous:
Very often, the firewall will block pings and therefore block the scan. nmap, by default, send out an ACK to port 80 and an ICMP (ping) before scanning to check to see if the system is up. If these are blocked by the firewall, it will report the system as down. Try running the scan with the -P0 switch to suppress the ping. This may help get you past the firewall.
OTW
The fracturing option is also possible... need to learn more about it, though. After seeing how easily they block any traffic, I feel a bit unprotected having no firewall on my Linux. Is there a general tutorial about how networks manage their ports? Have read about TCP/IP only yet.
ok so i found this to avoid firewalls...
http://pentestlab.wordpress.com/2012/04/02/nmap-techniques-for-avoiding-firewalls/
King:
Have you tested these to see if they work?
OTW
Yeah any PoC?
no..i haven't...i just thought of sharing first...I'm gonna try them later...schedule soo tight
Ok. Report back to us , please.
All of those techniques will work on some firewalls, but all firewalls are different. You may have to mix and match techniques to get past some firewalls.
Ok OTW..I will report back asap
Hello Null-Byte ! I am new to linux world. Can anyone please tell me how to get an i.p. of a website ? I tried to ping it but when I enter the i.p. in url bar ,i got a different website. Please help. Thanks in advance
ROBOCOP
to get ip of a website you just need to run ping command in your terminal or host command .
ping google.com or host google.com in your terminal
your ping command works very well in your windows also
Share Your Thoughts