Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use your network as a spring board for who knows what. When the police come a few days after, they are coming to your door—and not to talk about how nice your lawn is. Don't be that guy.
Step 1 Find Your Router!
No, not the actual physical router you have plugged in downstairs. You need to navigate over to your router configuration page. The actual GUI makeup will probably vary based on your ISP and your hardware, but the general ideas will apply across the board. I have access to some AT&T equipment in this lab, so we will use that for screen captures wherever possible. Your mileage may vary though. Leave me a comment if you have any trouble with this step.
But first, we need to find your router. This is done by locating the address of your default gateway. In Windows, we can peek at our interfaces with:
> ipconfig
Linux users can type:
$ route -n
And get this screen, showing the kernels routing table.
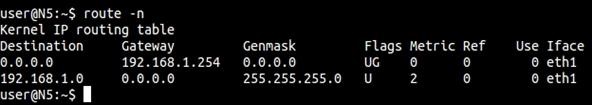
In both instances, the address under Gateway is the one you want. Here, it's 192.168.1.254. All we need to do in most situations is pop that address into our web browser, shown below.
If 192.168.1.254 doesn't work for you, the 3 other most common router IPs are 192.168.1.1, 192.168.0.1, and 192.168.100.1.
Let's take a look at a few more tips in detail.
Step 2 Use Encryption!
- WEP (Wired Equivalent Protection) 64-bit and 128-bit: WEP is an old, outdated wireless encryption standard. Never use WEP encryption, which can be hacked within seconds. Never ever. In fact you should make fun of your friends that do.
- WPA (Wi-Fi Protected Access): WPA is also referred as WPA-Personal. This is a new version of the wireless encryption standard and more secure than WEP. Most of the wireless adapters on your laptop will support WPA.
- WPA2: This is the latest wireless encryption standard that provides the best encryption. Always use WPA2, if both your wireless router and laptop wireless adapter supports it.
Like stated above, the newest and most secure kind of encryption is WPA2. Both WEP and WPA have been outpaced, so I would implement it over the other choices. I would trust my grandmother with a broomstick sitting on a bench outside over WEP.
Step 3 Change the Name of Your SSID!
Service Set Identifier, or SSID for short, is the name of your wireless access point. Well, it's the name other machines use to associate with it anyway, but you get the idea. Usually this is something the manufacturer sets by default. For example, AT&T uses 2WIRE routers, and the SSID on those are 2WIRExxx.
Plainly, this is a security problem. An attacker now knows the make and ISP of your router just from its name. Change it to something else, something funny maybe. Mine is Pretty Fly For A Wi-Fi.
Pro Tip: AT&T, among others, places the default system and network encryption keys on the actual router. In the case of AT&T, this is a string of numbers. If an attacker were able to get any kind of physical access, they could simply copy down the password.
Step 4 Filter Those MAC Addresses!
With the SSID issues covered, we can move deeper into our defense in depth. If you remember from my article, MAC addressing is a layer two (datalink) function and we like the idea of sorting out users based on it.
You can find your MAC address by typing:
$ ifconfig
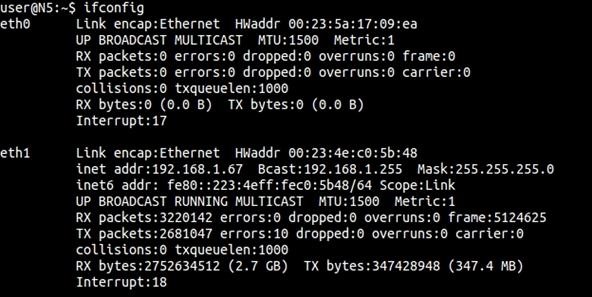
The HWaddr, or hardware address, is the one you want.
With MAC address filters, you go into your wireless router and enter your network adapter's MAC address. For every device you want to be able to access your Wi-Fi, those are the only ones that will be able to get access.
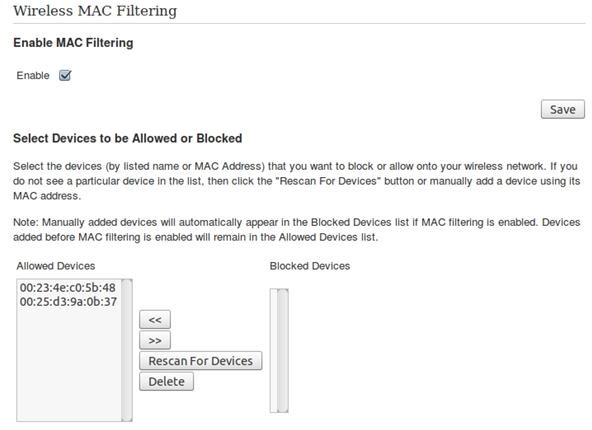
MAC filtering should be one of the first security items you set up after buying new hardware or moving around. I should point out that like the other steps, this is not an end all security fix, but more of layer to put in place between an attacker and yourself.
I say layer in this case because you can change a MAC address on Linux simply by typing:
$ ifconfig eth0 down
This brings the network interface (eth0 in this case) down, then type:
$ ifconfig eth0 hw ether [new MAC address]
Then bring the interface back up with:
$ ifconfig eth0 up
Step 5 Use the Router Firewall!
The job of the router's firewall is to help you protect your computer from unauthorized access from anybody within your AP's vicinity and that's why you need to enable it if it's not already.
Firewall works just like the name sounds—it helps your computer by staying in-between your machine and the other third-person or device that's trying to access the computer's network and will not allow them to have access to the connection unless permitted.
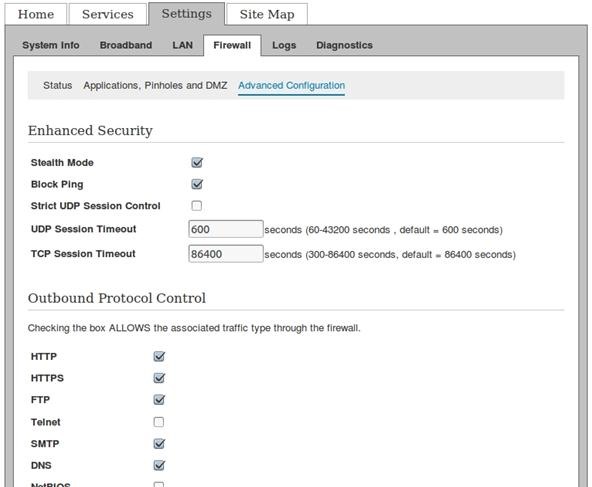
Most routers have easy-to-follow GUI interfaces listing common ports and even common applications and games sometimes. Another good feature to look for here is the firewall logs, and you should make it a habit to check these often. As you get used to seeing what normal traffic looks like, spotting abnormal and potential attacks will become more and more easy.
Step 6 Cloak Your SSID!
Wireless network cloaking in a nutshell is hiding the broadcast of your SSID to the public.
Hiding your SSID will only prevent casual kiddies from snooping around and trying to compromise. It shouldn't be considered a strong security measure, but more as a security precaution.
There are many programs that are able to scan for wireless networks, including hidden ones, and display their information such as IP addresses, SSIDs, and encryption types. These programs are capable of "sniffing" out any wireless networks in range by essentially eavesdropping and analyzing network traffic and packets to gather information about those specific networks.
This is another layer you can use, but understand you will need to provide the SSID each time you want to connect to the network.
Step 7 Disable Remote Admin Access!
Some routers have remote access enabled by default and others do not. Some require you to set up port forwarding and other have this done already. Your mileage will vary again, but it is worth the time to look into your specific hardware and check.
Remote access means someone outside of your network can point a web browser (or other network application) to your network with the correct port and log into the router. My opinion is to turn off this service, as most people will have no need to pop in and out of their router often.
This can be a tough one to do, since you may need to make changes to your router when you are home or traveling. However, you can be assured that the casual attackers will bypass your network if it's too much of a pain.
Step 8 Change the Default Admin Password!
Routers ship with default passwords so you, the user can configure them as needed. Sadly, a large amount of people just leave the password as is, presenting a massive security hole.
In Closing
If you followed all seven steps, your network should be a notch more secure than it was before. You are not immune, but someone will have to employ a few more tactics before they can start working on your machines.
Want extra security? Don't use wireless. Even with all the encryption and settings, the fact is you are still openly sending traffic and stripping a physical means of protection, your Ethernet cable. This is a threat model that doesn't apply to everyone though, so take your security needs into consideration when applying your personal policy on the network.
Did I miss a step? Do you have solid security ideas here? Leave us a comment, shoot me a message, or visit our forum!
Follow us on Twitter @NullByteWHT and on Google+!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.
























6 Comments
showing error. could not be retrieved....
Another good trick I use. Many access-points offer the ability to lower the TX power. By default this is typically set high to provide good coverage. By experimenting you can reduce this value to a level that suites coverage needs yet doesn't overextend the signal to unwanted visitors.
Nice article. The recent discovered flaw in WPS is also an issue since a lot new devices have it 'on' by default.
root@root:~# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 0.0.0.0 0.0.0.0 U 0 0 0 ppp0
10.0.0.1 0.0.0.0 255.255.255.255 UH 0 0 0 ppp0
101.0.0.0 0.0.0.0 255.0.0.0 U 0 0 0 eth0
WTF?
u mad bro
.... you from grate lakes
anyhow another tip if you go online and it asks you to retype your password dont be that guy
who is an idiot..... people can post sights from there computer and you will auto connect to it depending on your settings and wala you just gave them your password.
also check common dictionary's that are popular like backtracks darkcode.list
and all of gotmik,,,, http://g0tmi1k.blogspot.com/2011/06/dictionaries-wordlists.html
there are several others but basically don't use your name or a common just numbers .... use more then the standard 8 digits because an external server can brute force an 8 digit one in reasonable time
o and clocking your ssid dose nothing don't even bother its only annoying
when friends go to your place and want to connect
Share Your Thoughts