The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.
Today, I'll show you how to run a web domain through both a WHOIS query and through an email-to-domain query. This will let us build a profile on a target, and ultimately, link the results to entries in primary-source data (like business filings and government databases) that contain a wealth of information.
The internet is a rich source of data about people, organizations, and the various records and registrations they leave behind through their journey on the web. The Operative Framework tags, collects, and correlates this information. Taken together, it becomes simple to create a complete picture of a person or business from within a familiar framework interface.
Lightweight OSINT Scripts for Specific Tasks
The amount of information that can be accessed with a few keystrokes often surprises people who submitted the information into the public domain in the first place, without knowing how easy it would be to find. Tools like theHarvester can turn up the personal and work email addresses of a target, which can be run through the Operative Framework to fingerprint and expand our knowledge of a person by mining the data for relationships.
Tools like Maltego are robust frameworks to conduct investigations, but lighter OSINT modules and scripts exist to accomplish more specific OSINT investigations.
A favorite of mine is the Operative Framework (obviously), which provides a uniquely well-equipped suite to conduct reconnaissance on individuals or organizations from online databases. The Operative Framework allows you to conduct reverse WHOIS queries to email addresses and other information to correlate information. This creates a detailed overall picture by stitching together many details about a person or business from WHOIS and social directories.
The Operative Framework for Domain Reconnaissance
This tutorial will focus on installing the Operative Framework and running the email-to-domain tool to use found emails and discover other domains owned by an individual. While many people register their domains privately, domain registrars can leak the information anyway. Using research or scraping tools, or even just a person's business card, we will discover if they own any domains related to that email account.
This tool is most useful to run against businesses, business owners, and anyone likely to own online domains. It is possible to determine what kind of business a person is in, what assets they own, and other information by examining the web domains they have purchased to support such projects.
Step 1: Installing the Operative Framework
We will need Python to use the Operative Framework, but the benefit is that this allows the tool to run on macOS (aka Mac OS X), Windows, or Kali Linux. You can set it up by cloning the Git directory by typing the following into terminal.
git clone https://github.com/graniet/operative-framework.git
cd operative-framework
pip install -r requirements.txt
python operative.py
If you don't have pip, you can get it by running the following and installing via the python setup.py.
git clone https://github.com/pypa/pip.git
Step 2: Running an Email to Find Associated Domains
The Operative Framework is more similar to Metasploit than it to theHarvester. You can run modules which require you to set variables to then execute the module. You can examine the list of modules by typing modules.
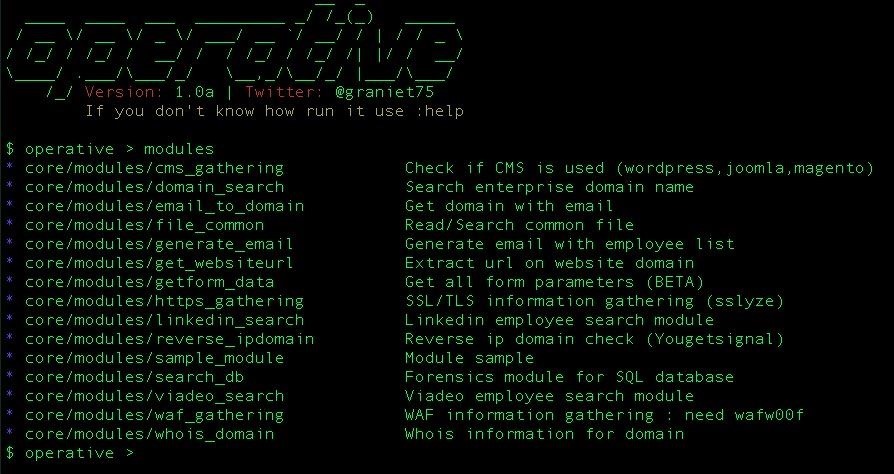
To select a module, you'll type use (the path of the module to use).
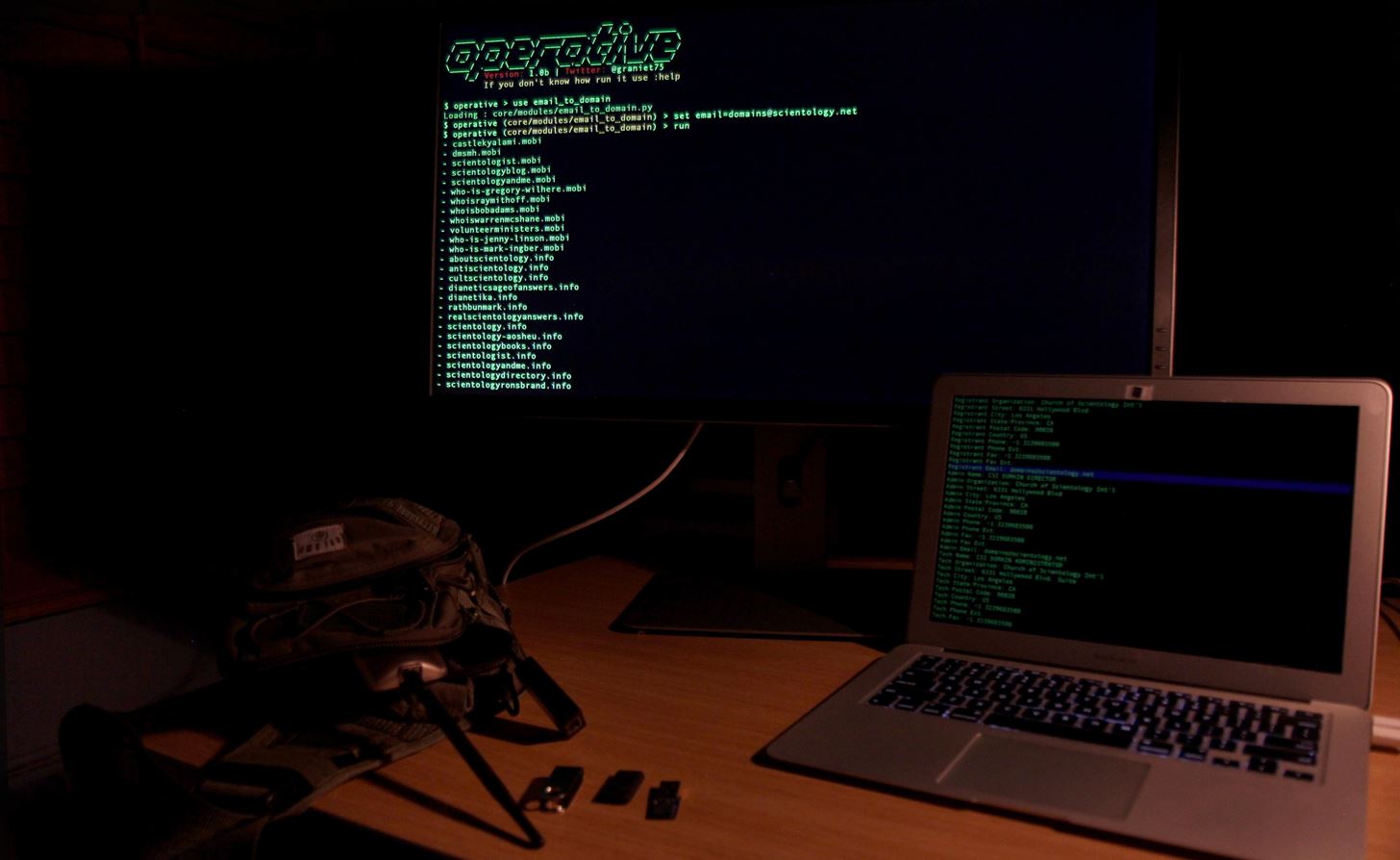
In this case, we will be running an email-to-domain search. First, let's generate a sample to run through our list. We will run a domain through the WHOIS module to pull an email address and see if the registrar owns any other domains. To load the WHOIS module, type this into the terminal:
use core/modules/whois_domain
Once we are in a module, we can see the available options by typing the following.
show_options
It is fussy about the underscore, and doesn't understand any other way of asking about options. In this case, we're trying to learn some info about technology, so let's use the random example technology.info.
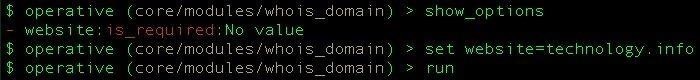
Here we see that "website" is the only unset option. Let's set this as the example with the following.
set website=technology.info
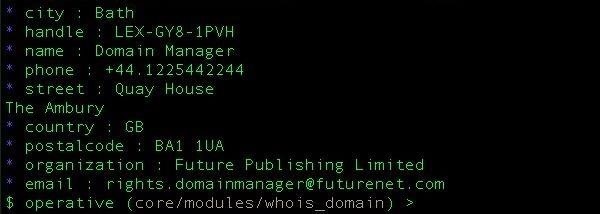
Bam! We get an email address for us to feed into the reverse domain tool. Type Control C to go back to the main menu, and then load the email to domain module by entering the text below.
use core/modules/email_to_domain
show_options
We will set our sample email the same way we set the website in the last module. Run the following.
set email=rights.domainmanager@futurenet.com
Run show_options to confirm the variable is set and then type run to begin the search. Here, we can see the results of the module. If the target does not own any domains, you can expect to see no results.
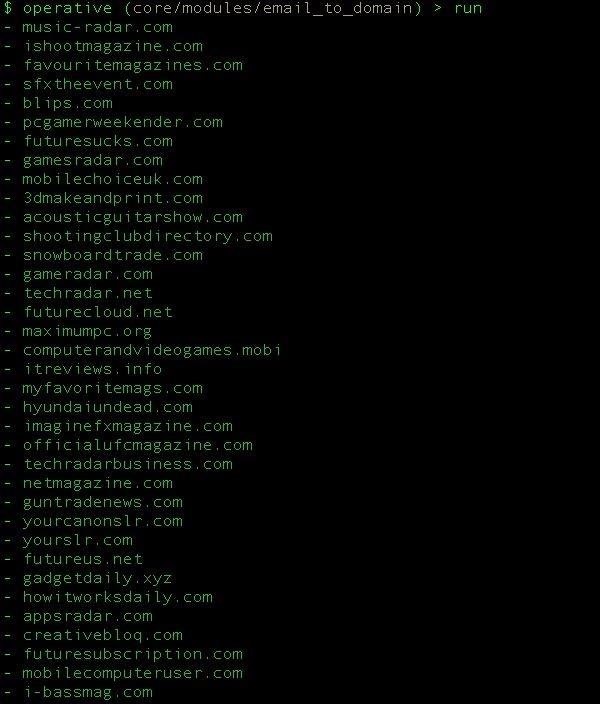
Step 3: Building a Profile from the Results
In our example, our search brings us back to an umbrella of domains owned by a single entity. When the website for the active entity on the domain is visited, it seems the business is a domain management portfolio specializing in technology-related domains.
This is the point at which we can make some decisions about where further information can be found to definitively correlate a person behind an email or domain. The Operative Framework contains a fingerprinting framework database to help collect and organize details about a target, which I will teach in future tutorials.
To expand our search, we should combine our domain pull with a query to a city, state, or local government agency database to provide primary source information.
Step 4: Cross-Referencing Results for a Fix
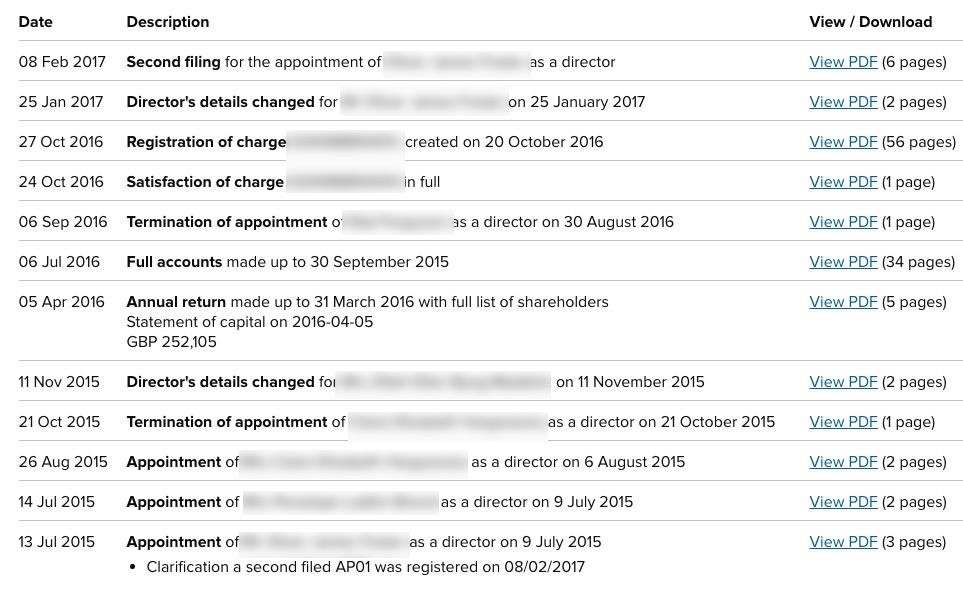
In our example domain, I narrowed the search to target the director of the business. Via the main domain, I see they have a California subsidiary, which means it's worth running a check with the California Secretary of State database.
No luck there for corporations or LLCs, but the UK equivalent for their home office has a bounty of information including corporate filings and other information about the current staff and directors. In those documents, I was able to find the executive director's personal details including date of birth and individual email address for contacting.
OSINT Is an Investigation, the Question Matters
The Operative Framework is a tool to help you pull clues together to fill in pieces of an investigation. By running queries on who owns a domain, and an email-to-domain query to assess what other domains they own, you can quickly assess a target.
A target business's operations, locations, and other information is easy to infer from this data. Here, we were able to go from a randomly selected domain to the ability to contact the director of the company who owns it through a series of database pulls.
An important note about OSINT tools — you must have a goal with your investigation, and the question you are answering must make sense. If it doesn't, your answer will not make sense either.
You can ask me questions here or @sadmin2001 on Twitter or Instagram.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















17 Comments
After 'pip install -r requirements.txt' both Kali and Ubuntu distros return following "command "python setup.py egginfo" failed with error code 1 in /tmp/pip-build-mJdbbd/json". Framework available to run, but fails after trying to use any module.
Check which version of python you have installed
What version of python must be installed and how do you check the version am new to kali but am getting great help here
#still facing the same error as above
2.7.12+ on ubuntu, 2.7.13 on kali
01v, type in 'python -V' in terminal
KANGAROO2 Thanks
Although thats the exact version i have 2.7.13 but am still facing the same error
I love this website!! Thank you.
I'm getting a slightly different error that I hope my post will help with..
root@kali:~/operative-framework# pip install -r requirements.txt
Requirement already satisfied: requests in /usr/lib/python2.7/dist-packages (from -r requirements.txt (line 1))
Requirement already satisfied: colorama in /usr/lib/python2.7/dist-packages (from -r requirements.txt (line 2))
Collecting pythonwhois (from -r requirements.txt (line 3))
Using cached pythonwhois-2.4.3.tar.gz
Requirement already satisfied: wafw00f in /usr/lib/python2.7/dist-packages (from -r requirements.txt (line 4))
Collecting sslyze (from -r requirements.txt (line 5))
Using cached SSLyze-1.1.1.zip
Requirement already satisfied: beautifulsoup4 in /usr/lib/python2.7/dist-packages (from -r requirements.txt (line 6))
Collecting json (from -r requirements.txt (line 7))
Using cached json-99.0.tar.gz
Complete output from command python setup.py egg_info:
Traceback (most recent call last):
File "<string>", line 1, in <module>
File "/tmp/pip-build-WKWG1s/json/setup.py", line 2, in <module>
raise RuntimeError("Package 'json' must not be downloaded from pypi")
RuntimeError: Package 'json' must not be downloaded from pypi
----------------------------------------
Command "python setup.py egg_info" failed with error code 1 in /tmp/pip-build-WKWG1s/json/
root@kali:~/operative-framework# python -V
Python 2.7.13
root@kali:~/operative-framework#
________________________________
edit to add...
Observations...
The operative version installed is 1.0b
Where you "use core/modules/whois_domain"
this command is now "use whois_domain", although the prompt does indeed change to
$ operative (core/modules/whois_domain) >
But then, with the next command (I've tried both 'show_options' and 'set website=technology.info') the programme crashes with...
Traceback (most recent call last):
File "operative.py", line 8, in <module>
operative.user_put()
File "/root/operative-framework/core/operative.py", line 53, in user_put
mecanic.load(user_input)
File "/root/operative-framework/core/mecanic.py", line 19, in load
load_module(name)
File "/root/operative-framework/core/mecanic.py", line 83, in load_module
use_module(module)
File "/root/operative-framework/core/mecanic.py", line 52, in use_module
mod = _import_(module_path, fromlist='module_element')
File "/root/operative-framework/core/modules/whois_domain.py", line 8, in <module>
import pythonwhois
ImportError: No module named pythonwhois
I hope this info is of use.
You need https://github.com/joepie91/python-whois
this is the main error that am having is with the json file
Collecting json (from -r requirements.txt (line 7))
Using cached json-99.0.tar.gz
Complete output from command python setup.py egg_info:
Traceback (most recent call last):
File "<string>", line 1, in <module>
File "/tmp/pip-build-i2wbBk/json/setup.py", line 2, in <module>
raise RuntimeError("Package 'json' must not be downloaded from pypi")
RuntimeError: Package 'json' must not be downloaded from pypi
----------------------------------------
Command "python setup.py egg_info" failed with error code 1 in /tmp/pip-build-i2wbBk/json/
thats where the error is any help??
Great tool however I am encountering the following issue when trying to use: python operative.py
Traceback (most recent call last):
File "operative.py", line 4, in <module>
from core import operative
File "/Users/VegetaSec/operative-framework/core/operative.py", line 7, in <module>
from core import mecanic
File "/Users/VegetaSec/operative-framework/core/mecanic.py", line 11, in <module>
from colorama import Fore,Back,Style
ImportError: No module named colorama
any ideas?
regards
apt-get install colorama
thank you, I should of specified that I am using OS X - would I be able to use port install or brew install do you know?
why after the pip install -r requirements.txt, the answer is
-bash: pip: command not found
is there anything i need to install first?
Hai
I have followed the steps till the use module part
am getting an error saying module not found but the module is listed when i type modules
Trying to use the social_network function and it throws an error asking me if I am sure I have the fullcontact.com API. So I can get the API, where and how is it added. I have looked and am lost where to add this to the framework.
Trying REALLY hard to find tools to use to find a targets info, as much as possible and not having a lot of luck unless I want to spend some major $$$$$. What all is available that will give me results? Any help is very much appreciated. (not talking about crippled scripts like Maltego either, FULL blown OINST apps)
Can you give an updated tutorial for v1. 10??
I load target but when running module it says can't find target and I can't figure out why! Unfortunately the interface is completely different this time..
Thanks for the article!
Share Your Thoughts