This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.
User Account Control (UAC)
Processes in Windows run at different levels of integrity, representing the different amounts of "trust" they have to interact with the computer. The levels are as follows:
- System - System level of integrity
- Administrator - High level
- Authenticated User - Medium level
- Everyone - Low level
- Anonymous - Untrusted
If User Account Control is enabled, programs run at medium (Or lower) integrity, even if the user starting them has Administrator rights. This limits damage malware can do to the computer, as it can only interact with user files. When a program needs to run on a higher integrity level, it has to prompt the user to give it admin rights.
UAC has 4 different levels:
- Always notify: User is notified any time anything needs elevated privileges.
- Notify me only when programs try to make changes to my computer: User is prompted when a program needs elevated privileges
- Notify me only when programs try to make changes to my computer (Don't dim the desktop): Doesn't dim the desktop when showing a prompt. Less secure than above level.
- Never notify: User is never notified about changes to the computer.
If a user is an administrator, they can press "Yes" to give the asking process higher integrity, or, if they are not an admin, they have to type in the administrator password.
Our goal here is to get a process to start with high integrity without interacting with the user. This technique will work only if they are an administrator, and UAC is not at "Always notify" level.
DLL Hijacking
DLL hijacking is a technique used to force programs to load malicious DLLs. A program normally should search for DLLs like this:
0.1 If DLL is already loaded, use it.
0.2 If DLL is on the list of known DLLs, stored in registry, load it from the path on the list.
- Hardcoded path
- System directory
- 16 bit system directory
- Windows directory
- Current directory
- PATH environment variable
However, some programs look into the current directory first, allowing us to hijack the search and make it load our DLL.
Auto-Elevation
For a program to be able to elevate without user consent it has to:
- Be signed with a certificate from Microsoft.
- Be in a secure directory.
- Have the "AutoElevate" property in it's manifest.
A program which meets those conditions can elevate without a prompt on the default settings.
Bypassing UAC
To recap, these are the conditions that allow bypassing UAC:
- Executable must be vulnerable to DLL hijacking.
- Executable must have the ability to auto-elevate.
- We have to be running a medium integrity process.
- User must be in the administrators group.
- UAC settings must be left on default values, or lower.
If all of these are fulfilled, the process of bypassing UAC is as follows:
- Copy our malicious DLL to a vulnerable program's directory.
- Execute the program, so it loads our malicious DLL.
The first step might seem impossible, seeing as we need to have admin privileges to copy files to protected locations, such as C:\Windows\System32. But quite conveniently, we can use the Windows Update Standalone Installer (wusa.exe) to unpack cabinet files into secure directories. That is possible because wusa can elevate to administrator without prompting the user.
The program we will be exploiting is called Mcx2Prov.exe. It is located in C:\Windows\ehome, and the malicious library needs to be called cryptbase.dll.
Steps to Bypass UAC:
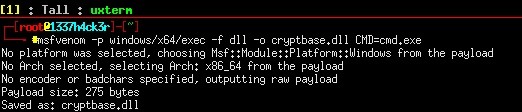
- Create our malicious DLL. We can write one ourselves, or use msfvenom. The DLL I am going to load will open Command Prompt. (Make sure the DLL has the correct bitness, and use x64 versions of payloads if needed. Use the command "systeminfo" to see system bitness.)
Syntax: msfvenom -p <payload> -f dll -o cryptbase.dll <payload options>
- Turn our DLL into a cabinet file. There is a tool on windows called makecab which will create the file for us.
Syntax: makecab <input file> <output file>
- Unpack the cabinet using wusa:
Syntax: wusa <input file> /extract:C:\Windows\ehome\
Be careful to use the absolute path to the cabinet file. You won't get an error if extracting fails, so double check everything worked correctly.
- Run Mcx2Prov.exe:

Pwned! There is another way to copy files, using code injection, and vulnerable executables vary by Windows version. Nevertheless, this exploit is quite reliable and easy to execute.
Additional Info:
Here are exploitable programs available:
On Windows 7:
- C:\windows\ehome\Mcx2Prov.exe
- CRYPTBASE.dll
- C:\windows\System32\sysprep\sysprep.exe
- CRYPTSP.dll
- CRYPTBASE.dll
- RpcRtRemote.dll
- UxTheme.dll
- C:\windows\System32\cliconfg.exe
- NTWDBLIB.DLL
On Windows 8:
- C:\windows\System32\sysprep\sysprep.exe
- CRYPTBASE.dll
- dwmapi.dll
- SHCORE.dll
- C:\windows\System32\cliconfg.exe
- NTWDBLIB.DLL
- C:\windows\System32\pwcreator.exe
- vds.exe
- UReFS.DLL
On Windows 8.1:
- C:\windows\System32\sysprep\sysprep.exe
- SHCORE.dll
- OLEACC.DLL
- C:\windows\System32\cliconfg.exe
- NTWDBLIB.DLL
- C:\windows\System32\pwcreator.exe -> vds.exe
- C:\Program Files\Common Files\microsoft shared\ink\CRYPTBASE.dll
- C:\Program Files\Common Files\microsoft shared\ink\CRYPTSP.dll
- C:\Program Files\Common Files\microsoft shared\ink\dwmapi.dll
- C:\Program Files\Common Files\microsoft shared\ink\USERENV.dll
- C:\Program Files\Common Files\microsoft shared\ink\OLEACC.dll
Mitigation:
- Do not unnecessarily give users admin rights.
- Set UAC to Always Notify (Extremely annoying).
Just updated your iPhone to iOS 18? You'll find a ton of hot new features for some of your most-used Apple apps. Dive in and see for yourself:






















6 Comments
Great guide, very interesting subject
Cheers,
Washu
Awesome tutorial bro
This is exactly was I have looking for lately! I was having trouble trying to bypass uac in wan! I will try it out!
Thank you so much!
BTW, is there a way to tell which UAC level the victim has?
UAC level is determined by several values in the registry, but the important one to us is ConsentPromptBehaviorAdmin. You can check the value of it using this command:
REG QUERY HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System\ /v ConsentPromptBehaviorAdmin
If it returns the value "5", bypassing is possible.
dll hijacking has always been an intimidating subject that I've hesitated to giving a try. Thanks to your tutorial its not anymore THANKYOU!
~Suser
Not working for me.
Wusa is not able to extract the tmp (cab) file when I run below command:
cmd> wusa cryptbase.tmp /extract:c:\windows\ehome
It works when I run:
cmd> wusa cryptbase.tmp /extract: --> but it shows a GUI box asking for selecting the location like we see when we download something and it asks where to store it.
Its not practical I think.
Do you have any idea why its not working?
Share Your Thoughts