For many of you, this is common knowledge. But I still regularly see comments posted here and elsewhere asking, "This <AV bypass> doesn't work, because when I upload my payload to VirusTotal...."
It's a totally understandable beginner mistake. After all, it seems like a clever thing to do. There are even a lot of otherwise perfectly nice tutorials out there that encourage you to upload your file to check it.
Years ago, VirusTotal DID have an option that would allow you to scan without distributing the file -- but then the AV companies fought to have that option removed.
VirusTotal (And Other Online Scanners) Hand Everything Over to Antivirus Companies
This has never been a secret. VT's About page spells this out quite clearly:
So you upload your custom payload and only 4 out of the 57 AVs flagged it? That's pretty impressive! Nice job! Unfortunately, you just auto-generated a report that will be sent to 53 antivirus product makers.
:(
If You Are Using Someone Else's Tool, You Are Making It Less Likely to Work in the Future, Ruining It for Everyone
"So what? It's just a practice file and I'd only be hurting myself."
AV companies aren't always detecting a payload signature -- they're often detecting the method used to hide it. Every time you upload a test payload, you're helping them along.
To demonstrate this, I broke my own rule (the only time, I swear!!)
First, I took a completely harmless EXE that happened to be sitting on my Kali desktop: accesschk, from Sysinternals. I uploaded it to VT:
Then I ran it through msfvenom with 100 iterations of x86/shikata_ga_nai. I did not embed a payload or otherwise alter it.
I uploaded my msfvenom-encoded (but harmless) EXE:
Respect the Developers Who Shared Their Code with You
Veil-Evasion was released in 2013. Chris Truncer, one of its creators, announced its release on his personal blog. At the very top, he posted this plea:
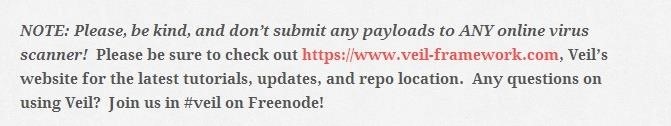
Aaaannnndddd a few days later someone posted this comment:
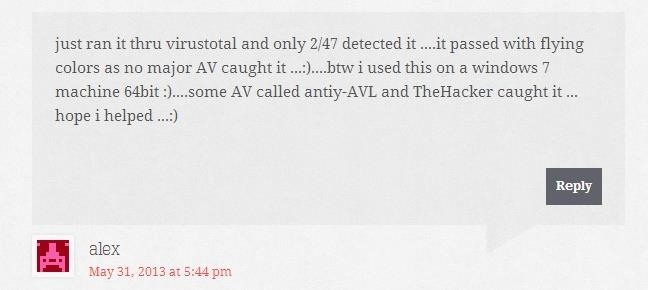
Thanks, alex!!.
And even now it's not hard to find numerous Veil tutorials that end with the demonstrator uploading their payload to VirusTotal:
But most importantly, when developers who are generously providing their scripts completely free of charge, go so far as to post a message in bright bold letters:
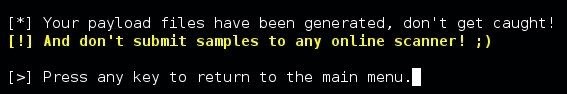
You should respect it.
VirusTotal Is Watching You
Just like every other website, VirusTotal tracks its visitors. And if you're trying to get a payload past AV, you'll be uploading a file, checking it, tweaking it, re-uploading it, rinse, repeat, etc. etc. That's not exactly the behavior of a typical user.
One researcher was able to watch as a team of hackers tested their new malware. We shouldn't be surprised if others are watching as well. From Wired, Sept. 2014:
It's No Guarantee
Just because a payload isn't caught on VT, doesn't mean that AV won't kill it as soon as it executes.
VT uses pure signature-based detection. But almost every AV out there has at least some manner of sandboxing or heuristic detection. This means that the AV might still detect your payload based on how the program behaves.
What to Do Instead
- The absolute best thing you can do is find out what AV your target uses, download a free trial, and install it on a VM to test. (Make sure you check the settings. Most will automatically report viruses they catch -- but you can turn that off).
- There are several scanning sites out there that claim they never distribute files to AV companies or anywhere else. But there isn't a good way to verify this, so beware.
- Do this instead: How to Safely Check Veil Payloads Against VirusTotal
Or... upload to VirusTotal anyway. If you're using your own encoding and obfuscation techniques (and not, for example, Veil). Maybe you're using a file splicer and a Hex editor to manually alter a signature. Then by all means, use VT if you want.
Yes, the file's signature will be distributed. But it'll take days or weeks before the signature is pushed out to users. If this is a one-off file you intend to use on a single target within the next few days, then you should be fine. Just don't be a jerk.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























8 Comments
Nit just virustotal guys!! Dont submit to any online scanner!!
GOOD POST.
i used to have multiple websites that act's like virus total but they are safe ,
Very informative post - many thanks.
Also, Virustotal itself can create a payload, and use Veil-Evasion preventing AVs detections, then it uploads it to its own site, right?
Thanks for the post
older post but ever-so-relevant, thanks for the enlightenment.
Recently (2-29-16) someone uploaded a sample of Hacking Team's Mac malware:
https://www.virustotal.com/en/file/58e4e4853c6cfbb43afd49e5238046596ee5b78eca439c7d76bd95a34115a273/analysis/
and almost immediately it was picked up by researchers and anti-virus companies.
Did Hacking Team accidentally upload their own sample to VirusTotal?
The website www.NoShareScanner.com is good and free if you want to review this.
Share Your Thoughts