Hot Null Byte How-Tos


How To: The Top 80+ Websites Available in the Tor Network
There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

How To: Set Your Wi-Fi Card's TX Power Higher Than 30 dBm
Do you have an Alfa AWUS036NH Wi-Fi adapter that claims it can go to 2000 mWs, or some card that can supposedly transmit power over 1000 mW? If so, you may have run into problems setting your card's TXPOWER higher than 30 dBm, which is about 1000 mW. Well, I will show you how to break that barrier and go as high as you want!

How To: Get a Jump Start into Cybersecurity with This Bundle
Cybersecurity is an industry that isn't going anywhere. After the mass move to online work, the need for more cybersecurity professionals skyrocketed. That demand isn't going away because more and more industries are keeping online and cloud services going for their workers.

Android for Hackers: How to Turn an Android Phone into a Hacking Device Without Root
With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

Hack Like a Pro: How to Set Up a Honeypot & How to Avoid Them
Welcome back, my aspiring hackers! Those of you who've been reading my tutorials for some time now know that I am adamant regarding the necessity of learning and using Linux to hack. There is no substitute, period.

How To: Use Burp & FoxyProxy to Easily Switch Between Proxy Settings
One of the best ways to dig into a website and look for vulnerabilities is by using a proxy. By routing traffic through a proxy like Burp Suite, you can discover hidden flaws quickly, but sometimes it's a pain to turn it on and off manually. Luckily, there is a browser add-on called FoxyProxy that automates this process with a single click of a button.

How To: Find Vulnerable Webcams Across the Globe Using Shodan
Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

How To: Use Kismet to Watch Wi-Fi User Activity Through Walls
Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

How To: Find Identifying Information from a Phone Number Using OSINT Tools
Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

How To: Crack Password-Protected Microsoft Office Files, Including Word Docs & Excel Spreadsheets
Microsoft Office files can be password-protected in order to prevent tampering and ensure data integrity. But password-protected documents from earlier versions of Office are susceptible to having their hashes extracted with a simple program called office2john. Those extracted hashes can then be cracked using John the Ripper and Hashcat.

How To: Perform Advanced Man-in-the-Middle Attacks with Xerosploit
A man-in-the-middle attack, or MitM attack, is when a hacker gets on a network and forces all nearby devices to connect to their machine directly. This lets them spy on traffic and even modify certain things. Bettercap is one tool that can be used for these types of MitM attacks, but Xerosploit can automate high-level functions that would normally take more configuration work in Bettercap.

The Hacks of Mr. Robot: How to Send a Spoofed SMS Text Message
Welcome back, my rookie hackers! As most of you know, Mr. Robot is probably the best hacker TV show ever! This is a great show about a cyber security engineer who is being enticed to hack the very corporation he's being paid to protect. This show is so good, I began a series to demonstrate how to do the hacks he uses in the show.

How To: Dox Anyone
Doxing is the act of finding one's personal information through research and discovery, with little to no information to start with. You may have seen doxing in the news, for instance when not so long ago, hacker team Anonymous doxed and reported thousands of twitter accounts related to ISIS. Doxing can be useful for finding the address of a coworker, or simply investigating people on the internet. The tutorial I will provide to you now will teach you the basics of doxing and how you can prot...

How To: Find Passwords in Exposed Log Files with Google Dorks
You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

How To: Intercept Images from a Security Camera Using Wireshark
It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

How To: Enumerate SMB with Enum4linux & Smbclient
SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

How To: Crack Shadow Hashes After Getting Root on a Linux System
After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

How To: Buy the Best Wireless Network Adapter for Wi-Fi Hacking in 2019
To hack a Wi-Fi network using Kali Linux, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, so I've rounded up this list of 2019's best wireless network adapters for hacking on Kali Linux to get you started hacking both WEP and WPA Wi-Fi networks.

Tutorial: Create Wordlists with Crunch
Greetings all. Before I get into the tutorial, I would like to mention that I am fairly new to Null Byte (been lurking for some time though), and what really appeals to me about this place is its tight, family-like community where everyone is always willing to help each other and the constant search for knowledge that inhabits this subdomain is a driving motivator for me to join in. I'm glad I arrived at the right time. Anyway, wipes tears (not really)...

How To: Use MinGW to Compile Windows Exploits on Kali Linux
Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

How To: Hack Wi-Fi Networks with Bettercap
There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

How To: Use Upip to Load MicroPython Libraries onto a Microcontroller Over Wi-Fi
MicroPython is an exciting language to use on ESP8266 boards and ESP32-based microcontrollers, but it doesn't always include all of the libraries you'll need for a specific project. This issue is less of a problem, thanks to the upip package manager.

How To: Automate Wi-Fi Hacking with Wifite2
There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

How To: Hack Windows 7 (Become Admin)
Step 1: Introduction: Hello! Hackers

How To: Create Malicious QR Codes to Hack Phones & Other Scanners
QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into custom QR codes.

How To: This Top-Rated Course Will Make You a Linux Master
Linux is a diverse and powerful operating system that virtually every IT professional must learn and know well. Whether you realize it or not, you have likely already used a Linux device, and learning to design things for it is a key step in any Data Science career path.

How To: Install & Use the Ultra-Secure Operating System OpenBSD in VirtualBox
OpenBSD implements security in its development in a way that no other operating system on the planet does. Learning to use the Unix-like operating system can help a hacker understand secure development, create better servers, and improve their understanding of the BSD operating system. Using VirtualBox, the OS can be installed within a host to create a full-featured test environment.

How To: Write Your Own Bash Scripts to Automate Tasks on Linux
Bash scripting is a convenient way to automate things on any Linux system, and we're going to use it here to automate certain tasks we use all the time.

The Hacks of Mr. Robot: How to Hide Data in Audio Files
Welcome back, my hacker apprentices! A you know, Mr. Robot is my favorite TV show this year, and not just for the realistic hacking. Rami Malek, the actor who plays Elliot, is incomparable in his depiction of a young man with social anxiety who is alienated from a superficial, materialistic society and wants to make a better world. I believe we will see a lot more of this actor in coming years.

How To: Tactical Nmap for Beginner Network Reconnaissance
When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

How To: A Guide to Steganography, Part 1: How to Hide Secret Messages in Images
This is the first of a multi-part series on steganography techniques. Steganography, the art of hiding things in plain sight, has existed for a long time, and in many forms. When you manipulate the alphabet to have your own cipher and decipher, this is considered steganography.

How To: Learn C# & Start Designing Games & Apps
Learning different coding languages can be difficult. You spend so much time mastering one and getting used to thinking along the channels you need for it that learning something new can sometimes be more difficult than starting from scratch. Starting from scratch, notably, is also difficult.

How to Use PowerShell Empire: Getting Started with Post-Exploitation of Windows Hosts
PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.
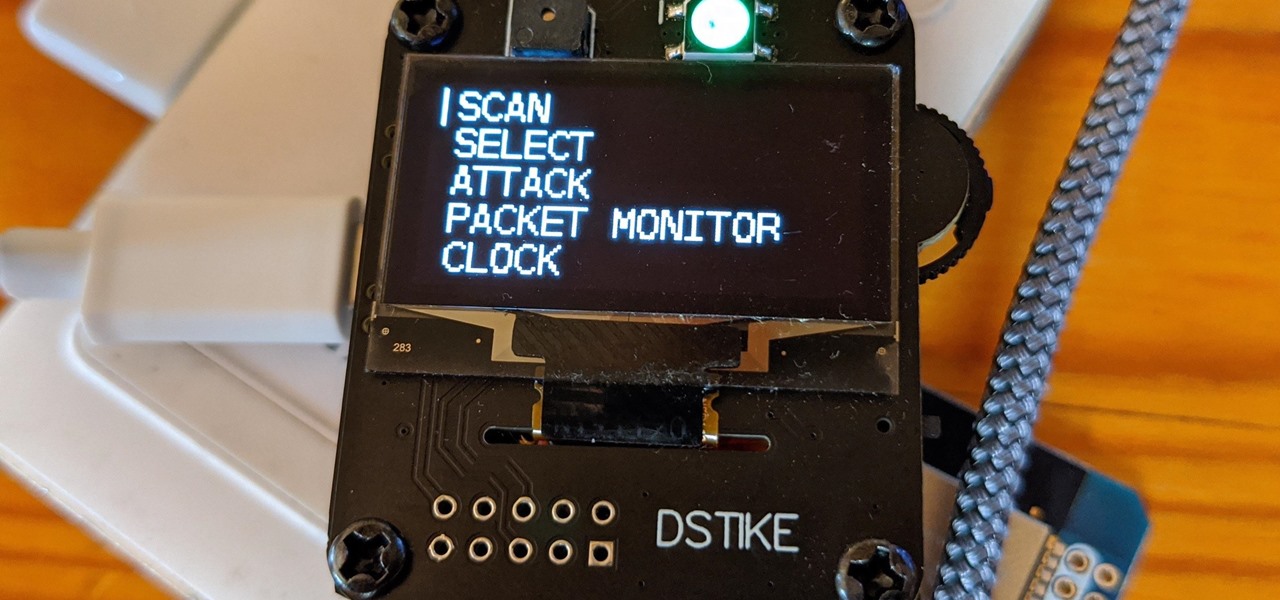
How To: Hack Networks & Devices Right from Your Wrist with the Wi-Fi Deauther Watch
The Deauther Watch by Travis Lin is the physical manifestation of the Wi-Fi Deauther project by Spacehuhn, and it's designed to let you operate the Deauther project right from your wrist without needing a computer. That's pretty cool if you want to do all the interesting things that the Wi-Fi Deauther can do without plugging it into a device.

How To: Get an Internet Connection in the Middle of Nowhere to Hack Remotely
If you're living or staying out in the middle of nowhere or a rural area outside of a big city or town — where there are no reliable cable, fiber, or wireless networks available — how can you get an internet connection? There are several possibilities, but they all come with tradeoffs, which we'll go over in detail.

The Hacks of Mr. Robot: How to Hack Bluetooth
Welcome back, my novice hackers! Episode 6 of Mr. Robot has come and gone and, as usual, it did not disappoint. Once again, our hero, Elliot, has used his extraordinary intellect and hacking skills to awe and inspire us.

How To: Attend Defcon Without Looking Like a Noob or Spending a Fortune
Defcon is the largest hacker conference with something for everyone, whether it be the talks, parties, villages, or any of the hundreds of events. In this guide, we'll take a holistic view at everything that goes into attending the con for the first time, from securing your electronics and making the most of your time to the logistics of getting there and finding the right place to stay.

How To: Make Your New Year's Resolution to Master Azure with This Bundle
Microsoft has plenty of products that you're likely familiar with, especially if you work or dream of working in IT. One of the most important now and in the future will be Azure, the company's cloud computing service. You might not know it, but a significant portion of the internet runs on Azure, and that share of the web is projected to keep growing in the coming years.

How To: Security-Oriented C Tutorial 0x0C - Buffer Overflows Exposed!
Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show.

How To: Build a Stealth Port Scanner with Scapy and Python
As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...


