Welcome back, my budding hackers!
We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.
Obviously, if we compromise a system, we're likely after some data inside. If so, we need a way to get the data out without being detected. On most systems, there is likely to be an IDS or IPS looking for malicious packets, both in and out. In addition, a vigilant security administrator will notice when a new port or service is open.
Ideally, the best method of extracting data would be undetectable from the system admin or others so they can't close off our extraction path. As an exfiltration can often take hours, days, or weeks, we need a covert channel that can't be detected by the security devices or the security admin.
How to Remain Undetected When Exfiltrating Data
In this tutorial, I will show you a tool called RECUB that will create a covert channel on a Windows or Linux system that is virtually undetectable by an intrusion detection system, nmap scanning, or even the operating system tools itself.
A Quick Description of RECUB
Microsoft describes RECUB this way on their website:
"This threat is classified as a backdoor trojan. A backdoor trojan provides remote, usually surreptitious, access to affected systems. A backdoor trojan may be used to conduct distributed denial of service (DDoS) attacks, or it may be used to install additional trojans or other forms of malicious software."
"For example, it might be used to install a downloader or dropper trojan, which may in turn install a proxy trojan used to relay spam or a keylogger trojan which monitors and sends keystrokes to remote attackers. It might also open ports on the affected system and thus potentially lead to further compromise by other attackers."
"This threat is detected by the Microsoft antivirus engine. Technical details are not currently available."
Step 1: Download RECUB
You can download RECUB here. RECUB has a client/server architecture, so you will need to put the server on the target and the client on our attack system.
Step 2: Install the RECUB Server on the Target System
Install it on the RECUB server by clicking on RecubSvr.
The server will silently run in the background until it is awakened by the client activating it.
Step 3: Install the RECUB Client on Your Attack System
Now install the RecubClient.exe on the attack system and run it as administrator. It should have GUI interface like that below.
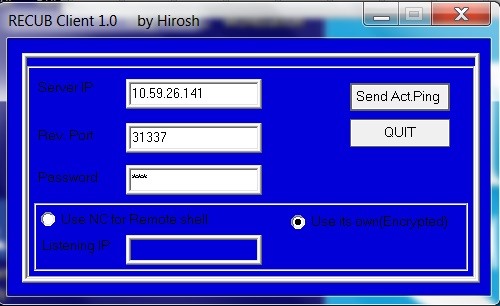
Now, enter the IP address and port that you want RECUB to communicate on. I have used port 31337, but you can use any port. The password is 123 and can't be changed without recompiling RECUB, so let's not change it.
Step 4: Send the Encrypted ICMP
To activate the server, RECUB uses an encrypted ICMP packet. Click on the "Send Act. Ping" button and it send the ping that activates the server on the target.
The RECUB server will intercept the packet, decrypt it, and make a connection back to the client. This will open a command shell on the client system that gives you control of the target system!
Better yet, we could use the HTTPS port 443, so to the security admin it will appear to normal HTTPS traffic.
Step 5: Test Whether Snort Can Detect It
Now that we have a covert channel running between these systems, let's use an IDS like Snort to see whether it can detect the traffic. Let's use Snort on our Kali or BackTrack system to sniff the traffic between these two machines and see if it triggers an alert.
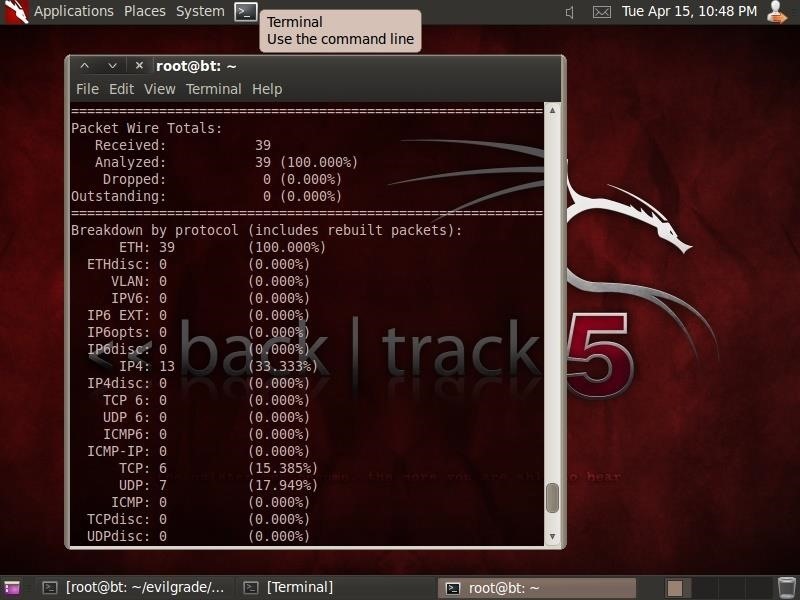
As you can see, this covert channel is totally invisible to Snort and does not trigger any alerts.
Step 6: Test Whether Nmap Can Detect It on Open Port & Service
Next, as our covert channel for exfiltration of data may need to be open for days or weeks, it's important that a vigilant security admin not be able to detect it.
Some of the better and more vigilant security admins will do a periodic scan of open ports and services on their networks. In this way, they can see whether a system or network has been compromised.
In many of our exploits, we have opened a communication channel between our control system and the victim system. If the sysadmin scans the system while this in place, they will see an unauthorized open port. This will lead to their action that will likely close that availability.
Now, let's do an nmap scan of the system with the RECUB server and see whether we can detect the covert channel. In the below command, -sT scan for TCP ports, -sU scans for UDP ports, and -p0-65535 tells nmap to scan all ports.
- nmap -sT -sU -p0-65535 10.59.27.89
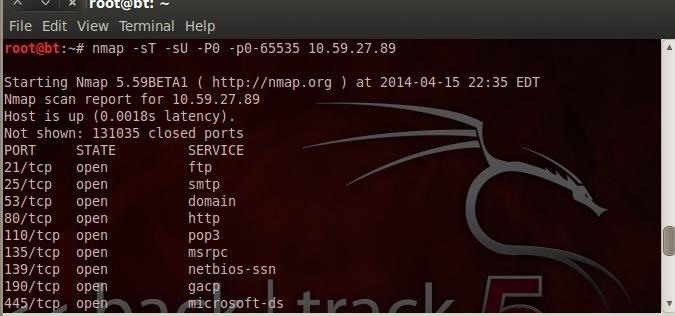
As you can see, nmap does not detect any unusual ports open on the system with the RECUB server.
Step 7: Test Whether the RECUB Process Is Visible
The RECUB covert channel is nearly undetectable, even by the operating system itself! One of the tools we have for viewing our running services is the Task Mananger. Let's open the Task Manager and see whether it shows the process RecubSvr.exe.
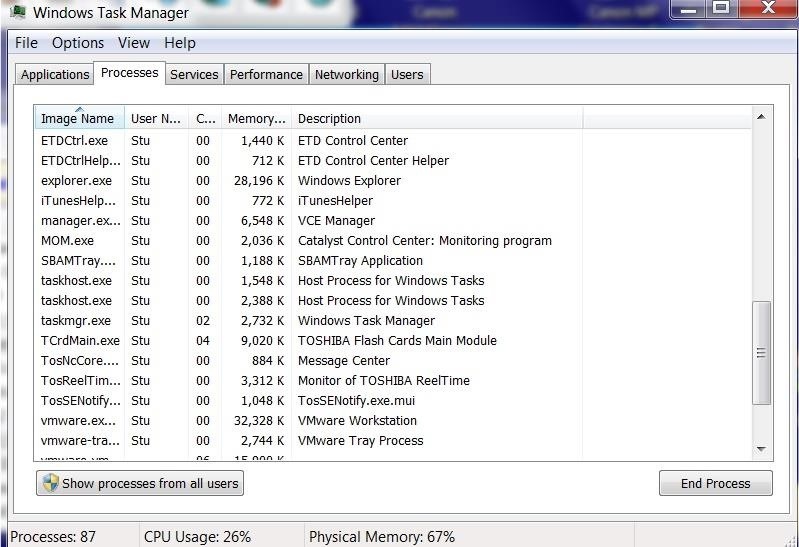
As you can see, even the operating system itself can't detect the service!
RECUB is one of the many tools that we place on the victim system that will enable us to control the victim system and remove the data that we are seeking. It is largely undetectable by the IDS, nmap, or the operating system itself. Some third-party tools can detect it, but most security admins will never look that deeply to detect a convert channel on the victim and all the while we can be quietly removing data without detection or interruption.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























15 Comments
How would you get this onto the victims computer and run it in the first place?
Metasploit or tftp as two possibilities. There are many more.
hi
is snort in kali ? i have looked a few times and not see it yet?
Yes. Just type snort.
hmm ya tried that before OK
this is what i get with typing snort in Kali ?
Brook:
I'm sorry. The folks at Offensive Security took snort out of Kali. You can download it at www.snort.org.
OTW
Question: Great article btw...anyhow...if MSE or now Microsoft's 8.1 security service now recognizes this and I'm sure automatically quarantines and deletes it...how is this useful? Does it only recognize it by name or is it more complex by recognizing the signature?
Robert:
Welcome to Null Byte!
Excellent question. Most malware is recognixed by signature. To get thispast AV software, you only need to change the signature. Its also important to point out that no everyone is running Windows 8.1. See my article on target market share and ATMs running XP.
OTW
How would go about changing the signature of RECUB with out access to the source code?
Do i need some kind of Reverse Engineering software ?
Is there a tool like in Matasploit just to change the signature
and can you get an IP address from a MAC address AP to a target PC?
THANKS
Brook:
There a multiple approaches that will work. First, you XOR the software and it will often change the signature enough to get past AV and IDS's.
Second, you could use software like IDA Pro to reverse engineer it.
Third, you can change the encoding of RECUB.
Fourth, you can use the same encoding but change the way programs internal operations but not its functionality.
I don't understand your last question, but there is not a tool that will do these things automatically that I am ware of.
OTW
Sir OTW,
Amazing, i loved this thread. If i remember correctly a covert channel is an "indirect way of communication". So, instead of getting the data directly, we force a part of a system (processor, ...) to behave specifically, and we from the outside analyze that behavior to extract from it the data (like if the data was piggybacked in the sub-system behavior). On what type of covert channel is RECUB based (storage, processing, timing ....) ??
Wow RECUB's C&C interface is very familiar. Fantastic work once again master.
Now for the flipside of the coin, as this seems to be a very common trojan, how can we ourselves look for a RECUB infection if it is using 443 and encrypted traffic. I have a metric fucktonne (a technical term at best) of HTTPS traffic, is there a particular field value to look out for?
I can download it for Windows, there are not .exe files.
Need help.
hi there,
i wonder how can i get the source code for me to do the reverse engineering in covert channel. Please help me.
Share Your Thoughts