In this tutorial I will be explaining the purpose of unique encryption/decryption scripts ( I will be referring to these at "UEDS" for this tutorial). Then, I will show you how to make one. Finally I will talk about the downsides to the method I use. I will also provide links explaining the concepts and algorithms used in encryption to anyone who wants to see what is going on under the hood.
The Purpose for Using UEDS
As most of us know you can use an open source program called OpenSSL to encrypt files. This uses intense algorithms to encrypt the data in a file and output in into another file. The only problem is end users tend to like to use easy passwords on things and/or stick to only one method of encryption. Since anyone has access to OpenSSL the only information someone would need to decrypt your file is the encryption method that you used and the password (which if you made guessable then you're pretty screwed.) On solution to this problem is to make a script that runs your file or files through multiple encryption methods with different and VERY hard passwords. This way someone trying to guess or brute-force your password would have to know what encryption methods were used, the order in which they were used, the long strings of gibberish used as passwords, and finally your password that you used in the UEDS.
Creating and Using Your UEDS
For this tutorial I will be scripting in bash using Sublime Text but any text editor should work. You will need openssl installed on Linux (already in Kali)
Step 1: Make the File.
first you need to make a file (you can name it whatever you like just don't use spaces as it may cause problems later).
Step 2: Write Your Script.
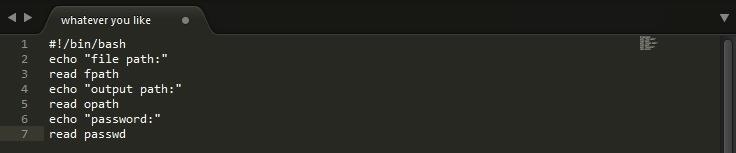
Start off any bash script like you would by locating the bash file:

They you would ask the user to input information to set certain variables.
now you need to use your knowledge of OpenSSL to construct the commands necessary for your UEDS.
Basic commands, options, and ciphers you will need:
openssl = opens ssl
enc = encrypt/decrypt a file
-e = specify encryption (default)
-d = specify decrypt
-in = specify input file
-out = specify output file
-k = use password
aes-256-cbc = my favorite cipher
more commands, options, and ciphers can be found here: https://www.openssl.org/docs/apps/enc.html
Now before you start writing the main part of the script you will need to understand how we will be using temporary files to transfer data while its being encrypted. What is going to happen when we encrypt is that the input file will be encrypted to a file called '1'. Then the encrypted data will be encrypted again to a file called '2'. Then this process will repeat until producing an output file. One this happens we will program the script to remove both the files called '1' and '2'. By doing this we don't overwrite the file as we are trying to encrypt. Now I'm sure their are easier ways to do this but for the sake of this tutorial I will be showing this method.
Now you will create your encryption algorithm iterations! Remember though that the key to true strong encryption is randomness. Try to be as random as possible with the ciphers and passwords used. Also remember that you had the user input data into variables for a reason so don't forget to include those in their respective places. Keep in mind that you can have one or more password variables but I will just be using one. Also remember to put a - in front of your cipher
IMPORTANT NOTE: The more iterations of encryption you put will affect the difficulty and confusing of making your decrypt script .
Construct your commands as such (all one command):
openssl enc -e (cipher) -in (input file for this tutorial 1 or 2 or a variable)
-out (output file for this tutorial 1 or 2 or a variable) -k (random password or variable)
Then you will switch the input and output files (if you are using the '1' '2' method) as long as you are not on the first or last lines where you will be using the variables you set in the beginning of the script. Then at the end you will type the "rm" command to remove the temporary files. If you find this is confusing see if the next picture helps.
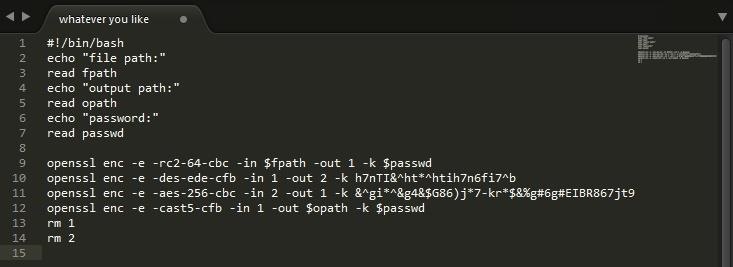
Now the amount of encryption algorithms you use is up to you but just know that the more times you encrypt it the exponentially fatter it becomes. You don't want a file that stores all your passwords in it to be 1gb worth of space. Also keep in mind that if you are encrypting larger files it will take longer and become even fatter. If you know that you are going to encrypt larger files focus less on the amount of iterations and more on the password. (don't give up multiple iterations entirely though I recommend at least 3-4)
Step 3: Saving and Executing Your Script
Finally save your file and give it executable permissions through the GUI or in the terminal with this command:
chmod 755 <UEDS path>
Then you will run your script by double clicking and clicking on run in terminal or by typing the command replacing UEDSname with the name of the script you just made:
./UEDSname
When the script executes mine will ask you for a "file path:" where you will input the file path to the file you want to encrypt is located. Don't put any apostrophes or quotes in the file path because it may cause problems (it did for me anyway). Then it will ask for the output file where you should specify where the final encrypted file will be saved. Finally it will ask you for a "password:" which will further make your file more secure. Once you have input all these items the script will start to encrypt using the '1' and '2' method as previously explained and encrypt encrypted files with the various ciphers that you put. Finally the encrypted file will pop out.
Step 4: Making a Decrypt Script
Once you have your encryption script the decryption script should be easier depending on how many encryption commands you used. What you need to do is essentially reverse the order of the commands and replacing the -e command with a -d. remember to adjust the positions of the variables so you don't break the script.
For example if my encrypt script looked like:
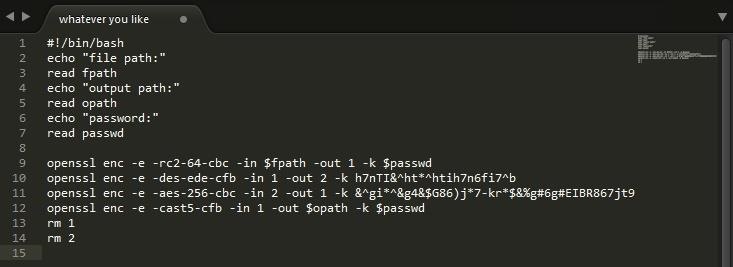
My decrypt script would look like:
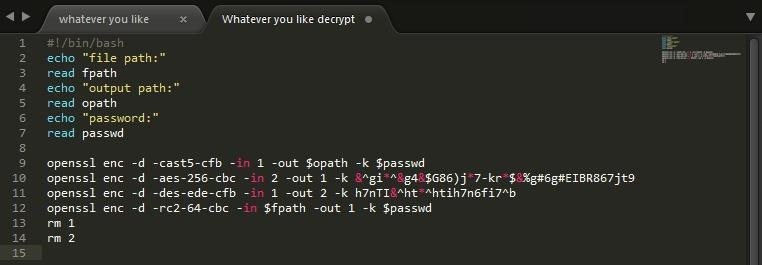
(Ignore the color change)
Then save your decrypt UEDS and chmod it as you did with the encrypt script. You will run the two files the same way but with the decrypt file you will enter the file path to the encrypted file.
Flaws
This is a good method to secure your files but like with everything it comes with flaws. Some of which I have talked about before, but just in case you missed them here they all are:
- Files you're encrypting increase in size exponentially.
- The more iterations you put the harder it becomes to make the decrypt file.
- If you lose the encrypt/decrypt files you have almost no chance of being able to decrypt it unless the unencrypted file hasn't been overwritten yet.
If you can deal with these flaws then good on you. You found another way to encrypt your files. This is good if you keep these on a USB and/or want to send encrypted files to other people on a site or network and don't want to worry about people intercepting and brute-forcing it.
More Information on Encryption Algorithms and How They Work
here are some links to explain what encryption algorithms are and how they work.
https://en.wikipedia.org/wiki/Encryption
https://en.wikipedia.org/wiki/Advanced_Encryption_Standard
Thanks for reading, my first really detailed tutorial. Hope it wasn't too long. Anyway see you in the next tutorial. maybe.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























2 Comments
Nice post! I have never really looked into OpenSSL and have stuck with GPG with myself as the recipient for most of my encryption, but this looks really sweet!
Makes me think, it would be really cool to make a decryption cluster or something that you could just upload a file and it bruteforces in like a week :P bruteforcing isn't about efficiency, its about beef :P
Thanks :D!
Share Your Thoughts