If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs at all, such as Cerberus, an anti-theft solution available right on Google Play.
Cerberus is marketed as an anti-theft program so that you or the police (with your assistance) can track down your Android phone if it's ever lost or stolen. However, while phone users see an anti-theft tool, hackers see a RAT that only costs 5 euros a year (about $5.80). That's a helluva lot cheaper than the $21.99 per month RAT that Tyrell Wellick used in Mr. Robot, and they have the same feature set.
As an anti-theft tool, Cerberus offers all the features that we've come to expect of a good RAT, including locating the device, backing up (aka stealing) data, locking or changing the PIN, wiping data, and taking photos. All of this and more can be done from any web browser or by sending special SMS text commands.
Aside from the super cheap cost, there are also other benefits. For one, it's available in the Google Play Store. And two, root is not required to make this tool work, though, root can be useful for certain functions like rebooting and wiping data.
However, Cerberus is an aboveboard company, so one must assume they log everything. Hackers should go through steps to ensure anonymity when accessing the service and targeted device. For example, using Tor, a VPN, and a spoofed MAC address from a public internet connection can help protect your identity.
Using Cerberus to Hack Android
If you're a white hat, pentester, or other security professional following this guide, it's a good idea to do this on your own device first for two reasons.
- It's good practice. You want to be as fast as possible when you have the target's device in hand to minimize the chances of getting caught.
- For whatever reason, the Cerberus team decided that installing the app should be the only way to create an account. So doing this on your own device will allow you to skip the account creation part during an attack and to make sure you have your subscription successively set up.
The first time you create an account, you'll automatically get a free seven-day trial that lets you try out the features of the app before you pay. Also, if you're only interested in a target for a one-time specific event, you can save a few bucks and just use the trial. There's no need to pay if you don't need to do this more than once.
Step 1: Access & Unlock the Target Device
First, you need to gain physical access to the target Android phone. Without this, you can't install the app without knowing the login credentials for the user's Google account. If you do manage to hack the user's Google account info, you can install the app to the device from the Play Store online, but that doesn't change the fact that you will need to have access to the unlocked phone for future steps, like for logging into your Cerberus account.
If you don't have the user's Google credentials handy, you'll need to gain physical access to the device and unlock it. Let's take a look at a couple of scenarios that could help in both gaining access and unlocking:
- The easiest and most often overlooked way is to simply tell the target some of what you're doing. Put a little spin on the story. If the target is part of your family or extremely close, play it as if you're putting an anti-theft app on everyone's phone. Neglect to mention that you can use that very same app to spy on them. If they're prone to losing their phone or paranoid about it getting stolen, you might actually be helping them out.
- If the target is not closely related, you could spin it as if you got X number of devices with your subscription plan and have some extras. Offer one of those extras to target. You might even get them to pay you for it. That's the beauty of Cerberus being an anti-theft app — plausible deniability. And, if you ever get caught spying on them, it's much easier to play it off as if you were simply worried about them or didn't realize what you were doing.
Assuming those options didn't work, you'll need to establish whether or not they have a lock on their phone and, if so, what kind. If it's a password or PIN, be diligent, and over time, remember and write it down. If the target is using a pattern, do the same, but you don't necessarily have to get it perfect as you can try several different variations pretty quickly. You can also analyze the screen smudges under a bright light, then line them up with the dots that appear for the pattern lock.

If the target is using a facial recognition lock, then you can attempt to hold up some kind of image of them and see if it'll unlock the device. The easiest way is to simply go to their Facebook account on your device and hold it up to the phone. However, this won't work if the device is using 3D facial recognition. In that case, or if they're using a fingerprint lock, then you're best served by trying to social engineer them into giving you their phone unlocked. Here are two more examples of how you might do that:
- Pretend to be interested in their make and model of phone. Say you're thinking about buying one.
- If you're going somewhere with them in the car, offer to help with navigation and say that your own phone doesn't have service or is dead. You can also use texting as the excuse since you don't want them texting and driving while you're in the car — offer to do it for them.
Other than that, you're left with the tried-and-true classics of grabbing their phone while they're in the shower or asleep. (Tyrell installed a RAT while his lover, aka the assistant of Evil Corp's CEO, was in the shower.) Either way, once you have physical access to an unlocked device, you're ready to move on to the next step.
Step 2: Install Cerberus on the Target Device
Quickly, open the Google Play Store, and search for "Cerberus anti theft," then press "install" and wait a few seconds while it downloads the roughly 6 MB file.

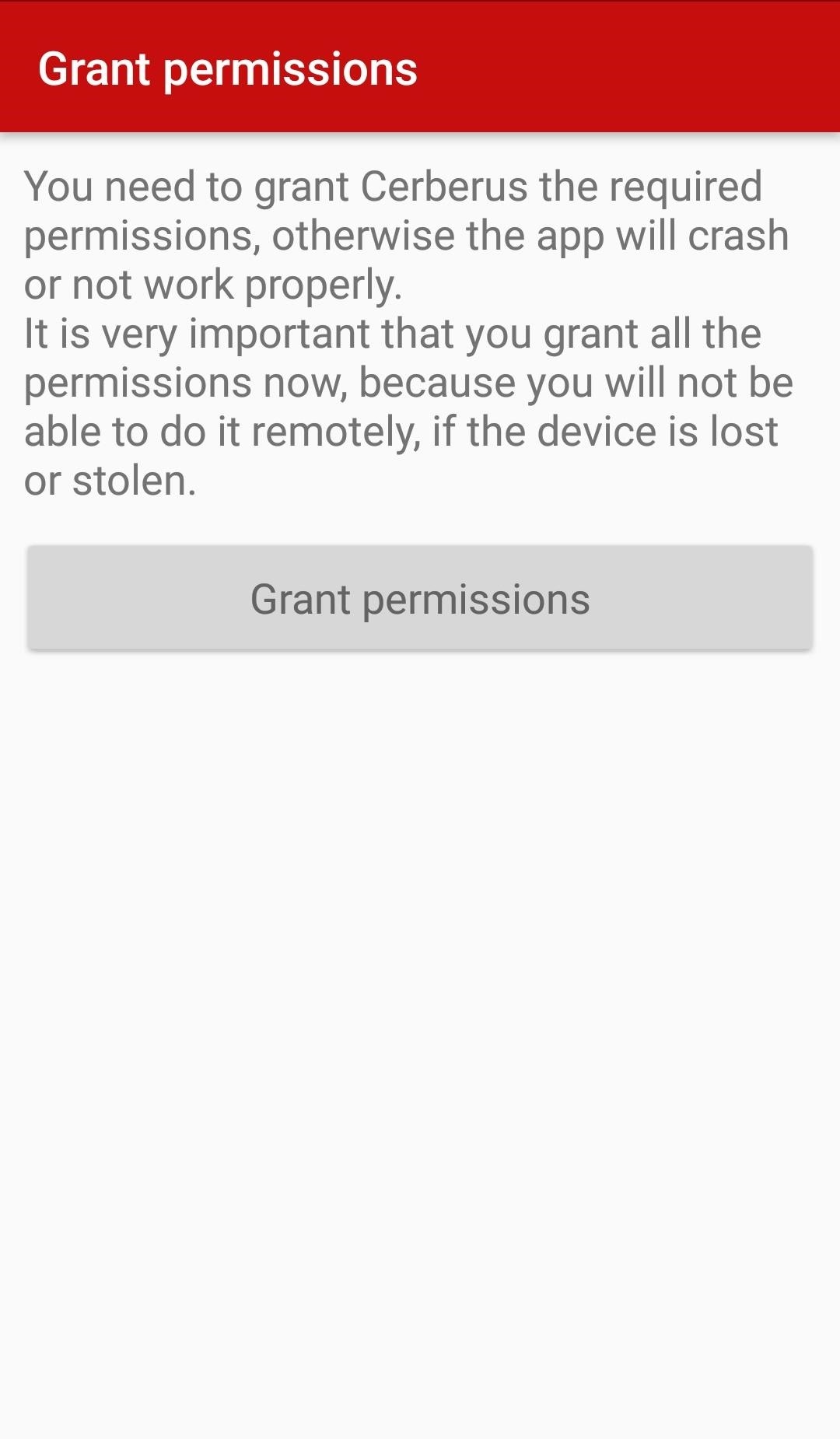
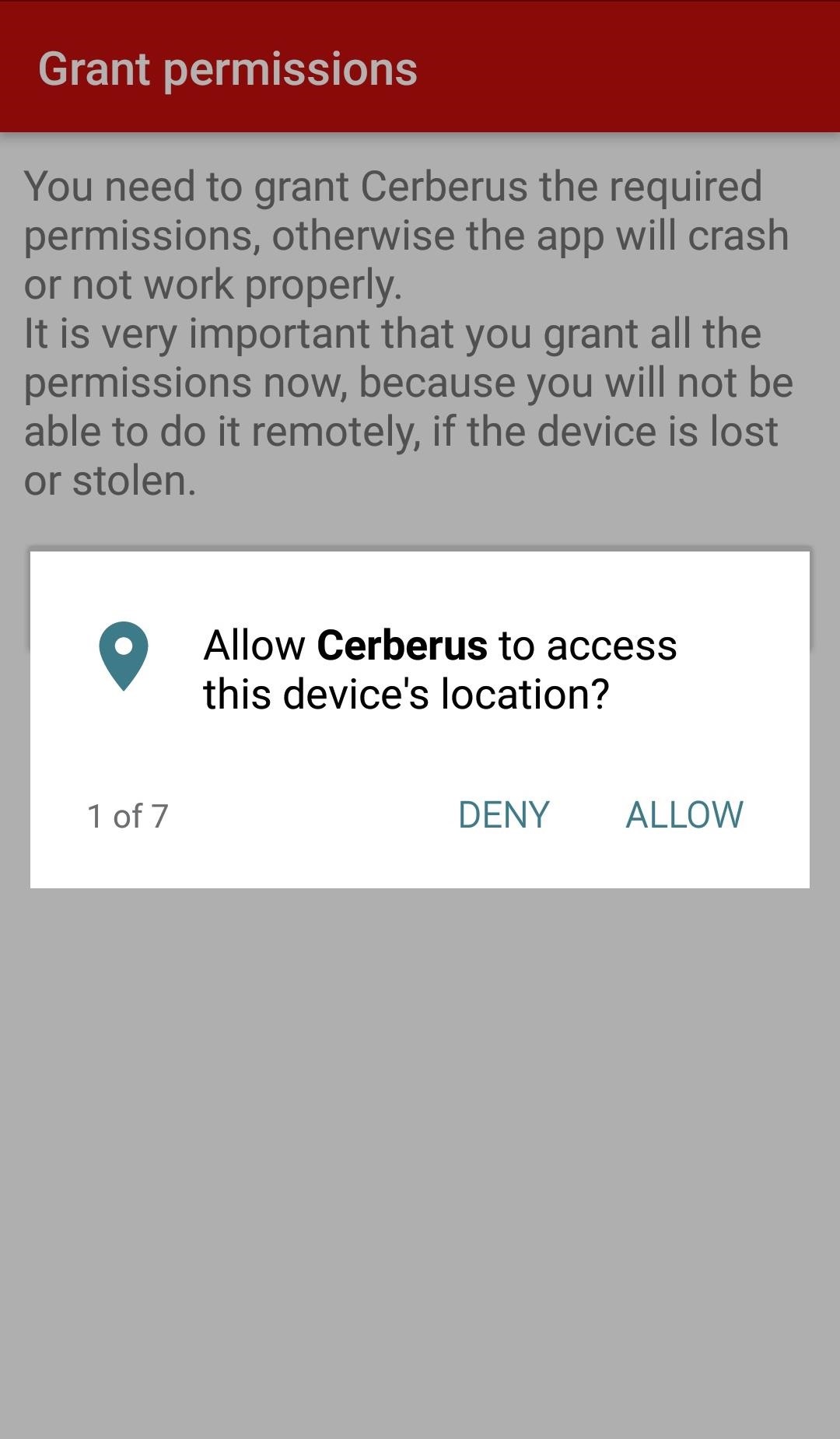
Next, tap "Open," then "Grant permissions," and tap "Allow" seven times. These are the permissions that will allow you to do things like tracking the device remotely, so it's very important that you allow them all.
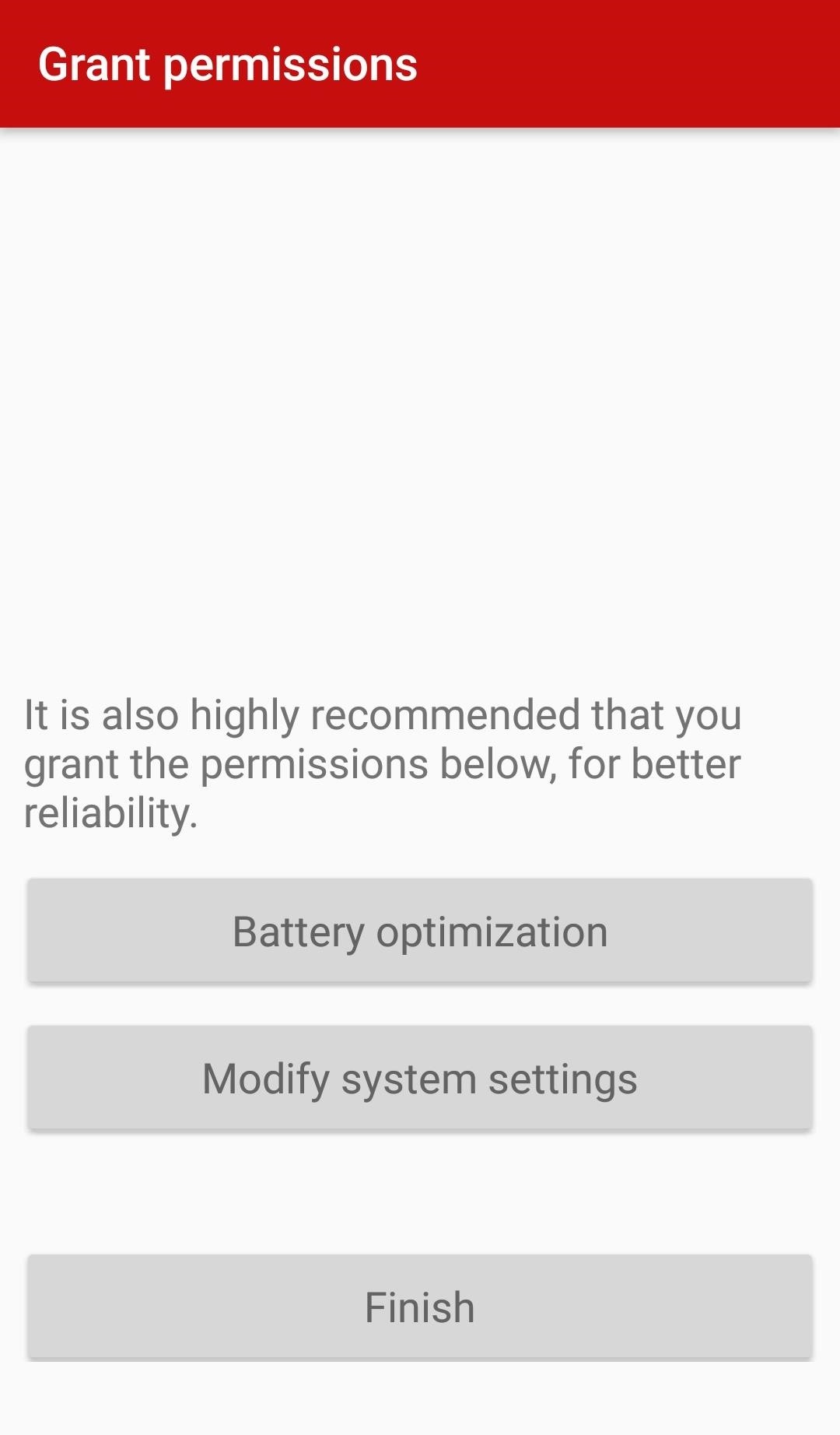
With that done, skip over "Battery optimization" — you can do that later. Right now, you're attempting to get all the necessary things done as quickly as possible so that if you suddenly lose access to the phone, the app will still work. Tap "Modify system settings," switch the toggle to "On," then press "Finish."
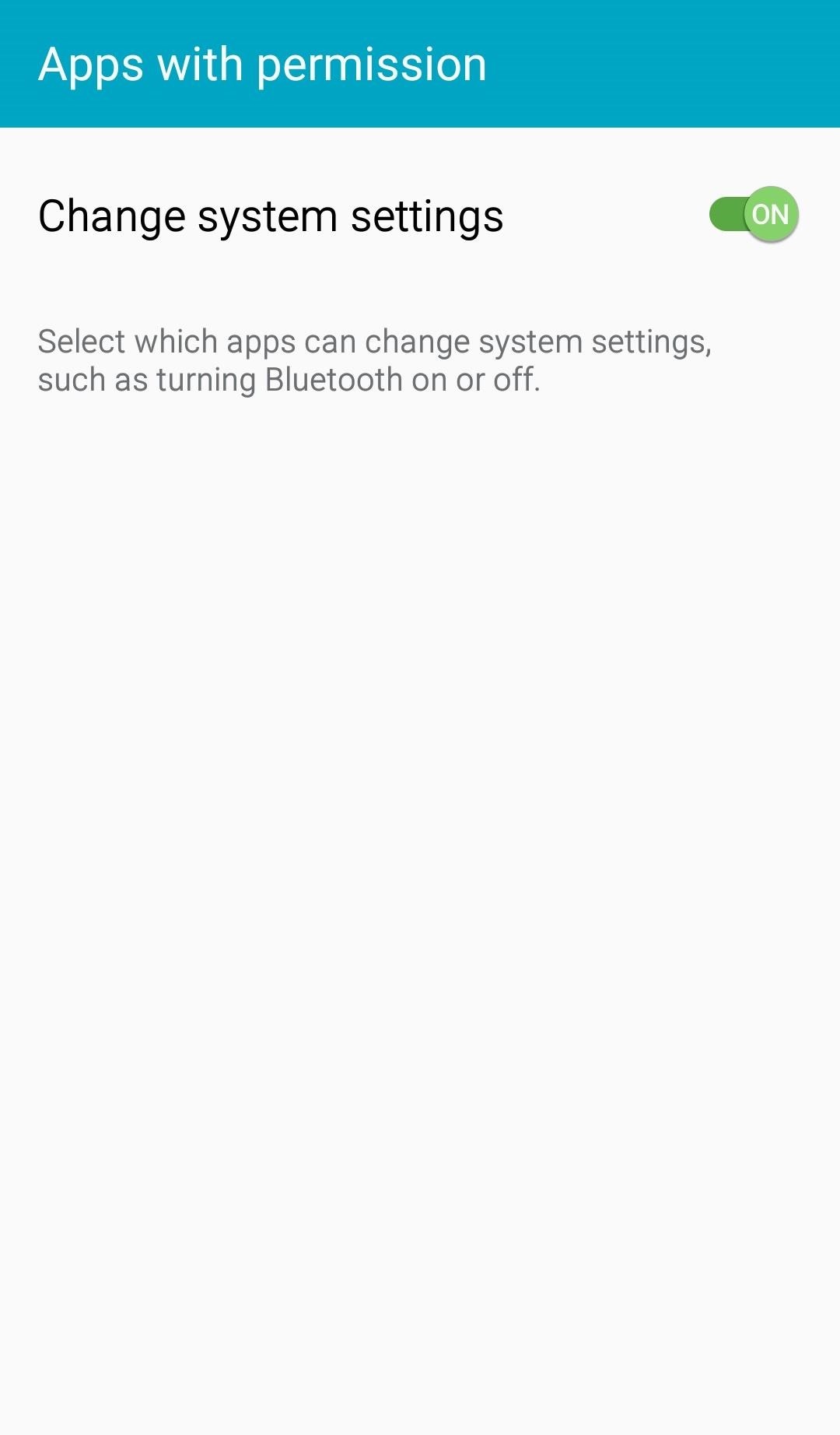
Step 3: Sign into Cerberus on the Target Device
The first time doing this, you need to create a Cerberus account. As far as I know, this is the only way to create a Cerberus account, so it's good to do this on your own Android device so you can skip this during an actual attack.
Remember operational security (OPSEC); Don't use your actual username or a username that you use on any other website. Also, choose a unique password. You might even want to make an email just for the purpose of using Cerberus, although that might be a little overkill, but still good OPSEC.
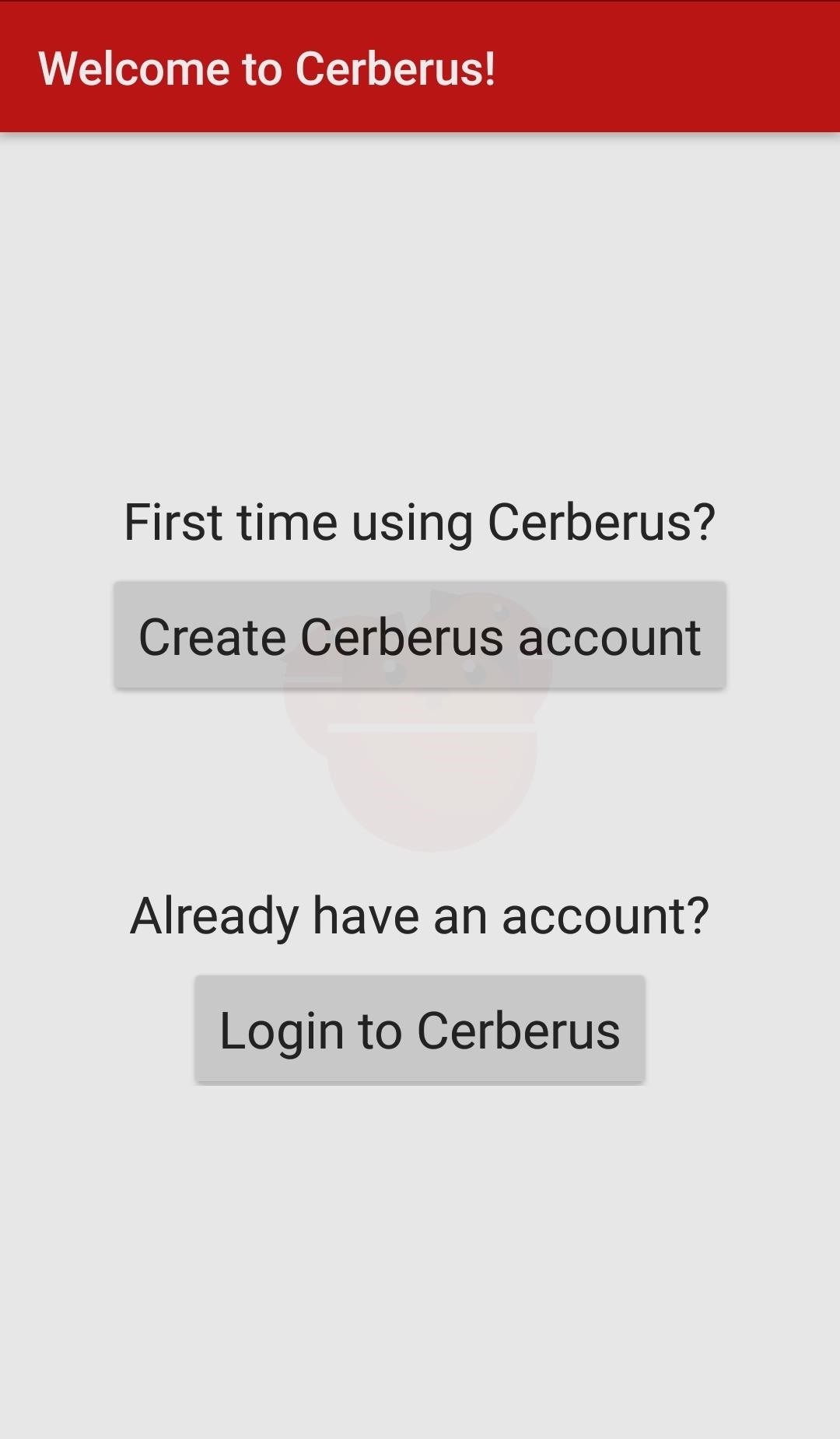
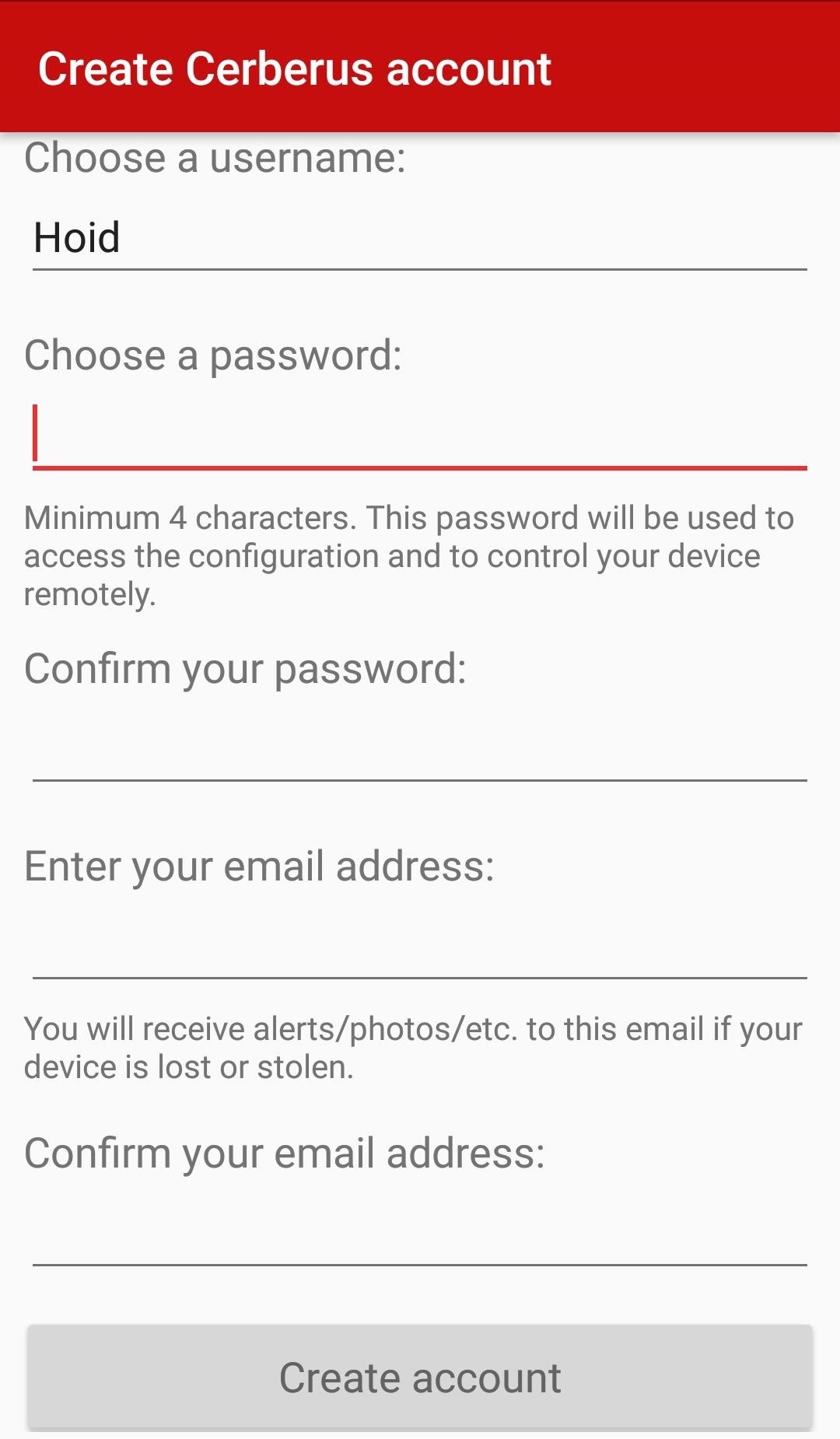
If you're going to use Cerberus on both your phone and a target's phone, remember to buy a license which supports at least two devices. Unfortunately, the seven-day free trial only supports one device. You don't want to be this far into hacking someone's phone and realize you forgot to do that.
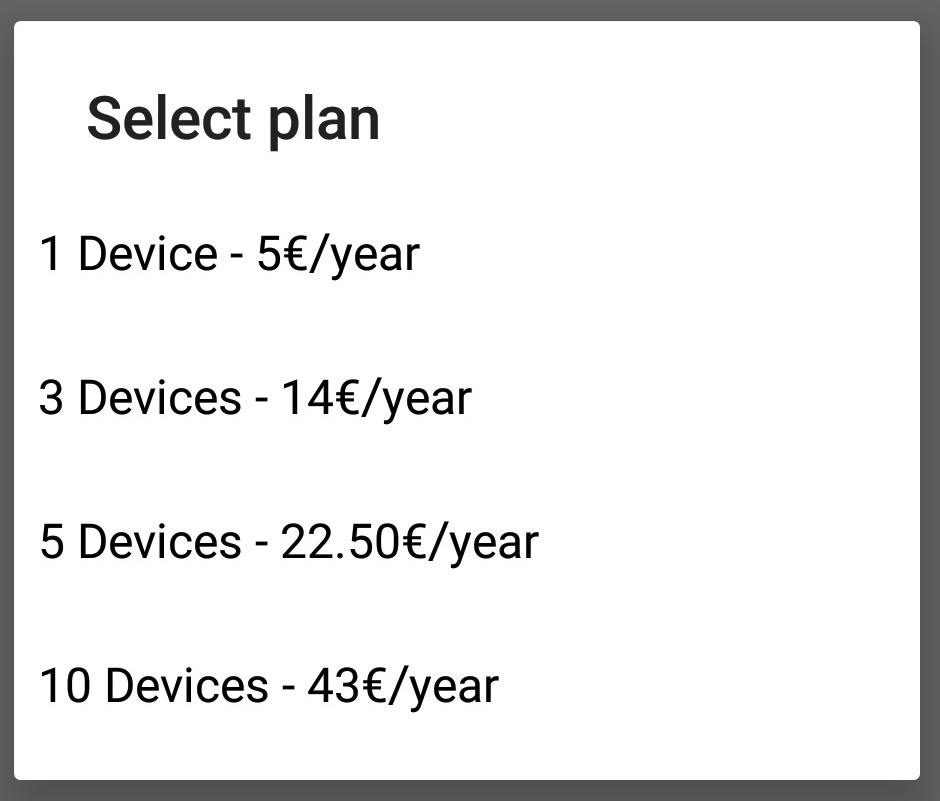
When doing this on the target's device, just sign into your existing Cerberus account. If the target's device offers to save the password, don't do it. There's no need to make things easy for the target.
Step 4: Enable Admin Privileges on the Target Device
You'll be taken to the main Cerberus Main configuration page. Scroll down until you see the Device administration heading. Just under it, tap "Status: Disabled," then "Activate" on the pop-up screen. This will give you the power to do things like erase data and change the lock screen so they can't ever lock you out of the phone again.
Next, check the box next to "Protect device admin." This will make it almost impossible for the target to get rid of the app and its powers if they discover it unless they somehow find out the Cerberus password you set or do a factory reset (which Step 7 below will block).
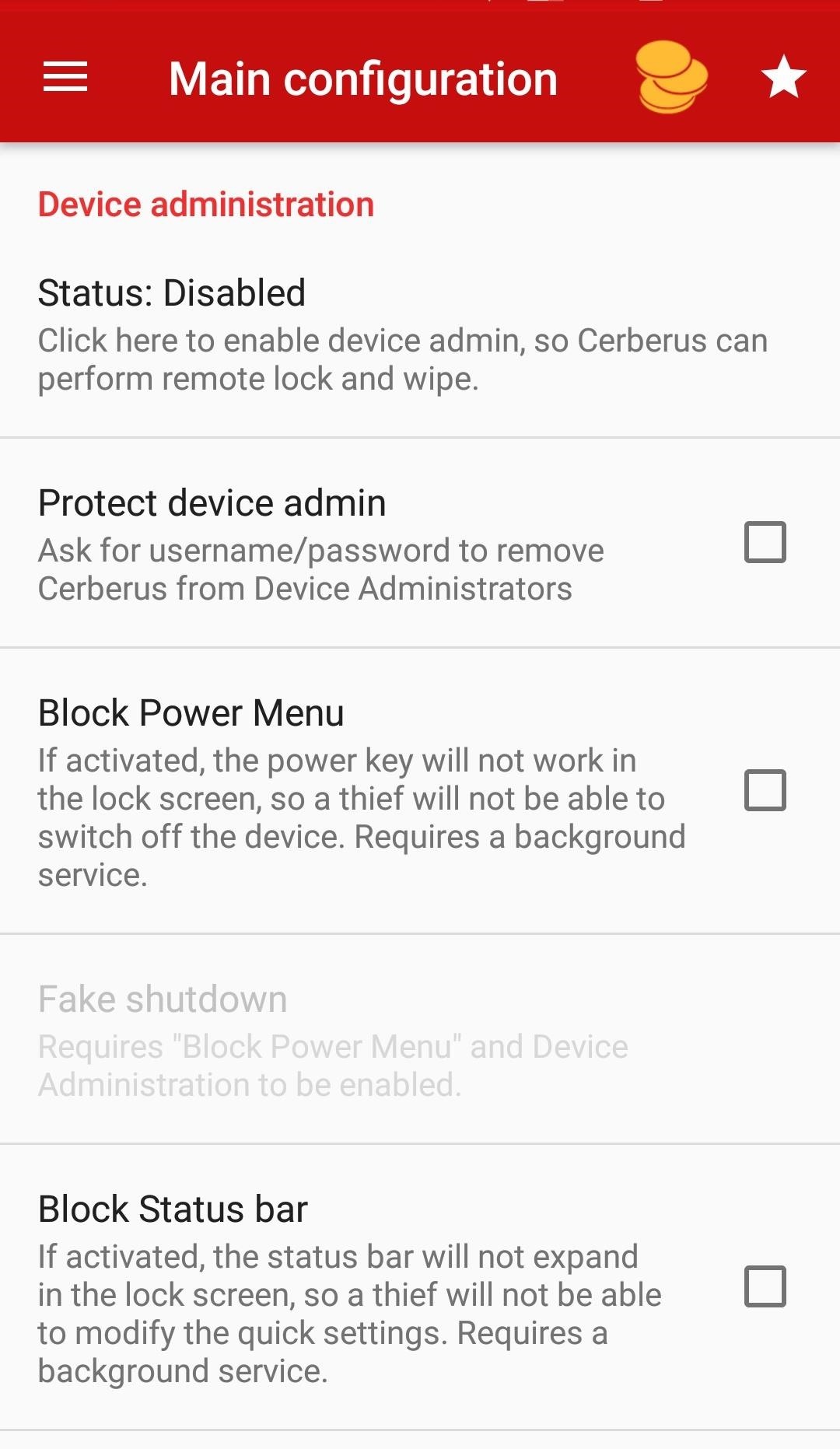
While you're on the Main configuration page, scroll down and tap either "Back up your files to Dropbox" or "Back up your files to Google" and link the account you want to use to steal the target's data. Keep scrolling and make sure all the boxes under "Remote wipe" and "Location history" are checked.
And that's all you need to do for the bare bones of this attack. You'll be able to do the things most people are interested in like tracking the phone. However, it will be blatantly obvious to the target when you do so as they will receive a notification. In the next few steps, we will look at how to hide the signs.
Step 5: Hide Notifications on the Target Device
It's pretty straightforward to hide Cerberus notifications on Android. Long-press the Cerberus app icon on the home screen or in the app drawer, tap "App info," then tap "Notifications" and switch off "Show notifications." Alternatively, on older Andriod devices, you may need to navigate to the "App info" manually by going to something like "Apps," then "Cerberus," in Settings.
Doing this will prevent the target from receiving any notifications when you perform Cerberus actions such as location tracking.
Once you've done that, the app is pretty stealth — most people aren't going to notice one more app buried in their app folder, particularly with the number of bloatware apps there are on phones these days. If there's a shortcut on the home screen for some reason, tap-and-hold on it, then drag it up to "Remove" it.
If time allows, there are more things that can be done to make it even stealthier.
Step 6: Change Data & Power Settings on the Target Device (Optional)
While you have the "App info" open, go ahead and tap on "Data usage," then toggle on "Unrestricted data usage." Next, go back and tap "Battery usage." From there, tap "Battery optimization," find and tap on "Cerberus" in the available lists, select "Don't optimize," then "Done."
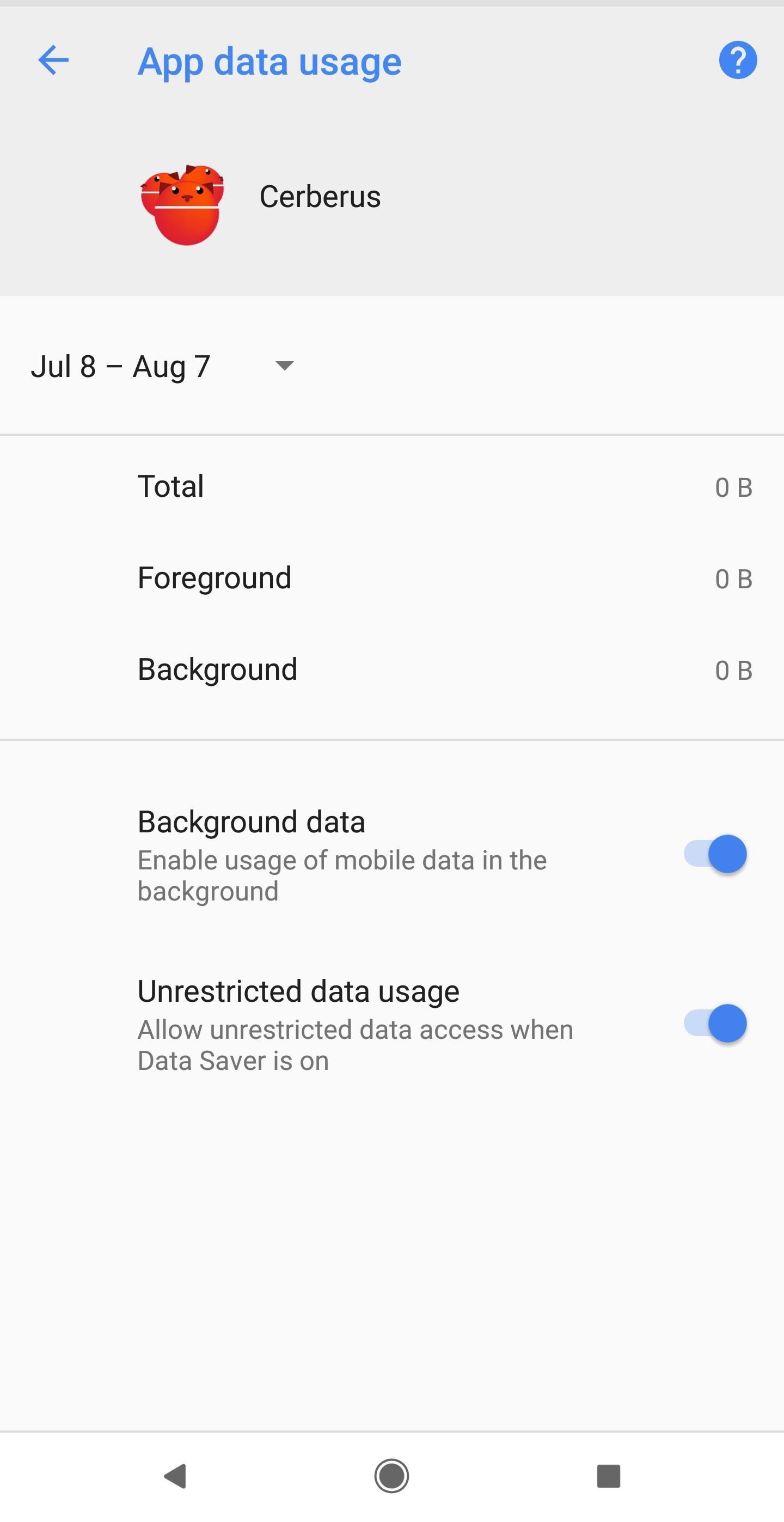
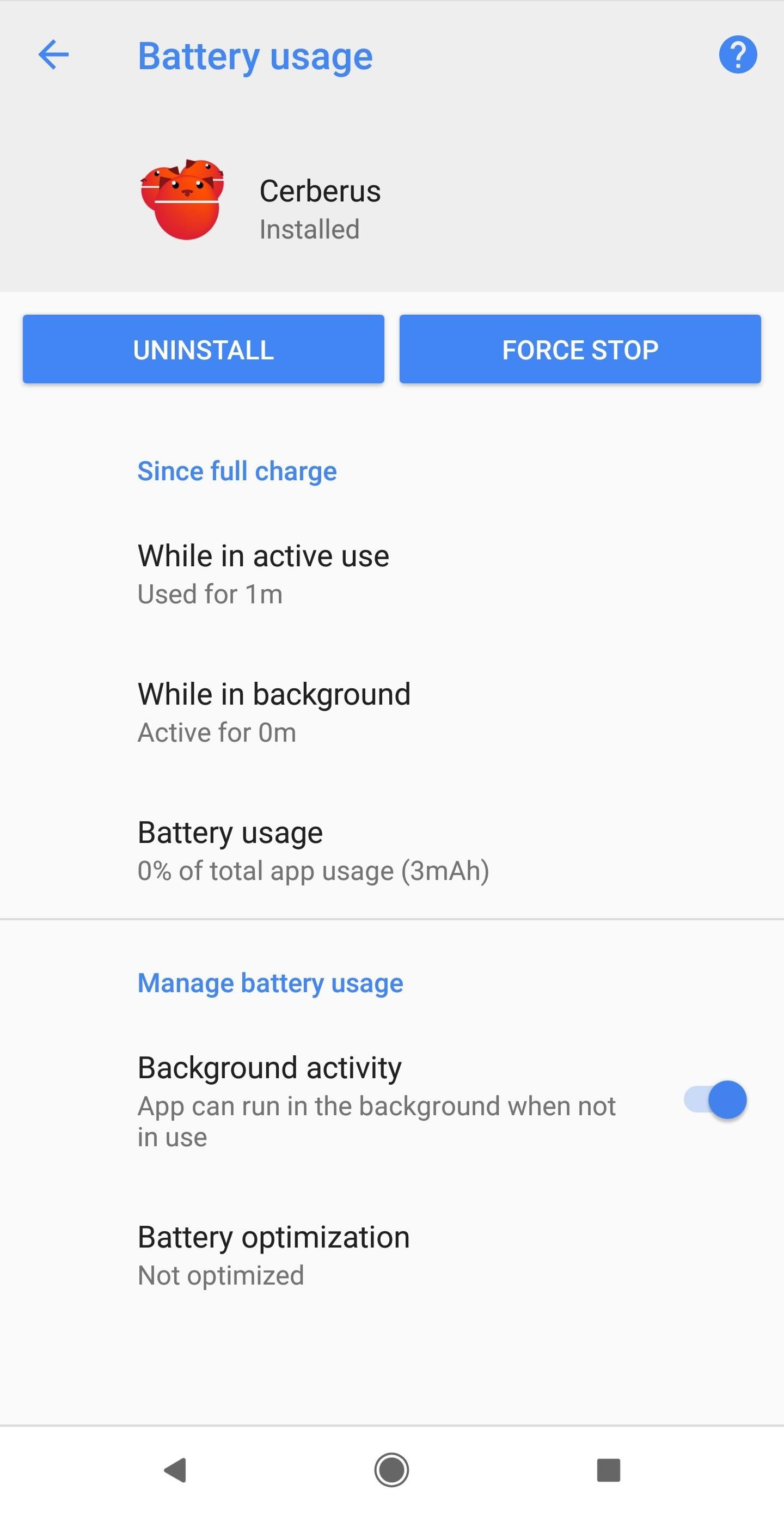
Changing these two settings will ensure that you're able to exfiltrate large amounts of data such as images and files with ease. Also, it guarantees data restrictions and battery optimization won't ever give you problems.
For example, you might have problems if the target's device is laying flat and still for more than a few minutes, in which case Doze Mode would kick in. The device will start looking for ways to save power including turning off the services of the Cerberus app, which would keep you from being able to track the target.
Step 7: Make It Impossible to Remove Cerebrus (Optional)
If you really have a lot of time available with the device, like more than an hour, you can make the Cerberus app a system app and prevent the user from removing it even if they do a factory reset. It will need to be a rooted device, or you will have to root it, hence why I say an hour or more of time.
For those of you who do have the time and want to make sure that the target can never rid themselves of this RAT, short of buying a new phone, then this step is highly recommended. Dallas from Gadget Hacks has already went through the options available for this process, so make sure to check out his full guide starting at Step 3 to convert Cerberus to a system app.
Step 8: Return the Target Device as Received
Everything's done on the phone side of things. Try to return the device to the same screen it was on when you picked it up, and return it to the same place you found it. It's unlikely any user would actually notice, but you can never be too careful.
Step 9: Take Control of the Target Device from the Web
You're ready to take control of the target device now. Open the Cerberus website and use your login credentials in the top-right corner.
Once you've logged in, Cerberus will immediately attempt to establish a connection with the devices linked to your account. If the device is not showing up, the most likely reason is that the device is powered off or out of data/Wi-Fi service, so just be patient.
On the right, you'll be able to see a log which will stay updated with all the commands being sent and received. When the device is connected, it will appear in the log and its location will appear on the map.
It's important to note that this location isn't always precisely accurate. First of all, there are the natural limitations of GPS and Cerberus is kind enough to provide you with that accuracy estimate. However, you have to keep in mind that it's the location the phone thinks it's at. That means if the user of the device is the kind of person that uses a GPS spoofing app, then you will not see the actual location of the device but only the location that the user is spoofing to.
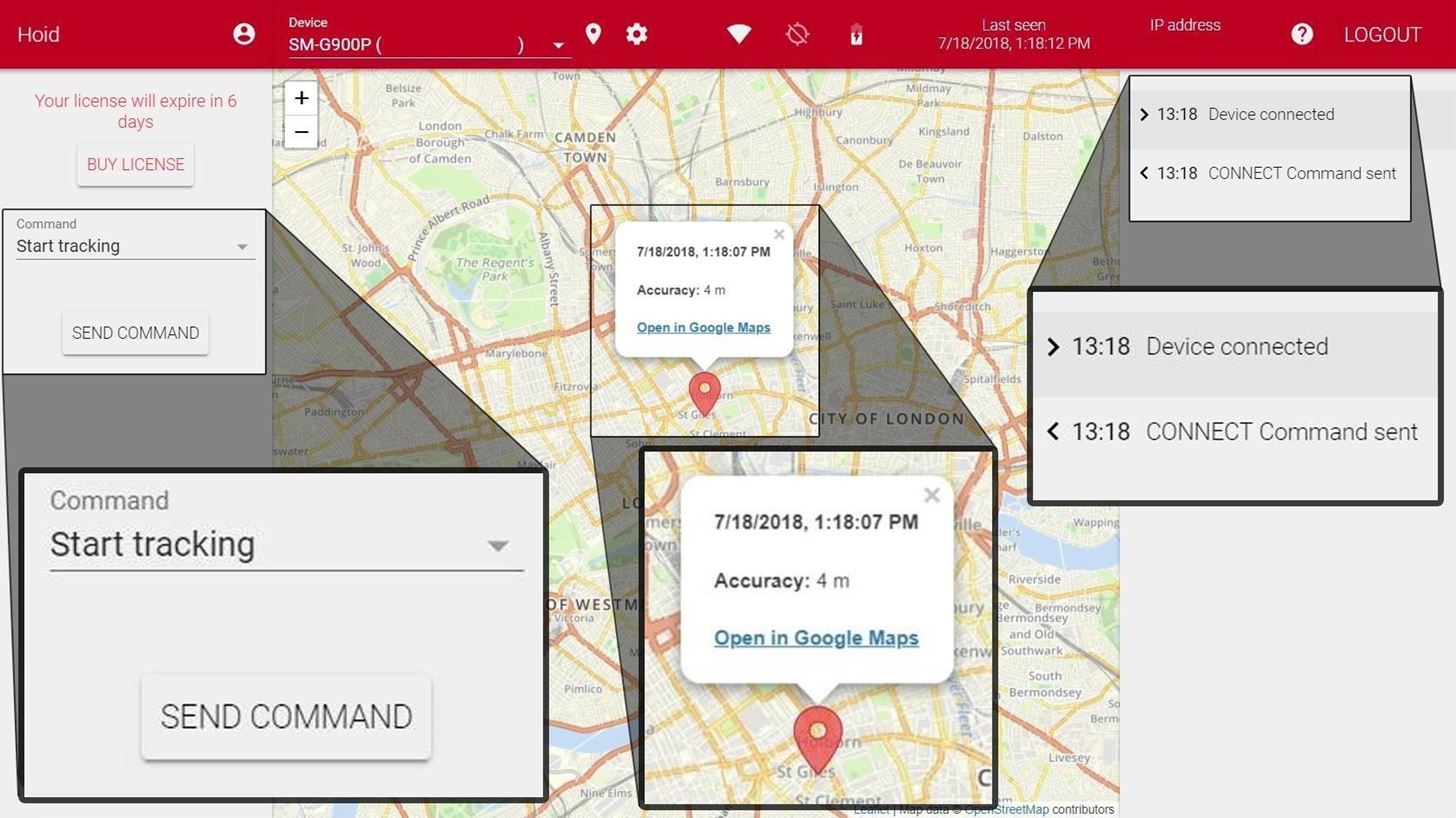
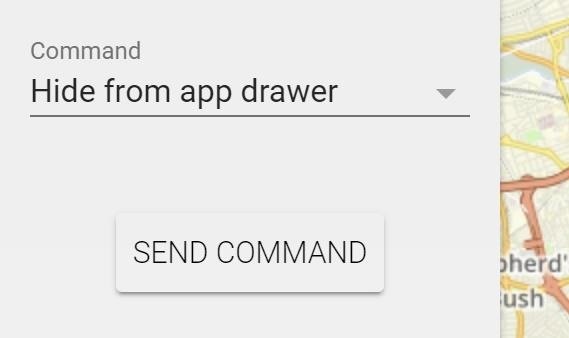
On the left, you'll find the command drop-down menu. It doesn't immediately tell you which options are and aren't available based on the settings and root status of the device, so you'll have to play around with a couple by clicking on them in the drop-down menu and then choosing "Send Command." If you want to check the in-app settings or you forgot to change one during the setup, then click "Change app settings" and "Send Command."
Step 10: Hide Cerberus from the Target's App Drawer (Optional)
The final thing you may want to do is hide the app so the target can't just stumble upon it. It's unlikely they would notice if you didn't do this, but it's best practice to do it anyways. From the Command drop-down, select "Hide from app drawer," then "Send Command." When they go scrolling through the list of all their apps, Cerberus won't show up anymore.
Bonus: Take Control of the Target Device via SMS Texts
Cerberus has the ability to let you send any of its commands to the app on the target device through text messages. To do this, send a text to the target's phone number that begins with cerberus, space, your password, and then a command. This feature is useful when the device has cellular service but no data service.
Below are some of the most useful commands listed. Note that these SMS texts are not hidden, so the user will see them and likely figure out what's going on. This is more for fun, and may be more useful for those actually using this for anti-theft.
cerberus password find (to locate the device)
cerberus password startemergency hours (to locate for any number of hours)
cerberus password screenshot (to grab a screenshot and send it to your email address)
cerberus password capturevideo (to capture a video and send it to your email address)
cerberus password speak text (to make the device speak a message)
cerberus password alarm text (to display a message and play a loud alarm)
cerberus password wipe (to wipe the device memory)How to Protect Yourself from Android RATs
There are few fundamental guidelines that you can follow to help prevent anyone from performing this sort of attack on you. First and foremost, put a lock on your phone.
- If you're using any of the last two generations of flagship Android phones, then the fingerprint sensor is your best option. They tend to be fast and reliable and offer the best security.
- Fingerprint sensor not an option? Try to avoid facial recognition unless it's 3D-capable, otherwise, the attacker can simply present a picture of your face in front of the phone and unlock it.
- Patterns are equally useless because an attacker can simply analyze your phone smudges in a bright light and get a good idea of the pattern to unlock it.
- Your next best option aside from fingerprint scanners or 3D facial recognition software is to use at least a six-digit PIN, preferably a full password.
Second, don't let anyone touch your phone for any reason. It's pretty hard for someone to download a RAT when they can't get ahold of the phone to begin with. As an extension of this, try to keep your phone within sight at all times, even when you're in the shower or the phone is charging.
Do keep in mind that an attacker could attempt to get you to download a malicious APK from them, so as always, be careful what you tap on your phone and be immediately suspicious of unknown sources.
If you have any questions, you can ask here or on Twitter @The_Hoid.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























3 Comments
or you could just set up an apache web server put meterpreter apk there. then quickly go to your website download apk and set it up. did it several times by social engineering. takes only 15 seconds free and more useful. if you open up 2 ports on your modem you could do it over wan too.
I stumbled on this post and it is much enlightening. This is 2019, is the app still applicable? I already downloaded if from "aptoide" as I couldn't find it on Playstore. The process described in the post is still relevant and applicable?
It is anything but difficult to fall prey to bumbling programmers, yet in the wake of understanding this, I trust you never must be a survivor of programmers who can't finish the activity given to them. I was at one time a casualty yet not any longer and this is on the grounds that I have discovered the best programmer ever and I wish to tell you that (cryptocyberhacker @ gmail com), Whatsapp:+15188160274 is as well as can be expected ever consider and he generally convey and he his solid.
Share Your Thoughts