Null Byte Features


How To: Find Hacked Accounts Online ~ PART 1 - haveibeenpwned
You must have read news about hackers dumping the data online, recent one was Ashely Madison. It's only the big companies' data, which gets noticed once it is out. There are many other small leaks which don't even get a mention. So this article is the first one of my series which will help you to find hacked accounts. Some of you must already know about this, but this post is intended for the new learners. This also serves as an example of my learning how a good service can be used in other w...

How To: Embed a Backdoor in an Exe File
Welcome back Hackers! We have embed a Backdoor in to a PDF file,Android package File.

Subterfuge: MITM Automated Suite That Looks Just Lame.
Remember when MITMing people to pentest webapps and log-ins you had to fire Ettercap,Arpspoof, SSLstrip, then look for credentials in the captured packets?

How To: Steal Form Data from Your Fake Website
Though you can use the Social Engineering Toolkit to clone websites, this way is much more customisable.

How to Train Your Python: Part 1, Introduction
Recently I've been looking around our wonderful community and I've seen some absolutely hands-down fantastic python scripting articles. But, in the end, these series weren't very extensive. I've been wanting to do a series on teaching python for a while now, and I don't mean just the basics, I mean to make an extensive series that takes it all the way from "Hello, World!" to popular third party modules, and everything in between!

How To: Run an VNC Server on Win7
OTW's great Tutorial Hack Like a Pro: How to Save the World from Nuclear Annihilation gives me the inspiration to try this on Win7 sp1.

How To: Use I2P to Host and Share Your Secret Goods on the Dark Web—Anonymously
Some of you might be using Tor to host hidden services, and some of you might not even know what hidden services are. If the latter's you, do not miss this article. Why? Because you can host your websites and services on the I2P darknet. It's safe and secure—it's anonymous.

How To: Who Is Anonymous? How the Wall Street Journal and the NSA Got It Wrong
Over the past couple of weeks, there have been a series of high-profile hacks and leaks. From the rooting of CombinedSystems, to a secret FBI conference call leak, all the way to the distributed denial-of-service (DDoS) attacks on U.S. government sites—with a lot in-between. As governments move to close their long fingers around the free speech that exposes their secrets, this shadowy collective of loose-knit, but like-minded individuals are hell bent on preventing them. Or are they?

Hack Like a Pro: Linux Basics for the Aspiring Hacker, Part 24 (The Linux Philosophy)
Welcome back, my aspiring hackers! Although this article may have been better placed first in this series, I doubt that anyone would have read it when just starting out studying Linux. Now, that you are well into your Linux studies and have some familiarity with how it operates, I'd like to take this moment to explain the philosophy around the Linux operating system.

Goodnight Byte: HackThisSite, Realistic 5 - Real Hacking Simulations
Last Friday's mission was to accomplish solving HackThisSite, Realistic 5, the fifth and last in my series of realistic hacking simulation missions. This time, telemarketers are invading people's privacy, and it was up to us to stop them! The job was to get root on the site and delete the contact database in order to return the right of privacy to its victims.

How To: Web Development for Hackers 1.1: HTML,CSS,JS
hello hackers,newbies and followers of this great community, after some research here in our community, I noticed that there is not even one tutorial that teach Web Development. We have a lot of tutorials on how to hack web site but many do not know exactly how a web site is composed, then I decided, meeting the community's needs, begin to teach people how to develop web sites.

Hack Like a Pro: Linux Basics for the Aspiring Hacker, Part 23 (Logging)
Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

News: 1.5 Million Credit Cards Hacked in the Global Payments Breach: Was Yours One of Them?
As hard as you try to protect your valuable information with strong passwords and anti-doxing measures, there's nothing you can really do when someone else gives up your goods. And that is the case with the recent Global Payments breach.

How To: The Art of 0-Day Vulnerabilities, Part3: Command Injection and CSRF Vulnerabilities
INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

How To: Set Up SoftEther VPN on Windows to Keep Your Data Secure
Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

How To: Set Up Private Internet Access in Linux
This tutorial is for those who've purchased an account with Private Internet Access to hide your VPN and would like to set it up in Kali. Please note, you can chose to run your PIA service from your Windows computer without configuring it in linux as long as you'll be using a NAT connection. Using a NAT connection will allow your Windows machine and Kali Virtual Machine to use the same IP address, hence if your IP is hidden on one, it will be hidden on the other.

How To: Probe Websites for Vulnerabilities More Easily with the TIDoS Framework
Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

Community Byte: Coding a Web-Based Password Cracker in Python
Welcome to another Community Byte announcement! In the past two sessions, we have coded an IRC bot in Python capable of issuing commands. Since it can issue commands and most of you are new to programming, that project will stay idle for a while. Other commands such as voice and half-op can be easily hacked in via common sense, even if you weren't there for that session.

Hacking Windows 10: How to Capture & Exfiltrate Screenshots Remotely
Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

How To: Simulate a RAT on Your Network with ShinoBOT
A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) toolkit. Unlike standard administration RATs, these tools are designed to be delivered stealthily and operate undetected.

News: God's Eye
If you have seen the movie Fast and Furious 7, you know what "God's Eye" is. Well this might spark interest to you.

News: Complete Arch Linux Installation, Part 2: Graphical User Interface & Packages
Welcome to the second part of the Arch Linux installation tutorial! We are installing Arch because of the amount of users who want to learn how to get into Linux. Arch is a simple, minimalistic distro, designed not to hold the users hand, but to push them to know their system and customize it to the core. This will make you feel accomplished, as well as give you the extra edge of being knowledgeable of the GNU/Linux operating systems.

News: Advanced Cracking Techniques, Part 1: Custom Dictionaries
How did it happen? How did your ultra-secure WPA password on your wireless network get broken into? Well, you might have just found yourself at the mercy of a cracker.

How To: Remove BackTrack & Install Kali as a Dual-Boot System Without Damaging Your Hard Drive
Yesterday, I wanted to remove BackTrack from my system and install Kali, and at the same time didn't want to damage my Windows 7 or my hard drive. I searched a lot of articles, but almost all of them wanted me to have a backup Windows 7 CD, which I don't possess.

How To: Phreak (Basics)
Get some tinfoil hats and make a time machine because we are about to go back to the 90s and learn about some phreaking.

How To: Become an In-Demand Data Scientist with 140+ Hours of Training
The overarching and expanding field of data science and analysis has become virtually inseparable from areas such as programming and development.

News: Use ProtonMail More Securely Through the Tor Network
ProtonMail has long been the favorite of journalists and security-conscious professionals, with Edward Snowden the most famous example. But these days, everyone cares about anonymity, so it's no surprise that ProtonMail currently has over 2 million users. And now the service is even better.

How To: Play Emulated Games on Linux with Your Xbox 360 Controller
I have to say, the Xbox 360 controller is the best controller ever created. When I first held it back in 2005, I swore that the dudes working at Microsoft came over and took a molding of my hands because of how great it felt. The thing felt like it was born there.

Social Engineering: How to Use Persuasion to Compromise a Human Target
Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

News: Hacker Points Out iOS Security Flaw That Allows iPhone Text Spoofing
Security researcher and iPhone hacker pod2g has brought attention to a flaw in Apple's iOS that allows the user to change the reply address of an SMS message. This bug has been a part of the iPhone's SMS since the first iPhone in 2007, but Apple has yet to address it. Basically, there's a section in the text payload called User Data Heading (UDH) that controls some advanced features, one of which is the reply address. By changing the reply address of a text message, you can make someone send ...

How To: Find Hacked Accounts Online ~ PART 3 - Cached Pages
Welcome learners, lets us proceed further with the information we already have. In this post we will explore more about finding hacked accounts online. We will look into how to find juicy info in pastes which are deleted on Pastebin.
How To: Cover Your Tracks After Hacking a Wifi
Greetings null-bytians. Say you have been able to penetrate your neighbour's AP, and of course you had spoofed your MAC address. Now you go on and test to see with excitement if the password really works and the MAC is still spoofed. You login successfully and you browse the web forgetting to check what your current MAC is. Well, if you may do an ifconfig command, you will see that your permanent MAC is being used. Oh!! and guess what, ... your real MAC has been logged. Even though there is t...

How To: Make a Change-of-IP Notifier in Python
In this article I'll show you how to make a simple IP address notifier. The program will text you your new IP address, in the event that it changes. For those of you with dynamic IPs, this is very useful. I'm constantly frustrated when my IP changes, and it's handy to be notified via text when it happens. To use the program, you'll need Python 2.7 or later, urllib2, and a program called "text" (see this article here to get it).

How to Train Your Python: Part 2, Basic Output, Variables, and Types
In python, or any scripting language for that matter, there are certain things that you will carry with you throughout your entire scripting career. Some of the most basic things that you will keep with you are output, variables, and their value types. We'll start by going over output, then cover variables and their types. So, let's get started!


How To: Use One-Lin3r to Quickly Generate Reverse Shells, Privesc Commands & More
A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

How To: Hack a Site Knowing a Bit of HTML (hackthissite.org) Part 3
Hi guys. I'm here to go for level 7 now lets get it start but i apologize u all that i posted this very late but now lets rock:
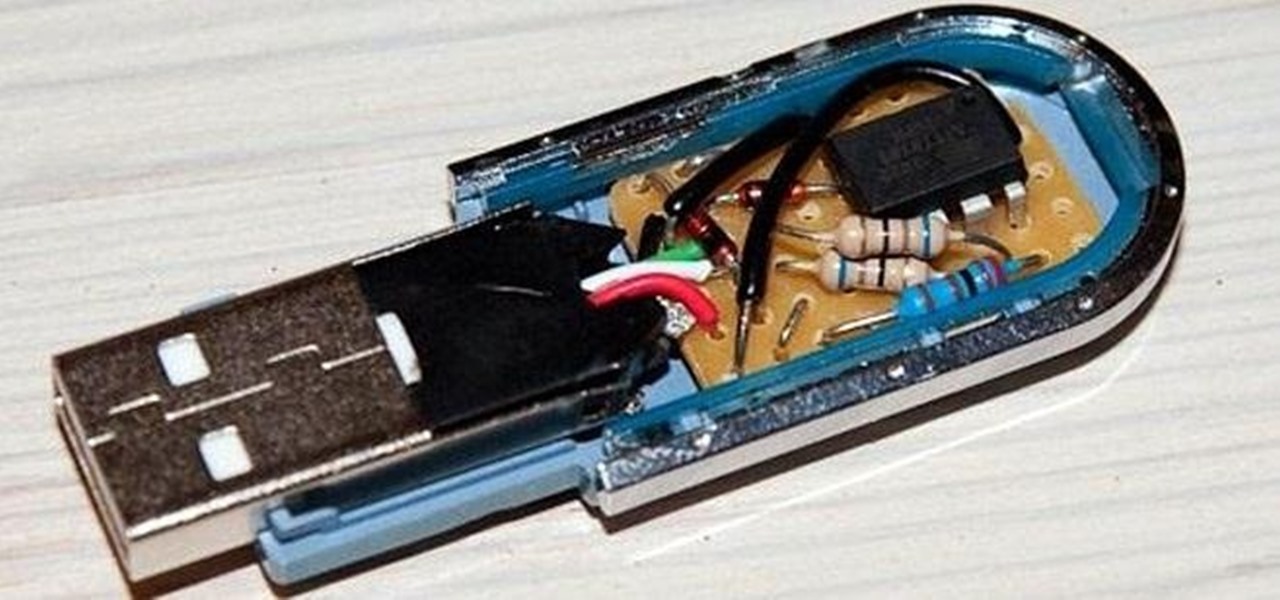
How To: Create Strong Passwords Automatically with This DIY USB Password Generator
No matter how many PSAs are published on the topic, studies continue to show that we are generally terrible at creating secure passwords and PINs. Using the same password (or variations of it) for multiple sites is another huge no-no that the majority of people ignore, and even though you should change your passwords frequently, most of us don't.

News: Catch Creeps and Thieves in Action: Set Up a Motion-Activated Webcam DVR in Linux
When it comes to webcams these days, most people are using their laptops over desktops. The cameras are centered, integrated, and require no configuring. They're a cinch and usually have great resolution. So, then what do we do with all of those old wired desktop webcams that we've accrued over the years? Even if you still use an external USB one, chances are you're not using it daily, so why not come up with a better use for it?

Farewell Byte: Goodbye Alex, Welcome Allen
Hello, fellow Null Byters. Today, with mixed feelings, I want to let you know that this is my last official post as the admin of Null Byte. I've come to the decision that I need to spend more time focusing on my studies. Over the past 5 months, I have enjoyed building this community and teaching people unorthodox methods of doing things, creating things, and hacking them. But I'm also excited to be delving deeper into the studies that brought me here in the first place.







