As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing man-in-the-middle attacks.

Hello Hackers! Welcome to my 2nd Post: This is a tutorial explaining how to hack android phones with Kali.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

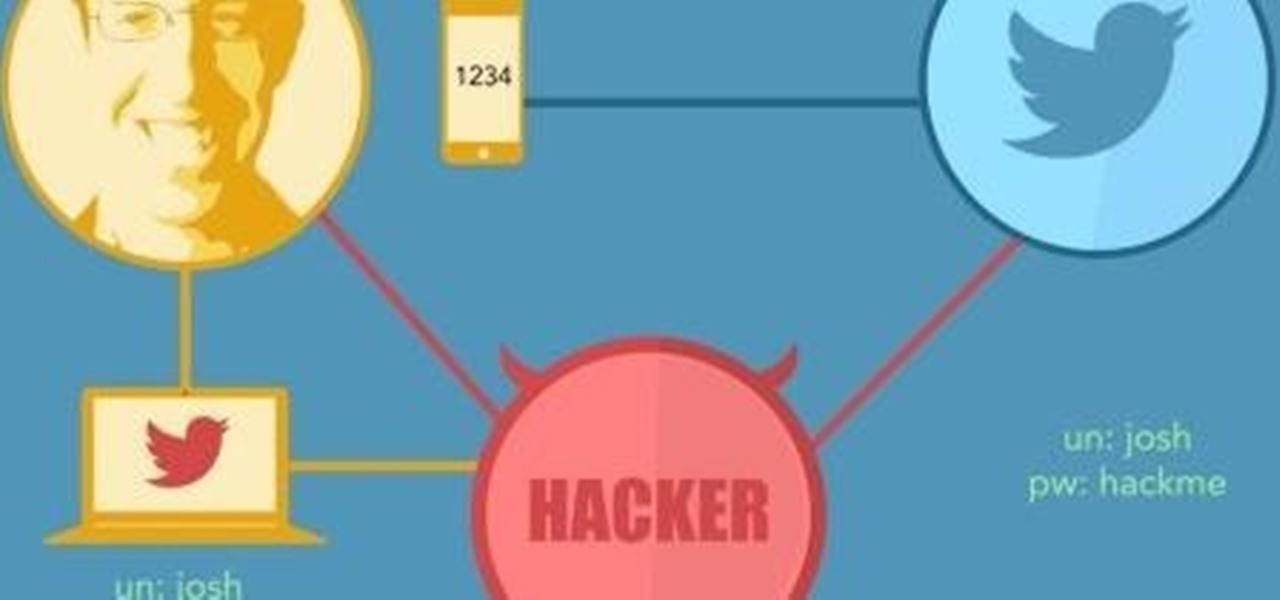
Researchers at the University of California, Riverside and the University of Michigan announced recently that they have developed a hack that works 92% of the time on Google's Gmail system on Android, as well as with the H&R Block app.

Hello Elite Hackers! Welcome to my 3rd Post, which explains how to hack any account like G-mail, Facebook, etc.

Hello My Fellow Hackerzz.. This is my first How-to and i'll be updating the “Hacking Android Using Kali” to msfvenom and some FAQ about known problems from comments. So Here we GO!!

Hello friends. This is actually my first how to.

Hey guys I am starting this Series because I thought there was a lack of post about Hacking from Android.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

OR rather How to make the Backdoor Persistent: Hello, my Cold and Merciless Hackers,

Welcome back, my budding hackers! This is the initial post of a new series on how to hack Facebook. It's important to note here that each hack I'll be covering is very specific. I have said it before, but I feel I need to repeat it again: there is NO SILVER BULLET that works under all circumstances. Obviously, the good folks at Facebook have taken precautions to make certain that their app is not hacked, but if we are creative, persistent, and ingenious, we can still get in.

Hi guys, this is going to be kinda like a follow up to my previous post on hacking facebook with the remote keylogger. If you haven't seen that post I suggest you do. So like you can click here. Anyway let's move on.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

Hello my fellow hackers, it's been a while since my last post, I can't get the time now-a-days for the posts but can manage to tend to comments.

Want to take advantage of your neighbor's super fast Wi-Fi connection? If they're smart, they probably have it password protected (otherwise you wouldn't be reading this, would you?). But if you have an Android phone, you can get back at them for always parking in your spot and slamming the door when they get home at 2 a.m.—by stealing...er, borrowing, their connection.

There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take camera snapshots, and even record with the microphone without the user knowing.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

Welcome back, my greenhorn hackers! As all you know by now, I'm loving this new show, Mr. Robot. Among the many things going for this innovative and captivating program is the realism of the hacking. I am using this series titled "The Hacks of Mr. Robot" to demonstrate the hacks that are used on this program.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

We've shared a capture-the-flag game for grabbing handshakes and cracking passwords for Wi-Fi, and there are some upcoming CTF games we plan on sharing for other Wi-Fi hacks and even a dead-drop game. While security-minded activities and war games are excellent ways to improve your hacking skills, coding a real video game is also an excellent exercise for improving your programming abilities.

Some of us use our smartphones for almost everything. Manufacturers know this, so they try to make their devices as convenient as possible to use, but sometimes that convenience comes with a cost to security. The very same technology that allows you to easily share music with friends and make purchases can also put you at risk. Photo by sam_churchill

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

In my last tutorial I very briefly introduced Zanti , but in this tutorial I will start to show its many features. The first step on hacking is recon . You could use Nmap , but the problem with Nmap on Android is that by itself, in order to gain full functionality your phone must be rooted. Thank goodness for a few geniuses in Zanti's dev team whom managed to implant full fuctionality of Nmap in Zanti without rooting your phone. With that being said, boot up your Android phone and lets start ...

This is my first How-To on Null-Byte, so I hope it's not too complicated written, because I am not a native english speaker. I don't use pictures, but this Tutorial is a good supplement for my updated Tutorial here.

Hi Elite Hackers! Welcome! to my 4th post. This tutorial will explain, how to extend a (hacked) AP's range with a wireless adapter. I made this guide because after hacking an AP it was difficult to connect to it (poor connection) and further exploit it. You can also use this:

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

Hi guys. Hope you all had a good Christmas , today i have a tutorial for you.

Hi , Today i will show you how to do HID Keyboard Attacks With Android BUT without using Kali NetHunter BUT You will need to install custom kernel to your Android device, that will add keyboard+mouse functions to it's USB port,So Lets Get Started

Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and modifying the kernel configuration to add special features, in this case, wireless adapter Alfa AWUS036H support, one of the most famous among Null Byters.

This past weekend, one of the most notorious hacker organizations in the world, Hacking Team, was hacked by some unknown organization. The Hacking Team is an Italian company that sells it software and services to companies and governments (yes, my rookie hackers, there are legitimate companies who sell their services to governments—Vupen, being one of the most famous and lucrative).

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

The Drug Enforcement Agency (DEA) has been purchasing spyware from the Milan-based Hacking Team and its US subsidiary Cicom USA since 2012. Public records reveal invoices between Cicom USA and the DEA that have ranged between $22,000 to $575,000 from 2012 to 2015.

The Null Byte community is all about learning white hat hacking skills. In part, this is because I believe that hacking skills will become the most valuable and important skill set of the 21st century.