Friday's Community Byte was weird. The intent was to do a HackThisSite mission, but upon time to begin, everyone in there was programming without my assistance, with the help of Sol Gates. This is great! It's really awesome that everyone enjoys programming that much and will make the effort to learn even when I am not present. So, a tip of my hat to Mr. Sol Gates and the rest of you fine people.

How to Crack Passwords Faster by Putting Your GPU to Work with HashcatSecurity on the internet is always changing. Not too long ago, having a 10 character password meant that you were safe from all forms of hash cracking. Hash cracking is when you take a string of characters that have been passed through a cryptographic hash and try to reverse them. The normal processors that are housed inside of our computer cases are general purpose. The processors are not meant for handling complex math an...

Password strength and encryption are important things when it comes to computers. A password is the entire security of your computer, and OS passwords are not hard to break. Most users believe that if you have a password on your computer via the OS, that you are safe. This is not true at all, sadly.

There is a near-infinite amount of ways a computer can be broken into. But that does not mean that there isn't a reason to secure our computers as best as we possibly can. It's like the principles of a secure house. Which are the most secure houses? The ones with locks and advanced alarms, obviously, but not for the reasons people normally think.

In Linux, all password hashes are normally stored using the MD5 hashing algorithm in the /etc/shadow file, but MD5 is algorithmically weak due to collision vulnerabilities. The new recommended standard are the higher level SHA-2 hashing algorithms, SHA256 or SHA512. As a friend pointed out to me, Ubuntu is currently the only distro implementing SHA-2 as the default. With SHA-2, your passwords take an unreasonably larger amount of time to calculate. This will greatly decrease how many password...
For those who doesn't want their root password on Kali Linux live USB persistent login to be reset to the default 'toor',

How did it happen? How did your ultra-secure WPA password on your wireless network get broken into? Well, you might have just found yourself at the mercy of a cracker.

Paying for web hosting isn't ideal in most situations. If you have your own website, hosting it yourself is very acceptable and easy to do, assuming your internet bandwidth permits. Most people want to run a personal site, nothing crazy, so hosting from home on low-bandwidth internet is actually a better solution in most cases.

This Null Byte is a doozey.

Welcome to the closing of the second HackThisSite and programming Community Byte. First and foremost, I would like to ask that people start showing up on time to the Community Bytes. If you need help converting your time zone to PST, go to Time Zone Converter. When users do not show up on time, we have to go backwards and catch everybody up. This wastes time and will also make other users' experience less enjoyable when they have to watch and listen to the same thing 100 times. Punctuality as...

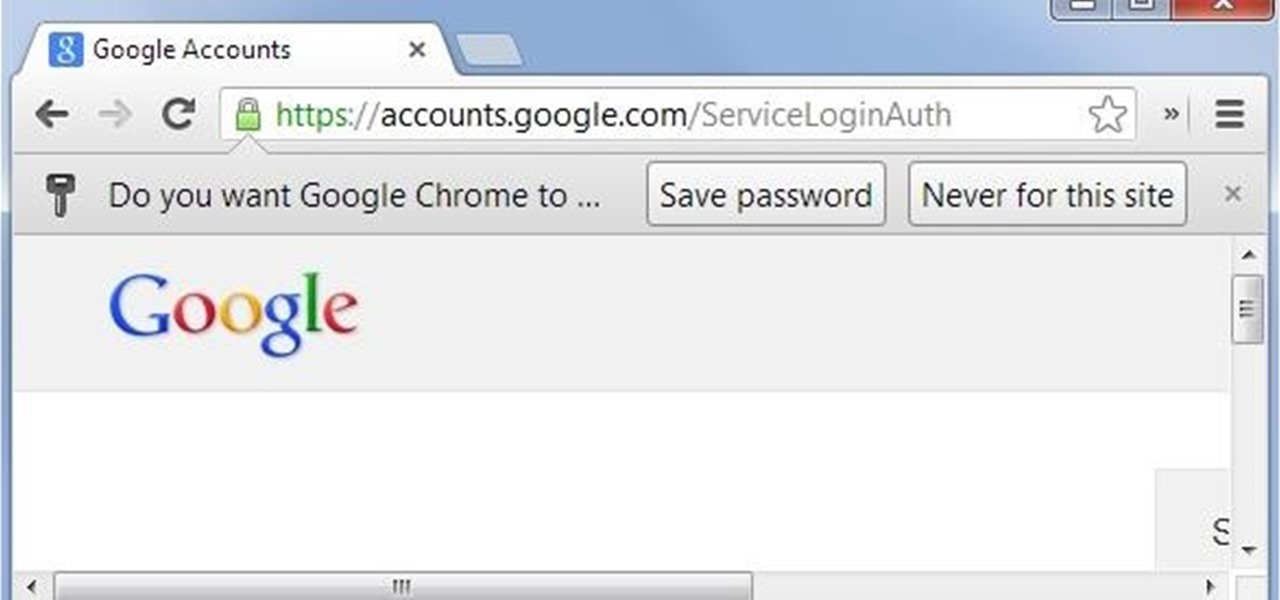
These days I found a very beautifull python script that just prints the google chrome usernames and passwords that are stored on your machine.

This is a followup from my recent series on XSS exploitation, giving a few extra attacks/tricks to try.

Lorrie Faith Cranor: What’s wrong with your pa$$w0rd? | Talk Video | TED.com.

A lot of different places have computers with controls on them for several things; some have controls for installing software, some for running software, blocking websites, opening certain file formats, etc.

Null Byte is looking for moderators. More threats to computers exist every day. Not only do we have computer viruses and malware, but we have rootkits and other nasty pieces of code that can log your keyboard strokes or even add your computer to a botnet to attack other websites. Your computer can be infected even if you have anti-virus software installed. I can't stress enough how easy it is for a hacker to write a piece of code that gets around every piece of anti-virus software.

Cheers to another completed Community Byte project! Things went well regarding timeliness and being friendly to the other coders and students. If you've got ideas for our next mission, or an idea for a tutorial, submit them to me. Friday, our mission was to take out HackThisSite, basic mission 5. This mission focused on JavaScript, again. This time there is a little bit more security in place.

Welcome to the Goodnight Byte for HackThisSite, Basic Mission 4. In Friday's session, we tackled some coding in Gobby. Nothing special, just a few modifications to the NullBot script we made a few session ago, and some education on regular expressions. Apart from coding, we did our scheduled HackThisSite mission. We had to take on some JavaScript, which was a new thing for Null Byte. This mission taught us about client-side HTML manipulation through JavaScript injections. This just means that...

Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their computers to protect from various threats. Here are a few things that should always happen when doing business on computers:

SSH is amazing, and we praise its existence on Null Byte for many reasons. Notably, it allows us to reroute our traffic through encrypted ports on our local host to be sent to its destination when on the go. You can even control your home computers remotely over a secure and encrypted connection. This is handy for a multitude of reasons.

Following the first part in this series on advanced cracking techniques, we are going to go over how we can intelligently crack passwords using the old-fashioned bruteforce method. These unique cracking techniques aren't widely used, because most crackers are Script Kiddies who have no idea what the concepts are behind cracking passwords, thus, word won't get around too quickly.

Skype is a great service. It allows a free solution for VoIP to VoIP calls, and cheap VoIP to landline calling. However, a very disturbing, little known fact that might push you away from Skype does exist. If you closely read the terms of service agreement, it clearly says that Skype is allowed to decrypt your messages whenever they please. Here at Null Byte, we tend to enjoy our anonymity, don't we?

Our mission for this week's Community Byte was to create a Python program to crack web-based passwords, like the ones you would see on an email or router login. I wanted it to be universal in the sense that it could be easily modified and adapted to another website just by changing a few variables. That was a success! Even though people weren't on time to the coding session, everything went well.

Archiving and compression is a great way to store and prepare files for sending. You can reduce the size of a file, turn a group of files into a single file, and even encrypt and password the contents! Just take a look at this image to see how much it compressed a 28GB text file.

Welcome to the second Null Byte in a series educating you on Social Engineering awareness and techniques. Today, I'm going to show you how a saavy Social Engineer would trick a friend into unknowingly surrendering their Facebook password. My intent is to warn and demonstrate how easy it is to succumb to phishing via Social Engineering, and therefore expose yourself.

Having an SSH or Secure SHell to tunnel your traffic through is something we have talked about many times at Null Byte. As we know, it allows us to securely route and encrypt our traffic through a remote server, effectively anonymizing us and protecting our traffic from all forms of analysis—simultaneously. We have gone over how to make a home SSH tunnel. However, the question has come up, "How can I get an SSH tunnel to somewhere other than my computer?" This would be useful in a situation w...

Permanently deleting files is something that a lot of people aren't aware of. Actually, most people think that once a file is deleted, it is gone forever. This is not the case. Hard drives write to the disk via magnetic charges, positive and negative correlate to 1s and 0s for binary. This is then interpreted into information for the computer to use and access.

Leaving your wireless router at its default settings is a bad idea. The sad thing is, most people still do it. Once they've penetrated your network, hackers will change your router settings so they'll have an easy way back in. This allows them to change your network into a shell or proxy so they can forward their traffic anonymously through you when committing other dirty deeds.

I have had a lot of people ask me, "How does my neighbor keep getting into my wireless?!". Chances are, these people are all using WEP, a deprecated wireless encryption protocol. Either that, or you are using one weak WPA passphrase.

When i went to class today, a good friend asked me a question. He wanted to know what the best hacking software was to basically do everything. What i told him was this: Well there isn't an "Ultimate" tool boot there are a number of tools which deserve a "Medal." So what i'm trying to say here... What are some of the best hacking tools available right now? For starters i created a list with some of the tools.

Social engineering is described as the clever manipulation of the natural tendency of human trust. All of the passwords, locks, and encryption in the entire world are useless against a good social engineer who can charm or trick you into giving it up.

Have you ever had this happen? Your main OS is windows, and you just istalled a nux dualboot. But when you installed GRUB to the mbr, your windows loader got deleted! Hence you are not able to get into windows anymore... Sucks. But there's also a solution!

Welcome, everyone! While Linux distributions are almost always used for exploits, security, pentesting and other stuff covered in Null Byte, knowing the Windows Command Line (or Command Prompt) is a useful skill that can help you in various ways, such as using exploit programs made for Windows or using the command line on someone else's Windows computer.

Null Byte is looking for forum moderators! Last Friday's mission was to accomplish solving HackThisSite, basic mission 9. This mission delves a little further into Unix commands and remote directory traversal (which is just a fancy term for going through folders blindly).

With a lot of Null Byters playing around with Linux because of its excessive use in the hacking world, some of you are bound to run into some trouble with the installation at some point or another. If you make a mistake, or you're intimidated by the wonky-looking installation screen, you may want to just stick with Windows. However, you may notice it can be hard to go back once you've crossed a certain point in the installation. Your Windows installation may be broken or unbootable.

Often times when staying at a hotel or anywhere for that matter, you'll whip out your laptop and check the local area for Wi-Fi. I know you've all been in my shoes when you find an unsecured network that appears to be public Wi-Fi belonging to the hotel or airport, and you connect to it. You connect fast and perfectly, only to find that when you open your browser, it says you don't have an account, and are filtered from accessing the web. This is because the owners of the network want to keep...

One of the main reasons I was held back from fully switching over to Linux was the fact that media streaming is nearly impossible. You have two choices in Windows: either you use file sharing with Windows Media Player, or you can just use the Windows Media Center. But both of these softwares are not for Linux or Mac. Microsoft doesn't like to make open source software because they believe in making a profit, instead of allowing others to innovate it.

Something that can shy a user away from making the switch to Linux is not having the option to go back to Windows. Luckily, there are solutions like dual-booting, where you can have both OS's installed right next to each other. However, Windows 8 appears as if it will block dual-boots with its neo-space BIOS that have been developed. Sneaky-sneaky. Windows users could still throw in a Linux live CD to try out Linux, but what does a Linux user do when they need something from Windows?

You want to put out a live web server, but you don't want to be owned in the process. An expert eye for security is not needed if you take a few basic steps in locking down the hatches. Most successful attacks today are not the complex, time-consuming tasks you might think, but simple lapses in policy that a hacker can take advantage of to compromise your server.

Last Friday's mission was to accomplish solving HackThisSite, realistic 2. This second mission in a series of realistic simulation missions was designed to be exactly like situations you may encounter in the real world, requesting we help a friend take down a racist hate-group website.

This is it! That last basic mission. Last Friday's mission was to accomplish solving HackThisSite, basic mission 11. This final mission in the basic series was made to give us the skills and a place to apply our Apache server knowledge. This will teach us how to traverse through awkward and custom directory structures.