Welcome back, my novice hackers!
We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal.
This msfconsole puts us into an interactive mode command prompt with the Metasploit Framework. This is my favorite way to use Metasploit, but certainly not the only way that is available to us.
Metasploit has multiple ways of accessing its power and tools including a command line (msfcli), a GUI (armitage), and a web-based (msfweb). In this tutorial, we're going on a tour of Metasploit to introduce you to the inner structure and some new capabilities of Metasploit.
Step 1: Open a Terminal & Find the Directory
In each of my previous tutorials, we've started from the interactive mode of Metasploit (the msfconsole). This time, however, let's go to the Metasploit directory directly so that we can explore its structure. We can get there by typing:
bt > cd /pentest/exploits/framework
Step 2: Look Around Inside the Framework
Now that we're in the Metasploit Framework directory, let's take a look around. First, let's do a listing on this directory.
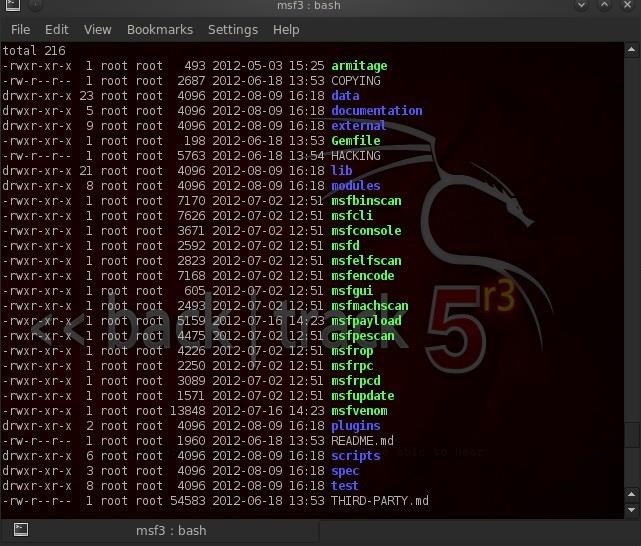
If you look to the top of this long listing, you will see a directory called armitage. This is a GUI for driving Metasploit that we'll return to in another tutorial.
Also note near the bottom a directory called scripts. This includes, among other things, meterpreter scripts such as key_scan that enables us to run a keylogger on the victim's computer.
Also note the following files—msfcli, the command line version of Metasploit, and msfencode, the command we used previously to re-encode a payload to get past antivirus software.
Step 3: Explore the Modules
Let's now explore the Metasploit modules. These are the blood and guts of Metasploit. We have, for instance, used "exploit" modules and "payload" modules. This is where they reside. Type in:
cd modules
ls -l
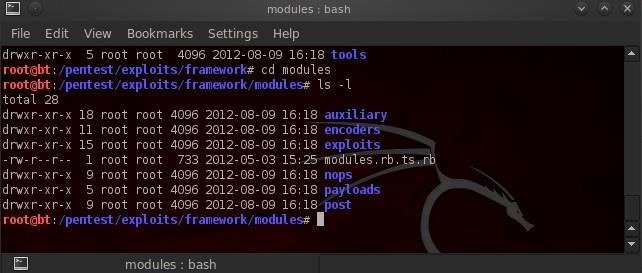
As you can see from the screenshot above, Metasploit contains multiple modules. These include:
- auxiliary
- encoders
- exploits
- nops (no operations)
- payloads
- post (post exploitation)
These are the key modules in Metasploit, and as you've already guessed, we haven't even begun to explore the auxiliary, nops, and post exploitation modules, although we have used the exploits, payloads, and encoders.
Step 4: Open the Exploits Module & Look Around
The module we're probably most familiar with are the exploits. This is the module that contains the exploits that take advantage of a vulnerability in an application or an operating system, which enables us to place our payload on the victim. Let's look inside. Type:
cd exploits
ls -l
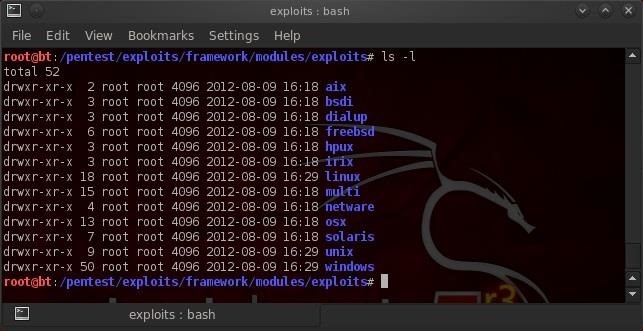
The exploits module is broken into sub-directories that are specific to the operating system we're attempting to exploit. For instance, you can see at the top the directory, aix, (IBM's proprietary UNIX operating system) exploits. As we scan down, we can see exploit directories for:
- freebsd
- hpux
- irix
- linux
- netware
- osx
- solaris
- unix
- windows
If you have done any of my Metasploit tutorials and hacks, you've likely used exploits in the windows exploits directory. Let's look around there. Type:
cd windows
ls -l
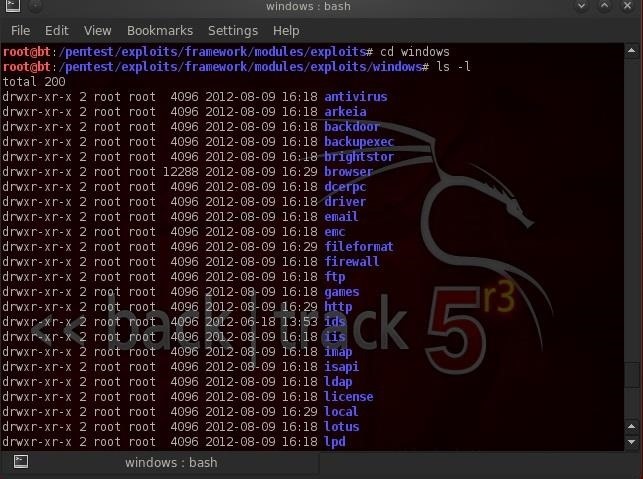
Now, we can see that the windows exploits are broken down into types of windows exploits. It's important to note that exploits are very specific. Not only are they operating system specific, but also application or service specific, port specific, and sometimes even language specific. Recently, we looked at exploiting the Internet Explorer in Windows 7. Let's see if we can find it in the browser directory. Type:
cd browser
ls -l
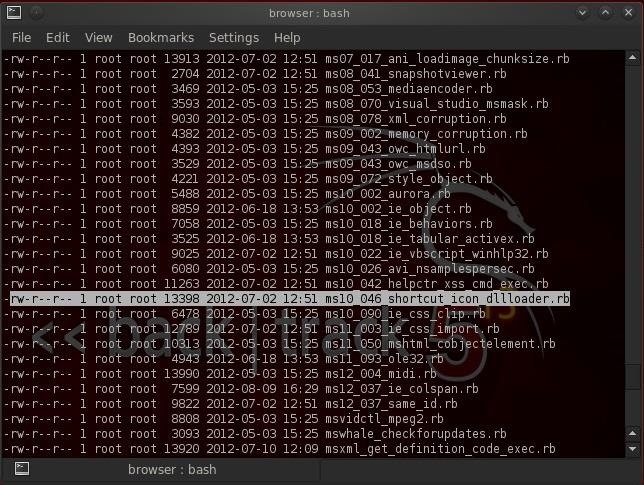
As you can see in the above screenshot, our ms10_046_shortcut_icon_dllloader exploit is highlighted.
If we wanted to, for instance, find an exploit in this directory to hack Adobe products from the browser, we could use our Linux skills and "grep" for it. Type:
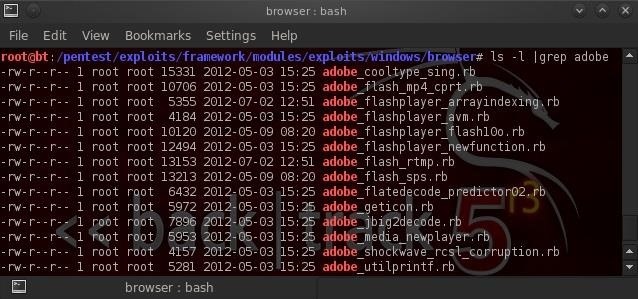
ls -l | grep adobe
When we hit enter, the terminal filters (grep) the output and shows us only the windows browser exploits that take advantage of Adobe products.
Step 5: Explore the Payloads Module
Next, let's navigate to the payloads directory. Type:
cd /pentest/exploits/framework/modules/payloads
Then we can do a long listing on that directory by typing:
ls -l
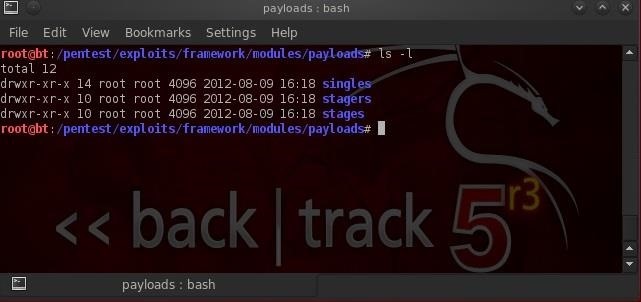
We can see that payloads are broken down by types.
- singles
- stagers
- stages
Let's open up singles to look around. Type:
cd singles
Once again, we can see that the Metasploit Framework categorizes the payloads by operating system. Let's move to the generic directory and see whether we can find the generic shell_reverse_tcp payload that we used to get a command prompt when hacking Windows XP. Type:
cd generic
ls -l
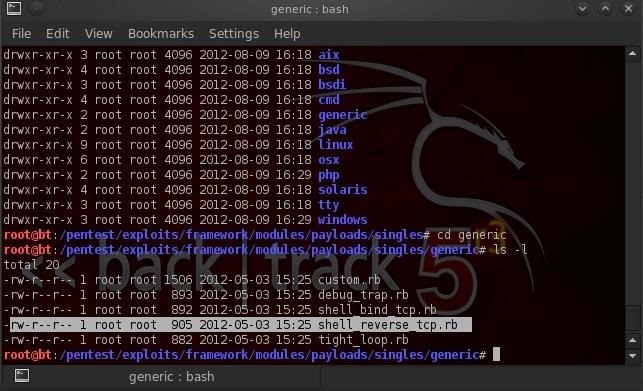
As you can see in this screenshot, I have highlighted the generic reverse tcp shell that we used earlier.
In the tutorial on encoding your payload to get past AV software, we created a payload that we re-encoded using shikata_ga_nai. Once we have that payload re-encoded to be undetectable to AV software and we want to use it other exploits, we could save it here in this payloads directory to make it available again and again to get past antivirus software
I'm hoping that this brief exploration of the structure of Metasploit was enlightening. I'll try to come back in the future and further elaborate on its structure including the post exploitation, auxiliary and nops modules, but don't wait for that. Start doing your own exploration to better understand this wonderful and powerful tool to make you a better and more effective hacker.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















16 Comments
master using ARMITAGE we can acess GUI mode of victims machine.???
King;
Armitage allows you to control Metasploit from a GUI. To run the victim from GUI, use VNC.
OTW
is vnc works for all o.s.???
There are VNC's for Windows, Linux and mac.
master otw : A question always strikes in my mind...how can i trace me stolen machine.....while its lan card and wifi card both have been changed....?????
Secret:
If I understand your question, you are asking "How can I trace my stolen machine?".
If the person who stole it changed out the network interface card (NIC) and the wireless interface card, it will be very difficult. Generally, the thieves are not sophisticated enough to do that especially if those cards are integrated to the motherboard.
OTW
YES master exactly it was my question.......master thr is not any other medium present other than NIC and WIFI card , to trace my machine...........actually one of my friend lost his machine ????
It will be difficult to trace even with the MAC addresses of those interfaces. If you have automatic updates for AV software, the AV firm may be able to help you trace it to an IP when it gets its updates. An IP can be traced to a city without a subpoena, but would require a subpoena or search warrant to trace it to a specific home/office.
thnx a lot master for ur quick responses.......u are really awesome.... i learnt a lot from here..... will be always grateful to u.............. :)
Secret:
You are so welcome. Hope you stay around as we have so much more to do and learn.
OTW
hi, i've a problem..
When i use the command line "msfconsole" i received this eroor message:
Failed to connect to the database: could not connect to server: Connection refused
Is the server running on host "localhost" (::1) and accepting
TCP/IP connections on port 5432?
could not connect to server: Connection refused
Is the server running on host "localhost" (127.0.0.1) and accepting
TCP/IP connections on port 5432?
i've had lot of problem during a pentest or when i execute an exploit in may lan machine..
Is this problem caused by this message of connection failure??
What can i do to fix this problem?
thanks...
and how do we actually link to to the target p.c i presume by ports and i.p adress
hy, occupytheweb
i'v a problem same like DARK SOUL .
and when i use the command line "cd pentest/exploits/framework" i recieved error message "bash: cd: pentest/exploits/framework: No such file or directory" how to fix it?
Hi, this is the msf directory of Kali /usr/share/metasploit-framework/modules, thanks and sorry for my English T.T
So any ad blockers for LINUX recommended? Love this site but it is EXTREMELY annoying to have ads constantly (and I mean constantly) loading and reloading while I try to read through the site...
(sigh of relief) NVM, I found an excellent one Adguard extension for Chrome browser. =) YAY! I can enjoy my favorite site again!
Share Your Thoughts